It's no secret that Google is all about AI. In their eyes, machine learning is the future of software development, and you can see evidence of this all over the last couple Android updates. They've used it to power all sorts of features in their Pixel phones, and they've even donated some of their AI smarts to AOSP for all Android manufacturers to share. But it looks like Samsung isn't exactly on board.

Every step in the evolution of computing brings an in-kind leap forward in user input technology. The personal computer had the mouse, touchscreens made smartphones mainstream consumer devices, and AR headsets like the HoloLens and the Magic Leap One have leveraged gesture recognition.

Web applications are becoming more and more popular, replacing traditional desktop programs at an accelerated rate. With all these new apps out on the web comes various security implications associated with being connected to the internet where anyone can poke and prod at them. One of the simplest, yet the most prevalent types of security flaws found in modern web apps are SQL injections.
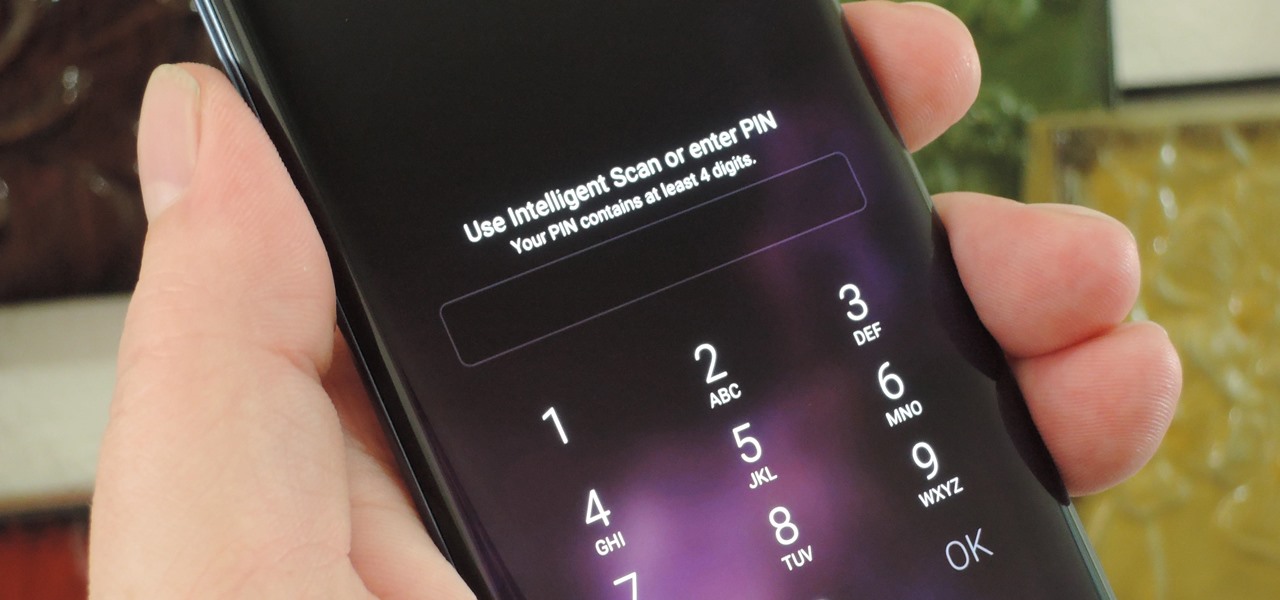
The Galaxy S9 is full of minor improvements and revisions that come together to make it a worthy upgrade over the Galaxy S8. One such improvement is facial recognition, which Samsung has fortified with machine learning and the inclusion of another sensor. The result of these efforts is called Intelligent Scan.

Google's new AI-powered camera, Google Clips, seems to be targeted at parents of young children in its current form, but the idea itself has unique potential. Just set it up somewhere, then you'll never miss a moment trying to capture the moment — you'll have a robot photographer taking care of that stuff for you.

Tesla hopes high-level personnel changes will help it gain an edge in neural network knowhow for its models' self-drive features, following the replacement of its Autopilot chief and the appointment of a recent Stanford grad to head its AI and Autopilot vision research.

SSH local forwarding is a must for covering your tracks and getting out there to do your work. Also called SSH tunneling, this process will put one or more steps between your machine and the machine you're working on, for security and other purposes. It can be a bit daunting for newbies to get down, and that's where Punchabunch comes in.

