Apple's latest iPhone and iPad software, iOS 15.5 and iPadOS 15.5, became available on May 16, so you can download and install it right now if you haven't already. While there aren't as many new features as iOS 15.4 and iPadOS 15.4 had, there are a few big ones in the U.S. you'll want to know beyond Apple's minuscule "About this Update" information in the "Software Update" menu.
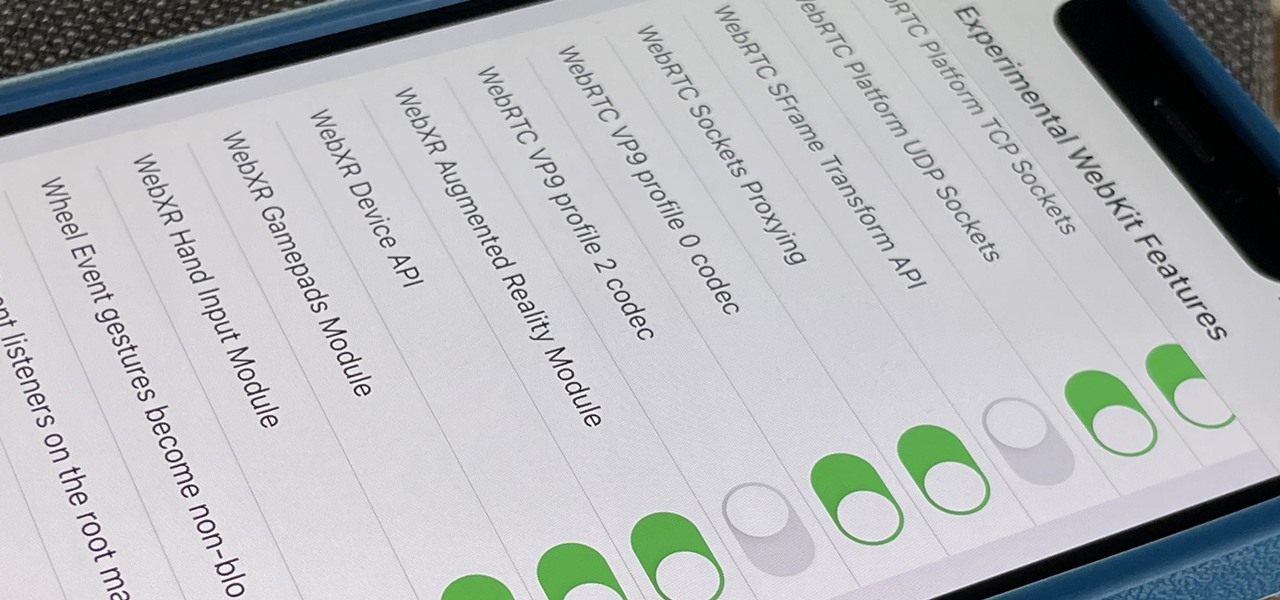
Safari's advanced experimental features give you access to new browser initiatives, upcoming web tools, element changes, behavior adjustments, and other preliminary feature tests in development by Apple. If you use them on your iPhone, you can either improve your Safari experience or wreck it. Resetting the flags provides a fresh start.

We always know roughly when Apple events are coming, but when their new product events pop up, they're always a pleasant tech refresher from the Cupertino tech giant.

When smartphones were first getting popular, apps were much more limited in scope. Because of that, it was easier to find better programs to do what was needed. Now, in the App Store alone, there are nearly two million apps for you to choose from. When you're just looking for an app that will work well for the task at hand, two million is a lot to sort through.

Apple released the second Release Candidate for iPhone on Friday, May 21. The new update, build number 18F72, comes four days after the company seeded the first 14.6 RC to developers and public testers, and two days after the first beta for iOS 14.7.

Apple pushed out the Release Candidate for iOS 14.6 on Monday, May 17. The 18F71 build includes new features and bug fixes, including an option to unlock your iPhone with Voice Control. It comes just hours after Apple announced Spacial Audio and Lossless Audio playback for Apple Music, new features that will require iOS 14.6 to run.

The era of virtual meetings has been evolving every few months, with augmented reality filters leading the charge in changing the way we interact when chatting via video streams.

