
How To: Apple Music Subscribers Just Got a Massive New iPhone Feature
A massive new feature just hit Apple Music, and it's the biggest thing to happen to Apple Music since Apple Music was even a thing.


A massive new feature just hit Apple Music, and it's the biggest thing to happen to Apple Music since Apple Music was even a thing.

One advantage to using Apple's ecosystem is Continuity, which allows you to move files, media, and tasks seamlessly between all your Apple devices. It even lets you use one device to help with actions on another, like unlocking your Mac with your Apple Watch or using your iPad as a second display. Now, things are even better with Continuity with Handoff's new FaceTime functionality.
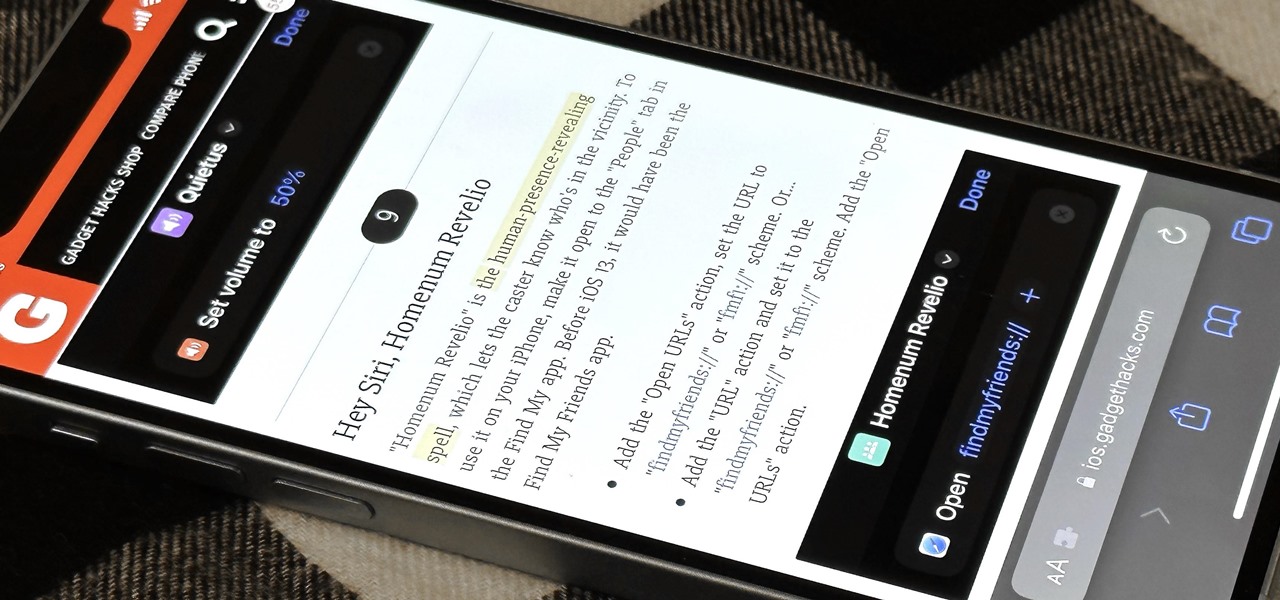
Safari has a major new feature for your iPhone, something that will change how you share, receive, and interact with links — and nobody is talking about it. The feature works on the latest iOS software, as well as the latest iPadOS and macOS versions. Still, you won't find any information about it in Safari's app or settings, so it's pretty hidden if you haven't seen it by accident yet.
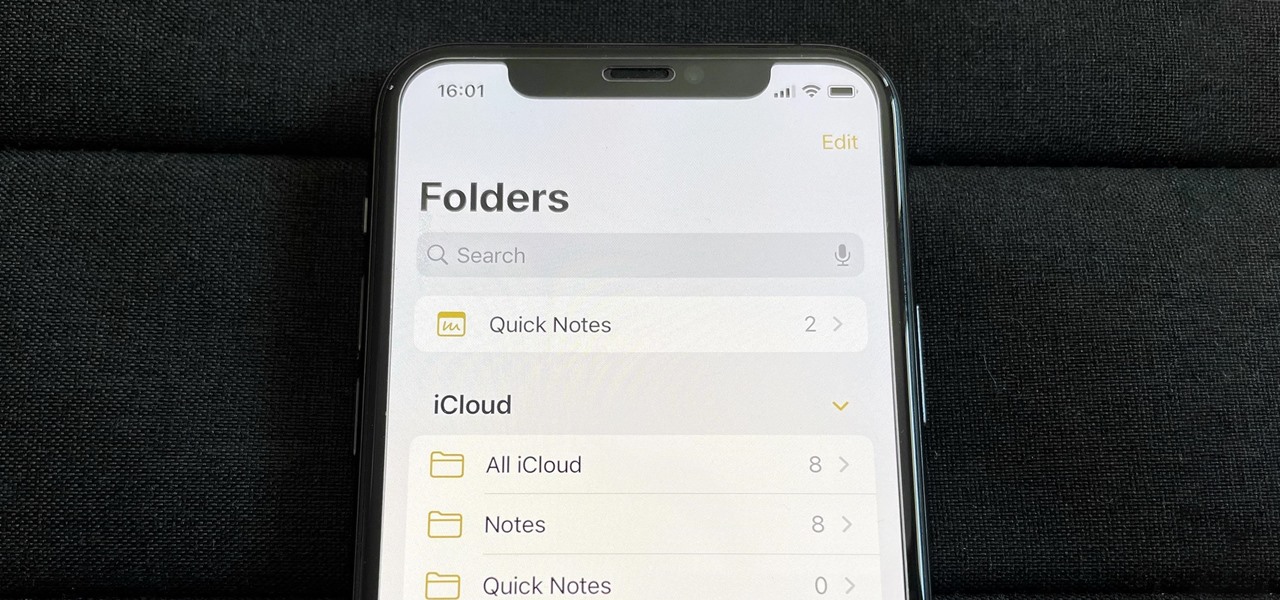
If you use the Notes app on your iPhone and haven't updated to the newest software yet, you're missing out on some pretty valuable upgrades that improve smart folders, note security, collaboration, and more. So what are you waiting for?

