
How To: Phreak (Basics)
Get some tinfoil hats and make a time machine because we are about to go back to the 90s and learn about some phreaking.


Get some tinfoil hats and make a time machine because we are about to go back to the 90s and learn about some phreaking.

Getting a good night's sleep is critical to maintain good health, a better mood, and clear your mind for whatever the day has planned for you. But in practice, whether you're tired or not, the world has a way of preventing it, either through your partner's snoring, your neighbor's music, or the road construction going on right by your bedroom window. It can get rough.

OnePlus changed the way we think about high-end phones. Their "Never Settle" motto led me to ditch my high-cost smartphone for their flagship One, which not only packs some pretty impressive hardware, but won't break the bank. Now that OnePlus has made a name for themselves with the One, they're trying their hands at ROMs, too.

Most diehard Mac users have used TinkerTool at some time or another, and if you haven't, it's time to start. Whether it's to change your system's font or to disable UI animations, it seems like anything you could ever think about tweaking in Mac OS X is doable through TinkerTool. And now, developer Marcel Bresink has updated his app to work with Yosemite, so let's see what it can do now.
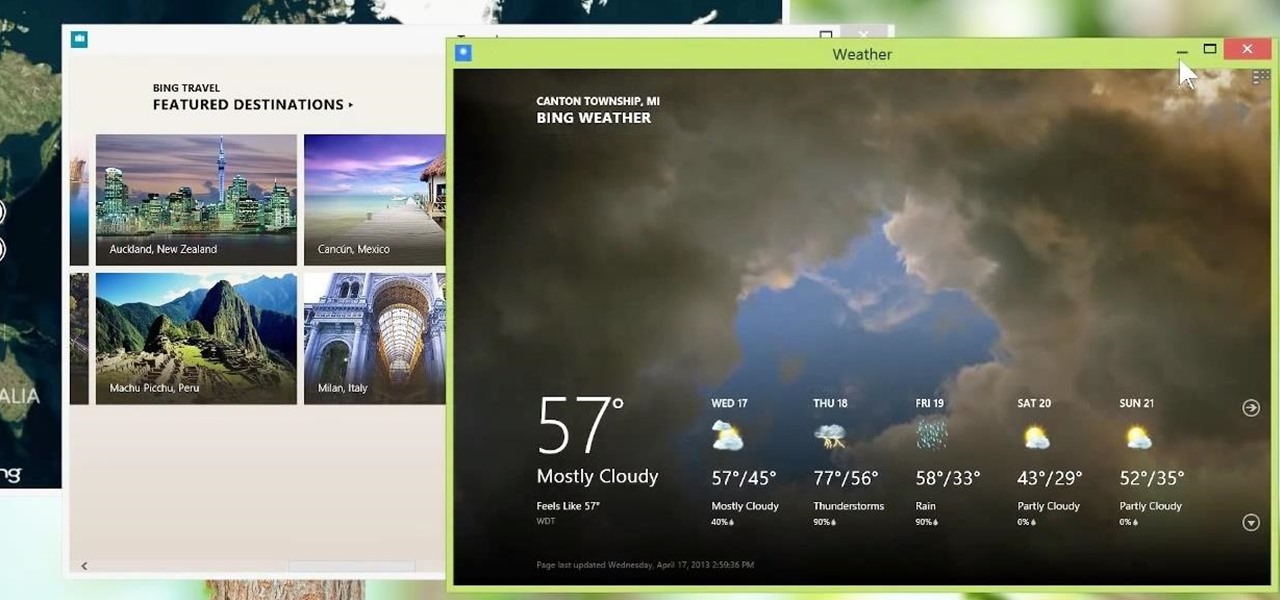
Metro apps are pretty nice, but they absolutely suck on a Windows desktop with a mouse and keyboard. That's to be expected though, since Metro (also known as Modern UI or Microsoft design language) was created mainly with touch input in mind for Surface Pros and Windows Phones.