Improving your experience online is getting easier every year. Browsing can be safe, easy, and boundary-less with the right VPN, and gaming online is working better than ever to connect and compete with other players.

We all know that using a VPN not only has a ton of benefits but is essential in our digital age. But did you know that you can get access to your own industry-leading VPN for life with one one-time payment? Even better, we've found an amazing deal on one right now: for a limited time, a YoData VPN: Lifetime Subscription is on sale for just $17.99. That's 69% off the regular price of $59.

Apple ProRAW, the new RAW shooting format available on the iPhone 12 Pro and 12 Pro Max, is now available in iOS 14.3. But you won't find a switch for it in the Camera app after updating your iPhone, and that's because it's an opt-in feature you have to unlock.

There's a lot of talk these days about how the iPhone 12, 12 mini, 12 Pro, and 12 Pro Max can shoot Hollywood-quality video with HDR and Dolby Vision. The video processing is really cool when it works, but as of right now, you might find its limitations outweigh its use to you. If that's the case, there's a way to turn it off.

If there's anything we've learned during 2020, it's that working and learning from home is going to shift the way we do business. With Microsoft announcing that its staff will be allowed to permanently work from home, expect more businesses to follow suit.

If you're a hacker, pentester, or any other type of Null Byte reader, and would like to create a website to showcase your services and skill set, you may not have the time or energy to do it the long way.

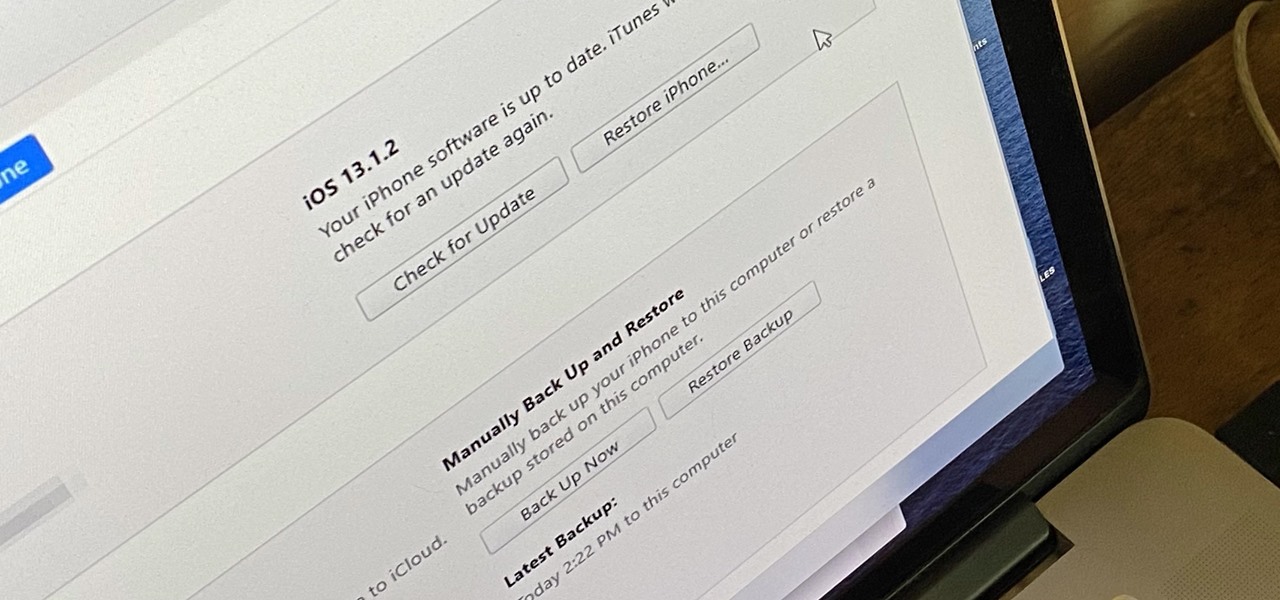
Whenever something goes wrong with your iPhone, or whenever you want to downgrade from an iOS beta back to the regular iOS release, you can restore your iPhone to your last saved state. Restoring to an iCloud backup is great but won't work in all situations. Plus, if you saved a backup on your computer, that may be the best route to take to get back all of your data.

