Windows XP will always have a special place in my heart—it's the operating system I grew up on. It guided me through the glory days of AIM, Napster, and MySpace, but now it's dead. The OS that had been supported by Microsoft for twelve years officially lost its support on April 8th, 2014. Just like that, Microsoft has killed the beast, but for those of you who stubbornly refuse to cooperate, you can resurrect the dead. If you have Windows XP, this little known hack will get you further suppor...

If you thought humans were reading your résumé, think again. Robots do, and their one solitary objective is to systematically crush the hopes and dreams of those who don't make the cut. Instead of paying a few humans to read thousands of résumés over a couple weeks, many companies use computer programs that can do the job in less than an hour. In fact, at least 90 percent of Fortune 500 companies use what they call an applicant-tracking system, aka rejection machines.

Before cutting the rotors select a centering cone that fits about halfway through the center hole of hub-less rotor or bearing spacer to center the rotor to the spindle. After select two identical clamps that fit the rotor without interfering with the machined surfaces of the rotor. Slide one clamp onto lathe shaft, open end out Slide spring, followed by centering cone. Slide on the rotor and outer clamp followed by the bushing, spacer, and nut. Tighten nut and Install damping strap. Adjust t...

Black Mirror, Netflix's technology-horror anthology, never fails to provide thought-provoking entertainment centered around emerging and futuristic technologies, and the third season's second episode, "Playtest," delves deep into the worlds of mixed, augmented, and virtual reality. While designed to leave you haunted by the end, offering a more "evil" narrative than we'll likely see in our actual future, the episode explores possibilities that aren't as far off as one might think.

With the growing list of products Apple offers, the number of devices connected to your Apple ID can get quite extensive. Having all those devices connected to your Apple ID helps you keep track of them, but when it comes time to part ways with an Apple TV or Apple Watch, those devices can still be attached to your Apple ID. In some cases, this could affect the overall security of your account.

When you drive along the deceptively sedate streets of Silicon Valley, there are few hints that all those nondescript office parks and low-rise buildings contain the very future of the planet, but they really do. On a recent trip to tech's epicenter, I found that out firsthand when I got to visit the offices of Meta, the startup that produced the Meta 2 augmented reality headset.

Contrary to popular belief, augmented reality apps have been available for a while now. I remember using the Layar app (still available for iOS and Android) to explore nearby businesses and landmarks with varying success via an early-generation Android handset.

Kali Linux is known as being the de facto penetration-testing Linux distribution but can be a pain to use as an everyday OS — even more of a pain if that means carrying around a second laptop or the constant frustration of using the finicky Wi-Fi on virtual machines. But there's another option: installing a Kali subsystem on your Windows computer as a convenient compromise.

Every Friday, Next Reality reviews the latest headlines from the financial side of augmented and mixed reality. This Market Reality column covers funding announcements, mergers and acquisitions, market analysis, and the like. This week's column is led by two companies cashing in on visual inputs.

As an avid coffee drinker, I used to be a big fan of single-serve coffee machines. One day, the machine decided to stop working—which does happen from time to time—so I decided to go old school and use my automatic drip. Then, I realized that all I had were pods of single-serve coffee grinds, and I was all out of regular coffee filters!

In recent weeks, major bank websites around the world have experienced outages after being have been hit with Distributed Denial of Service (DDoS) attacks. Although few, if any, of these banks have been totally knocked offline, these DoS attacks have dramatically slowed the response time of their websites to legitimate customers. The most recent victim was the Royal Bank of Scotland. Due to this attack, RBS customers were unable to access their accounts for about an hour last week.

Welcome back, my hackers apprentices! To own a network and retrieve the key data, we only need to find ONE weak link in the network. It makes little sense to beat our heads against heavily fortified systems like the file and database server when we can take advantage of the biggest weak link of all—humans.

This step-by-step tutorial will show you how to install Mac OS on Windows 7 on Virtual Box. Video: .

Notes: My guides are setup like old Lego instruction booklets; picture intense/text lacking. Just remember you're building from the ground up, each step is a layer to go onto the previous layer.

Tech-savvy programmers and developers usually apply their unique talents exclusively to creating apps and websites — two high-paying and exciting pursuits that can open countless doors and opportunities in multiple fields.

One of the most critical bugs to come out in the last five years was Shellshock, a vulnerability which allows attackers to execute arbitrary code via the Unix Bash shell remotely. This vulnerability has been around for a while now, but due to the ubiquity of Unix machines connected to the web, Shellshock is still a very real threat, especially for unpatched systems.

With the announcement of ARKit 2.0 at WWDC 2018, Apple is bringing some powerful new capabilities to mobile augmented reality apps this fall.

User interfaces for computers have evolved over the years, from the introduction of the keyboard and mouse on the personal computer, to touchscreens on mobile devices, to natural voice recognition. However, the same cannot be said for robots or drones—until now.

