In this video we learn how to alter your IP address. To do this, you will need to go to this website: http://shadysurfing.t35.com. After you go here, you will be directed to the site, click on the left hand side toolbar to display your IP address. Then, go to the web based proxy and search for the site you want to visit. From here, the site will pop up under a different IP address. You can use there at school or at work, whenever you don't want the information for where your IP address has be...
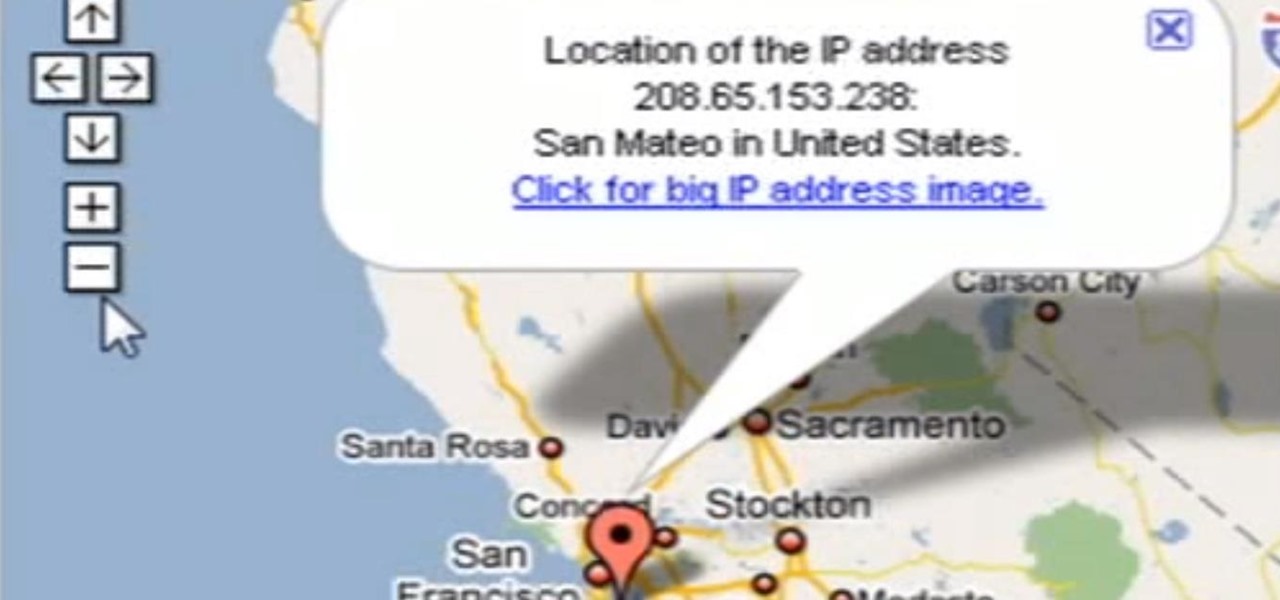
Need help tracing an IP address to a location? Well, Tinkernut has a clear and effect way to help out.
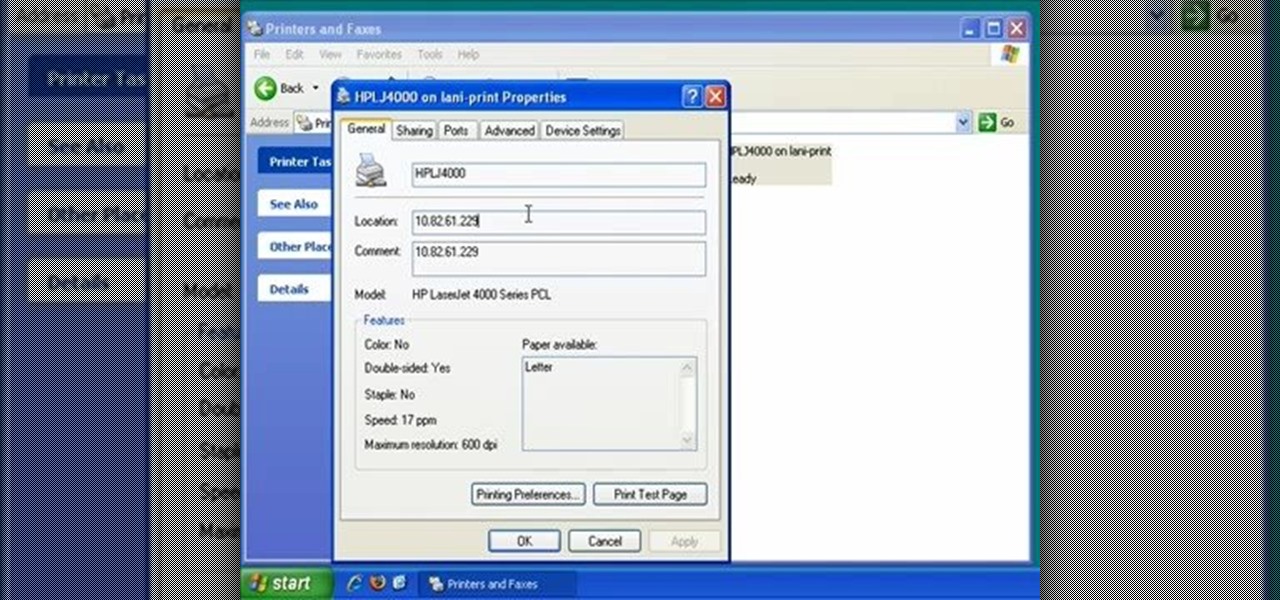
In this video, we learn how to find the IP address of a printer on your computer. Before you begin, make sure you start on your main desktop. First, click on the "start" menu, then click on "control panel" and last click on "printers and faxes". Once you're in there, right click on the printer you want to see the IP address for and then click on "properties". After this, you will find the IP address under the "location" section. You can look up the IP address for all the printers in your netw...