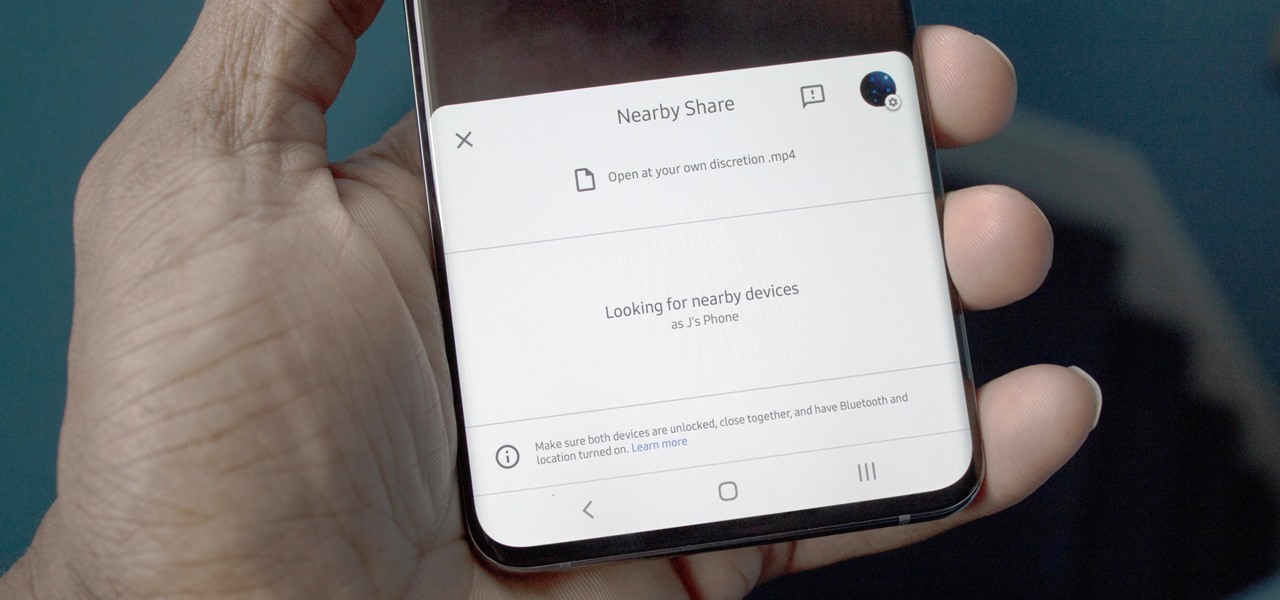
Android has finally got a proper alternative to Apple's AirDrop. With a few touches, Nearby Share lets you send files, links, and even tweets to Android, Windows, macOS, ChromeOS, or Linux. But AirDrop has not been without its share of issues, and thankfully, Google has learned from them.

Attacks against databases have become one of the most popular and lucrative activities for hackers recently. New data breaches seem to be popping up every week, but even with all of that attention, databases continue to be a prime target. All of these attacks have to start somewhere, and we'll be exploring a variety of methods to gather information on PostgreSQL databases with Metasploit.

The response to the COVID-19 pandemic means that social distancing has become the new normal. It also means that more Americans are using video conferencing to connect with colleagues working from home or friends and family in quarantine because of the new coronavirus.

Apple released iOS 13.4 to public beta testers on March 18. The update comes the same day we learned that iOS 13.4 would be made available March 24. The sixth beta is iOS 13.4's GM (golden master), even though Apple refers to it as "beta 6."

Apple released iOS 13.4 to registered developers on March 18. The update comes just hours after news broke that iOS 13.4 would hit all compatible devices on March 24. The update is the GM (golden master), which makes it the same build as the official release we expect to see on March 24, although Apple does refer to it as "beta 6" on the dev site.

When it comes to iOS beta updates, developers get their updates first, and once they do, public testers play the waiting game. Sometimes Apple releases the public version three hours later. Other times it waits 24 hours. It's a roll of the dice almost every time. As for iOS 13.4 public beta 2, it's the latter case, coming exactly one after developer beta 2.

Last week, Apple released the first iOS 13.4 beta with fun and useful new features, such as new Memoji, an upgrade Mail toolbar, and the ability to control your NFC-compatible car via CarKey. To add to that, Apple just released iOS 13.4 developer beta 2, but does the update have any more new changes to be excited about?