The potential of augmented reality is often shown in science fiction movies, but a new exhibit marries the genre with very real-world AR technology, to great effect.

The rise and fall of Meta, the Silicon Valley-based augmented reality startup that looked to challenge the likes of Microsoft's HoloLens, and others, took just six years.

Kali Linux, by default, probably doesn't have everything you need to get you through day-to-day penetration testing with ease. With a few tips, tricks, and applications, we can quickly get started using Kali like a professional white hat.

Despite the popularity of Pokémon GO, augmented reality gaming hasn't quite caught on yet. The makers of the popular World of Tanks game aren't taking a shot at Niantic's crown yet, but they are looking at giving spectators a new way to watch the game.

Now that the cat's out of the bag, Magic Leap has published videos of a pair of apps that will be available to Magic Leap One early adopters.

Space might be the final frontier, but NASA is making a detour into augmented reality first. The Spacecraft AR app, developed by NASA's Jet Propulsion Laboratory (JPL) in collaboration with Google, debuted exclusively for Android this week (an iOS version is also in the works).

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

Apple has billed ARKit as a means to turn millions of iPhones and iPads into augmented reality devices. The refrain is similar for Kaon Interactive, a developer of product catalog apps for businesses.

Apple demonstrated their continued interest and investment into the awesome world of augmented reality during their Sept. 12 event, highlighting a few new AR games that will appear on iPhones thanks to ARKit. But that's not all you can expect — as long as you have an iPhone with an A9 chip or later, there will be a ton of cool new AR tools, games, and other apps to play around from the App Store.

One of the defining parts of my childhood was getting extremely frustrated with claw machines at arcades. Usually, that was because as fun as they were, they were probably rigged and wouldn't actually grab anything. Which is why a new claw machine demo made with Apple's ARKit is all the fun of the game, without the rigged frustration.

You would think most people would agree that you shouldn't use your smartphone while driving. Apparently, most people would be liars, according to recent data from the National Safety Council (NSC) and Zendrive.

At the WinHEC Shenzen 2016 Keynote, Microsoft showed off a system running Windows 10 smoothly on an ARM processor. This could be great news for developers of mixed reality software.

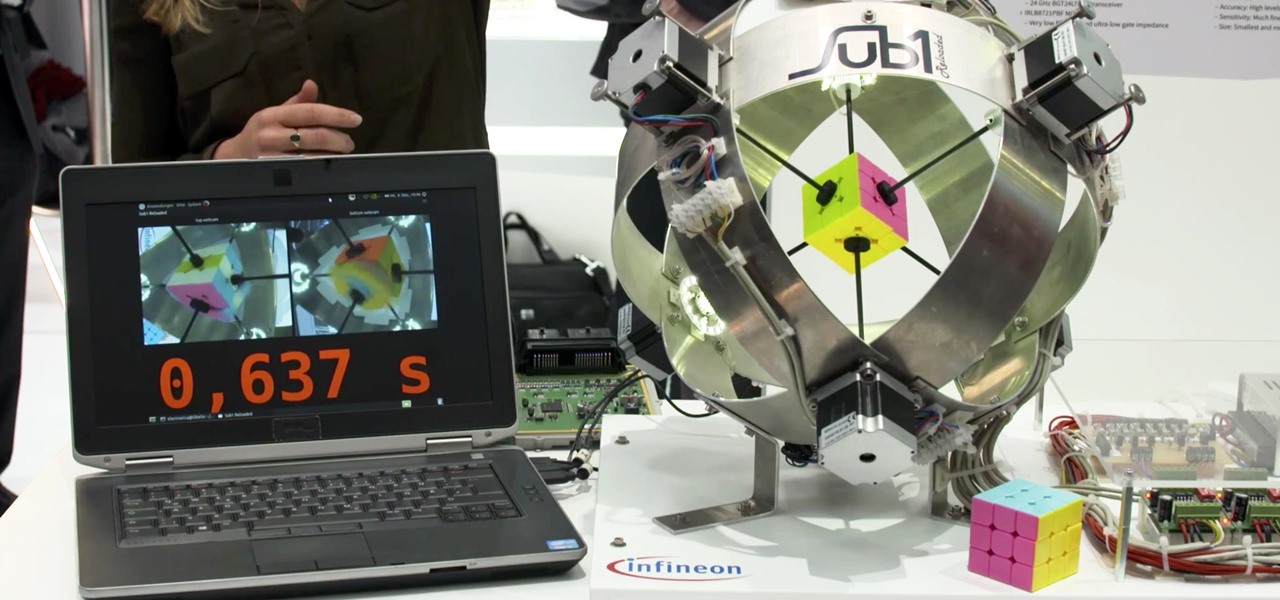
In December of last year, Australian Feliks Zemdegs broke the human world record for solving a Rubik's Cube with a time of 4.737 seconds. Well, this robot did it way, way faster by solving one in under 1 second. Don't tell me a robot takeover isn't real possibility.

