It sounds like a dream come true: just press a button on your phone, and 30 seconds later, a machine produces a custom-made, ready-to-eat meal. Finally, science comes through for the truly lazy!

Welcome back, my tenderfoot hackers! A short while ago, I started a new series called "How to Spy on Anyone." The idea behind this series is that computer hacking is increasingly being used in espionage and cyber warfare, as well as by private detectives and law enforcement to solve cases. I am trying to demonstrate, in this series, ways that hacking is being used in these professions. For those of you who are training for those careers, I dedicate this series.

Normally, office supplies and food don't mix, but you can use a paper shredder to make fresh pasta in your very own home (...or office). In other words, you don't have to buy a bulky and expensive piece of equipment to make fresh pasta. If you already have a paper shredder, you can simply feed pasta dough through it for perfect tagliatelle noodle strips that will taste far better than anything you can buy at the store. Step 1: Clean Your Machine

Welcome back, my hackers apprentices! To own a network and retrieve the key data, we only need to find ONE weak link in the network. It makes little sense to beat our heads against heavily fortified systems like the file and database server when we can take advantage of the biggest weak link of all—humans.

Welcome back, my budding hackers! One of the keys to becoming a professional and successful hacker is to think creatively. There is always a way to get into any network or system, if you think creatively. In previous tutorials, I have demonstrated ways to crack passwords on both Linux and Windows systems, but in this case, I will show you a way to get the sysadmin password by intercepting it from a Remote Desktop session.
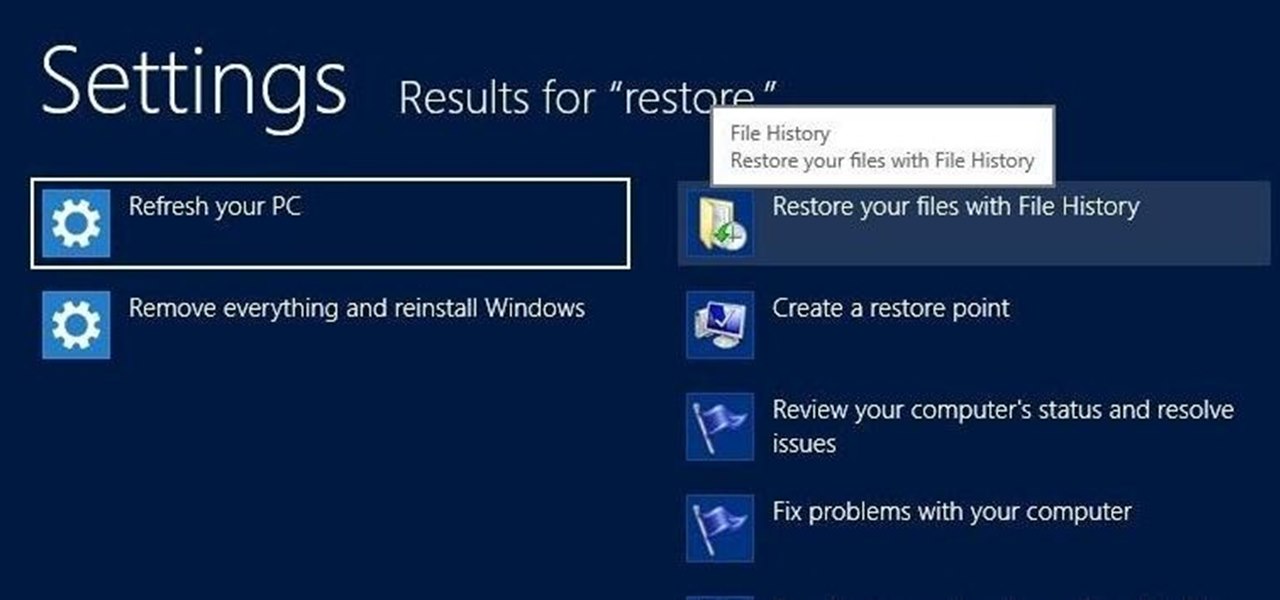
There is nothing worse than losing valuable information or programs on your computer. And if you've ever accidentally deleted a file or document, you know how agonizing that entire process can be.

Cloth diapers are a little bit more work than the disposable kind. No need to worry, with some regular laundry detergent and vinegar your baby will be happy as a clam in his clean and irritant free diapers.

Check out this demonstrational video to learn how to create lighting FX and fog behind the back of a tombstone that's a great prop for Halloween sets.

While our time with the Protostar VM from Exploit Exercises was lovely, we must move on to bigger things and harder challenges. Exploit Exercises' Fusion VM offers some more challenging binary exploitation levels for us to tackle. The biggest change is that these levels are all network services, which means we'll write our first remote exploits.