The largest and arguably most widely known event of its type, especially in the US, the Sundance Film Festival is an annual celebration of independent film—ones made outside the Hollywood system. This year, a new type of experience appeared at the Sundance Film Festival in an installation called "The Journey to the Center of the Natural Machine." This mixed reality presentation offered the user the newest type of storytelling in a long and important line—continuation of the species kind of im...

Welcome back, my budding hackers! Metasploit, one of my favorite hacking/pentesting tools, has so many capabilities that even after my many tutorials on it, I have only scratched the surface of it capabilities. For instance, it can be used with Nexpose for vulnerability scanning, with Nmap for port scanning, and with its numerous auxiliary modules, nearly unlimited other hacking related capabilities.

Welcome back to a tutorial on malware. We'll be discovering a method to beef up our little trooper. Without further ado, let's jump right in!

As many of you know, processor's clock frequency improvement got stuck in about 2003, causing the origin of multicore CPU (and other technologies). In this article I'll introduce you on how to run code simultaneously in various processors (I suppose that all of you have a multicore CPU). When you write code without any parallel directive, it only executes in one CPU at the same time (see it below). OpenMP make simple to work with various cores (if not with all of them) , without so much heada...

Whether it's the start, middle, or end of summer, it's prime-time grilling season. If you find yourself without a grill, however, it may seem as if half your summer plans of swimming by the pool while stuffing hot dogs in your face could be ruined.

Welcome back, my fledgling hackers! Sometimes, for a variety of reasons, we can only get a command shell on our target system. For instance, with Metasploit, it's not always possible to get the all powerful Meterpreter on our target system. In other cases, we may be able to connect to a command shell via Netcat or Cryptcat.

Welcome back, my novice hackers! New hackers often ask me the same question: "What is the easiest platform to hack?" My response is always the same—it is not a platform, but rather a particular piece of software that is easiest to hack, which is on nearly every client-side system. That software is Adobe Flash Player.

Privilege escalation is the technique used to exploit certain flaws to obtain elevated permissions relative to the current user. There are a vast number of methods out there to go from user to root on Linux, and keeping track of them all can be difficult. This is where automation comes into play, and a privilege escalation script called Linux Smart Enumeration is one to take advantage of.

The transcribing app can be an invaluable tool, especially if you're a student or are in a profession that relies on audio journals or interviews. These apps can convert important recordings like lectures and meetings into text for you to carefully read through to better comprehend.

Kali Linux is established as the go-to operating system for penetration testing, but in its default configuration, it's less than ideal for regular desktop use. While in many scenarios, a live boot or virtual environment can resolve these issues, in some situations, a full installation is better. A few simple changes can be made to a Kali Linux desktop to make it safer to use in this environment.

In this tutorial, we learn how to change a 20 inch tire. First, you will need to remove the valve core with a removal tool. Then, rotate the rim until the beat is separated. From here, secure the rim on a machine so it can be unmounted from the tire. After the tire has come off from the wheel, repeat this on all of the different tires. When finished, use the same tool to put the new tire back on. Then, you will need to inflate the new tire that you just placed on. Finish this off by putting b...

In this video we learn how to make a fun party dress with oversized bow. First, lay the fabric flat down on the ground and cut it in half. After this, measure your bust, waist, and hips and mark it on the fabric. After you have all of the pieces of fabric cut out that you need for the dress, put it all together. Use a sewing machine to sew the different pieces together. Then, grab the extra piece of fabric you have from the scrap pile. Use this to make the large bow and sew it onto the dress ...

No more do you have to buy additional equipment just to send a quick fax out. And no more going to the local copy store to pay for faxes. Windows 7 has a great feature built right in called Windows Fax and Scan. See how it works.

In this tutorial, we learn how to install a foot throttle on your lawn tractor. First, weld the petal onto the base and create your own holder for the rod so it stays in position. You will have to bolt it down so it stays in place and doesn't move. On the other side, put a holder on it so the rod stays in place and doesn't move. There should be a bolt on it so it doesn't move and a clamp that is welded onto the end of it. The, string a thin metal wire to connect onto the end and bolt it onto ...

We enjoy the fuzzy wool yarns at craft stores as much as any other knitter, but did you know that yarn doesn't have to be made from wool or any of the typical yarn fibers? In fact, you can make your own yarn at home. Don't worry, we're not going to put you in front of a weaving machine.