What could Apple be planning here? Are we going to see some revolutionary new features for the iPhone? Will we see mostly bug fixes and security patches? It's time to find out, as Apple just released the first developer beta for iOS 13.4.

One of the first steps when pentesting a website should be scanning for hidden directories. It is essential for finding valuable information or potential attack vectors that might otherwise be unseen on the public-facing site. There are many tools out there that will perform the brute-forcing process, but not all are created equally.

Along with rebranding Magic Leap 1 for enterprise customers, Magic Leap has gifted its developer community with some new toys with a tease of more to come in 2020.

UnrealIRCd is an open-source IRC server that has been around since 1999 and is perhaps the most widely used one today. Version 3.2.8.1 was vulnerable to remote code execution due to a backdoor in the software. Today, we will be exploiting the vulnerability with Metasploit, examining the underlying code to understand it, and creating our own version of the exploit in Python.

Web application firewalls are one of the strongest defenses a web app has, but they can be vulnerable if the firewall version used is known to an attacker. Understanding which firewall a target is using can be the first step to a hacker discovering how to get past it — and what defenses are in place on a target. And the tools Wafw00f and Nmap make fingerprinting firewalls easy.

Reconnaissance is one of the most important and often the most time consuming, part of planning an attack against a target.

For years, Apple's Notes app has been a reliable way to jot down important ideas, tasks, plans, and more. While there are apps on the market that advertise themselves as being more feature-filled than the stock iOS option, Apple is now giving them a run for their money. Here are 14 new features and changes you'll see with Notes in iOS 13.

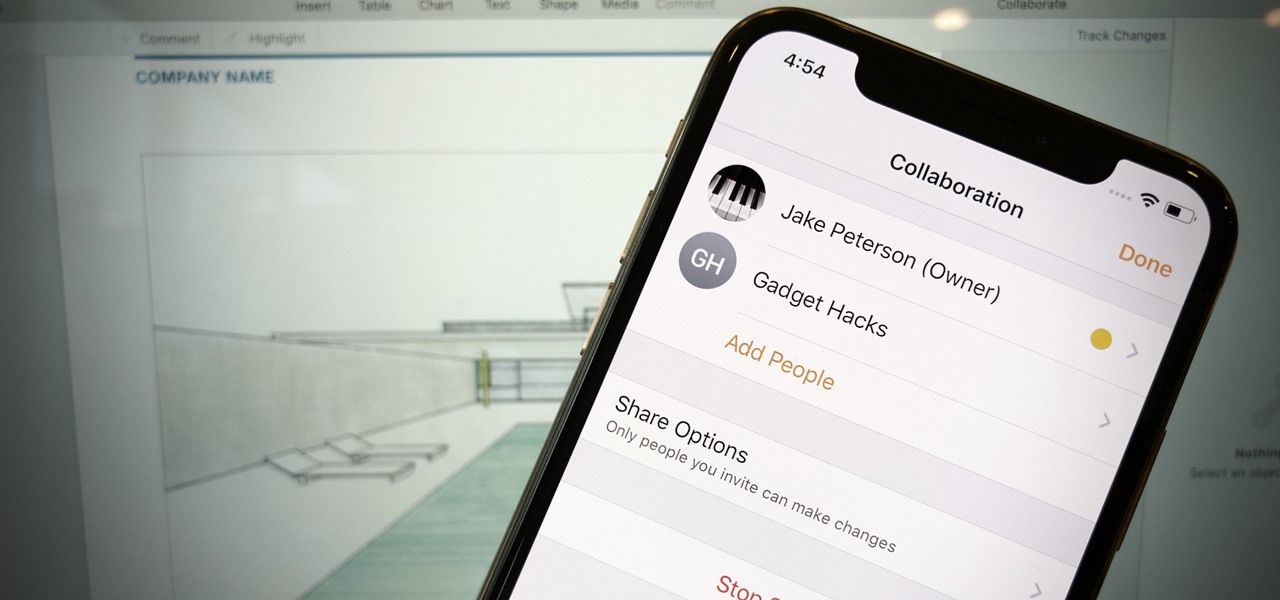
Google Docs is made for teamwork and collaboration, but Apple's iWork suite also comes with the same functionality. If you're working on a Pages document on your iPhone, and you want input from other members of your team, you can easily invite them to view, comment, edit, and more right alongside you.