Video games have come a long way over the last 30 years. In the late-'80s, Atari, Nintendo, and Sega were taking gaming from arcades to living rooms. Back in 1994, the Super Nintendo and Sega Genesis were in bedrooms everywhere, and over the next couple of years, were slowly being replaced by Sega Saturn, Nintendo 64, and the first ever Sony PlayStation.
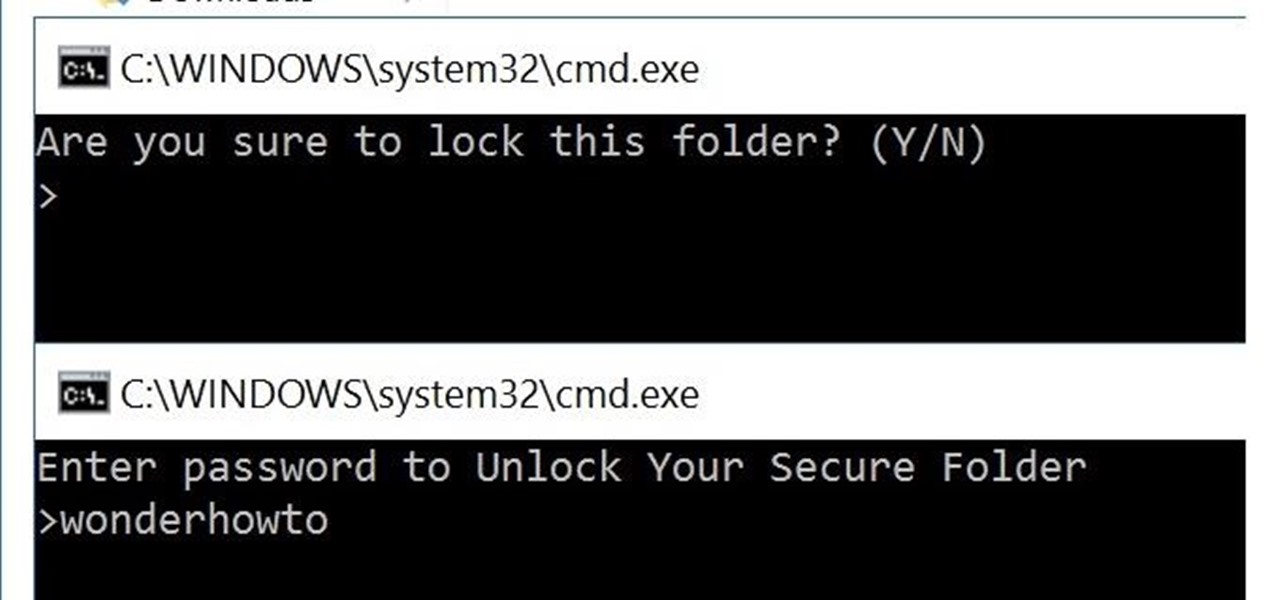
You can easily lock any folder on your Windows computer with a simple Notepad hack. By creating a batch file, you can hide a folder and require a password be entered before it becomes visible and accessible. This is a great tool for locking sensitive information, like pictures, financial statements, and a lot more.

One good thing about having friends who are constantly on their phones and tablets is it's easy to figure out what to get them for Christmas. Everyone hates getting gifts that just sit around, so it's always nice to get something that improves an item you use on a daily basis.

The video for Robin Thicke's "Blurred Lines" got its fair share of attention due to the three topless models who star in it. In the second version, they're covered up, but just barely. Both the song lyrics and the lack of clothing sparked plenty of debate, controversy and even parodies.

We've all had to write an essay or research paper at some point, and undoubtedly the hardest part about it is always the citation, right? If you ask me, it's a huge pain in the arse. Even more so if you're gathering your facts from a huge variety of sources.

The gold standard of great foods on a stick is reserved for honey battered corn dogs and shish kabob (which is surprisingly spelled just like it sounds). But when I saw this absolutely amazing concoction of breakfast food combined with the queen of meats, I fell in love. Now, if you are looking at this picture and still don't know what it is, you are definitely not a chicken and waffles fan, otherwise you would have figured it out right away. I mean, what else goes well with syrup-drenched wa...

