When it comes to hacking guides, most are written from the perspective of a Linux user. There are a few outliers, but it's mainly Linux, which leads to the idea that Linux is the only OS that's viable for hacking. This couldn't be further from the truth. A properly set up Apple machine can do quite a bit of heavy lifting.

It feels great to wrap up in a big, fluffy towel after a steamy shower, but it's frustrating when that towel isn't quite up to the job. Over time, towels lose their ability to hold water and dry as needed thanks to daily use and the biggest culprit—laundry detergent.

Skulls. What spooky Halloween décor or staging of Hamlet is complete without a skull or two popping up? For ghoulish special effect and/or setting a dramatic scene, skulls are absolutely integral. Well, with some artistry, hardware supplies, and a good dose of patience, you can create your own inexpensive prop skulls for use however you please.

Un-dull your crocheted sweater with a little creativity. Adding some decorative details and features to your clothing will do wonders for fashion, and could hide unsightly holes! Embellishing with crochet can be a creative way to repair a piece of clothing, and it can add flair to a piece by inserting a neckline or a hem.

If all things go well, you'll only have to take your road test once. That's the goal: to ace your test on the first try and then start driving on your own. Granted, it's a nerve-racking experience, but keep in mind that the California Department of Motor Vehicles wants you to pass. So much so, they give you the examination answers ahead of time! All you have to do is study.

Russian cyber disinformation campaigns have many missions, but one of particular interest is using technology to monitor, influence, and disrupt online communications surrounding culturally sensitive topics or protests. The ability to watch these events, and even filter positive or negative tweets to amplify, gives rise to the ability to execute a number of disinformation campaigns.

The easiest way around a security policy is to find users who don't follow it. The Have I Been Pwned database identifies accounts with information breached by major third parties like Yahoo and LinkedIn. With Maltego, hackers can locate breached accounts created using company email addresses, potentially giving attackers access to a company account if the employee reuses a compromised password.

The internet is constantly under siege by bots searching for vulnerabilities to attack and exploit. While conventional wisdom is to prevent these attacks, there are ways to deliberately lure hackers into a trap in order to spy on them, study their behavior, and capture samples of malware. In this tutorial, we'll be creating a Cowrie honeypot, an alluring target to attract and trap hackers.

Don't panic if you spill grease on your clothes or the couch. Start tackling it instead. Learn how to get grease stains out of fabric with this how-to video.

Today's post is a small go-to guide for beginner programmers in Null Byte. With many of our community members picking up programming from our Community Bytes, it only makes sense to lay out a one-stop guide for your reference. Hopefully this guide will help you make an educated and thoughtful choice on what programming languages you want to learn, and how you want to learn said languages.

Augmented reality might not be able to cure cancer (yet), but when combined with a machine learning algorithm, it can help doctors diagnose the disease.

Greetings my fellow hackers.

It seems like each day new rumors and leaks come out for Huawei's upcoming P series devices. Everything from its name change to its specs has been leaked, sometimes with contradicting rumors. One of the biggest leaks is the inclusion of triple rear cameras, a first for smartphones.

This is the very first article in my series on setting up a Mac for hacking. In this series, I will be operating under the assumption that you have a clean install of macOS (previously OS X). If you aren't starting with a clean installation, there may be a few differences, but nothing we can't help you out with.

Check out this video to learn how to build a rapid fire egg dispenser in Minecraft. You can also load this machine with arros, snowballs, and other goodies and watch them fly. This machine fires a lot of items in a little time.

Check out this video for an elegant solution to the problem of sugar cane harvesting. Streamline your harvesting with this clever, effective, machine. Watch the video to learn how to replicate this design and build your own sugar cane harvesting machine in Minecraft.

Watch this instructional quilting video to quilt a tendril or "C" background fill with a longarm sewing machine. This pattern is a simple and convenient way to create an elegant background fill on many kinds of quilts. It helps to draw the tendril pattern with pen before trying it with the longarm sewing machine. Customers love it.

A router table is a stationary woodworking machine in which a vertical spindle of a woodworking machine projects from the table, allowing you to cut wood at many different speeds. Different cutter heads or drill bits may be mounted on the router depending on the material you're working with.