The latest Star Wars movie, Solo: A Star Wars Story, has grossed almost $350 million worldwide during its first month in theaters. This is a good opportunity to discuss how hackers can use media hype (in this case, Hollywood movie hype) to disarm an unsuspecting Windows user into inserting an evil USB stick into their computer.

Its official: On May 8, T-Mobile finally released the Android Oreo update for the LG V30 and V30+. Now, every major US wireless carrier has pushed the update. For me, this update is a big deal. Not only does Android Oreo bring some new tools and features, but LG has also included a few additions as well.

There's no doubt Kali has established itself as the most popular penetration distribution available. However, just because it's the fan favorite of beginners and security researchers doesn't make it right for everyone. Manjaro Linux is a beginner-friendly Arch-based distribution which can be easily weaponized with the Black Arch expansion, creating a friendlier first-time Arch experience.

PowerShell Empire is a post-exploitation framework for computers and servers running Microsoft Windows, Windows Server operating systems, or both. In these tutorials, we will be exploring everything from how to install Powershell Empire to how to snoop around a target's computer without the antivirus software knowing about it. If we are lucky, we might even be able to obtain domain administrator credentials and own the whole network.

Twelve years ago Google launched its Cloud Platform, and the world has never been the same. This suite of cloud computing services has changed how modern businesses operate. Whether you use it for data storage, management tools, computing, or machine learning, the Google Cloud Platform is essential.

In the coming years, artificial intelligence (AI) will revolutionize every facet of technology and business. AI researchers are in high demand. Salaries in this field are regularly in the hundreds of thousands of dollars.

More information is available to us now than ever before. We simply cannot make sense of so much data on our own. Thankfully, we have programs to do the heavy lifting for us.

File permissions can get tricky on Linux and can be a valuable avenue of attack during privilege escalation if things aren't configured correctly. SUID binaries can often be an easy path to root, but sifting through all of the defaults can be a massive waste of time. Luckily, there's a simple script that can sort things out for us.

SSH, or the secure shell, is a way of controlling a computer remotely from a command-line interface. While the information exchanged in the SSH session is encrypted, it's easy to spy on an SSH session if you have access to the computer that's being logged in to. Using a tool called SSHPry, we can spy on and inject commands into the SSH sessions of any other user logged in to on the same machine.

One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get around these defenses, and we'll be looking at two methods to beat the system and successfully pull off LFI.

UAC is something we've all dealt with on Windows, either as a user, administrator, or attacker. It's a core feature of the Windows security model, and for the most part, it does what it's supposed to. But it can be frustrating as a hacker when attempting privilege escalation, but it's easy enough to bypass UAC and obtain System access with Metasploit.

We already know that Samsung's Galaxy S7 is one of the most versatile smartphones ever made, complete with edge-to-edge displays, water resistance, and a huge battery. But what's versatility without durability? How much punishment can the Galaxy S7 take? Let's play a game of Samsung Galaxy S7 Punch-Out!! and see what happens.

Welcome back my networking geeks. In this part we are going to keep discussing about IP Addressing and I hope after you finish reading it you will become an IP wizzard.

Recently, I've been experimenting with BeEF (Browser Exploitation Framework), and to say the least, I'm hooked. When using BeEF, you must "hook" the victims browser. This means that you must run the script provided by BeEF, which is titled "hook.js", in the victims browser. Once you've done that, you can run commands against the victims browser and cause all kinds of mayhem. Among these commands, there is an option to use the victims webcam. This is what we'll be doing here today, so, let's g...

Welcome back, my novice hackers! There are SOOOO many ways to hack a system or network, which means you need to think creatively in order to be successful.

Maybe you don't have Mac OS X Lion yet, but you can dress Snow Leopard up just like it with this Lion theme. Watch the video to learn how to get a Mac OS X Lion theme on your Mac Snow Leopard machine.

You can wear the dress you've always wanted to by making it yourself at home, with nothing more than a sewing machine, a shirt, and a few yards of fabric. Follow the instructions in this video to learn how to make clothes that fit your body, and sense of style, perfectly.

ProjectKinectMagicMirror combines augmented reality and CT-scan imagery to create a virtual "X-ray machine." Another amazing Microsoft Kinect hack to add to the vault. The ingenuity is infectious... Get inspired. Make-your-own.

It's time to replace the water filter on your Krups coffeemaker - something you should do approximately every two to three months for best results. This quick video shows you how to easily replace the charcoal filter on your Krups coffee machine.

It doesn't make common sense for most people to use irons on anything other than cloth, but if you'rea (really) careful you can actually employ irons to flatten and straighten paper products, as well.

Coffee is one of the world's greatest discoveries, but a bad cup of joe can be devastating for your morning. Technivorm makes some of the world's best coffeemakers, and their Technivorm Moccamaster drip coffee brewer is one of the greatest. It's handmade in the Netherlands, and is considered to be the best coffeemaker ever. Poul Mark, founder of Transcend Coffee in Edmonton, Alberta Canada, demonstrates how to brew a great pot of coffee with this renowned Dutch-made machine.

