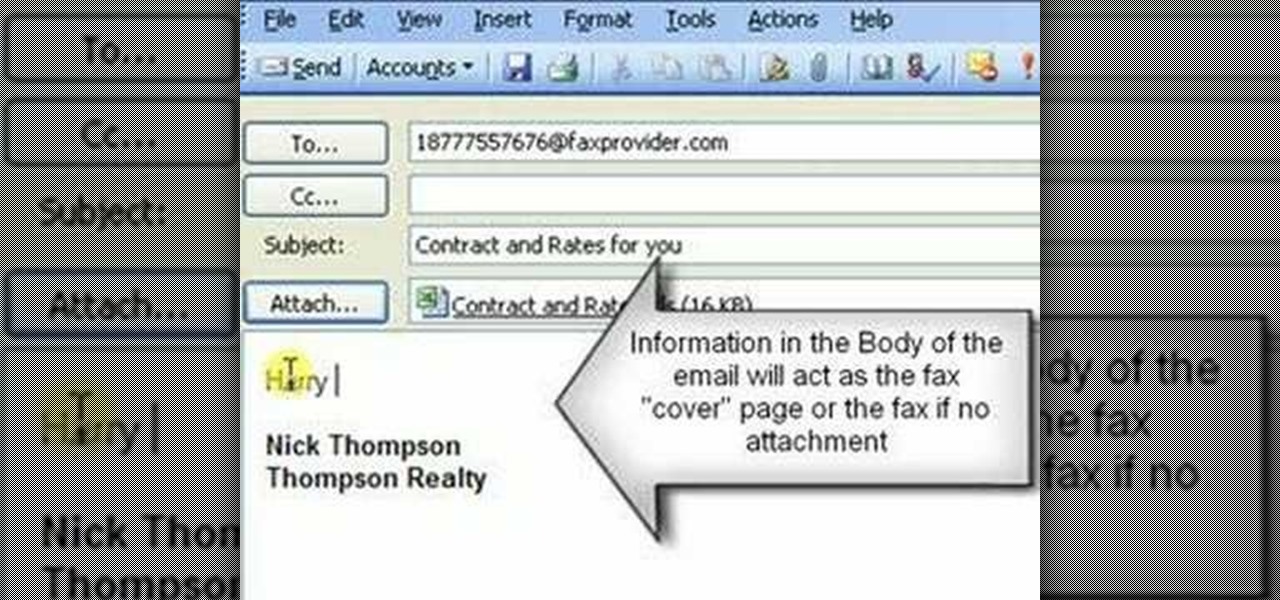
How To: Send a fax through your email
Check out this video tutorial on how to send a fax with email using Internet Fax. You'll need an Internet fax provider, and a phone number, so don't think it's easy as one, two, three.


Check out this video tutorial on how to send a fax with email using Internet Fax. You'll need an Internet fax provider, and a phone number, so don't think it's easy as one, two, three.

A tutorial on how to "break in" to your Windows machine after you have lost the password. This works in Windows NT, 2000, and XP machines without an encrypted file system. I then show you how to wipe a hard disk to assure no one can gain access to your data once the drive is sold or discarded.

Make an Eddie Earthworm doll. Yes, you will need cloth and pins. A sewing machine is helpful. Part 1 of 3 - How to Make an Eddie Earthworm doll.

Watch this video from the Concrete Network for tips on using the Mongoose concrete cutting machine to cut intricate designs in concrete surfaces before coloring.

This video shows you how to adjust headlights. Unfortunately it uses a precision machine so you won't be able to do this at home.

The Patch Kit by Designs in Machine Embroidery makes it easy and profitable to embroider patches. Watch how simple it is to use this time and money saving product.

The Magna-Hoop Pro, the latest innovation from Designs in Machine Embroidery makes it easy to embroider an afghan.

This week on Threadheads, the ladies of Compai are helpin' us out with a very special viewer request, plus we hang out and take a look into their popular DIY book series 99 ways. So sit back, relax, grab your sewing machine and get comfy.