This video demonstrates how to work out your quadricep muscles using a leg extension machine. The video walks you through adjusting the machine to your body type and explains how to perform the exercises correctly.

Video: . Hi, this is a quick demo about how to backdoor executables (software) sent over HTTP using MITMF, backdoor factory

Welcome back, my hacker novitiates! In the previous part of this series, we looked at how to use Metasploit's web delivery exploit to create a script to connect to a UNIX, Linux, or OS X machine using Python. Many members of the Null Byte community have asked me, "Can we do the same for a Windows systems?" The answer is YES!

Welcome back, my neophyte hackers! In today's hack, we're going to have a bit of Halloween fun. Have you ever had a boss who made you miserable with his micro-management and nagging? Maybe you thought he unfairly fired your friend/colleague? Well, now here's your chance to get a bit of revenge and keep him or her off your back!

For anyone using open source information to conduct an investigation, a balance between powerful tools and privacy controls are a must. Buscador is a virtual machine packed full of useful OSINT tools and streamlined for online research. This program can easily be set up in VirtualBox, and once that's done, we'll walk you through some of the most useful tools included in it.

Barrow's article on Pupy made me wish for a RAT that could target an OS frequently used by gatekeepers at startups, tech companies, and creative firms: macOS. Once run, a RAT can do severe damage by dumping a user's stored credentials for many accounts. The best loot lives in the Chrome Password cache, and EvilOSX, an OS X RAT, infiltrates macOS and dumps these credentials.

Welcome to the sequel to the latest post on writing 64 bit shellcode! This tutorial will assume that you are aware of everything mentioned in the last one, as I will try to make this tutorial void of formalities and straight to the point! If you have not read the last one, I suggest doing so unless you are familiar with basic assembly programming and system calls. This is by no means rocket science, so therefore I will simply repeat my TL;DR from last time before we get started, so that the a...

Before cutting the rotors select a centering cone that fits about halfway through the center hole of hub-less rotor or bearing spacer to center the rotor to the spindle. After select two identical clamps that fit the rotor without interfering with the machined surfaces of the rotor. Slide one clamp onto lathe shaft, open end out Slide spring, followed by centering cone. Slide on the rotor and outer clamp followed by the bushing, spacer, and nut. Tighten nut and Install damping strap. Adjust t...

While SSH is a powerful tool for controlling a computer remotely, not all applications can be run over the command line. Some apps (like Firefox) and hacking tools (like Airgeddon) require opening multiple X windows to function, which can be accomplished by taking advantage of built-in graphical X forwarding for SSH.

A remote administration tool, or RAT, is a piece of software used for remotely controlling machines. They are commonly used by tech support to gain remote access for troubleshooting purposes, but RATs are also an important part of a hacker's advanced persistent threat (APT) toolkit. Unlike standard administration RATs, these tools are designed to be delivered stealthily and operate undetected.

Welcome back, my amateur hackers! Many of you here are new to hacking. If so, I strongly recommend that each of you set up a "laboratory" to practice your hacks. Just like any discipline, you need to practice, practice, and practice some more before you take it out to the real world.

In my first installment in this series on professional hacking tools, we downloaded and installed Metasploit, the exploitation framework. Now, we will begin to explore the Metasploit Framework and initiate a tried and true hack.

Black Mirror, Netflix's technology-horror anthology, never fails to provide thought-provoking entertainment centered around emerging and futuristic technologies, and the third season's second episode, "Playtest," delves deep into the worlds of mixed, augmented, and virtual reality. While designed to leave you haunted by the end, offering a more "evil" narrative than we'll likely see in our actual future, the episode explores possibilities that aren't as far off as one might think.

Web applications are a prime target for hackers, but sometimes it's not just the web apps themselves that are vulnerable. Web management interfaces should be scrutinized just as hard as the apps they manage, especially when they contain some sort of upload functionality. By exploiting a vulnerability in Apache Tomcat, a hacker can upload a backdoor and get a shell.

No operating system is stricken with as many vulnerabilities as Windows, and it's often a race to release the latest patches to fix things. From an attacker's point of view, knowing which patches are present on a Windows machine can make or break successful exploitation. Today, we will be covering three methods of patch enumeration, using Metasploit, WMIC, and Windows Exploit Suggester.

