You don't have to be a frequent flyer to know how indispensable navigation apps have become. Many of us rely on these apps for traveling from state to state and getting around in foreign cities, but even more of us count on these apps to beat rush hour traffic and find the quickest routes to school or work. So naturally, we all have our favorite mapping apps, but which one is truly the best?

Hacker's are always looking for new ways to exploit systems and exfiltrate passwords, even in hashed form. Sophisticated brute-force attacks powered by high-end GPUs can perform millions of password attempts per second. But Ubuntu and Debian users aren't completely helpless. There are ways to harden the hashed password to better defend against Hashcat attacks.

Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands.

With just a few taps, an Android phone can be weaponized into a covert hacking device capable of running tools such as Nmap, Nikto, and Netcat — all without rooting the device.

When it comes to attacking devices on a network, you can't hit what you can't see. Nmap gives you the ability to explore any devices connected to a network, finding information like the operating system a device is running and which applications are listening on open ports. This information lets a hacker design an attack that perfectly suits the target environment.

For anyone wanting to keep information private, plain text is a format of the past. Instead, cheap, powerful encryption is widely available, but often not easy enough to use to attract widespread adoption. An exception to this rule is EncryptPad, an easy to use application that lets you encrypt text, photos, or archives with strong encryption using a password, keyfile, or both.

For the uninitiated, it can be difficult to buy that special hacker in your life a perfect holiday gift. That's why we've taken out the guesswork and curated a list of the top 20 most popular items our readers are buying. Whether you're buying a gift for a friend or have been dying to share this list with someone shopping for you, we've got you covered with our 2018 selection of hacker holiday gifts.

In a previous tutorial, we were able to place the Mona Lisa on vertical surfaces such as walls, books, and monitors using ARKit 1.5. By combining the power of Scene Kit and Sprite Kit (Apple's 2D graphics engine), we can play a video on a flat surface in ARKit.

In a previous tutorial, we were able to measure vertical surfaces such as walls, books, and monitors using ARKit 1.5. With the advent of vertical plane anchors, we can now also attach objects onto these vertical walls.

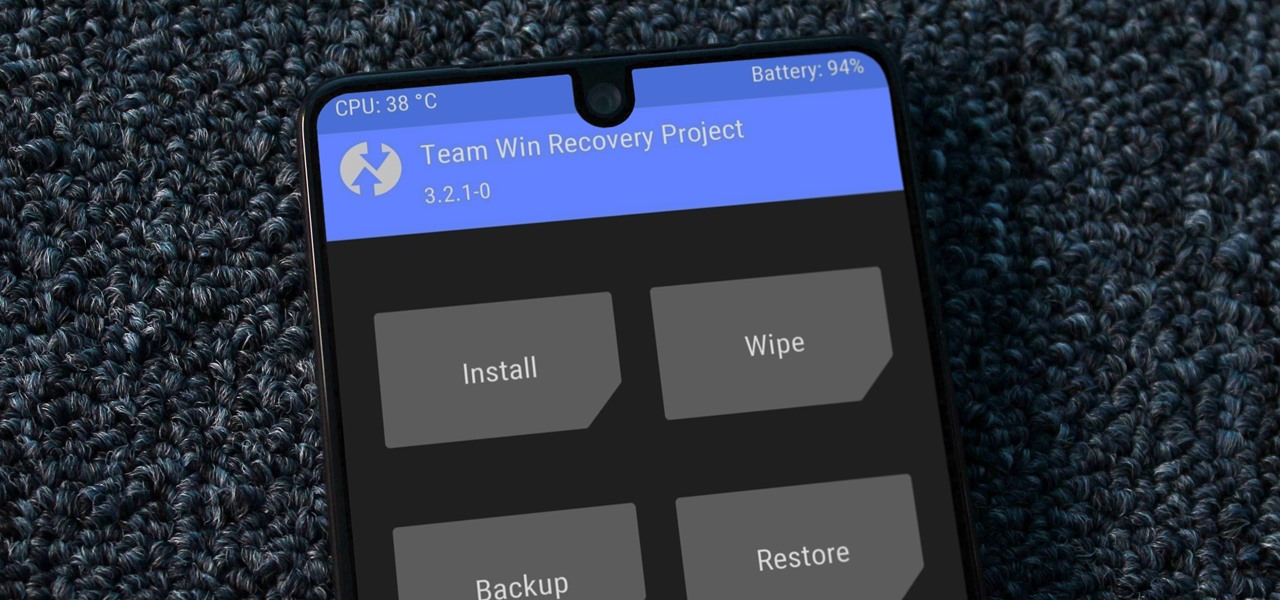
For modders, there are few tools more important than TWRP. TeamWin's custom recovery makes flashing mods like Magisk, Xposed, and custom ROMs incredibly easy, and it lets you root your phone at the press of a button. On top of that, it can make complete backups of your phone in case you mess up. That's why, for Essential users, this should be the first mod you add.