Most packages sent to you via delivery services include a tracking number that allows you to track it from the creation of the shipping label all the way to your doorstep. The U.S. Postal Service includes tracking information with many of its mailing services, but not for first-class mail or periodicals. Luckily, there's a workaround to that limitation that you can set up pretty quickly.
Apple seeded the official version of iOS 13 to compatible iPhones on Sept. 19. Since then, we've seen two major updates — iOS 13.1, which, by our count, introduced 22 new features, and iOS 13.2, which also added 22 new features. Today, Dec. 10, Apple introduced the third major update: iOS 13.3.

When joining a new network, computers use the Address Resolution Protocol to discover the MAC address of other devices on the same network. A hacker can take advantage of ARP messages to silently discover the MAC and IP address of network devices or actively scan the network with spoofed ARP requests.

Hackers rely on good data to be able to pull off an attack, and reconnaissance is the stage of the hack in which they must learn as much as they can to devise a plan of action. Technical details are a critical component of this picture, and with OSINT tools like Maltego, a single domain name is everything you need to fingerprint the tech details of an organization from IP address to AS number.

Backdooring a powered-off MacBook is easy when a few minutes of physical access is allowed. That attack works well if the hacker also shares a Wi-Fi network with the victim, but this time, I'll show how to remotely establish a connection to the backdoored MacBook as it moves between different Wi-Fi networks.

In previous tutorials we have encountered these things called pointers and addresses but we still don't know what they really are. Let's learn a bit more to clear things up.

Unless you've been living under a rock with no internet connection, it's safe to say that you've heard of the Heartbleed flaw that allows practically anyone with the right knowledge to steal your personal information, such as passwords, credit card numbers, and e-mail addresses using OpenSSL.

If you're with AT&T and need to change wireless-user information, you can do it easily through the business mobility online customer portal, AT&T Premier. Whether you're needing to change email addresses, phone numbers or physical addresses, this is the place and way to do it.

