This is a tool I wouldn't want to do without in my kitchen. It's full name is the Jaccard Super Tendermatic Meat Tenderizer but if you refer to the "Jaccard", most food folks will know what you are talking about. Jaccard makes lots of food prep products but this is probably their most well known. There are other tenderizers on the market, but this one is better made and uses higher quality materials than most. High quality stainless steel blades in a sturdy plastic case that is machine washab...

This German video is amazing. A joyously analog interpretation and deconstruction of the digital gaming experience. Malte Jehmlich is as primitive and inspiring as the the Vanuatu natives who devoted themselves to cargo worship after World War II!

Here at WonderHowTo, we appreciate the fine art of photography (including its extensively vast bag of mind boggling tricks). We also enjoy playing with fire. Sorry, most of us are little boys at heart, and we can't get enough tutorials that fall within the playing-with-matches realm.

L4D2: The Port Finale The Third Chapter in The Passing is the Port Finale. It's similar to the Dead Center finale, where you have to gather gas cans spread throughout the map and fuel the generator to lower the bridge.

Microcontrollers are great. You can do anything from water your garden to catch wildlife trash diggers in the act—and on the cheap. I prefer to use the Arduino microcontroller because of the large and helpful community built around the website. Though it is my favorite, there are some drawbacks to using an Arduino board in every project. It gets expensive, the board can take up too much space, and the rat's nest of breadboard wires are a pain to repair.

Welcome to Minecraft World! Check out our tutorials, post to the community corkboard, and come play on our free server!

If you are a pet owner, going on vacation can be stressful. Usually, you need a friend or neighbor to come over everyday and feed your pets. However, by enslaving robots you can keep your pet happy and enjoy a stress-free holiday.

Dreams are like an internal human holodeck. Inside your mind, anything is possible, from your grandest wishes to your worst nightmares. This is all well and good, but what if you could control your dreams and become the omniscient god of a handpicked reality whenever you go to sleep? Inception took this idea to the logical extreme by invading other people's dreams.

Some of you might be using Tor to host hidden services, and some of you might not even know what hidden services are. If the latter's you, do not miss this article. Why? Because you can host your websites and services on the I2P darknet. It's safe and secure—it's anonymous.

This morning, I received a message from a friend who was reading a hack log, and she had some questions about the commands used. This got me thinking, as Linux has a ton of commands and some can be archaic, yet useful. We are going to go over everything you need to know to read a hack log and hopefully implant the steps in your head for future use.

TOP MOVIES 2011 The Artist (2011)

Oh yeah, this is a big topic, at-least for me. All the frequent flyers will/should be interested in this topic. I'm sure all of you have heard at-least something about the TSA, and most of it should have been bad. Complaints, lawsuits and general disgust surround this organization. Is there a reason, or are the 'extremist liberals' at it again? Let's find out!

Pull up outside any construction site and you'll see tools scattered about—hammers, jigsaws, nail guns, hydraulic pipe benders—these are the tools of the trade. You would be hard-pressed to build a home or office building with just your hands! On that same page, security professionals also have their own go-to tools that they use on the job site, only their job site is your server.

We're officially seeking Null Byters on a weekly basis who are willing to take the time to educate the community. Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (IF up to par, of course). There is no need to be intimidated if you fear you lack the writing skills. I will edit your drafts if necessary and get them looking top-notch! You can write tutorials on any skill level, and about anything you feel like sharing that...

We're officially seeking Null Byters on a weekly basis who are willing to take the time to educate the community. Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (IF up to par, of course). There is no need to be intimidated if you fear you lack the writing skills. I will edit your drafts if necessary and get them looking top-notch! You can write tutorials of any skill level, about anything you feel like sharing that is ...

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server.

Overclocking is quite an awesome thing. When computer components are designed, they are made to run at a certain speed, otherwise known as their clock and bus speeds. These limits are not actually limits. You can overclock components, which essentially makes them go faster than their set limitations. This can save you a lot of cash when newer components come out and you don't have enough money to upgrade. However, when you overclock components, you must be careful and make sure that the machi...

WonderHowTo is made up niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

Are you finding that the Google+ features you've been waiting for are still not rolling out quickly enough for you? Although we've provided many solutions to Google+ issues with different Chrome extensions, it still seems like it's not enough. Now that we've been using Google+ for almost two months, our priorities have changed, and we're finding that we want and need different extensions to make Google+ work better. From filtering to circles, these Google+ Chrome extensions will solve many of...