This video demonstrates how to work your hamstrings by doing leg curls. The video walks you through setting up the seated leg curler machine and performing the exercises correctly.

This video demonstrates how to use a leg press to work out your quads and glutes. The video walks you through setting up the machine to your body type and performing the exercises correctly to avoid injuries.

On Wednesday, as expected, Apple unveiled the next generation of iPhones, namely the iPhone XS and iPhone XS Max along with the more affordable iPhone XR, each equipped with a TrueDepth sensor.

While we've seen Snapchat apply sky segmentation to AR content, the makers of the Blue Sky Paint app have applied similar capabilities to create and share airborne art.
For many of us, getting to inbox zero is the highlight of our day. But if you used your email address to sign up for various sites and services, your inbox is probably cluttered with all sorts of spam, news letters, and unimportant emails. Thankfully, Gmail has a feature that can solve this by using machine learning.

A development duo has concocted an iPhone app that displays related tweets based on objects recognized by the device's camera.

Hello, everyone. Stealth is a large part of any successful hack; if we don't get noticed, we're much less likely to be caught. In these next few articles, we'll be building a shell based on keeping us hidden from a firewall. There are many ways to stay hidden from a firewall, but we'll only be incorporating a couple into our shell. This article will outline and explain these evasion concepts and techniques.

Do you remember my last article on how to hook any web browser with MITMf and BeEF? Well, we are using the tool once again, but this time for auto-backdooring....

Want to get even this Halloween? Want to scare somebody with nothing but a few lines of code? Here's how it can be done...
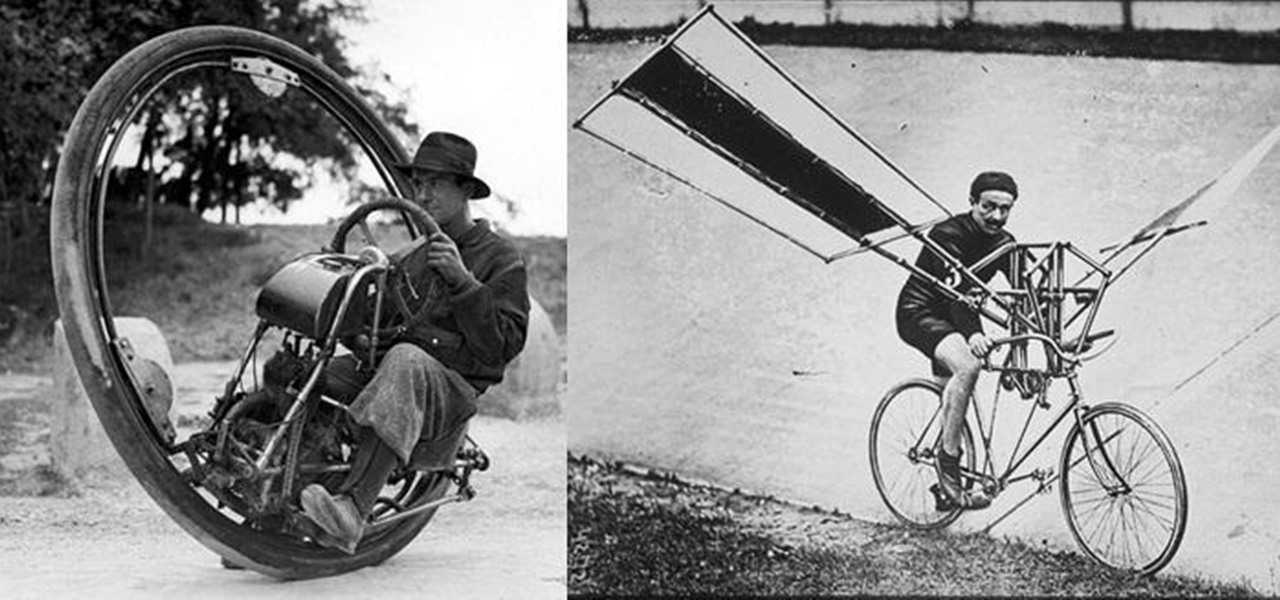
We don't spend much time thinking about bicycles today, do we? Sure, they're a "green" alternative to driving everywhere in cars, but the vast majority of America has dismissed them as simply being too much work, or more importantly—too slow. That wasn't always the case, though, I assure you!