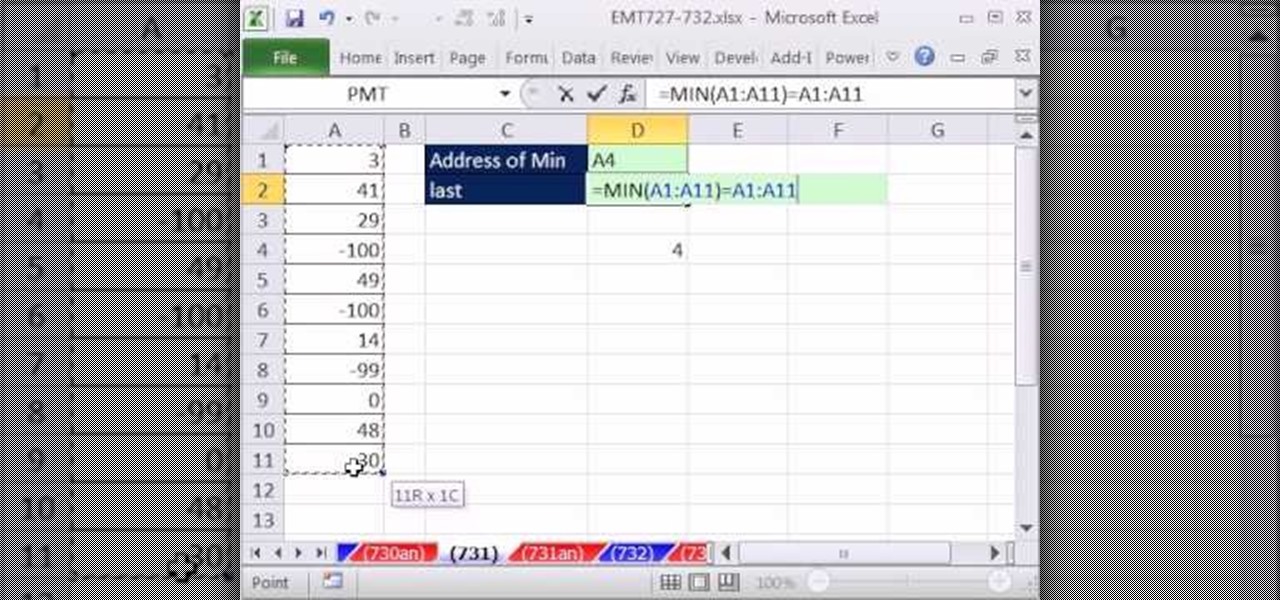
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 730th installment in their series of digital spreadsheet magic tricks, you'll learn how to create a formula that will retrieve the cell address of the minimum value in column. To accomplish this, you'll use the ADDRESS, MATCH, INDEX, MIN, ROW and LOOKUP functions.

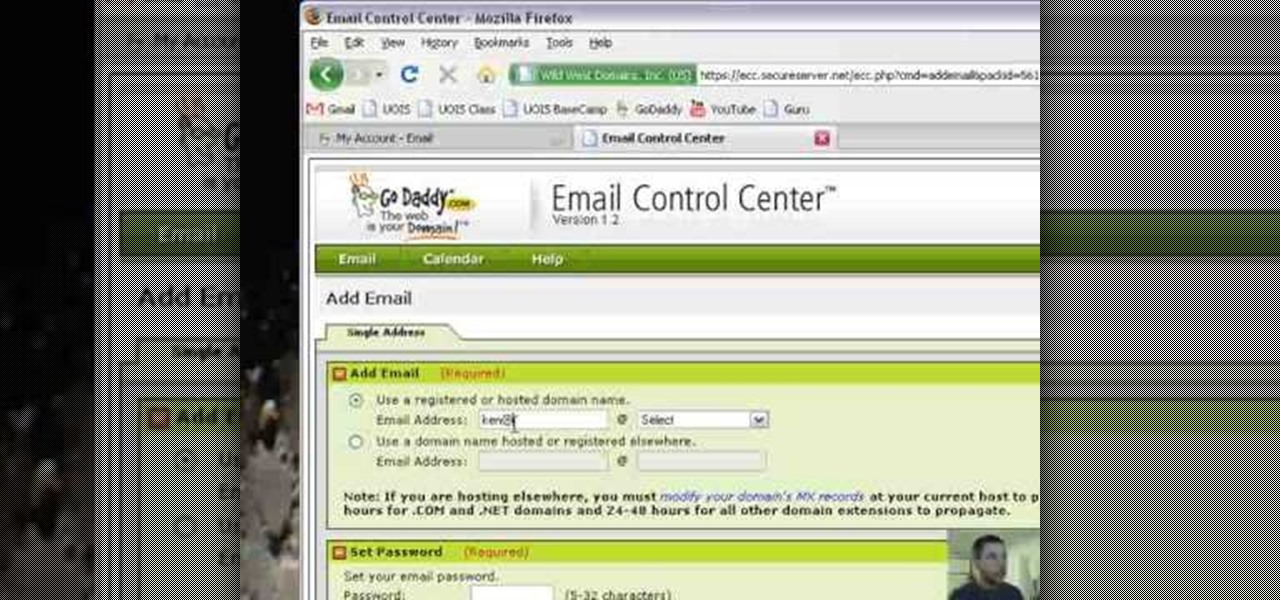
Want to set up a custom email account for a domain hosted by GoDaddy? It's simple. So simple, in fact, that this free video guide can present a complete overview of the email address creation process in just over three and a half minutes' time. For complete instructions, and to start using your own custom email addresses, watch this helpful how-to.

