
News: Apple Brings 3D Scanning to macOS Monterey with Object Capture
As brands and content makers create more augmented reality experiences, the demand for tools to create 3D content grows in kind.


As brands and content makers create more augmented reality experiences, the demand for tools to create 3D content grows in kind.
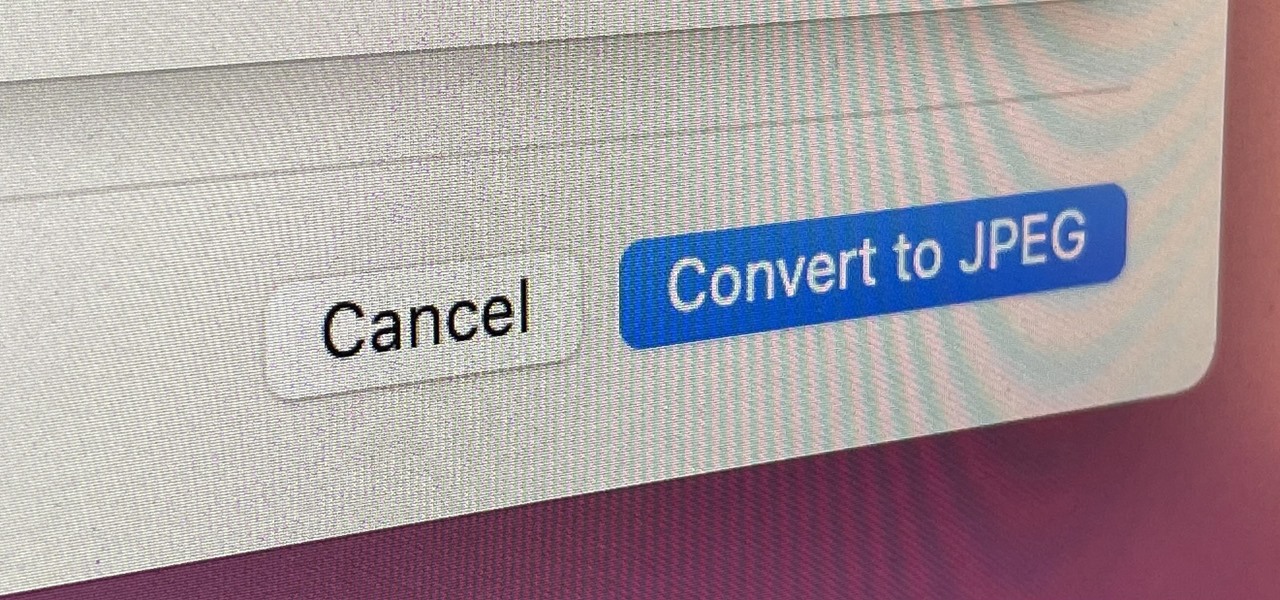
If you regularly run into issues opening images that use the .heic extension, the easiest solution is to convert the file into a more compatible format. Using apps like Photos and Preview on a Mac makes the process simple, but macOS Monterey just streamlined the process so that you don't even have to open an app anymore.

This is a delicious recipe you can make in your crock pot or slow cooker! For this recipe, you will need (apart from a slow cooker): a box of spaghetti, grated Monterey Jack cheese, grated Parmesan cheese, 1/8 teaspoon garlic powder (or one garlic clove), 1 cup sour cream (or fat free yogurt) and 1 egg.

Chile con queso, a classic Tex-Mex dip, is inexpensive, easy to make, and positively delicious! Round up these ingredients (16 oz cheddar cheese, 1 cup chiles, a medium onion, 1 clove of garlic, canned tomatoes, beans, 6 oz Monterey Jack cheese, and either tortilla chips or rice to serve it with) and you're ready to cook! Follow along with the steps in this quick video cooking show and learn how to make this tasty Mexican snack.