Paper or plastic is a thing of the past; both options are equally terrible for the environment. With this tutorial, learn how to turn your old bed sheets into funky grocery tote bags. You will be the envy of everyone at the store with these adorable, homemade bags.

Managing screen real estate can be a chore on any operating system. In this video, learn how to set up a split-screen display for your machine running Windows Vista.

While scrunchies might not be that common a hair accessory anymore, you can make one of your own by following the steps in this how-to video. You will need two satin fabric pieces of 50cm, a sewing machine, sewing thread, a pair of scissors, marking pins, as well as brown and black satin fabrics. It's so easy to make, even a cat can do it. Check out this video sewing tutorial and learn how to make a frilly hair scrunchie.

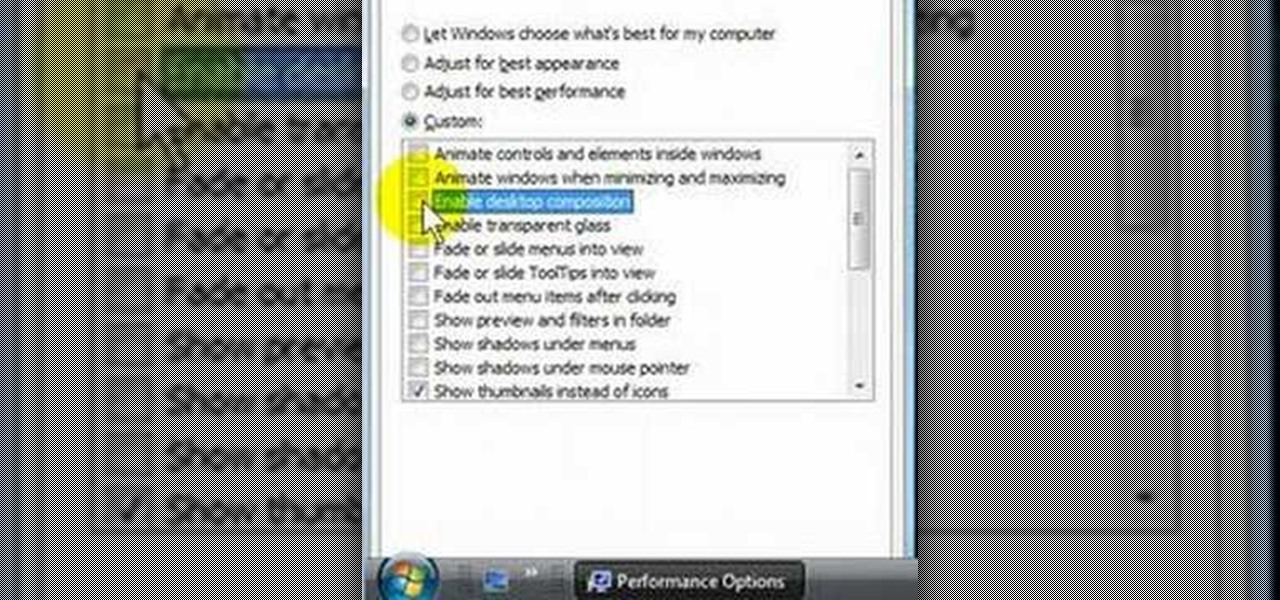
Are you disappointed with the sluggishness of Microsoft Windows Vista? In this Windows video tutorial, you'll learn how to use the Performance tool in Windows Vista to disable senseless features you don't need and to make Vista run more quickly in the process. For more, or to get started speeding up your own Windows Vista machine, take a look!

New to the Ubuntu Linux distribution (or one of its derivatives) and looking for a way to start programs automatically when you boot up your machine? Take heart: This video tutorial will show you how to accomplish just that using your system preferences. Take a look!

Create a card with an embossing machine and chalk. Any embossed image can be colored in easily with a little big of chalk for a soft effect. Watch this video card-making tutorial and learn how to use embossed paper and chalk to make a card.

Watch this video tutorial to learn how to bypass the cumbersome process of making squaring backings for your quilts. This is an attempt to show you how and why you may never want to make a perfect square backing for your longarm sewing machine again.

This video card making tutorial shows how to make a name placard, great for social functions. Also demonstrated are how to use a Cuttlebug embossing machine and how to replicate the stamp kissing technique. Watch this instructional video and learn how to make a name card placard.

Often we neglect simple tools because the big fancy machine tools are so attractive. But often these basic tools are the best for the jobs. This how to video is a quick review of some basic hand tool techniques with Kaleo Kala.

This how to video sewing tutorial demonstrates how to sew a whip stitch by hand, just in case you don't have a sewing machine. The straight stitch is excellent for simple hems, decorative stitching and gathering fabric.