New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 363rd installment in their series of digital spreadsheet magic tricks, you'll learn how to create an array formula using the ADDRESS, MIN, IF, COLUMN & ROW functions that will return the address of the first non-blank cell in your Excel spreadsheet.

Here you will see how to add a contact to the address book of a Nokia N97. Follow these steps to add a contact to your Nokia M97's address book: From the home screen, tap the "Contacts" icon and then tap "Add New Contact". Enter in the contact information and tap "Done". Tap "Exit" to return to the home screen. To set a contact as one of your favorite contacts, tap "Add to Favorites", and select the contact you wish to add as a favorite. Tap "OK" You can also do things such as add a called ID...

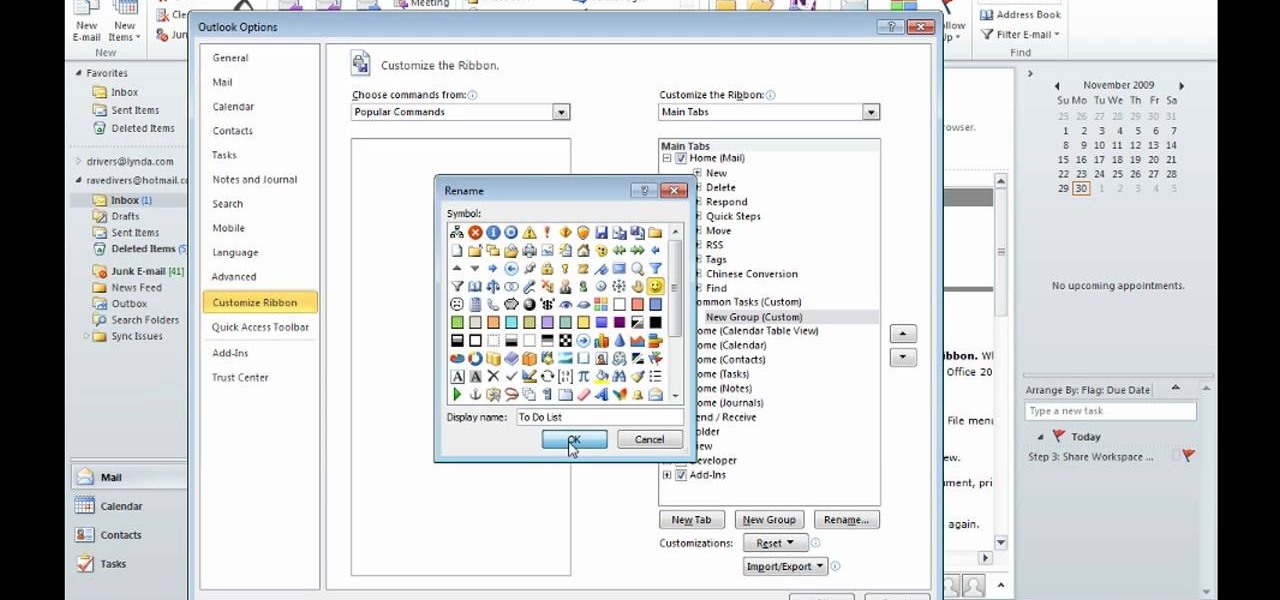
After you launch Outlook 2010 in your computer, you will see the Ribbon strip immediately in the main window. The button for writing a new e-mail is separated from a button for creating new items in the calendar, contact list or task manager. An independent Quick Steps section offers functions allowing you to move a message into different folders, to save it into a calendar as a meeting reminder, to quickly forward it to a chosen person or to more people and to forward it with a FYI note. If ...