In a previous tutorial, we were able to measure horizontal surfaces such as the ground, tables, etc., all using ARKit. With ARKit 1.5, we're now able to measure vertical surfaces like walls!

Apple officially released iOS 12 to everyone on Sept. 17, and while the new iPhone XR, XS, and XS Max will come with the software by default, you have a choice on whether or not to update your current iPhone model from iOS 11. There are a lot of tempting features to want to update right away, but there are also some compelling reasons to wait it out and install at a later time.

Kali Linux, by default, probably doesn't have everything you need to get you through day-to-day penetration testing with ease. With a few tips, tricks, and applications, we can quickly get started using Kali like a professional white hat.

Think back to when you last wanted to transfer some music or videos to your friend's smartphone and how difficult and slow it was. As powerful as our phones are, the default file sharing options are limited. There are, fortunately, some better options which make moving files easy, secure, and painless.

Have you noticed the many utility ARKit apps on the App Store that allow you to measure the sizes of horizontal planes in the world? Guess what? After this tutorial, you'll be able to do this yourself!

Have you been noticing SpaceX and its launches lately? Ever imagined how it would feel to launch your own rocket into the sky? Well, imagine no longer!

Hashes containing login passwords are transmitted between Windows computers on local Wi-Fi networks. By intercepting and decrypting these hashes using Responder and John the Ripper, respectively, we can learn a target's login credentials which can be later used to gain physical access to their computer.

After a hacker has configured Metasploit on a remote private server, created a resource script for automation, and created a simple payload, he or she can begin the process of remotely controlling someone's Windows 10 computer with just a few moments of physical access — even if the computer is off.

Security-minded users can reduce the risk of phishing by enabling Advanced Protection on important Google accounts, requiring a U2F security token to log in. Using these keys isn't intuitive on most popular smartphone platforms, and you can find yourself locked out if you don't plan ahead. You'll need to learn and practice using U2F keys on your device before enabling this layer of security.

Dating websites allow you to see a person in a very intimate context, framing their successes and accomplishments in life to an important audience. The information contained in these profiles often can't be found elsewhere, offering a unique look into the personal life of the user.

Many guides on Null Byte require using the Secure Shell (SSH) to connect to a remote server. Unfortunately for beginners, learning to use SSH can become a confusing mix of third-party programs and native OS support. For Chrome OS users, using SSH is even more difficult. We'll fix this by using the Chrome Secure Shell to establish an SSH connection from any device that can run a Chrome browser.

With Virtual Network Computing, you don't need to carry a spare keyboard, mouse, or monitor to use your headless computer's full graphical user interface (GUI). Instead, you can connect remotely to it through any available computer or smartphone.

For all those times when an app either isn't available or simply won't cut it, your phone's internet browser provides access to your favorite websites and services. But some browsers are flat-out better than others, and chances are, the browser that came pre-installed on your phone isn't the best option out there.

JavaScript is one of the most common languages used on the web. It can automate and animate website components, manage website content, and carry out many other useful functions from within a webpage. The scripting language also has many functions which can be used for malicious purposes, including stealing a user's cookies containing passwords and other information.

Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing us to intercept and modify network data. This can be dangerous for private data, but also be fun for pranking your friends.

Ransomware is software that encrypts a victim's entire hard drive, blocking access to their files unless they pay a ransom to the attacker to get the decryption key. In this tutorial, you'll learn how easy it is to use the USB Rubber Ducky, which is disguised as an ordinary flash drive, to deploy ransomware on a victim's computer within seconds. With an attack that only takes a moment, you'll need to know how to defend yourself.