Want a very nontraditional take on a classic American comfort food? Then this hearty and spicy recipe is it. Made with ample helpings of salsa, cilantro, black beans, yellow corn, green and red bell peppers, and enchilada sauce, this casserole dish will make your mouth smoke with its succulent hotness. The casserole is then topped with a layer of Monterey and Jack cheese for added crunch and gooeyness.
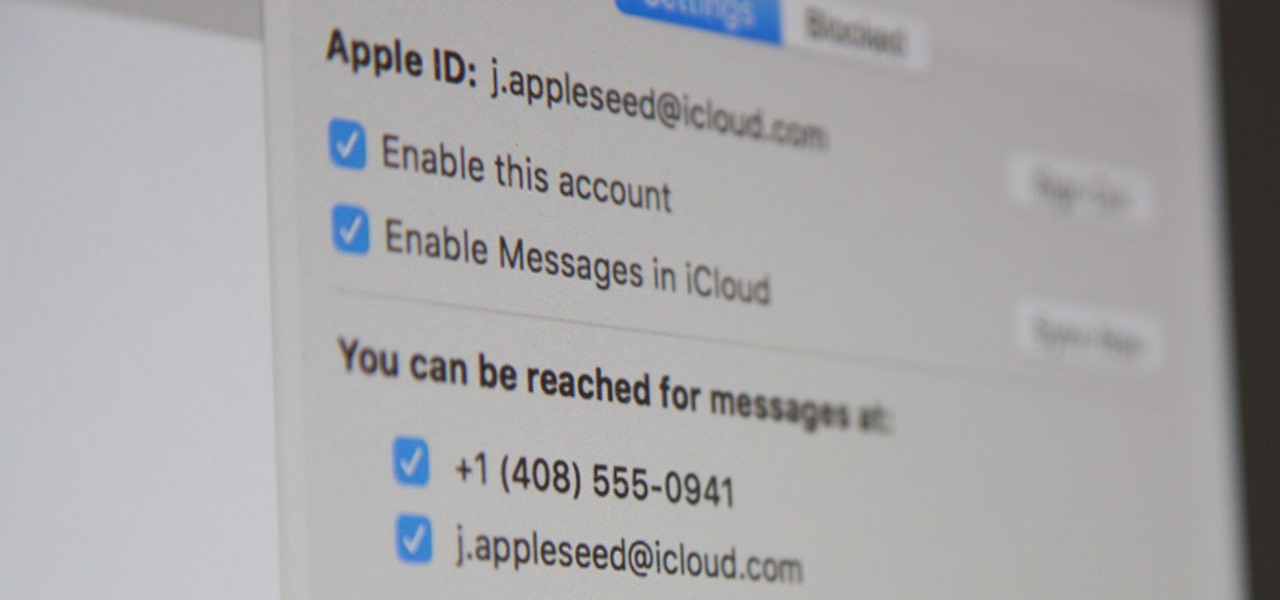
Apple pushed out iOS 11.4 on May 29 to iPads and iPhones, which included the long-awaited Messages in iCloud feature. The company did not release macOS High Sierra 10.13.5 at the same time, limiting the usefulness of being able to sync messages in the cloud since 10.13.4 is not compatible with Messages in iCloud. But three days later, Apple finally released macOS 10.13.5.

Fish is delicious, and as the Harvard School of Public Health points out, incredibly good for you. There are many studies that show regularly consuming a couple of servings of fish per week can help prevent heart disease and may well reduce your chances of stroke, depression, and getting Alzheimer's. After all, there's a reason why fish is called "brain food."

Sonya McDaniel of the Food Corner presents this healthy and delicious recipe for sausage stuffed acorn squash.

This video shows how to make this spicy chicken dish. The chicken breasts are marinated in advance for 24 hours. They are grilled with the skin down first, which helps preserve the moisture and flavor of the chicken.

The Food Corner brings us a unique idea – enchiladas cooked in a crock-pot. The ingredients needed are tortillas, cooked hamburger meat, pinto beans and black beans, some water, a can of tomatoes with green chilies, cumin, pepper, chili powder, Monterey jack cheese and sharp cheddar cheese.

Tamales are very laborious to make, but they are definitely worth it. This cooking how-to video shows you the step by step process of making Mexican tamales with Mexican chorizo. You can use chorizo as your stuffing agent or any other meat.

While you might suspect your MacOS computer has been infected with malware, it can be difficult to know for sure. One way to spot malicious programs is to look for suspicious behavior — like programs listening in on our keyboard input or launching themselves every time we boot. Thanks to free MacOS tools called ReiKey and KnockKnock, we can detect suspicious programs to discover keyloggers and other persistent malware lurking on our system.

Nothing beats an appetizer packed with healthy spinach and delightful cheeses. It's the perfect party snack, and in this video, you'll learn the recipe for Spinach & Cheese Swirls from Holiday Kitchen. These spinach and cheese appetizers are made with puff pastry, and look so good, your friends will think you're hiding the caterer!