This video is provided by "Betty Sell" from AAA travels. In this video she tells about the international travel and also about the important documents to be carried while carrying out an international travel, that is the international driving permit, commonly called as an IDP. It's very important to carry an IDP while traveling overseas because an IDP acts as an important recognizable form of photo identification which helps us to communicate with foreign authorities. To get more information ...

You love your iPhone and you can't live without it, but it's lacked the basic ability to cut, copy, and paste across multiple apps. With Apple's OS 3.0 upgrade, you can do it all with just a few taps. Watch this Howcast guide to learn how to cut, copy, and paste on your iPhone.

Wouldn't it be great if we could all enjoy the music, photos and movies on our home computers even when we're not home? Some would think it a luxurious feature, but it's totally possible for anyone who has Windows 7 and an internet connection. See how!

New to the Ubuntu Linux distribution and interested in setting up an address book for to keep track of your contacts? In this how-to, you'll learn how to make maximum use of the address book built into the Evolution email client. Take a look!

Check out this video to learn how to search more effectively in the Google Chrome browser. This video will explain how to manually enter keyword searches in Google Chrome and Chromium, which will allow you to search using any engine from the address bar.

Your manuscript is complete, and you have a list of your favorite agents and a strong query letter... but how do you properly address letters to agents? You neither want to be too formal nor too casual - strike the perfect balance.

In this clip, you'll learn how to reinstall an accidentally-deleted system application like TextEdit, Preview, iCal, Address Book or QuickTime without reinstalling OS X. With a little know-how, it's easy. So easy, in fact, that this video guide can offer a complete overview of the process in a matter of a few minutes. For more information, including a complete demonstration and detailed, step-by-step instructions, watch this home-computing how-to from MacMost.

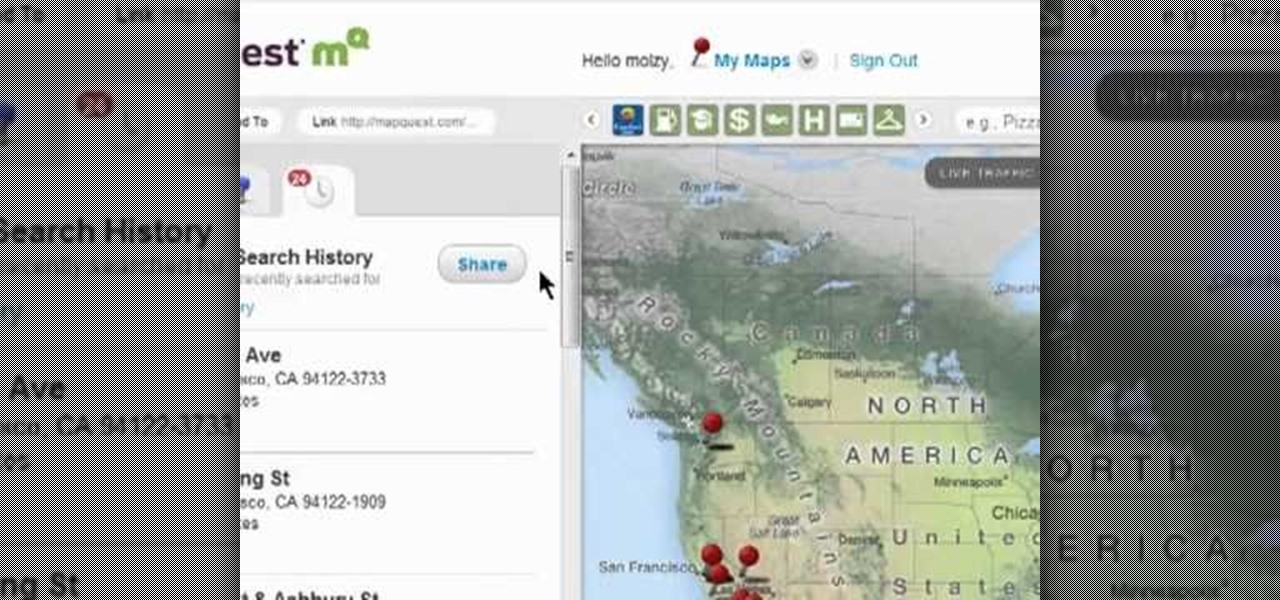
In this clip, you'll learn how to view the list of your previously searched addresses on MapQuest Maps. It's easy. So easy, in fact, that this home-computing how-to can present a complete, step-by-step overview of the process in about two minutes. For more information, including detailed, step-by-step instructions, take a look.

