Coverage for the 88th Academy Awards, aka the Oscars, will air live this Sunday, February 28th at 4 p.m. PT (7 p.m. ET). The ceremony itself, hosted by Chris Rock, is set to begin at 5:30 p.m. PT (8:30 p.m. ET).

Instead of suffering through long, dull meetings with your supervisors and coworkers, you can turn those office table sessions into your very own psychological experiment.
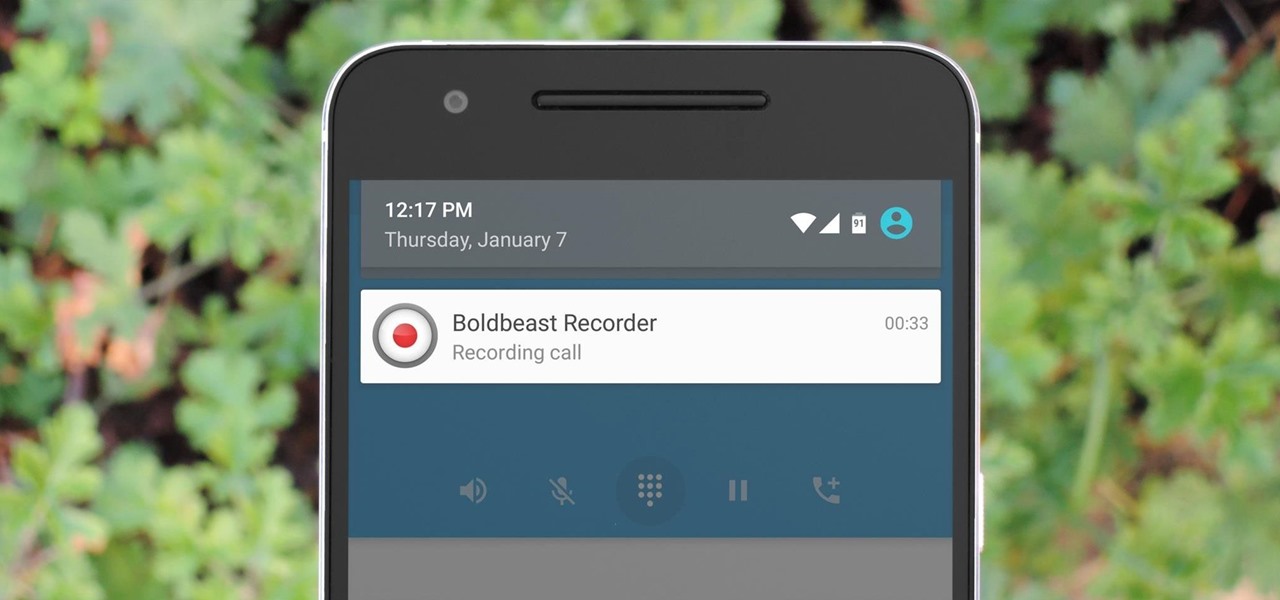
There are plenty of legitimate reasons that you might want to record a phone conversation. Let's say you operate a business and take orders over the phone, and you don't want to miss an item. Or perhaps you need to jot down some notes from a recent conference call, and things were just happening too quickly in real time.

Brand loyalty is one of the main factors behind our decision to choose a particular mobile device, but it doesn't have to be the entire equation. Educated consumers know that certain devices simply fit their budget and usage better than others, which means you can't always let a logo dictate what kind of phone or tablet you buy.