While it hasn't gotten as much attention as iOS 10, Apple's big 10.12 update to their Mac operating system is finally out for all to enjoy—and you can download it for free from the Mac App Store right now.

The USB Rubber Ducky and the Digispark board both suffer from the same issue when attacking macOS computers: a keyboard profiler pop-up which tries to identify any non-Apple USB keyboards. While it's an annoying setback, the solution is a simple modification that allows Mac computers to be targeted, which affects the ability to target Windows and Linux devices.
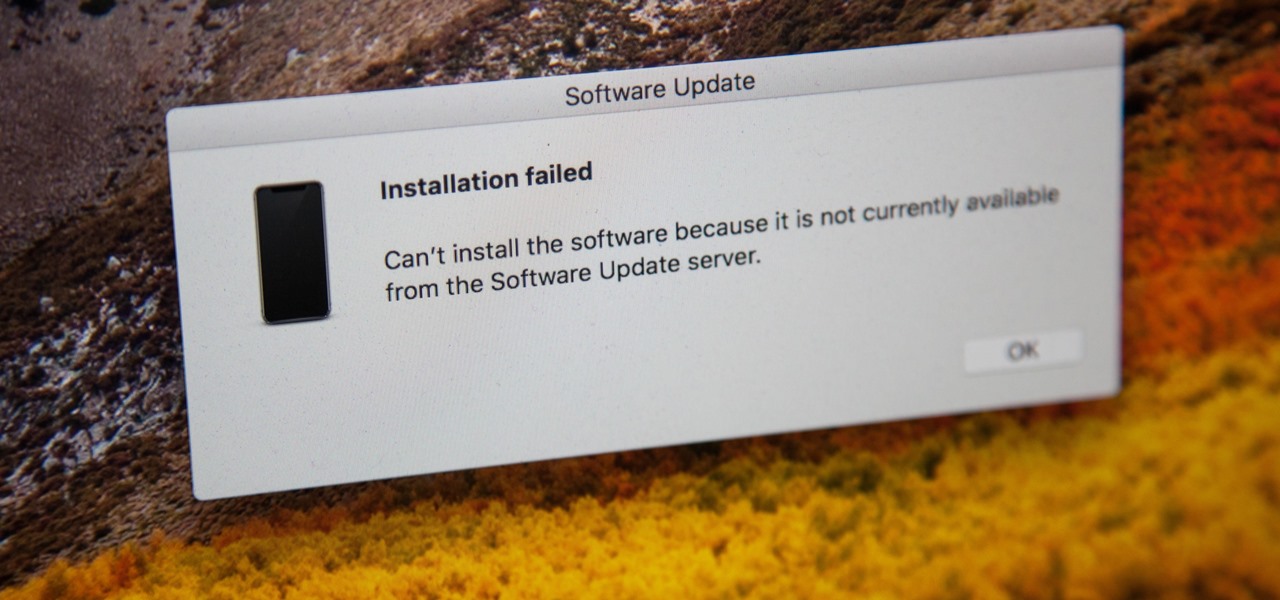
If you're currently running macOS 10.11 or higher on your Mac and connect your iPhone to sync with iTunes, you may get an alert saying that "a software update is required to connect to your iPhone." Here's everything you need to know about what that means, how to update your system, and what to do if updating doesn't work.

In usual Apple fashion, there are new wallpapers to go along with their new operating systems, iOS 10 and macOS Sierra. The background that's included in iOS 10 for iPad, iPhone, and iPod touch is a crashing aqua-colored wave with land just below its surface, and macOS Sierra's is a razor-sharp mountain ridge from the Sierra Nevada mountain range in California.

While MacOS computers have been spared from some of the most famous malware attacks, there is no shortage of malicious programs written for them. To keep your computer safe from some of the most common types of malware, we'll check out two free tools. These tools can automatically detect ransomware encrypting your files and watch for unauthorized access to your microphone and camera.

Locating and abusing files containing unsafe permissions is an easy and surefire way to elevate shell privileges on a backdoored macOS device. This time around, we'll be more aggressive and attempt to phish a user's login password by prompting a convincing popup message merely asking the target for their password.

MacOS isn't known as an ideal operating system for hacking without customization, but it includes native tools that allow easy control of the Wi-Fi radio for packet sniffing. Changing channels, scanning for access points, and even capturing packets all can be done from the command line. We'll use aliasing to set some simple commands for easy native packet capture on a macOS system.

Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks.

A powered-off MacBook can be compromised in less than three minutes. With just a few commands, it's possible for a hacker to extract a target's password hash and crack it without their knowledge.

The misconception that macOS is more secure than the Windows operating system is far from the truth. With just one small command, a hacker can completely take over a MacBook and control it remotely.

Apple's Gatekeeper security software for macOS (Mac OS X) is vulnerable to remote attacks up to version 10.14.5. An attacker that's anywhere in the world can exploit MacBooks and other Mac computers by sharing a single ZIP file.

Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, we'll outline dozens of macOS-specific attacks penetration testers should know about.

It's important to know who you're dealing with after hacking your target's MacBook. Getting remote access is simple, but covertly gathering information about the user and their system can be a challenge.

With the rise of website encryption (TLS), sniffing passwords from network activity has become difficult. However, it's still possible to quietly exfiltrate a target's network traffic in real time to extract passwords and sensitive information. Pertaining to macOS, there are two methods for retrieving traffic from a backdoored Mac.

While hackers have taken advantage of numerous vulnerabilities in Adobe's products to deliver payloads to Windows users via PDF files, a malicious PDF file can also wreak havoc on a Mac that's using the default Preview app. So think twice before double-clicking a PDF open on your MacBook — it might just be a Trojan with a rootkit inside.

The conversation of which operating system is most secure, macOS vs. Windows, is an ongoing debate. Most will say macOS is more secure, but I'd like to weigh in by showing how to backdoor a MacBook in less than two minutes and maintain a persistent shell using tools already built into macOS.

It looks like there is a fatal flaw in the current macOS High Sierra 10.13.1, even straight from the login menu when you first start up the computer. This severe vulnerability lets hackers — or anyone with malicious intentions — do anything they want as root users as long as they have physical access to the computer.
A macOS computer can reveal a lot of information about the owner, including which Wi-Fi network they have permission to access. With an Arduino-based attack, we'll use a five-dollar setup to inject a rogue Wi-Fi network and steal the list of trusted Wi-Fi networks, allowing us to see where the computer has been.

With a simple social engineering trick, sudo passwords can be captured in seconds without the target's knowledge. The passwords can then be saved to a file or exfiltrated to another computer on the network.

The first few minutes after gaining access to a MacBook are critical — but where do we begin? Using tools built into macOS, we can develop an in-depth understanding of running background processes, detect antivirus software, locate sensitive files, and fingerprint other devices on the network. All of this can be done without installing additional software or modifying any files.

With just one line of Ruby code embedded into a fake PDF, a hacker can remotely control any Mac computer from anywhere in the world. Creating the command is the easy part, but getting the target to open the code is where a hacker will need to get creative.

Using Netcat to backdoor a macOS device has its short-comings. If the compromised Mac goes to sleep, the Netcat background process will occasionally fail to terminate correctly; This leaves Netcat running infinitely in the background and the attacker with no new way into the device. As an alternative, we'll use the lesser-known Tcl shell which can handle abrupt backdoor disconnections.

With the macOS stager created and the attacker's system hosting the Empire listener, the malicious AppleScript can be designed and disguised to appear as a legitimate PDF using a few Unicode and icon manipulation tricks.

The newest version of macOS has arrived. While everyone's mind is being blown by Mojave's groundbreaking new Dark Mode, we'll be taking advantage of its insecure file permissions to establish a persistent backdoor with a self-destructing payload that leaves little evidence for forensics.

Barrow's article on Pupy made me wish for a RAT that could target an OS frequently used by gatekeepers at startups, tech companies, and creative firms: macOS. Once run, a RAT can do severe damage by dumping a user's stored credentials for many accounts. The best loot lives in the Chrome Password cache, and EvilOSX, an OS X RAT, infiltrates macOS and dumps these credentials.

Sharks. The first thing that comes to mind is "Jaws", Steven Spielberg's horrifying shark film that scared generations of young adults from entering the ocean waters. But not all sharks are as violent (and hungry) as "Jaws", so jump in the water and know a few guidelines to stay safe. Escape a shark’s jaws of death with these lifesaving strategies.

Enchiladas are a Mexican staple that can be made with chicken, beef, or cheese. This easy recipe makes a tasty and satisfying meal.