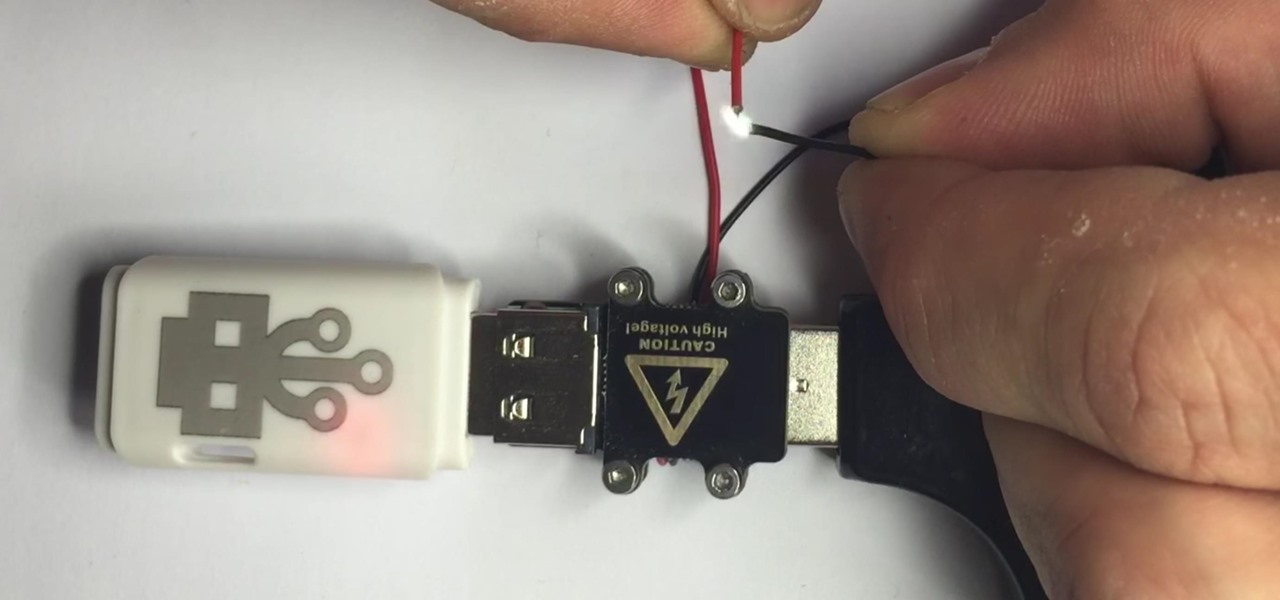
There are two types of bad USBs out there. One lets you trick the computer into thinking it's a keyboard or other USB device, and the other goes straight over malicious into computer killing territory.

Augmented reality has a variety of applications, but lately the face has been a major point of concentration for many companies. We're all pretty familiar with face swapping by now, but ModiFace employs similar technologies for more practical purposes.

Hello everyone. I'm Calypsus and i've been around for a while learning from various tutorials, expanding my knowledge and this is one of the best platforms for newbies to sharpen the skills. Today i decided to register myself and contribute to this wonderful community. Since this is my first post, any kind of feedback is appreciated.
According to security firm Kaspersky Lab, CoinVault and Bitcryptor ransomware are officially dead.

There are a lot of great tutorials on Null Byte using Python to create backdoors, reverse shells etc, so I thought it might be worthwhile making a tutorial on how to convert these python scripts to exe files for Windows victim machines.

Essentially, the Anti-Griddle does exactly what its name promises: it turns things almost instantaneously cold when you drop them on its "grilling" surface. Unlike home methods of flash freezing, its staggeringly low temperatures (-30°F/-34.4°C) allows ingredients that normally can't be frozen—like oil or alcohol—to turn into solids in the wink of an eye. As you might imagine, this allows chefs to play with textures and tastes in a way that was previously unimaginable.

Convenience is a big deal these days. You can buy single-serving or single-use sizes of just about anything, from fruits and vegetables to sanitizing wipes, and, apparently, even bananas. Uhh, it already has a wrapper...

Have a PC but hate Windows? Maybe you've just heard a ton about the new Mountain Lion OS X and want to see if it lives up to expectations. Either way, you can install Mountain Lion on your Intel-based PC in a few easy steps. All you need is a copy of the OS X and an 8 GB USB flash drive. The first step is getting Mountain Lion onto the flash drive. You'll need to format the drive with one partition as Mac OS Extended, Journaled and select Master Boot Record under options so that it's able to ...

Remember those Choose Your Own Adventure novels? If your school was anything like mine, they were so popular you were lucky to find one to check out at the library. But there's no worries now, thanks to this handy HTML5 app, which makes it easy to write and share your own 'choose your own adventure' novels. inklewriter is a free tool designed to make writing interactive stories simple. Basically, you start typing and inklewriter helps you organize your story, making it easy to add, remove and...