In 2013, Offensive Security released Kali Linux, a rebuild of BackTrack Linux derived from Debian. Since then, Kali has gone on to become somewhat of a standard for penetration testing. It comes preconfigured with a collection of tools accessible by a menu system, tied together with the Gnome desktop environment. However, Kali Linux isn't the only penetration-testing distribution available.

Imagine for a moment that a VPN is like putting on a disguise for your computer. This disguise works to change your IP address, secure your traffic with encryption, and mask your location to bypass regional restrictions. This makes it a helpful tool for both whistleblowers and journalists. VPNs are also built into the well-known Tor Browser.

RouterSploit is a powerful exploit framework similar to Metasploit, working to quickly identify and exploit common vulnerabilities in routers. And guess what. It can be run on most Android devices.

Full disclosure: I really like Apple's stock ringtones on the iPhone. After all, there are over 50 to choose from if you include the classic ones. With all that choice, why would you ever need more? Personally, I get bored easily, and I'd like my music to play when people call. Apple doesn't let us pick a song from our music libraries, but there is still a way to use our favorite tunes as tones.

With some of the groundwork out of the way in getting a Mac set up for hacking, it's time to start looking at toolboxes. Our first toolbox is Git, which will be used throughout future tutorials.

While iOS 11 is ready to take over your iPad, iPhone, and iPod touch, let's take a step back and check out all of the new features that iOS 10 brought to the public when it was released to everyone in Sept. 2016.

Apple has revolutionized how we write with the introduction of its new Writing Tools, powered by Apple Intelligence. In beta on iPhone, iPad, and Mac, these tools allow you to select text and use intelligent features to summarize, proofread, or rewrite it until the tone and wording are just right. In a future beta, Writing Tools can even write original content for you.

Apple's hottest new FaceTime feature, SharePlay, comes packed with sharing options, and the biggest one lets you share your device's screen with the people you're FaceTiming. It didn't make it in time for the big iOS 15 release, but it did arrive in iOS 15.1, released Oct. 25, and here's how it works.

Data can be injected into images quickly without the use of metadata tools. Attackers may use this knowledge to exfiltrate sensitive information from a MacBook by sending the pictures to ordinary file-sharing websites.

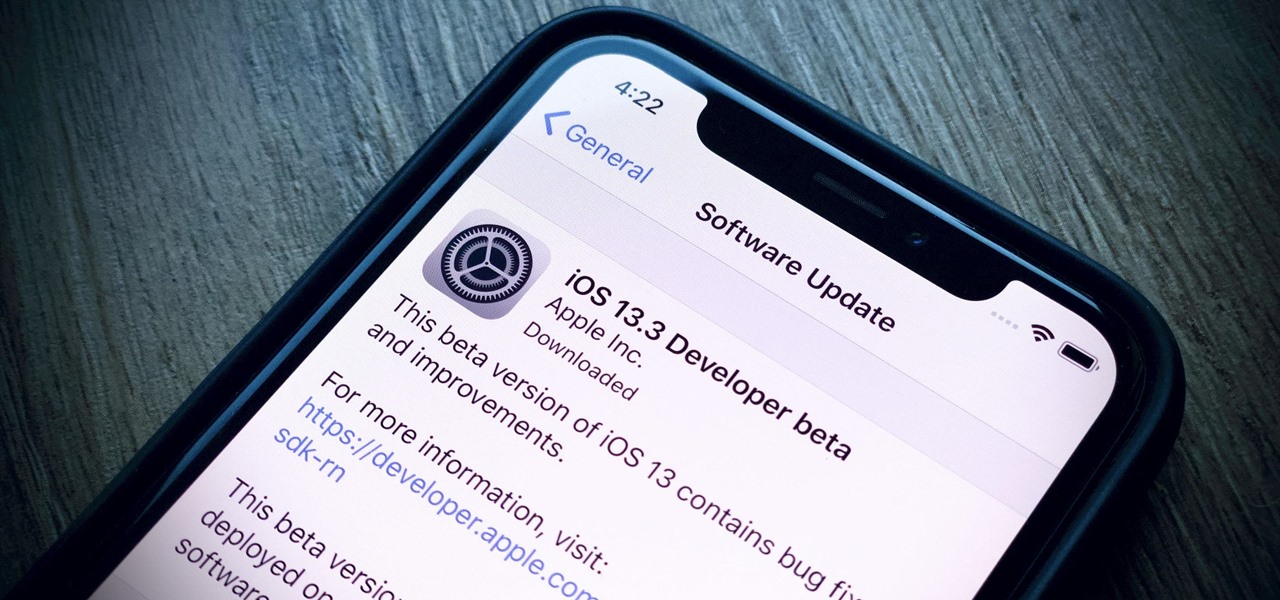
Apple's already gone through iOS 13.0, 13.1, 13.2, 13.3, 13.4, and 13.5 betas, and now it's time for iOS 13.6. If you want to try out new features on your iPhone before the masses, install either the developer or public beta.