Frankly, I never cared about the care labels on my clothing. They supposedly held some secret key to keeping clothes clean and bright, but who wants to look at little icons and a bunch of fine print for every single garment they wash?

Glitches can be extremely annoying when playing some of your favorite games, but sometimes, only sometimes, there are glitches in the game that give you an unprecedented advantage against the computer or other players online.

It's really no wonder why Christmas is the most popular and widely celebrated holiday of the year. Your whole family gets a chance to spend some much needed quality time together—and not just gorging on food like at Thanksgiving. But in all seriousness, that's not the reason at all... we're talking Christmas presents here.

If you've ever logged on to the popular music application Pandora, your password is saved onto that computer in the local storage...for good.

With the release of Windows 8 right around the corner, if you plan on buying it (or just want to see what it's all about), it's a good idea to take advantage of the free trial before you shell out any money. If you're an Apple user who doesn't have a deep-seated disdain for Microsoft products, this tutorial will show you how to install the Windows 8 preview to try it out on your MacBook. First things first, you'll want to download the Release Preview on Microsoft's website (make sure to save ...

Hello! Today I would like to write a few lines about making a simple bed for your pet, for example, your cat or a bunny, using your old fabric. All interested can stir up a bit in the closet. I am sure there's an old towel or a blanket just waiting to be reused. Or some old clothes, made out of fleece, etc...

Sometimes you just want to grill. It doesn't matter where you are, what you have, or whom you're with—you just want a delicious burger and you don't care what it takes.

Mountain Lion (OS X 10.8) is out today, available in the Mac App Store for just $20. Unfortunately, installing Mountain Lion requires that you already have a Mac running Snow Leopard (OS X 10.6) or Lion (OS X 10.7). If you're currently running a Leopard system, you're out of luck, and need to pay $29 to upgrade to Snow Leopard, and then an additional $20 to upgrade again to Mountain Lion. That sounds like way to much trouble to me. But why exactly is Leopard incompatible? Turns out it's not—m...

If you're an AirPods user, things are a lot better with iOS 18 and iPadOS 18. If you're not, it may finally be time to grab yourself a set of AirPods, especially if you're into privacy and gaming.
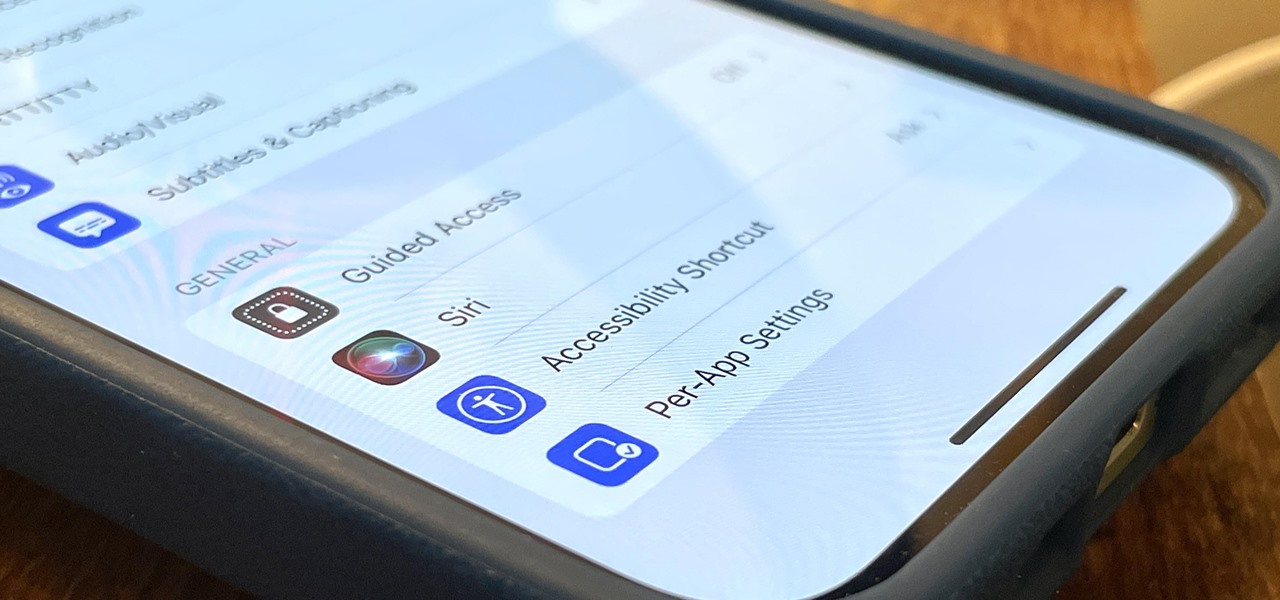
I use the Accessibility Shortcut on my iPhone practically every day, whether it's to dim the screen below the standard threshold, keep my child confined to a specific app, or open up the simulated magnifying glass. But with iOS 15, there are at least three more things I can use it for, and one of them is really good.
When compared to last year's model, the Pixel 4a has upgrades that go beyond the spec sheet. But since it's one generation old, 2019's Pixel 3a can be had for one hell of a discount right now, and it's still got two full years of software updates coming its way. So which one really is the better buy?