Apple's iOS 16 for iPhone includes even more ways to customize your Memoji characters, and it even removes some barriers that were in place in iOS 15.

Yo dawg, Snap heard you using Snapchat augmented reality Lenses in your messages, so it's putting its AR Lenses in other messaging apps.
Your iPhone keeps track of every single place you go, especially those you frequent most often, and syncs those locations across all your iCloud-connected devices. People who gain access or already have access to your iPhone, iPad, iPod touch, or Mac may be able to view all of these locations to see where you've been and where you might be. If this worries you, there are things you can do.
Apple's "Spring Loaded" event introduced us to many new and exciting products, including iMac and iPad Pro models with the M1 chip, an upgraded Apple TV 4K, a purple iPhone, and the long-awaited AirTag. However, one of the most anticipated announcements came in the form of a software update — the biggest update since iOS 14.0 and iPadOS 14.0 came out — and that's iOS 14.5 and iPadOS 14.5.

Apple's new iOS 14.5 will be coming out very soon, and that's even more evident now with the release of the iOS 14.5 Release Candidate (RC) on Tuesday, April 20. Anyone can install this update and get all of the same features iOS 14.5 will give everyone for iPhone; only you'll have a head start to using all of the updates in Maps, Music, Podcasts, Reminders, Shortcuts, Siri, and more.

Never being contacted for a job you're interested in interviewing for is a terrible feeling. It might make you feel inadequate as if your qualifications aren't up to par, but the problem might be that your resume isn't even getting read in the first place.

Screen mirroring software has been around for ages, allowing you to mirror your iPhone to a projector, laptop, TV, or another device. It's useful to have during lectures, presentations, and meetings, so it's no wonder why Apple created its AirPlay technology. However, AirPlay doesn't work in all situations.

