For almost a decade, projector phones have tried to entice consumers with their convenience as media machines. While these devices are alluring, they've never really taken off with mainstream success. The latest effort, Moviphone, sounds tempting if you watch a lot of films and TV on your smartphone, but is it good enough to be your daily driver?

There's no doubt Kali has established itself as the most popular penetration distribution available. However, just because it's the fan favorite of beginners and security researchers doesn't make it right for everyone. Manjaro Linux is a beginner-friendly Arch-based distribution which can be easily weaponized with the Black Arch expansion, creating a friendlier first-time Arch experience.

The internet is constantly under siege by bots searching for vulnerabilities to attack and exploit. While conventional wisdom is to prevent these attacks, there are ways to deliberately lure hackers into a trap in order to spy on them, study their behavior, and capture samples of malware. In this tutorial, we'll be creating a Cowrie honeypot, an alluring target to attract and trap hackers.

Being able to write your own hacking tools is what separates the script kiddies from the legendary hackers. While this can take many forms, one of the most coveted skills in hacking is the ability to dig through the binary files of a program and identify vulnerabilities at the lowest level. This is referred to as binary exploitation, and today we're going to check out a tool known as Protostar.

Kali Linux is the obvious first choice of an operating system for most new hackers, coming bundled with a curated collection of tools organized into easy-to-navigate menus and a live boot option that is very newbie-friendly. But Kali isn't the only distribution targeted at pentesters, and many exciting alternatives may better fit your use-case. We've already covered BlackArch Linux, now it's time to talk about Parrot Security OS.

PowerShell Empire is a post-exploitation framework for computers and servers running Microsoft Windows, Windows Server operating systems, or both. In these tutorials, we will be exploring everything from how to install Powershell Empire to how to snoop around a target's computer without the antivirus software knowing about it. If we are lucky, we might even be able to obtain domain administrator credentials and own the whole network.

As was mentioned by the great OTW last week, TOR, aka The Onion Router, has had its integrity attacked by the NSA. In an attempt to reduce the anonymity granted by the service, the NSA has opened a great many nodes of their own. The purpose is presumably to trace the origin of a communication by compromising some entrance and exit nodes. Once both are compromised, it is much easier to correlate traffic with a particular individual.

Say whatever you want, but Steampunk is primarily a maker culture. Consider that Steampunk has existed since the 1960s and yet more or less languished in obscurity until approximately 2005, which is when it made the leap to costuming. That costuming was what provided the leap to the tangible, despite the fact that Steampunk art had also existed for years.

AppleScript is quite an easy scripting language to use. In this guide, I will be showing you several commands. Near the end, I will show how these can be used to create a fake virus that actually does no harm.

It's finally out. After months of testing, iOS 13 is available to install on your iPhone, which means over 200+ new features you can use right now. The update, released on Sept. 19, can be installed over the air or from a restore image using iTunes in macOS Mojave and older or Finder in macOS Catalina. Ditto for the 13.1 update issued on Sept. 24.

A hacker with privileged access to a Windows 10 computer can configure it to act as a web proxy, which allows the attacker to target devices and services on the network through the compromised computer. The probes and attacks appear to originate from the Windows 10 computer, making it difficult to detect the attacker's actual location.

Android's settings menu is actually pretty daunting. There are options for nearly everything, so in the sea of various menus and submenus, it's easy to overlook important privacy and security settings. On Google's Pixel phones in particular, there are 20 such settings that you should double check.

Whether it's for health reasons or just to look better, many of us want to get in shape. It's a long process that starts with nutrition, and dieting is never easy. Fortunately, there are some great food-tracking apps that will make it a lot easier to become a healthier version of yourself.

Hackers often rely on lazy system admins and unpatched vulnerabilities to get access to a host. Keeping intruders off of our machines requires us to update daily, only run the services we need, and read the code, among other things, but we can still make mistakes. Luckily for us, we can limit the damage caused by those mistakes by running SELinux.

In the previous article, we learned how to set up our VPS, configure our PHP server, and developed an in-depth understanding of how the payload works. With all that taken care of, we can get into disguising our payload to appear as an image and crafting the note in the greeting card being delivered to our intended target.

There's an iOS feature that benefits many users, but it's absolutely vital if you wear AirPods or other headphones models connected to your iPhone. A large number of iPhone users don't even know about it, especially since it's disabled by default and hidden deep in the system settings.