3D printers allow hackers and makers alike to create something from nothing. They're an incredible technology that lets you build protective cases and covers for gear such as a wardriving phone and Raspberry Pi-Hole. 3D printers can even help you out in a bind when something breaks, and it's impossible to get the part, since you can just print one out yourself.

One of the most exciting things as an ethical hacker, in my opinion, is catching a reverse shell. But often, these shells are limited, lacking the full power and functionality of a proper terminal. Certain things don't work in these environments, and they can be troublesome to work with. Luckily, with a few commands, we can upgrade to a fully interactive shell with all the bells and whistles.

While our smartphones are many things, one of their primary functions is to make calls. Many of us try to avoid ever having to make calls, but there are situations when it's a must, such as wishing your grandma happy Birthday or calling 911 — and in those times you want stellar call quality.

Hackers are always seeking zero-day exploits that can successfully bypass Windows 10's security features. There has been extensive research into creating undetectable malware and entire GitHub projects dedicated to automating the creation of undetectable payloads such as WinPayloads, Veil v3, and TheFatRat.

After a long hiatus, we shall once again emerge from the shadowy depths of the internet to build an exploit. This time, we'll be looking at how to defeat a non-executable stack by using the ret2libc technique — a lean, mean, and brilliant way of exploiting a stack overflow vulnerability.

Many lazy cooks skip rinsing off their grains before they cook 'em, but that's a big mistake for a few reasons. Some grains have coatings on them that need to be rinsed off to cook properly and taste good.

Many of you are ready to capture the litany of 4th of July fireworks that will litter the night sky, but if you're using a phone to capture the burst of fire in midair, it can get a little tricky. Don't worry, though — you'll be fine if you use these tips.

In less than a month, WWDC, Apple's Worldwide Developers Conference, will reveal the company's plans for the upcoming iOS 18 and iPadOS 18 software updates. But we already know what accessibility features will be hitting iPhones and iPads later this year, and many of them will be helpful to everyone, not just users with accessibility issues.

As we've seen with other tools and utilities, administrators typically use certain things to do their job more efficiently, and those things are often abused by attackers for exploitation. After all, hacking is just the process of getting a computer to do things in unexpected ways. Today, we will be covering various methods to perform banner grabbing to learn more about the target system.

Microsoft's built-in antimalware solution does its best to prevent common attacks. Unfortunately for Windows 10 users, evading detection requires almost no effort at all. An attacker armed with this knowledge will easily bypass security software using any number of tools.

The art of fuzzing is a vital skill for any penetration tester or hacker to possess. The faster you fuzz, and the more efficiently you are at doing it, the closer you come to achieving your goal, whether that means finding a valid bug or discovering an initial attack vector. A tool called ffuf comes in handy to help speed things along and fuzz for parameters, directors, and more.