In the latest software updates for iPhone and iPad, there's an even easier way to view all your saved Wi-Fi networks and credentials and share them with family, friends, and others who need access.

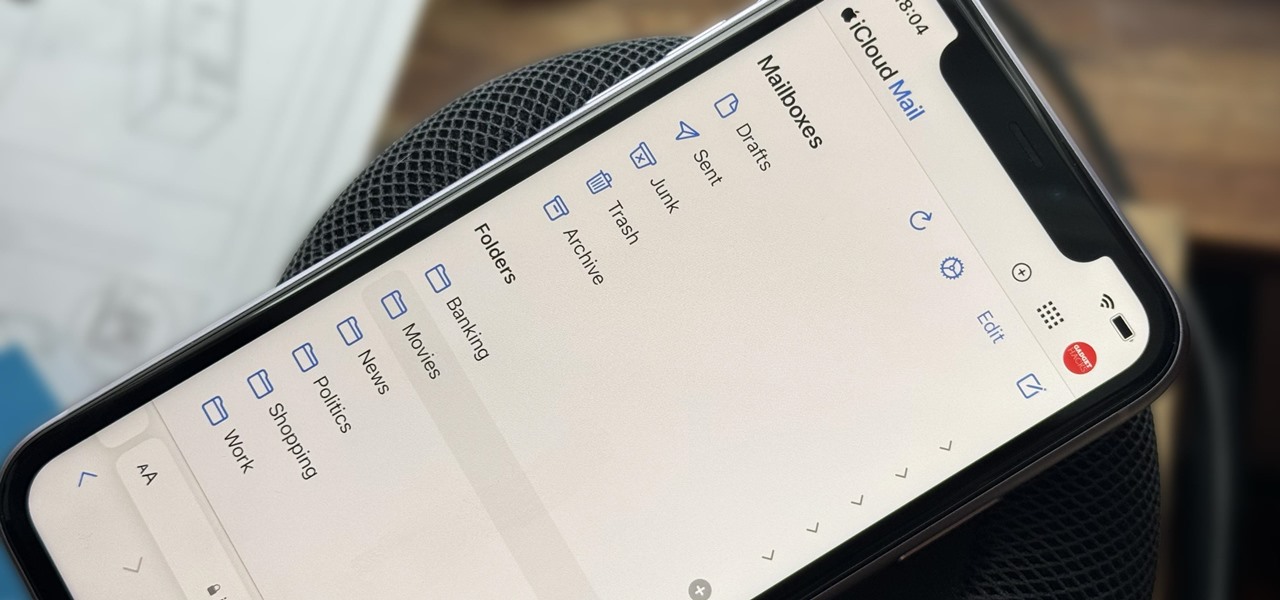
Apple includes a lot of helpful features for iCloud email addresses, but one of its best-kept secrets will give you total control over organizing your inbox like a pro.

Apple's Podcasts app just got a big feature: transcripts. Before, you had to rely on third-party services or the off chance that podcast creators posted transcription links to each of their episodes. Now, you can view, read, and search show transcripts directly in Podcasts, whether uploaded from the creators or automatically generated by Apple.

The Reminders app is a simple yet powerful task manager, and it does a great job of reminding you to start an errand, alerting you to a project that's supposed to be done, or prompting you about a recurring chore. But with the latest Reminders update, the dates and times you set for tasks can act more like due dates thanks to the new early reminders feature.