Need some help figuring out what your IP address is? It's easy. And this brief video tutorial from the folks at Butterscotch will teach you everything you need to know. For more information, including detailed, step-by-step instructions, and to discover your own IP address, take a look.

In this tutorial, Brian teaches us how to make your wireless network secure. First, go to the start menu, then go to run and type in "cmd", then type in "iconfig /all". Now a new window will pop up and you will look for the default gateway. Find the IP address to log onto the routers you have. Now, type in your IP address into your address bar on your internet browser. You will be asked to log into your account with your password and user name, which you can find at the manufacturers website....

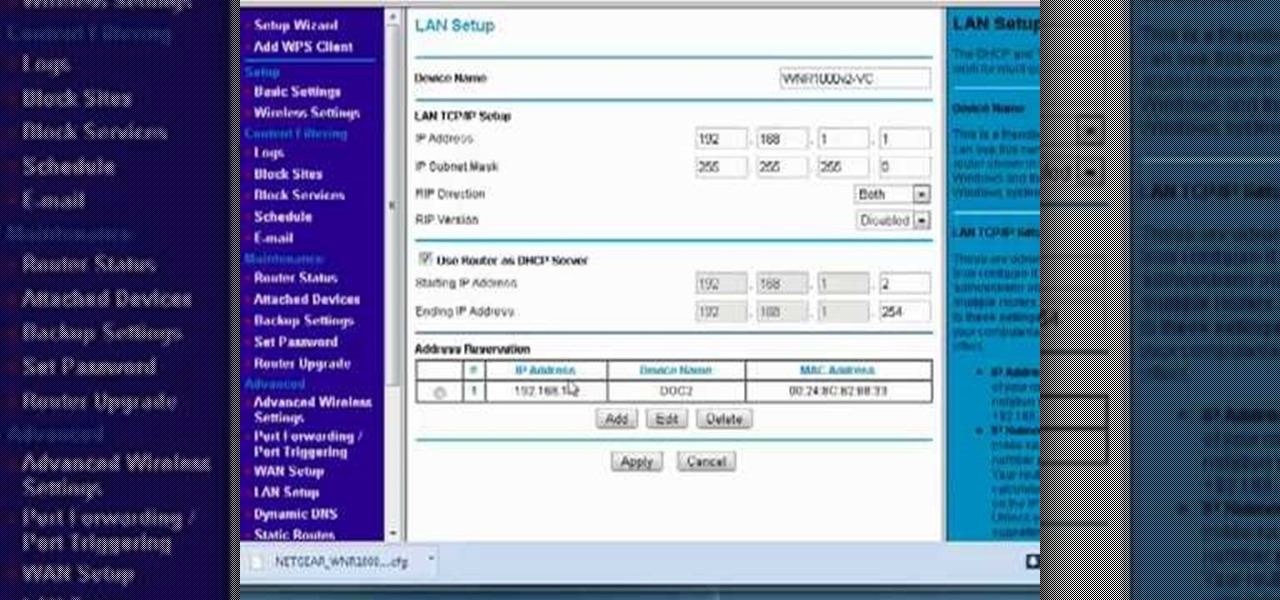
Interested in reserving a specific IP address on your Netgear wireless router? This clip will show you how it's done. It's simple! So simple, in fact, that this home-computing how-to can present a complete, step-by-step overview of the process in just over three minutes. For more information, including complete, step-by-step instructions, take a look.

