Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to edit Super Mario World levels with Lunar Magic.

Many ways to help the environment are costly, but using less electricity is one measure that will save you money. Learn how to lower your electric bill with this how to video.

Learn how to get out lipstick stains. It's not just lipstick on your collar; your favorite shade can turn up anywhere! That's why you need a battle plan.

Compulsive gambling is a recognized addiction, just like alcoholism or chemical dependency. Follow these steps to see if you might fit the profile. Recognize the signs of compulsive gambling with this guide from Howcast.

A few handy tricks can turn your school cell into a cozy suite. You Will Need

There’s nothing a rabbit likes more than toys they can climb inside, shred, and drag around. With a good pair of scissors, you can make a steady supply of bunny-pleasers that won’t cost you a thing.

Whether you want to pave your patio or give someone cement shoes, here's how to mix concrete like an expert. Learn how to mix concrete by hand with this instructional video.

Go thrifty! Go vintage! Go second hand. With the right approach and an open mind, a trip to your local thrift store can yield some fashionable bargains. Buying used is a smart solution to this economy, and gives you a smart sense of fashion.

Your dog travels all around the house all day. Here are five places to remember to keep clean. Watch this how-to video as the Dog Channel offers five places your dog encounters that are important to clean regularly. Remember he always travels to his toys, crate and bed.

Making your own homemade wallet can be a fun and rewarding hobby. Get your sewing machine out and you can add your own style and personality to your wallet. Learn how to make a homemade wallet from a professional seamstress in this free sewing and crafts video series.

Learn how to do single leg knee extensions. Presented by Real Jock Gay Fitness Health & Life. enefits

Learn how to do seated leg presses. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do alternate hand kiss wide grip pull ups. Presented by Real Jock Gay Fitness Health & Life.

Learn how to do rope hammer curls. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do lean barbell single side rows. Presented by Real Jock Gay Fitness Health & Life. Benefits

Well I've converted one of these rc bikes into a snarling (ha ha) nitro powered machine. I'm now going to convert my other stock model into a brushless monster. This particular bike had a rather bumpy crossing from the USA when I bought it from ebay. It got damaged in it's box and was returned to the sender. He, very nicely, found a new set of front forks, fitted them and posted it back to me, for no extra charge! Top Man! It's a bit sluggish, stock, so I think sticking a MAMBA MAX 7700kv mot...

In this tutorial, we learn how to make day of the dead paper mache sculptures. First, you will make the paper mache sculptures into different body shapes, then use a sharp knife to carve along the sculpture. Use different paints and colors to make the characters more believable and realistic. Use a thick paper mache when making these, because you will lose a lot of layers when you are thinning it down and shaving it into shape. When finished, you will attach the different pieces of body parts...

Mudtokens of YouTube found a way to quickly level up in Modern Warfare 2 and wants to share. His method of doing this is to get 12 of your friends into a ranked lobby, making it a full game. After this, you get one person from each team, who will be the one getting ranked up. For this to work, however, you need 2 load outs, both of which need to have One Man Army and Stopping power, one with a light machine gun, and the other with a riot shield. The two meet up in the game, and take turns blo...

See how to vote in York County in PA by watching this video tutorial. With the new touchscreen electronic voting machines in Pennsylvania, you'll need to check out this video to make sure your ballot gets counted. So, if you want to get out this year and vote for Hillary or Obama, then make sure you do it right, don't screw up! This video is a must for you old folks with no computers skills at all, so get up to date and vote electronically in your county election.

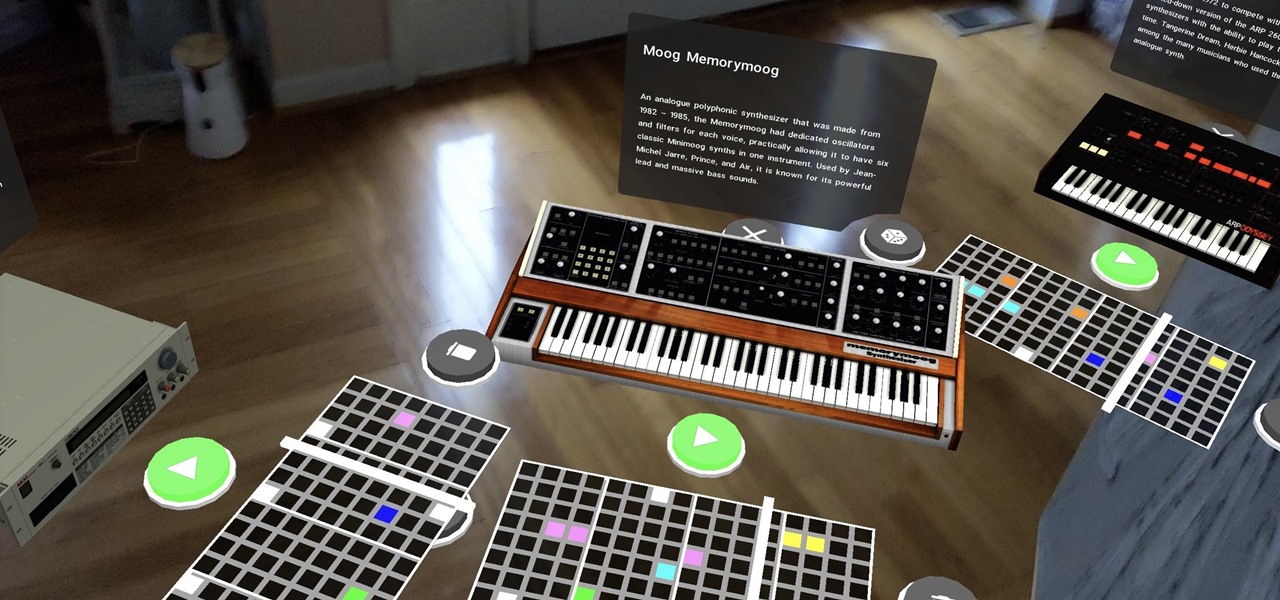
Museum curators typically frown upon visitors touching paintings, sculptures, and artifacts, but not when those exhibits are displayed in augmented reality.