Imagine a scenario where you're nowhere near your iPhone, but it's on loud, and you really need to silence it. An alarm may be blaring, notifications could be spitting out sounds left and right, and calls may be ringing. Things can get annoying real quick for whoever's around it. Plus, all that attention makes it easy for someone to find and possibly steal your iPhone. Luckily, you can quiet it down.

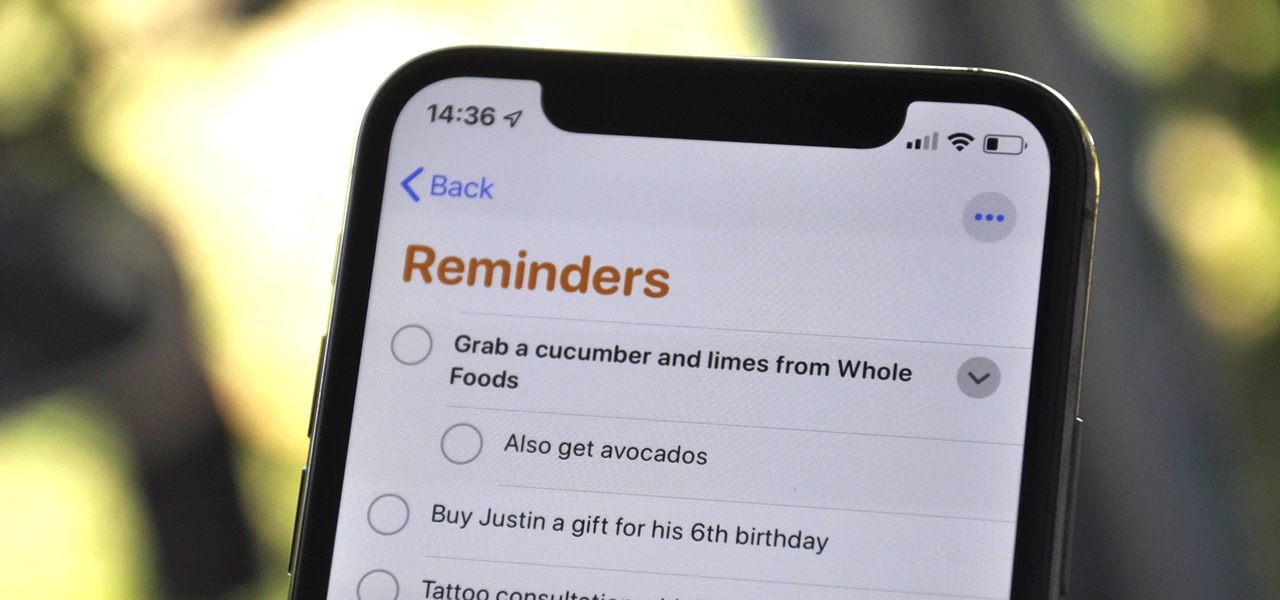
Things are a bit more organized in Apple Reminders, so the cluttered mess that it once was is no more in iOS 13. The slapped-together feel in older iOS versions was the main reason I never used it that much, but the updated version for iPhone has finally got me hooked.

The updated Reminders app in iOS 13 makes productivity a little bit more seamless on the iPhone. The overhauled user interface makes it easier to find your reminders, the new Messages integration makes it simpler to remember to-dos regarding your contacts, and the new toolbar provides shortcuts to tasks that were once clunky and confusing.

When researching a person using open source intelligence, the goal is to find clues that tie information about a target into a bigger picture. Screen names are perfect for this because they are unique and link data together, as people often reuse them in accounts across the internet. With Sherlock, we can instantly hunt down social media accounts created with a unique screen name on many online platforms simultaneously.

UAC is something we've all dealt with on Windows, either as a user, administrator, or attacker. It's a core feature of the Windows security model, and for the most part, it does what it's supposed to. But it can be frustrating as a hacker when attempting privilege escalation, but it's easy enough to bypass UAC and obtain System access with Metasploit.