In this video, we learn how to upload Wordpress files using Filezilla. Before you get started, you will need to know the host, username, and password for your domain name. After this, click the quick connect button to connect to your server. The left hand side will show the local files on your server. Look in the root directory of your server and right click, then choose "create directory". Now, click on the plus sign to see a blog sub directory. Next, find where you downloaded Wordpress onto...

Skinny jeans are by and large the most popular cut of jeans in the fashion world right now, but purchasing a solid pair (from JBrand or William Rast) could set you back upwards of $300. And really, who wants to drop $300 for a few strips of denim that happen to have a name brand label sewn on the butt?

T-shirt rugs and placements exactly like the one presented in this tutorial sell for upwards of $150 at home decorating stores, so why not save money and reduce your consumption by simply repurposing old T-shirts yourself?

In this video, we learn how to froth milk using a steam wand on a traditional espresso machine. First you will foam your milk then you will mix the milk. First you will pour your milk into a container and place it inside of your steamer and turn it on full power. The milk will start to foam and you will see bubbles rising on the top. Keep this going for about 30 seconds then tap down your milk two times. When you look at the milk, it will be a rich and creamy texture. You can add this to your...

In this how to video, you will learn how to build up your arm strength for pitching. This involves using exercises that give you more focus on the muscles you will use for throwing. A high cable curl and crunch is a useful exercise for doing this. It involves gripping the rope on a weight machine and combining two different exercises together as one. You first start out with a curl, and then move on to a crunch. Repeat this for as many times as necessary. This will help you get a little extra...

This video explains how to make an inexpensive compost roller. The video begins with a composed pile shown covered with a tarp to keep rain away from. The materials needed for this project consists of 3" barrel nuts(2), 3" hinges(3) and machine screws(3pk) from a local Wall-Mart. The tools needed for this project consist of an electric drill with drill bit, screw driver, wrench, jig saw or key saw and a heavy duty utility knife. The compost roller made was just a simple plastic drum with a hi...