Deep in their heart of hearts, most Americans dream of having their car festooned with missile launchers and machine guns. Anyone who cuts them off or looks at them funny in traffic could be dispensed with quick and extreme justice, leaving a real-life James Bond and his passengers free to pursue their American dreams faster than everyone else. Racing games and shooting games are among the two most popular types of video games. So why aren't there more games where one can race cars and shoot ...

There's no doubt about it—the most elite military force in the United States is hands down, the Navy SEALs. They can operate at sea, in the air and on land, and their ability to conduct missions underwater separates them from most other military units in the world. They've fought in World War II, Vietnam, Granada, Afghanistan and Iraq, but have gained some serious hype in recent years thanks to SEAL Team Six, aka DEVGRU, aka NSWDG, who saved Captain Richard Phillips from Somali Pirates in 200...

Dropbox continues to make headlines with their recent programming blunder which left the accounts of its 25 million customers wide open during a four-hour time span. During the duration, anyone in the world could access any Dropbox profile by typing in any password. And seeing as this wasn't the first security failure, everyone, including the most loyal users are considering dropping the Dropbox.

A woman from space that who has been dead hundreds of years has been resurrected on the internet and you're the IT assigned to fight the viruses attacking her. Child of Eden is a mesmerizing musical game, with fluid animations, great game play, and lots of replay ability.

I love my laptop. It goes wherever I go. Unfortunately, that means that it also gets pretty grubby after a while. The screen gets dusty. The frame gets smudgy. The spaces between the keys fill up with crumbs of questionable origins. And my desktop? That thing is a dust bunny magnet.

In 2007, Nintendo introduced the world to motion control video games with the Wii. Microsoft and Sony built on Nintendo's phenomenal success and released their own motion control products for the XBox 360 and Playstation 3 late in 2010: the Kinect and the Move. The Move is basically an improved Wiimote that looks like a sci-fi Harry Potter wand, but the Kinect just might be the most important video game peripheral of all time.

Guiding internet users to useful content is one of the most lucrative businesses in the world. This process is called aggregation. Google and other search engines form the top of the food chain, aggregating all of the content on the web in response to queries. There are all sorts of other important aggregators though, and you probably use at least one every day: Fark and Reddit for web content, Rotten Tomatoes for movie reviews, and Metacritic for a variety of media, but most importantly, vid...

No time for elaborate practical jokes this April Fool's? Not a problem, it's 2011—meaning, apps can do just about anything these days. Measure beauty, check for STDs, even fix late night drunken social media stupidity. So why not pranks? Below, 10 digital solutions for your April Fool's Day wickedness.

In Google definitions a macro is defined as "a single computer instruction that results in a series of instructions in machine language". Basically a macro is a programming script that tells the computer what to do. You can tell a computer (via a macro) to move a mouse, click, type or do any task that a computer can do with automation. There are also many (primitive) computer viruses that are coded entirely in a macro script. There are many ways to create a macro script but I will only go ove...

It's really a shame that it is so hard for people to make money on the internet these days. The dot com bubble has receded and scams are plentiful on the web. There are, however, a couple of legitimate ways to make a few extra bucks online, Amazon Mechanical Turk, or MTurk for short, is one of them. The idea of MTurk is to hook up programmers with people that do tasks that computers can not, these tasks are called HITs (Human Intelligence Task). These tasks include article creation, creative ...

The whole world seems better when you’ve had a full night’s sleep, and if you don’t believe me, you’re JUST FRIGGIN’ WRONG. Studies show that getting enough sleep during nighttime hours can make you less irritable, help you lose weight, and reduce your risk of cancer and other totally bogus-time diseases.

Many folks seem to treat their computers as a sort of mysterious alien technology that only the shamans of the IT Department can comprehend. You might have gotten it into your head that you're just not good at computers and will never understand them. On the contrary, getting a basic grasp on all the amazing stuff inside your computer doesn't require you to be a technological genius. Most people will never have a need or desire to open up their computer and poke around. But it's your machine....

The days of trundling hoops, hopscotch and painted wooden rocking horses are long since past. The latest trend in toys? Biofeedback. Electroencephalography. A decade into the 21st century, the toy market is awash in products that incorporate functional neural sensors.

In Alan Wake, there are hidden messages hidden throughout the levels that are only visible with a flashlight. If you don't flash the light at a particular spot, you will not be able to see the message.