If you're an AirPods owner, you know the sound — that decrescendo of little beeps and boops means imminent "death" for your wireless earbuds. Other than that infamous chime, however, it's not overly clear how to check your AirPods, AirPods Pro, or AirPods Max power levels. That's why we've listed all the ways to do so.
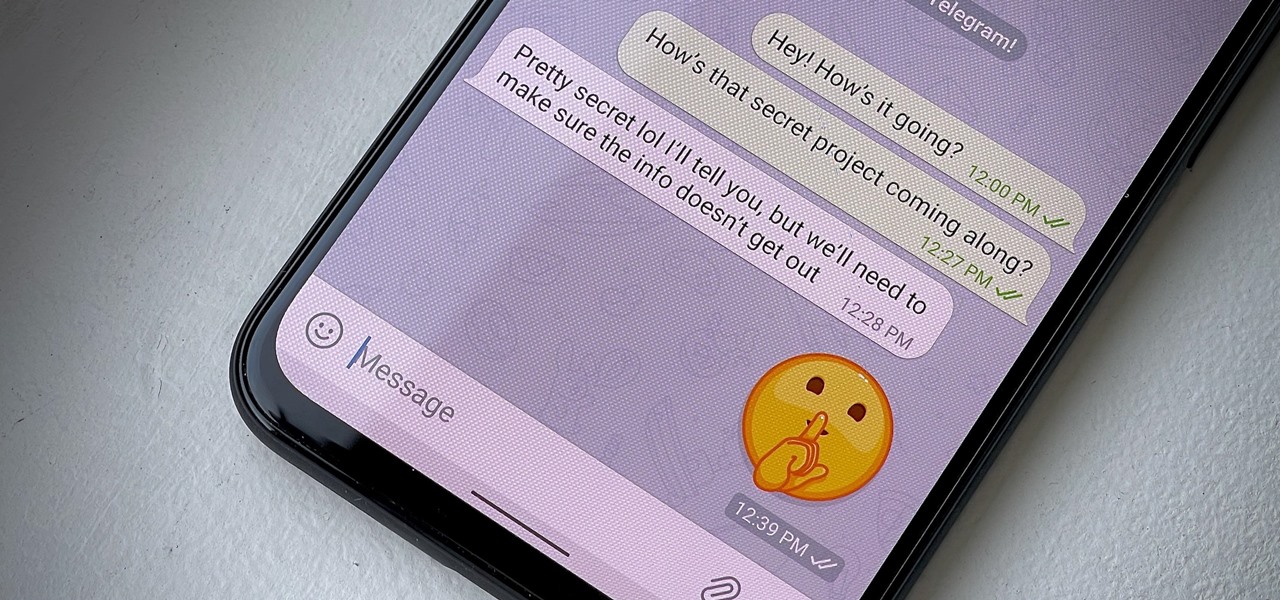
Have some sensitive information you need to share with somebody on Telegram but are worried it might fall into the wrong hands? You don't have to worry anymore because Telegram now sports a way to automatically delete all new messages in any chat of your choosing, not just end-to-end encrypted ones.
Your Apple Music subscription is tied to the Apple ID that subscribed, so you can stream content from any iOS, iPadOS, macOS, tvOS, or watchOS device that your Apple ID is signed in to. However, things get slightly more complicated when you want to listen to Apple Music on another device you use with a different Apple ID, such as a work iPhone. Complicated, but not impossible.

Since iOS 11, a thumbnail preview appears on your iPhone whenever you take a screenshot. It's useful for access to quick sharing options and editing tools, but you can't disable the preview image. You can wait for it to disappear or swipe it off-screen, but that's as good as it gets — until now. In an iOS 14 update, there's an option to disable the screenshot preview — only you won't find it in Settings.

While obvious, it's a lot more difficult to hack into a locked computer than an unlocked computer. As a white-hat hacker, pentester, cybersecurity specialist, or someone working in digital forensics, there's an easy solution — make it so that the computer won't fall asleep and lock automatically in the first place.

Apple just released the eighth public beta for iOS 14 today, Wednesday, Sept. 9. At this time, beta 8 (18A5373a) seems to be a minor update to iOS 14, introducing bug fixes to improve the software's overall stability.