The art of privilege escalation is a skill that any competent hacker should possess. It's an entire field unto itself, and while it's good to know how to perform the techniques involved manually, it's often more efficient to have a script automate the process. LinEnum is one such script that can be incredibly useful for privilege escalation on Linux systems.

NetBIOS is a service that allows for communication over a network and is often used to join a domain and legacy applications. It is an older technology but still used in some environments today. Since it is an unsecured protocol, it can often be a good starting point when attacking a network. Scanning for NetBIOS shares with NBTScan and the Nmap Scripting Engine is a good way to begin.

Popping a shell is often the main goal of a hacker, and it can be exciting when executed properly, but sometimes they do have their limitations. Metasploit's Meterpreter probably needs no introduction, but this powerful, dynamic payload can offer a leg up over normal shells. To prove it, we'll show how to take a normal command shell and elevate it to a Meterpreter session.

With only one profitable quarter in the last two years, LG's mobile division is undergoing a shakeup. With a fresh set of executives, LG has delayed the expected launch of the upcoming G7 and instead decided to start the year with yet another variant of the V30.

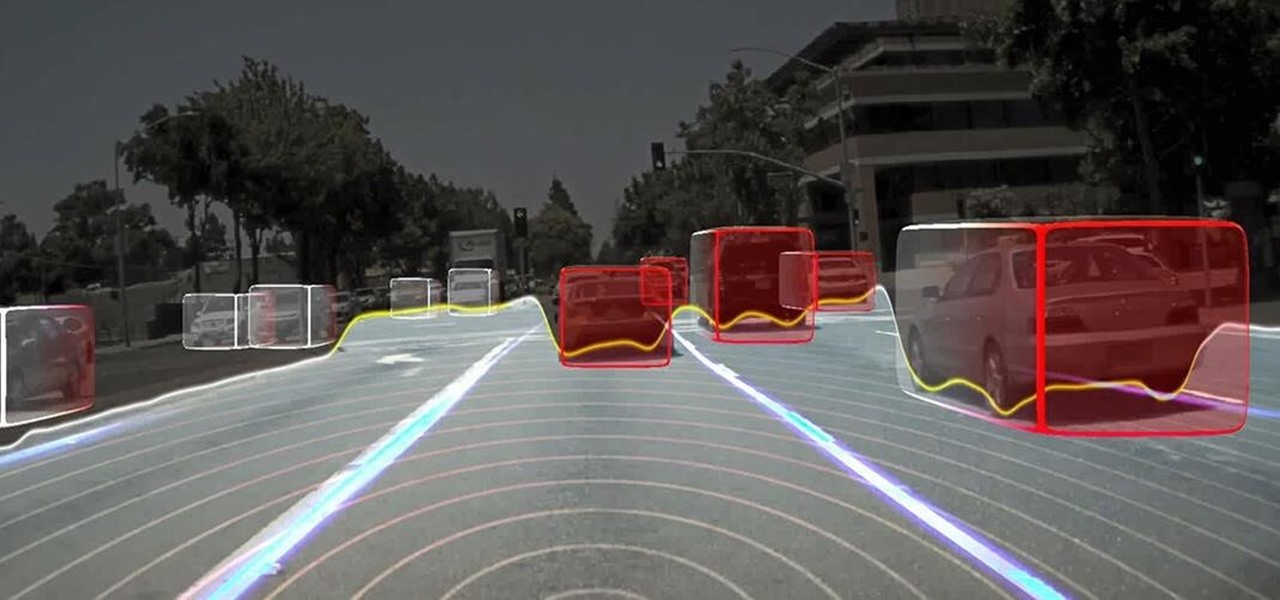
Long before Nvidia figured out how to embed neural networks in its graphics processor units (GPUs) for driverless vehicles, it and other chipmakers were already making the same kinds of devices for 3D games and other apps.

Nvidia has emerged as the indisputable leader in chips for Level 3 and even more advanced driverless applications, catching some of the world's largest semiconductor makers and automotive suppliers by surprise.

Welcome back, my greenhorn hackers! A few years back, Microsoft implicitly recognized the superiority of the Linux terminal over the GUI-based operating system by developing PowerShell. Since Windows 7, every Windows operating system has had PowerShell installed by default, and they even made PowerShell capable of running Linux commands on Windows!