You've decided you want to lose weight or build lean muscle. That's great! Now grab your smartphone. It's a valuable asset that can help you achieve your physical fitness goals, whether to improve your health or enhance your appearance, and I'm going to show you how.

Sudo is a necessity on most Linux systems, most of which are probably being used as web servers. While the principle of least privilege is typically applied, sudo misconfigurations can easily lead to privilege escalation if not properly mediated. Which brings us to SUDO_KILLER, a tool used to identify sudo misconfigurations that can aid in privilege escalation.

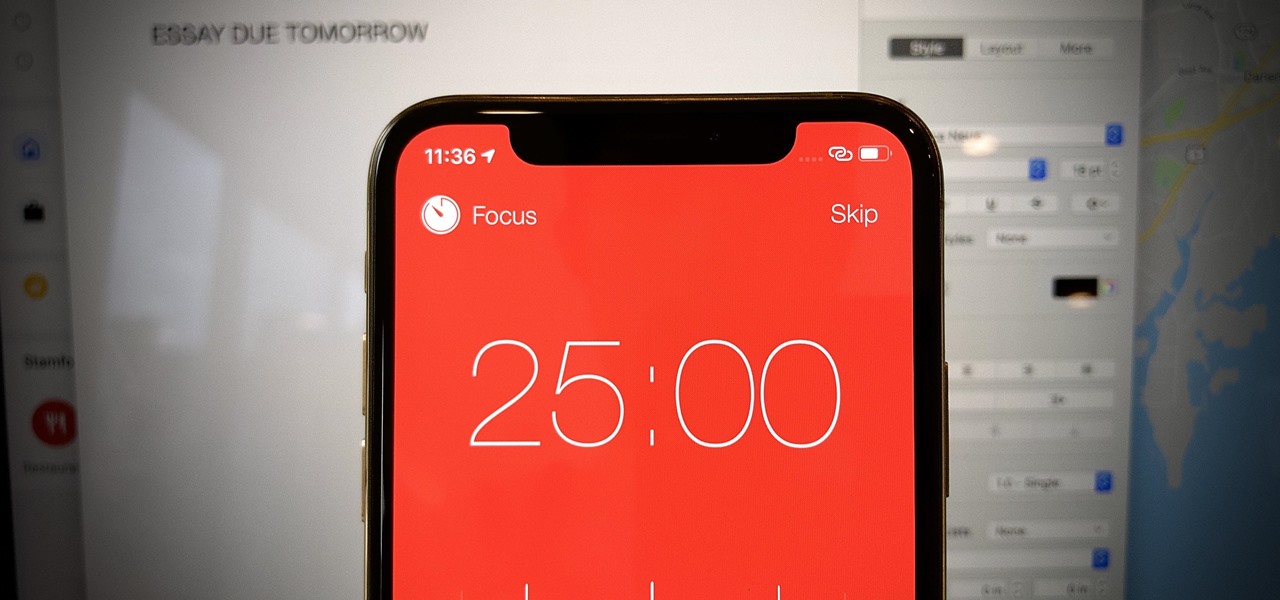
Procrastination is an ugly beast. At first, it seems so innocent to spend five minutes checking Reddit or Twitter. You'll get started on work right after. Next thing you know, it's 1 a.m. and that paper is due in seven hours. Before you start another YouTube video, know you don't have to be like Spongebob. You can be like me, taking control of your productivity with the right app.

Hackers are always seeking zero-day exploits that can successfully bypass Windows 10's security features. There has been extensive research into creating undetectable malware and entire GitHub projects dedicated to automating the creation of undetectable payloads such as WinPayloads, Veil v3, and TheFatRat.

Kali Linux has come a long way since its BackTrack days, and it's still widely considered the ultimate Linux distribution for penetration testing. The system has undergone quite the transformation since its old days and includes an updated look, improved performance, and some significant changes to how it's used.

Smartphones are now indispensable when traveling. Domestic and overseas travel alike require food, navigation, translation, and so much more to make work or vacation successful. Gone are the days of lugging multiple tourist books around with you everywhere you go — you need to let your smartphone handle the dirty work.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

Will the predicted apocalyptic date — December 21st, 2012 — really be the end of the world? In this ongoing five-part series, we examine what would happen if zombies, nuclear weapons, cyberwars, earthquakes, or aliens actually destroyed our planet — and how you might survive.