First off, I would like to say two things. One, this is not for beginners; if you don't feel that you understand this how-to at all, do not try it. Second, never ever install random software or change settings if you do not trust the source.

You won't have to ask Santa for holiday-themed augmented reality experiences, because practically any social and shopping app that offers AR effects has them available now.

Before the internet, acquiring enough data to analyze was challenging. Now we have the opposite problem: a deluge of data makes trying to sort through it nearly impossible. That's where data science comes in.

The overarching and expanding field of data science and analysis has become virtually inseparable from areas such as programming and development.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

After the spectacular rise and fall (and rebirth) of Glass, Google is taking another run at augmented reality smartglasses.

The research team at Google has found yet another way for machine learning to simplify time-intensive tasks, and this one could eventually facilitate Star Wars-like holographic video.

In the previous article in this short series, we learned how to find our neighbor's name using publicly accessible information and how to monitor device activity on their home network. With this information at our disposal, it's time to get into installing and configuring the necessary tools to begin our attack on John Smith's computer.

With Virtual Network Computing, you don't need to carry a spare keyboard, mouse, or monitor to use your headless computer's full graphical user interface (GUI). Instead, you can connect remotely to it through any available computer or smartphone.

Argo AI is coming late to the party, but has begun testing a fleet of driverless cars in hopes of developing robo-taxi services to eventually compete against those that Waymo, Uber, Cruise Automation, and others plan to offer.

Nvidia's decades-long development of graphics processor units (GPU) for PCs has given it a major leg up in the driverless space.

Hyundai Motor Company says it will launch its driverless tech ahead of schedule, but the Korean carmaker will remain behind mainstream rivals, including General Motors (GM), Nissan, and Honda.

The world is full of vulnerable computers. As you learn how to interact with them, it will be both tempting and necessary to test out these newfound skills on a real target. To help you get to that goal, we have a deliberately vulnerable Raspberry Pi image designed for practicing and taking your hacking skills to the next level.

The rumors have been confirmed by Samsung themselves: Samsung has developed a virtual assistant of their own, named Bixby.

A bacterium which triggers respiratory disease has been detected in the water systems of two Pennsylvania nursing facilities.

This Is for the Script Kiddies: This tutorial is about a script written for the How to Conduct a Simple Man-in-the-Middle Attack written by the one and only OTW.

This tutorial is for those who've purchased an account with Private Internet Access to hide your VPN and would like to set it up in Kali. Please note, you can chose to run your PIA service from your Windows computer without configuring it in linux as long as you'll be using a NAT connection. Using a NAT connection will allow your Windows machine and Kali Virtual Machine to use the same IP address, hence if your IP is hidden on one, it will be hidden on the other.

Automated tattoos are now a reality, with 3D printers being hacked into tattoo machines. Multiple people have posted videos of their 3D printer that can "print" tattoos, with one of the more impressive ones shown in the two videos below.

If you're marginally inclined towards computers, you've probably been approached at some point by a family member who wants you to "fix" their system during a visit home. With the holidays coming up, these opportunities (or ambushes) are even more likely.

It's tough out there on the battlefield, especially when your stuck in the trenches and your comrades are dropping like flies. There's no hope. At least, until the next airsoft battle.

Samba can be configured to allow any user with write access the ability to create a link to the root filesystem. Once an attacker has this level of access, it's only a matter of time before the system gets owned. Although this configuration isn't that common in the wild, it does happen, and Metasploit has a module to easily exploit this security flaw.
Before smartglasses makers can dream of taking smartglasses to mainstream consumers, they must first determine the right mix of form, function, and price that will drive customers to buy into what they're hoping to sell.