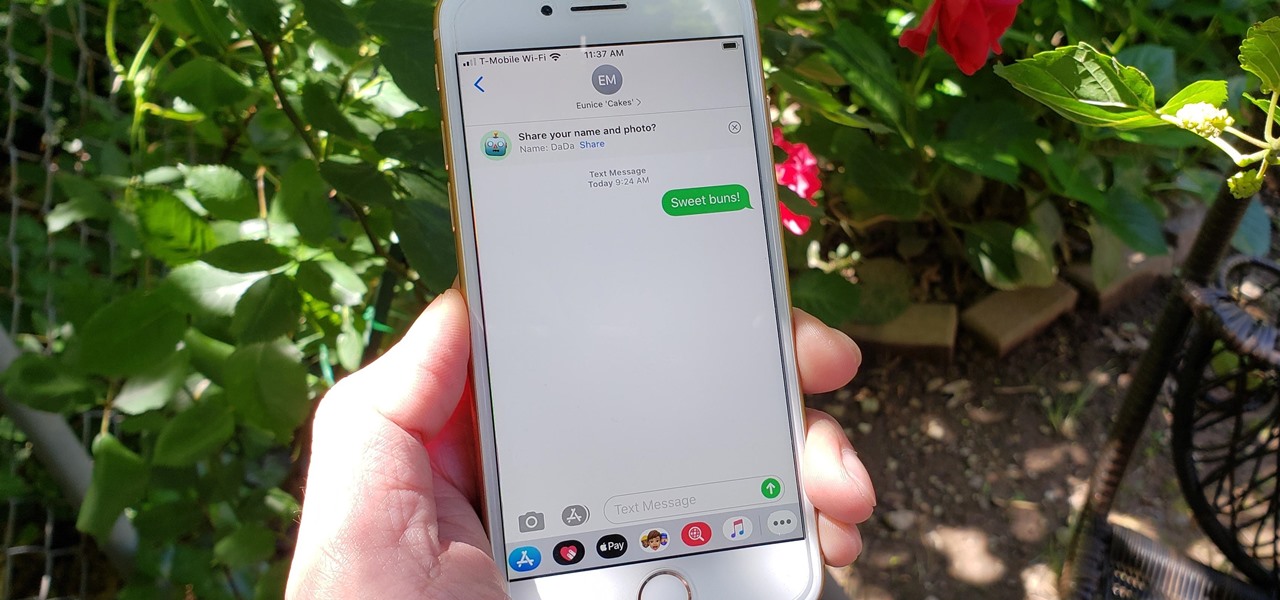
For quite some time, popular messaging apps such WhatsApp and Skype have let you set a profile picture along with a display name to make you more instantly identifiable to loved ones and colleagues. Apple has finally caught up with this fad in iOS 13. That means you can set a custom name and profile image within iMessage so others can quickly view who's messaging them at a glance.

An incredible amount of devices use Bluetooth or Bluetooth Low Energy to communicate. These devices rarely have their radios switched off, and in some cases, are deliberately used as trackers for lost items. While Bluetooth devices support MAC address randomization, many manufacturers do not use it, allowing us to use tools like Bettercap to scan for and track Bluetooth devices.

The Windows 10 desktop and microphone can be livestreamed without using Remote Desktop Protocol (RDP) software and without opening any ports on the target computer. A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in real time no matter where they are. Hackers are watching and listening, and there are few ways to protect yourself.

Canary tokens are customizable tracking links useful for learning about who is clicking on a link and where it's being shared. Thanks to the way many apps fetch a URL preview for links shared in private chats, canary tokens can even phone home when someone checks a private chat without clicking the link. Canary tokens come in several useful types and can be used even through URL shorteners.

It's easy to forget just how cool face filters are. Augmented reality has come a long way, and apps like Instagram now offer a suite of impressive effects to play with, but some of the best ones aren't easily found. There is a treasure trove of exclusive, custom face filters that are unavailable to the general public, but not at all inaccessible — you just need to know the trick to getting them.

Directory traversal, or path traversal, is an HTTP attack which allows attackers to access restricted directories by using the ../ characters to backtrack into files or directories outside the root folder. If a web app is vulnerable to this, an attacker can potentially access restricted files that contain info about all registered users on the system, their permissions, and encrypted passwords.