This Mig Welding Video Demo shows how simple and easy it is to use a MIG welding machine. Mig Welding Machines are use throughout the world. They are the suited for many welding applications. This video demonstration demonstrates Mig welding by welding two pieces of sheet metal together. Watch this video welding tutorial and learn how to fuse two pieces of sheet metal together with a Mig welder.

In this video tutorial, viewers learn how to refurnish hardwood floors. Using a drum or belt sander, begin by cutting 36 grit abrasive. Then remove all the old finish marks and scratches from the main body of the floor. Using an edge sander, do the same thing. Now vacuum the floor and then repeat the process once again with both sanding machines, except use 50 grit abrasive this time. For the third time, use 80 grit abrasive and 100 grit abrasive for the fourth time. Remember to vacuum each t...

In this Diet & Health video tutorial you will learn how to check your own blood pressure. Checking blood pressure is a very important part of your personal health routine. Using machines that are widely available, you can easily and quickly check your blood pressure. The target figure will be 140 over 90. The other parameter is the pulse rate. If you are higher than these figures, you need to take a second opinion and consult your GP. Wrap the arm band around the upper arm above the elbow. Pl...

Make sure to get a complete upper body workout and add cable crossovers to your exercise routine. These crossovers can be done at varying angles to work a variety of chest and arm muscles without changing machines. Your pecs will thank you.

This video welding tutorial shows two arc or stick welding machines and explains how to connect the leads and hook it up ready for welding. Those interested in welding for metalwork will learn the proper machinery and equipment needed for welding and how to use the equipment correctly. Watch this instructional video and start welding.

Lawn mowers and lawn tractors are great machines and the latest models have some features worth checking out. New, fancy zero turn mowers, and four wheel steer mowers can make mowing your lawn quicker and easier. Tim Carter of Ask the Builder takes you through some of those new lawn mower features.

A CNC router machine is probably the most useful tool a hobbyist can own, but the price for a CNC machine on the market is way more than the average hobbyist is willing to spend. You can build your own CNC with very basic tools, little knowledge of machinery, mechanics, or electronics, but be warned, these machines are inherently dangerous, so wear the proper protection and use common sense. At the very least, read the instructions and precautions on every tool you use.

A CNC router machine is probably the most useful tool a hobbyist can own, but the price for a CNC machine on the market is way more than the average hobbyist is willing to spend. You can build your own CNC with very basic tools, little knowledge of machinery, mechanics, or electronics, but be warned, these machines are inherently dangerous, so wear the proper protection and use common sense. At the very least, read the instructions and precautions on every tool you use.

It can be said that bicycles hold a certain excitement as simple machines that we can use to move our bodies faster than usually possible, pumping and pushing in sync with the gears and pedals. Yet sometimes things go awry, parts break down, tires fail, chains come off of gears. In this free video guide to bicycle repair and maintenance, learn how to keep your bike in good riding shape, or fix it on the road, should the need arise. Lessons include how to fix a flat tire, install new hand grip...

These are some tricks for advanced computer use. These are PC only and meant for use on Windows XP machines.

Now that the iPhone 4 made its way to Verizon, there's a whole new crowd of smartphone users that are looking for jailbreak methods. And GreenPois0n has come to the rescue (yet again).

Antivirus programs usually aim to prevent malicious software from crashing your system, not ARE malicious software that crashes your system. Except, that was the case with AVG Anti-Virus yesterday when they released a software update that rendered 64-Bit Windows 7 systems useless. It affected both free and paid AVG owners.

WikiLeaks. In recent weeks, it's been the hottest topic on the web. It's been attacked on a multinational level by political influence peddling.

Basically its like good ole trampoline dodgeball. however there are machines surrounding the trampoline ready to shoot the dodgeballs at high speeds. Last man standing wins, that is if a man is still standing.

Introduction The 3 major anonymity networks on the Internet are Tor/Onionland, I2P and Freenet. If you feel confused on which one is the "best" one to use the answer is simple. Use all three!

Driving under the influence of alcohol is extremely dangerous. Police officers use breathalyzer tests to check if you are too intoxicated to be driving. However, many of the machines they use are faulty at times. This video will give you some tips on how to avoid getting that DUI. Avoid a false positive breathalyzer test.