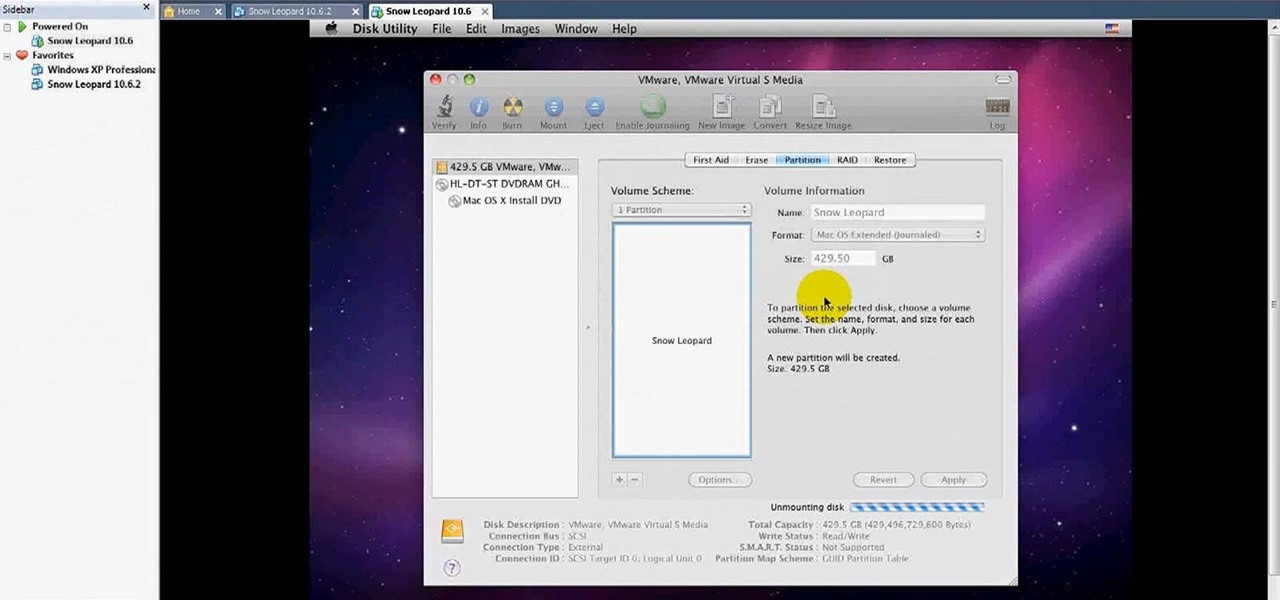
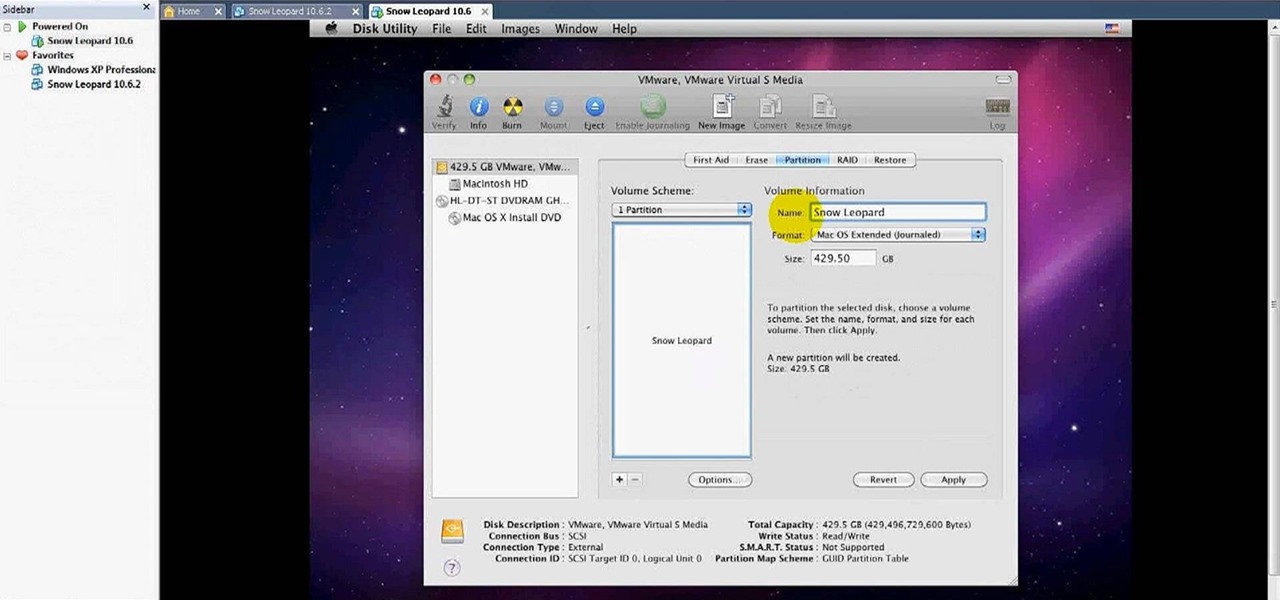
In this video tutorial, viewers learn how to install Mac OS X Snow Leopard in Windows PC using VMware Workstation as virtual machine. Begin by downloading the program from the link provided in the video description. ISO image is made especially for Windows PC users. Mac users can download the DMG file from there too. This video is a complete tutorial for installing Snow Leopard in Windows 7, XP, or Vista.

In this video tutorial, viewers learn how to install Mac OS X Snow Leopard in Windows PC using VMware Workstation as virtual machine. Begin by downloading the program from the link provided in the video description. ISO image is made especially for Windows PC users. Mac users can download the DMG file from there too. This is a full video guide on how to install Snow Leopard in Windows 7, XP, Vista using VMware Workstation and download all the software (VMware workstation, Mac OS X Snow Leopar...

In this tutorial you are inside a music store. From the beginning you are told stringing a Nylon string guitar is different than other guitars. You start by removing the old string from the machine head. You thread the new string through the head towards you. You will need to loop two times over and under and hold both ends of the string in place. As soon as the string is tight you can bring the end that is in the back over and through the main part of the string. Once the new string is in pl...

In this video tutorial, you'll learn how to change a damaged belt or brushbar on the Vax V-026 Rapide Deluxe carpet washer.

In this video tutorial, you'll learn how to change a damaged belt/brushbar on the V-006 Turboforce vacuum cleaner

This how to video is a good general reference for anyone making their own pants, trousers, or jeans; basically any article of clothing with a fly front. The example uses a Suitability pants pattern, and can also be used to substitute a button fly. Watch and learn how to sew on a zipper to a pair of pants or trousers using a sewing machine.