EternalBlue was a devastating exploit that targeted Microsoft's implementation of the SMB protocol. Metasploit contains a useful module that will automatically exploit a target, as long as it's vulnerable. But what if we wanted to exploit this vulnerability without Metasploit holding our hand? It can be done using a Python file to exploit EternalBlue manually.

While most kids his age are busy playing Fortnite, 11-year-old Yumo Soerianto is developing augmented reality games. Kids like Soerianto are the future of the augmented reality field — they'll likely be coming into their own as professional developers right as AR technologies become lightweight and powerful enough to be contained in a pair of sunglasses.

With Virtual Network Computing, you don't need to carry a spare keyboard, mouse, or monitor to use your headless computer's full graphical user interface (GUI). Instead, you can connect remotely to it through any available computer or smartphone.

Being able to write your own hacking tools is what separates the script kiddies from the legendary hackers. While this can take many forms, one of the most coveted skills in hacking is the ability to dig through the binary files of a program and identify vulnerabilities at the lowest level. This is referred to as binary exploitation, and today we're going to check out a tool known as Protostar.

Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing us to intercept and modify network data. This can be dangerous for private data, but also be fun for pranking your friends.

A potentially groundbreaking new app targeting retail financial services hopes to bring augmented reality to your local bank and credit union.

CEO (and NR50 member) Tim Cook and Apple unveiled the long-awaited lineup of next-generation iPhones today on stage of the Steve Jobs Theater, packed with hardware improvements to facilitate AR experiences from ARKit, which will arrive with the iOS 11 on Sept. 19.

Tesla founder and CEO Elon Musk said during the Model 3 launch party Friday night that all Tesla cars in production have the same driverless hardware, signaling that Tesla's jump to Level 4 hinges on a software update — but Musk didn't exactly say that.

The world is full of vulnerable computers. As you learn how to interact with them, it will be both tempting and necessary to test out these newfound skills on a real target. To help you get to that goal, we have a deliberately vulnerable Raspberry Pi image designed for practicing and taking your hacking skills to the next level.

Robots are always really cool, if you ask me. Sometimes they're made out of Legos, and that's even cooler.

This tutorial follows the same idea as my original tutorial for windows, but I've redone it to work with Mac OS X. Here's how to get a meterpreter session from your victim opening a malicious word document:

Hello friends! This tutorial will teach you how to build a local pentesting lab on your Linux machine which will enable you to easily install common web applications so you can practice locating and exploiting their known vulnerabilities (or discover new ones!). In particular, this is an excellent way to learn how to hack Wordpress, Joomla, and Dupral plus many more!

So you want to create a meterpreter virus, but you keep getting caught by AV. How do you create one that will go undetected? In this tutorial, I'll teach you how to code your own simple virus that will download a powershell payload from an apache webserver and execute it - bypassing antivirus.

First of all, Merry Christmas and Happy New Year to all Null-Byters that learn and teach in this wonderful site. In this article we will explore the basics of the meterpreter's IRB (Interactive Ruby Shell).

In the last tutorial, we learned how to make functions and how they work on the high level. This time, we will take a peek under the hood again, stare deep into its soul and see its ugliness face to face to see how it works in the lower level.

Do you ever thought that you can't control an Internet disconnected system? I saw a funny video in Chema Alonso's youtube channel (A well-known hacker of my country and creator of Fingerprinting Organizations with Collected Archives among other security tools), and decided to post something similar.

Imagine this scenario: You exploited a system using metasploit and you want to install a backdoor. You have a few options;

I grew up in a rural town, and that meant that we dehydrated a lot of food. Even with a hungry family of five, there was no way that we could eat all of the season's tomatoes before they molded, or all of the orchard's apples before they grew soft, or all of the wild mushrooms that we picked. And so our dehydrator was always getting a good workout.

Did you know Kali 1.0.8? You probably did, and you probably know about the EFI boot option that has been added.

This is the best how-to's website that I've ever seen, and I wanted to join it. It taught me a lot, but, because I'm here to learn too, please correct me if I'm wrong.