In this video tutorial, viewers learn how to get more room in a web browser. Users will need to use the Mozilla Firefox web browser. Begin by going to the Firefox add-on website and search for "status address bar". Then click on Add to Firefox to install the add-on. Once installed, any link that is moused over will appear in the address bar. This means that users are able to hide the address bar clicking on View and deselecting Status-bar. This video will benefit hose viewers who use the Mozi...

How to Use COD4 Cracked Servers.

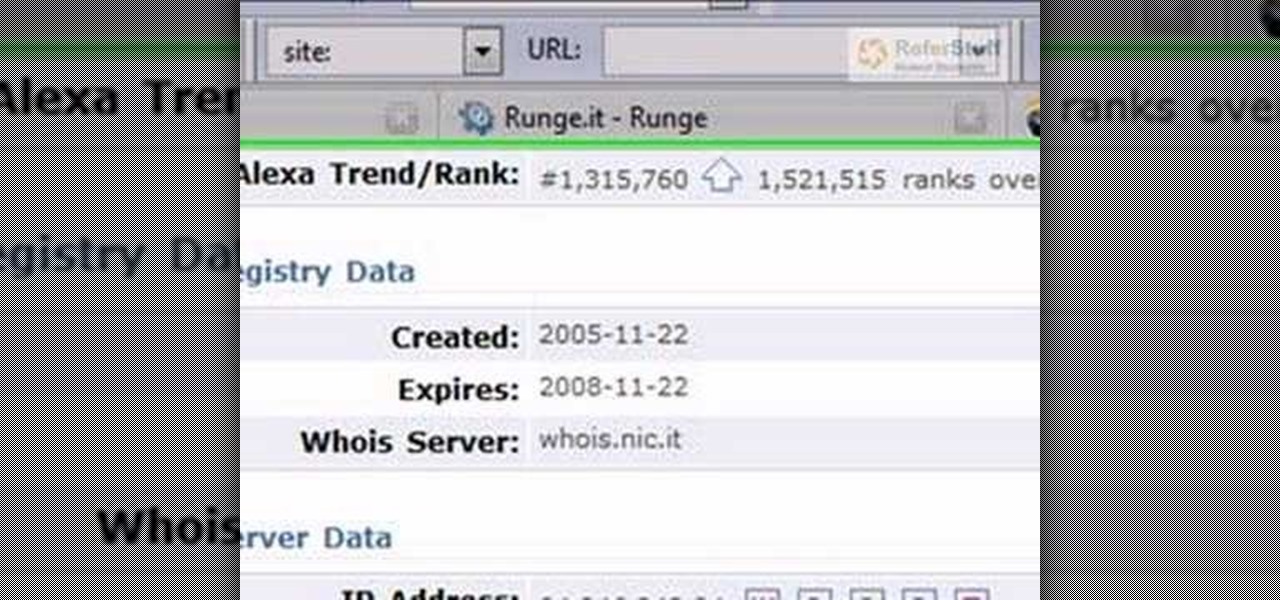
In this video from richardfallah we learn how to track a scam email. You can tell a scam from an email that looks a bit funny. So if it's an email that looks like it's from Bank of America, you might see a link to click that actually would take you to another site which is an exact clone of the Bank of America website, but it has a different web address. This is NOT Bank of America! They will try to steal all of your information if you type in your personal information. Whois is a great tool ...