Apple just released the eighth developer beta for iOS 14 today, Wednesday, Sept. 9. Beta 8 (18A5373a) appears to be a minor update offering bug fixes to improve overall stability.

For the past five years, Apple has been hosting live media events in September to reveal new Apple products and the stable release for its latest operating systems. This year is no different, and it has a Sept. 15 date, but it may not be the only event coming up before the end of 2020.

It's a common misconception that iPhones are impervious to cyberattacks and "more secure" than Android. And when an iPhone does get hacked, it's nearly impossible to tell that it happened.
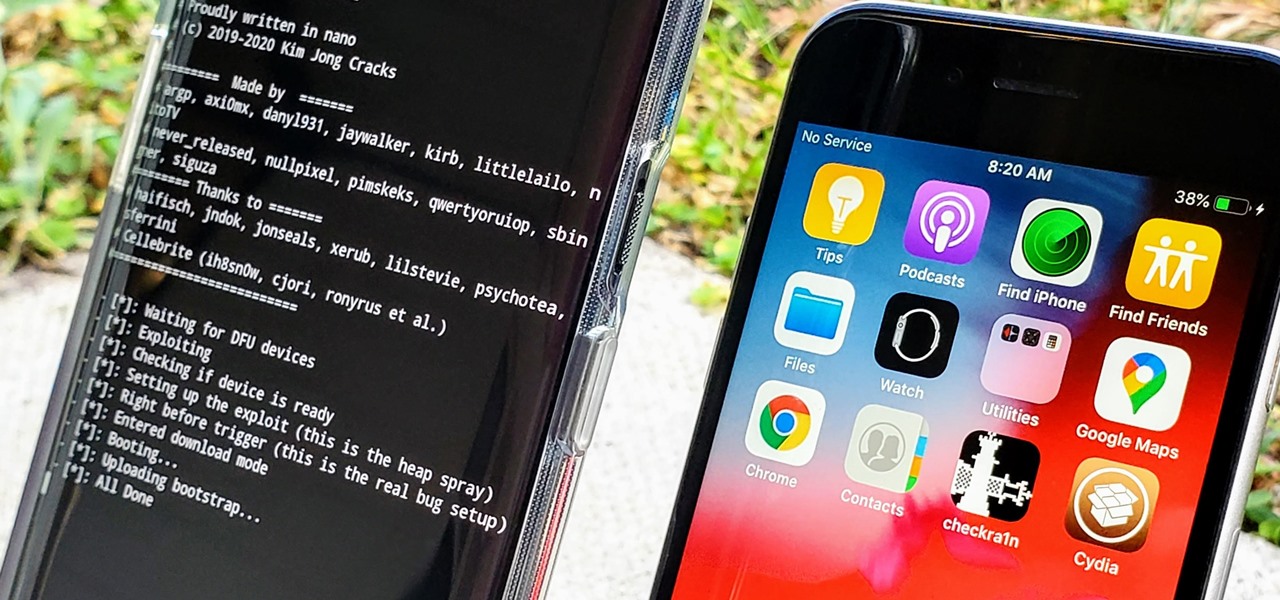
In the iPhone modding scene, the Checkm8 bootrom exploit, by developer axi0mX, led to a powerful jailbreaking tool known as Checkra1n. With it, you can jailbreak a variety of iPhone models without worrying about it getting patched later on. But in the past, it required you to have a macOS computer — but not anymore.
There's no doubt iOS 13 has dominated the talk around the Apple community this month. Since the announcement and release of the first developer beta, we iPhone users have had a treasure trove of new features and changes to explore and discuss. Now the fun continues with iOS 13 dev beta 2. Who's ready to start up the conversation all over again?

Smartphone videos get better and better each year. Seven or eight years ago, who would have thought iPhone and Android phones could support 4K video recording. Some phones can even shoot slow-motion at 960 fps. But no matter the resolution or frame rate, a phone's rolling shutter can make quick movements in front of the camera appear wobbly, distorted, or with artifacts.