My first ever post on here was 'Keeping your hacking identity secret' and it did very well, and its not something I see here on null byte. So read along.
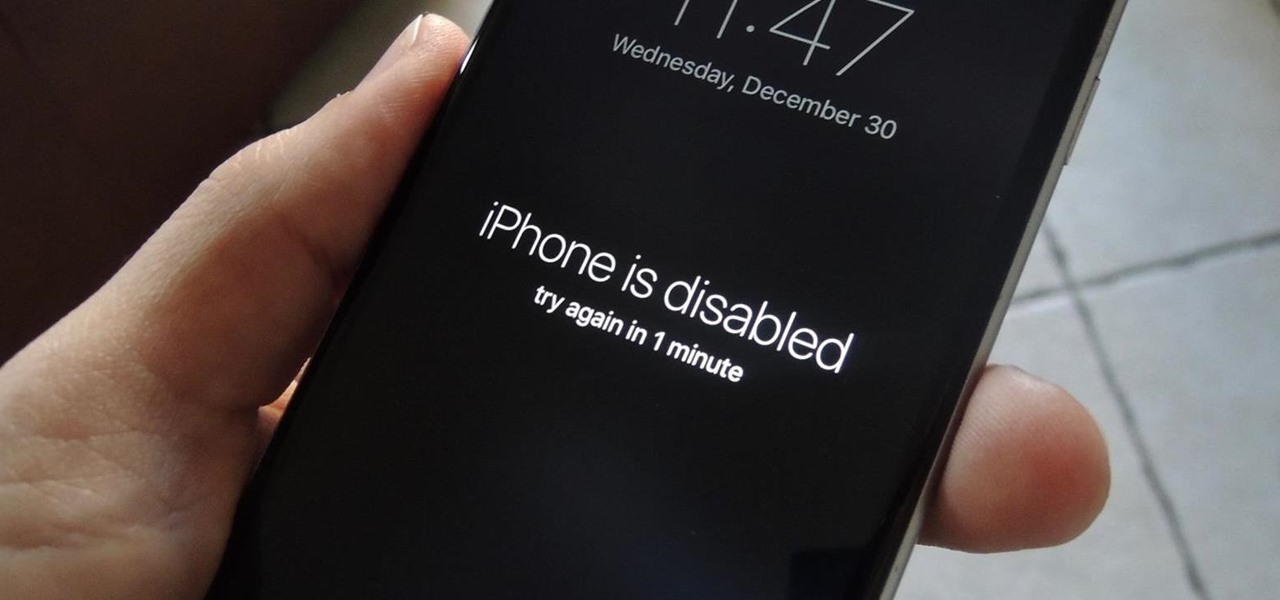
With Touch ID on iOS devices, it's a little more difficult to lock yourself out. However, it can still happen if you don't use it, have a busted fingerprint scanner, or use an older device that doesn't have Touch ID, which means you're passcode dependent (unless you have zero lock screen security).

Smartphones are almost always connected to the internet, so it stands to reason that they can be hacked remotely. Or perhaps a jealous boyfriend or girlfriend got hold of your device physically, in which case they could've potentially installed a keystroke logger, a virus, or any other type of tracking app to spy on you.

While password cracking and WPS setup PIN attacks get a lot of attention, social engineering attacks are by far the fastest way of obtaining a Wi-Fi password. One of the most potent Wi-Fi social engineering attacks is Wifiphisher, a tool that blocks the internet until desperate users enter the Wi-Fi password to enable a fake router firmware update.

Like the majestic mountain structure it's named after, Apple's latest version of OS X, El Capitan, goes a little deeper to expand on the foundation laid by Yosemite. While the update may not be as monumental as some have hoped, it is an improvement and includes tons of useful new features you don't want to miss.

Nothing gets me functioning in the morning better than strong coffee. And if I'm going to start my day with a dreaded workout, that steaming cup of caffeine is the exact motivation I need to get going. Although coffee might not seem like the best beverage to drink before hitting the gym, it actually has a few hidden benefits over water that may surprise you.

In general, smartphones and cars don't mix—but this is mainly because you have to take your eyes off the road to poke around on your handheld gadget. In reality, the only difference between your smartphone and your car's FHWA-approved infotainment system is that the latter is mounted in a fixed position and has an oversized interface that makes it easy to use without looking away from the road.

I've been involved in the Android scene for a very long time and have grown to develop a love/hate relationship with CyanogenMod. While I do like the stability they offer in their custom ROMs, they don't always include the flashy features on top of their vanilla Android base.

When most people think of "gaming computers," they're probably thinking of Windows-based PCs. They offer a huge variety of devices with better equipped software and hardware for a cheaper price, and there are more available games than there are for OS X-based systems.

Texting has become the king of communication—gone are the days where everyone called each other. These days, it's down-right weird when someone calls first. Whether it be on a phone or on a computer, SMS and MMS messages are the most common way people keep in contact, so why not make sure your app of choice is the best possible one out there?

With the amount of time we spend glued to our smartphones, they could be considered a second job (if only we got paid). I spend a large part of my day scrolling through Reddit, Facebook, Instagram, and countless other apps, and burn through hours and hours without even noticing.

Is your Mac starting to feel messy and sluggish after using iOS 8 on your iPhone every day? Even with all of the iOS-friendly features built in to Mac OS X Yosemite, your Mac can still feel kind of "old" in comparison to an iOS device—but it doesn't have to. Using the tips and tricks below, you can easily make your Mac desktop or laptop look and feel like iOS 8 in no time.

Throwing a party means making sure everyone has fun, but that pursuit can quickly get out-of-hand. Before you know it, you're once laid back get-together has received so many RSVPs that it becomes obvious you're throwing the party of the century. With an over-abundance of beer and an inflated guest list, your newly-formed epic reputation must live up to the hype.

Welcome back, my greenhorn hackers! As hackers, we often take for granted that nearly all of our hacking tools and operating system are free and open source. I think it's important to examine a bit of background on how we arrived at this intriguing juncture in the history of computer software. After all, we pay for nearly all of our other software (Microsoft, Adobe, etc.) and nearly everything else we use in life, so how is it that Linux and all our hacking tools are free?