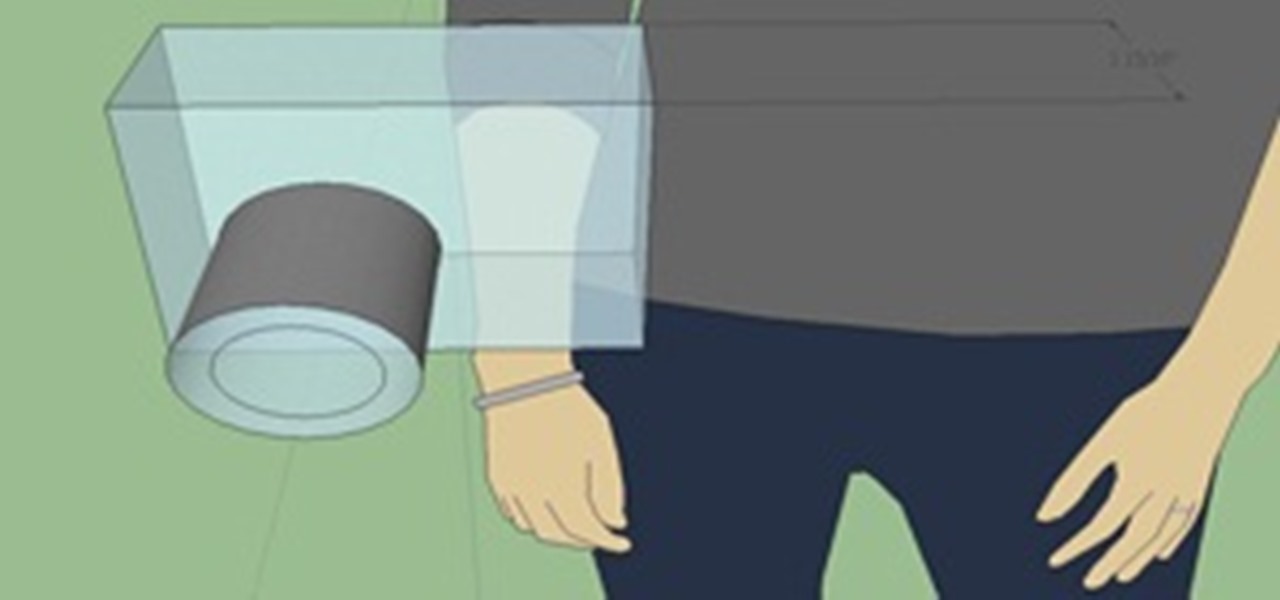
Creating any object you want is as simple as point and click if you have a 3D printer at home. If you don't have one handy, there are a few companies that offer printing services online. But to help services realize your design in extruded plastic, you have to make a 3D computer model for the printing machine. For beginners, the free Google SketchUp application is the best choice of software. Using only a few tool bar buttons and a scroll wheel computer mouse, you can model literally any obje...

WonderHowTo is a how-to website made up of niche communities called Worlds, with topics ranging from Minecraft to science experiments to Scrabble and everything in-between. Check in every Wednesday evening for a roundup of user-run activities and how-to projects from the most popular communities. Users can join and participate in any World they're interested in, as well as start their own community.

You're sitting in front of your grandmother's Windows XP machine that has the worst infection you've ever seen. Safe mode? No dice. Restore points? They're compromised. Even worse, all of the files are hidden and none of the executables will run! This leaves her computer in a bricked state. Without some serious CPR, it will be lost to you. Sure, you could just reinstall the system, but then you might lose all of that valuable data.

Big brother is watching when you're playing around on another system—and big brother is that system. Everything from operating systems to intrusion detection systems to database services are maintaining logs. Sometimes, these are error logs that can show attackers trying various SQL injection vectors over and over. This is especially so if they are using an automated framework like sqlmap that can spam a ton of requests in a short time. More often than not, the access logs are what most amate...

Injection is an attack vector that involves breaking out of a data context and switching into a programming context through the use of special characters. These characters are significant to the interpreter being used, but not needed for the general user input being asked for.

Introduction The 3 major anonymity networks on the Internet are Tor/Onionland, I2P and Freenet. If you feel confused on which one is the "best" one to use the answer is simple. Use all three!

If you're a frequenter of Null Byte, I bet you have at least some interest in information security. Furthermore, you have a hobby that if applied in certain ways, will get you arrested. I've received quite a few messages from the community here about federal cybercrime law and how it applies to them, so I decided to get together with my lawyer to come up with some answers.