If you want to get started sniffing Wi-Fi networks, you usually need to start with a wireless network adapter. But thanks to a Wi-Fi sniffing library written in Arduino and the ultra-cheap ESP8266 chip, you might not need one. For less than $10 in electronics, you can build a tiny Arduino Wi-Fi sniffer that saves Wireshark-compatible PCAP files and fits anywhere.

A relay is an electrical component that works like a light switch, where it's turned on or off with an electrical signal. By connecting a relay to a Wi-Fi connected microcontroller like an ESP8266, you can build a connected switch that can be controlled from the web browser of any device connected to the same Wi-Fi network — all for just a couple of dollars.

Apple's latest mobile operating system for iPhones, iOS 12, was released to everyone Monday, Sept. 17, and it's the same exact build that developers and public beta testers received as the "golden master" on Sept. 12, the day of Apple's 2018 special event. Install it to start taking advantage of the 100+ features iOS 12 has to offer right now.

Due to weaknesses in the way Wi-Fi works, it's extremely easy to disrupt most Wi-Fi networks using tools that forge deauthentication packets. The ease with which these common tools can jam networks is only matched by how simple they are to detect for anyone listening for them. We'll use Wireshark to discover a Wi-Fi attack in progress and determine which tool the attacker is using.

Russian cyber disinformation campaigns have many missions, but one of particular interest is using technology to monitor, influence, and disrupt online communications surrounding culturally sensitive topics or protests. The ability to watch these events, and even filter positive or negative tweets to amplify, gives rise to the ability to execute a number of disinformation campaigns.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

In our last ARKit tutorial, we learned how to measure the sizes of horizontal planes. It was a helpful entryway into the arena of determining spatial relationships with real world spaces versus virtual objects and experiences.

Kali Linux is established as the go-to operating system for penetration testing, but in its default configuration, it's less than ideal for regular desktop use. While in many scenarios, a live boot or virtual environment can resolve these issues, in some situations, a full installation is better. A few simple changes can be made to a Kali Linux desktop to make it safer to use in this environment.

Ever notice how some augmented reality apps can pin specific 3D objects on the ground? Many AR games and apps can accurately plant various 3D characters and objects on the ground in such a way that, when we look down upon them, the objects appear to be entirely pinned to the ground in the real world. If we move our smartphone around and come back to those spots, they're still there.

The easiest way around a security policy is to find users who don't follow it. The Have I Been Pwned database identifies accounts with information breached by major third parties like Yahoo and LinkedIn. With Maltego, hackers can locate breached accounts created using company email addresses, potentially giving attackers access to a company account if the employee reuses a compromised password.

Analysis of photographs and social connections can be a huge component of social engineering. Understanding who a person is, as well as who they know, can establish links within a company. This information could be used by hackers to execute elaborate social engineering attacks.

Google Calendar is a cornerstone of the Google Suite, perhaps second only to Gmail itself. Whereas email is constantly plagued by phishing attacks, as of yet, the calendar is a relatively untapped social engineering attack vector. But it's relatively easy for an attacker to inject a meeting or event into a target's Google Calendar and use it to exploit them.

Beginners learning brute-forcing attacks against WPA handshakes are often let down by the limitations of default wordlists like RockYou based on stolen passwords. The science of brute-forcing goes beyond using these default lists, allowing us to be more efficient by making customized wordlists. Using the Mentalist, we can generate millions of likely passwords based on details about the target.

While Wi-Fi networks can be set up by smart IT people, that doesn't mean the users of the system are similarly tech-savvy. We'll demonstrate how an evil twin attack can steal Wi-Fi passwords by kicking a user off their trusted network while creating a nearly identical fake one. This forces the victim to connect to the fake network and supply the Wi-Fi password to regain internet access.

A powered-off Windows 10 laptop can be compromised in less than three minutes. With just a few keystrokes, it's possible for a hacker to remove all antivirus software, create a backdoor, and capture webcam images and passwords, among other highly sensitive personal data.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

Your home has walls for privacy, but Wi-Fi signals passing through them and can be detected up to a mile away with a directional Wi-Fi antenna and a direct line of sight. An amazing amount of information can be learned from this data, including when residents come and go, the manufacturer of all nearby wireless devices, and what on the network is in use at any given time.