PowerShell is an essential component of any Windows environment and can be a powerful tool in the hands of a hacker. During post-exploitation, PowerShell scripts can make privilege escalation and pivoting a breeze, but its execution policy can put a damper on even the best-laid plans. There are a variety of methods, however, that can be used to bypass PowerShell execution policy.
It feels like every few months, some new feature is discovered in the Pixel's Camera app. By taking advantage of machine learning and the high-quality camera, Google continues to add hidden functions that improve your life even if they're a little niche.

Network enumeration is one of the essential phases of an attack, but it can take a lot of time and effort depending on the size. We've all been spoiled by Nmap and similar tools, and while there is a learning curve involved, they are extremely useful. But there's also GoScan, a tool that builds upon Nmap, offering an automated way to enumerate networks and services quickly.

The internet has undoubtedly changed the way we work and communicate. With technological advances, more and more people can collaborate on the web from anywhere in the world. But this remote-friendly environment inherently brings security risks, and hackers are always finding ways to exploit systems for other uses.
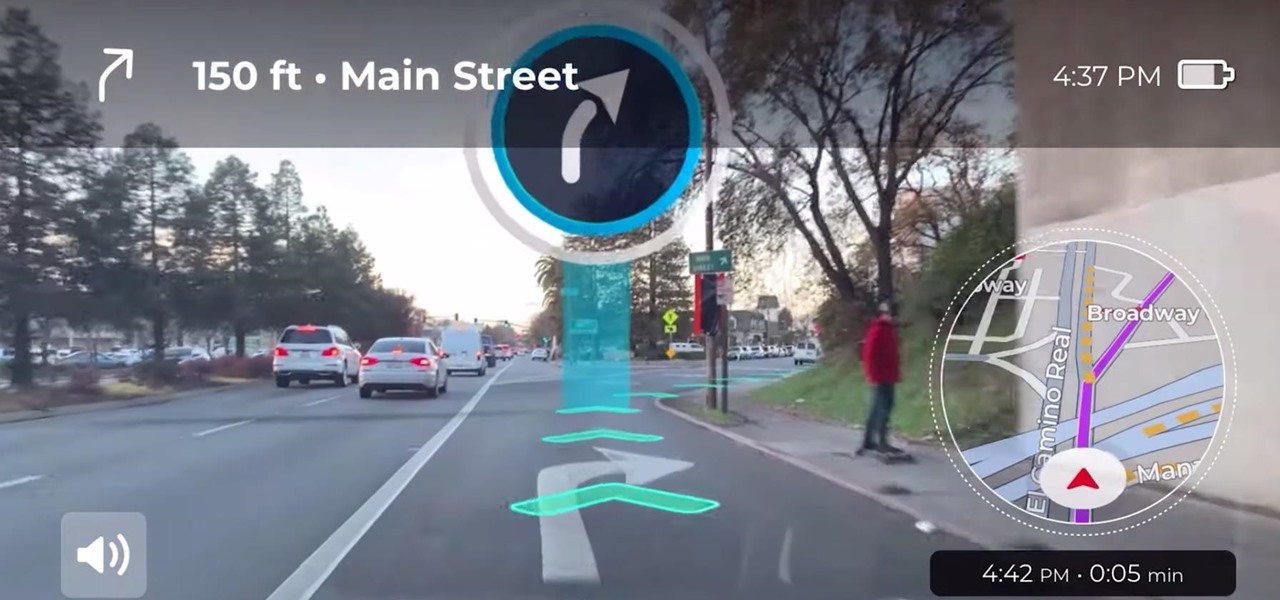
Google pushed a new kind of augmented reality walking navigation to the mainstream last year, and now startup Phiar is hoping users will use its AR app in the same way for driving navigation.
When Google introduced the Call Screen feature with the Pixel 3, I had never been more excited to get a Pixel device. This AI feature provided real protection against rising spam and robocalls, which billions of people deal with each year. After a recent update to the feature, you can reduce robocalls and other spam calls to nearly zero.
After opening up its Spark AR platform on Instagram for all creators, Facebook is already expanding the platform's capabilities on its Snapchat killer.