This tutorial goes over how to edit the text document that controls the hot key (shortcut key) commands. It doesn't go into the advanced commands or even begin to describe the various commands that you can invoke by changing the text document, but most of the users who will be editing this are ADVANCED USERS. NEVER. NEVER change the shortcut settings on a machine that is not yours and ALWAYS. ALWAYS make a backup copy of the document before you start to work on it.

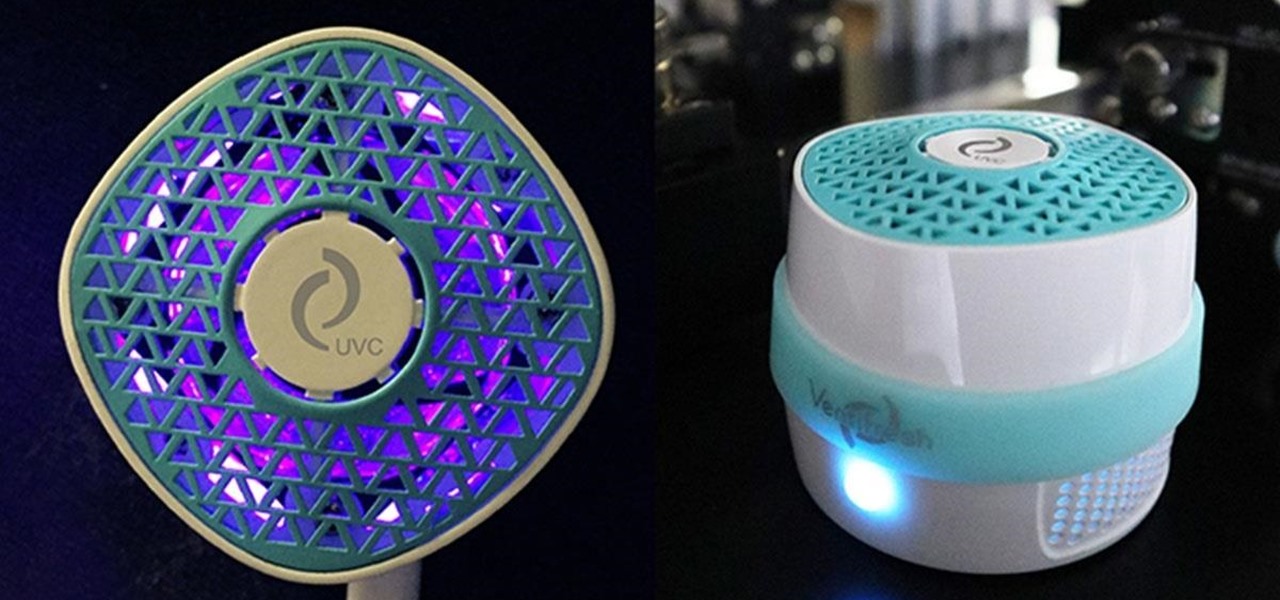
Having the right air quality can turn a room into an atmosphere. With a humidifier, you can see your skin dewy and your sinuses clear. Proper temperature control will keep you comfortable and content, and the right air purifier will give you clean air and peace of mind. If you're in the market for a humidifier, an air conditioner, a heater, or an air purifier but just need to find the perfect one to match your needs and your budget, then check out some of these great deals.

Do you believe you just don't have an intuitive sense of math? Sadly, this is the case for many people. The reality is that math is learned with practice. No one is born with a math gene making them more intuitive than others.

Choosing which programming language to learn next can be a truly daunting task. That's the case regardless of whether you're a Null Byter just beginning a career in development and cybersecurity or you're a seasoned ethical hacking and penetration tester with years of extensive coding experience under your belt. On that note, we recommend Python for anyone who hasn't mastered it yet.

A lot of time can be wasted performing trivial tasks over and over again, and it's especially true when it comes to hacking and penetration testing. Trying different shells to own a target, and testing out privilege escalation commands afterward, can eat up a lot of time. Fortunately, there is a tool called One-Lin3r that can quickly generate shells, privesc commands, and more.

UnrealIRCd is an open-source IRC server that has been around since 1999 and is perhaps the most widely used one today. Version 3.2.8.1 was vulnerable to remote code execution due to a backdoor in the software. Today, we will be exploiting the vulnerability with Metasploit, examining the underlying code to understand it, and creating our own version of the exploit in Python.