When you think of an online music service nowadays, Spotify is probably near the first that come to mind, and for good reason. Being able to create, share, and take all of your playlists anywhere, across all of your devices, is something that I couldn't live without. Unfortunately, nothing this good is free, and with Spotify Premium, users of their free service are left with very limited features when streaming on their mobile devices.

Apple prides itself on simplicity, but the company makes downloading video and music files onto your iPad or iPhone an overly complicated process, requiring iTunes and/or iCloud.

While most of us don't think twice about dragging a pattern or using Touch ID to open our phones, or entering a password in for our email and bank accounts, these features are there to protect some of our most private information. Only problem is, they don't do a good job of it.

Only a handful of food products are impervious to spoilage—dried rice, salt, sugar—but even among those, honey is unique in that it remains edible without any preparation necessary. It's like this: if you came across honey in an Egyptian tomb, as archaeologists have, you could taste it and never guess it was thousands of years old.

Without a comprehensive root method for all Android phones and tablets, a device-specific approach is needed. And since we always cover new rooting methods for all the popular phones here at Gadget Hacks, we've built this always-updated guide to rooting many mainstream Android devices.

Welcome back, my apprentice hackers! In this series on password cracking, I have been attempting to develop your skills in the age-old art of password cracking. Although it might seem like a simple and straightforward exercise, those of you who have attempted password cracking know that there are many subtleties to this art.

When you misplace your Android device, finding it with the Android Device Manager, or even better, Whistle Me, can help you find it no problem. But what about when your phone is not just hiding under the couch cushions? Your worst nightmare just came true. It's officially gone.

With apps and games getting bigger and more memory-hungry every year, storage space is at a premium. High-definition videos and photos of innumerable pixels certainly don't help the matter, either.

You probably already know by now that a custom Android ROM can change your user experience and give you what feels like a new OS on your device, and there's no shortage of them out there to try out.

Welcome back, my hacker apprentices! Several of you have written asking me how you can check on whether your boyfriend, girlfriend, or spouse is cheating on you, so I dedicate this tutorial to all of you with doubts about the fidelity of your spouse, girlfriend, or boyfriend.

The holiday season is almost over, bringing the year to an end, and what better way to end it than with some tonsil hockey from the dime across the room on New Year's Eve?

Welcome back, my greenhorn hackers! I recently began a series on scripting and have received such positive feedback that I'm going to keep this series going. As I've said before, to graduate from the script kiddie to the pro hacker, you'll need to have some scripting skills. The better you are at scripting, the more advanced your hacking. Ultimately, we are leading up to developing the skills to build your own zero day exploits.

It's rare that a developer listens to the wishes of the masses, but that's exactly what CyanogenMod has done with their new CyanogenMod Installer, which automates the entire ROM installation process on your HTC One or other Android device. Previously, upgrading from the stock HTC One ROM to CyanogenMod required an unlocked bootloader, a custom recovery, the latest CM version, and Gapps. Let's be honest—unlocking the bootloader is a pain the ass, and probably the only reason stopping most peop...

There are few apps on my iPhone that I visit on a daily basis, and one of them is Drippler, the discovery and news app that tells you everything you need to know about your device.

Apple may have made Mavericks more accessible to Mac users everywhere at the fair price of zero dollars, but unfortunately, they made it trickier to create a bootable install drive of the Mac OS X 10.9 operating system.

For over 20 years, a tiny but mighty tool has been used by hackers for a wide range of activities. Although well known in hacking circles, Netcat is virtually unknown outside. It's so simple, powerful, and useful that many people within the IT community refer to it as the "Swiss Army knife of hacking tools." We'll look at the capabilities of Netcat and how the aspiring hacker can use it.

The integration of technology into automobiles is becoming more and more widespread each year. Tesla's Model S features a 17" display in the middle of the dash with navigation, music control, and even an Internet browser. Mercedes is working on incorporating Google Glass into their cars. Even Honda's 2014 Accord LX (their lowest trim level), boasts Pandora music streaming, Bluetooth connectivity, and a rearview camera and display.

Why can't I see who is stalking my Facebook profile?

The iPod changed the music and electronics industries when it was first introduced way back in 2001. It is credited with ushering in the age of "connected devices," and has held a huge market share of around 70% for years. At the height of its popularity, the iPod made up almost 50% of Apple's revenue. Now that the smartphones and tablets we use every day have the ability to store and play music, the iPod's glory days are over. Nevertheless, there are millions of people who still use them, an...

Facebook just released its new "home on Android" last Friday, appropriately called Facebook Home. Taking a cue from Amazon's Kindle, Home serves as an "operating system" that runs over Android.

Today's project will show how you can convert your laptop, smartphone, or tablet computer into a makeshift projector—just in time for March Madness! It's super cheap to build, and can add a little bit of creative fun to your next sports party.