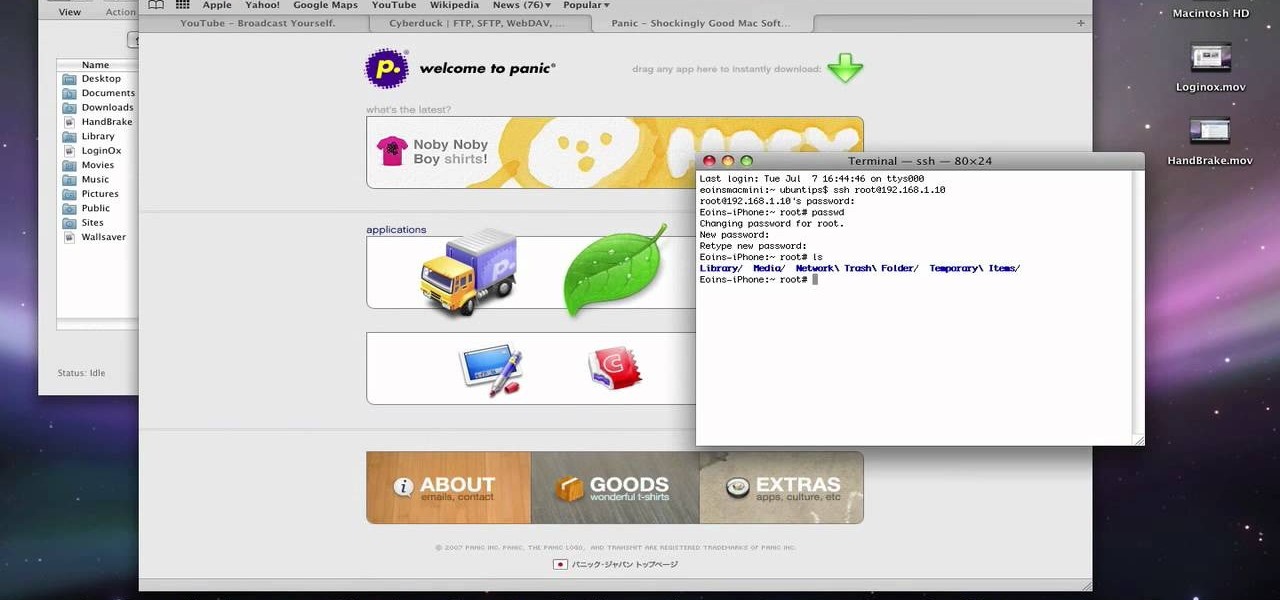
This video describes about accessing an iPhone in Ubuntu using open SSH, cyber-duck, Netatalk. For accessing using SSH, make sure your iPhone's Wi-Fi connectivity is on. Now open your terminal and type "SSH root@'address'". Here address refers to the IP address of your iPhone. You have to type a password to access the iPhone contents. Once you are authenticated type "ls" and you will be shown with the contents of the iPhone. The second method is using cyber-duck. In it, choose SFTP as the con...

CC, which stands for "carbon copy", is a familiar phrase in email, but can also be used in business letters and legal documents. This can be especially useful for letters you want to spend up a company or organizational chain, letting each recipient know exactly who else received the same document.

Learn to create a script in Windows XP that will find the IP address of a network PC.

One of Apple's most prominent iOS 16 features lets you unsend iMessages, but those aren't the only things you can take back. Your iPhone's Mail app also has the Undo Send feature, and unlike the Messages app, you can even customize the amount of time you have to stop an email before it's too late.

You may not want to disable notifications for the Mail app entirely on your iPhone since you could miss essential emails when they come in. But you can at least silence conversation threads on an individual basis. Doing so won't mute all conversations from the same sender, only the thread you select. Plus, it works for group email threads where things can get chaotic.

In the previous article, we learned how to set up our VPS, configure our PHP server, and developed an in-depth understanding of how the payload works. With all that taken care of, we can get into disguising our payload to appear as an image and crafting the note in the greeting card being delivered to our intended target.

After numerous scandals like the Equifax data breach and the 2016 US election, cybersecurity has become a significant issue for Americans. Unfortunately, anytime we use our devices, we're open to a cyber attack — especially when we browse the web. However, there are ways that we can make it harder for hackers and data miners.

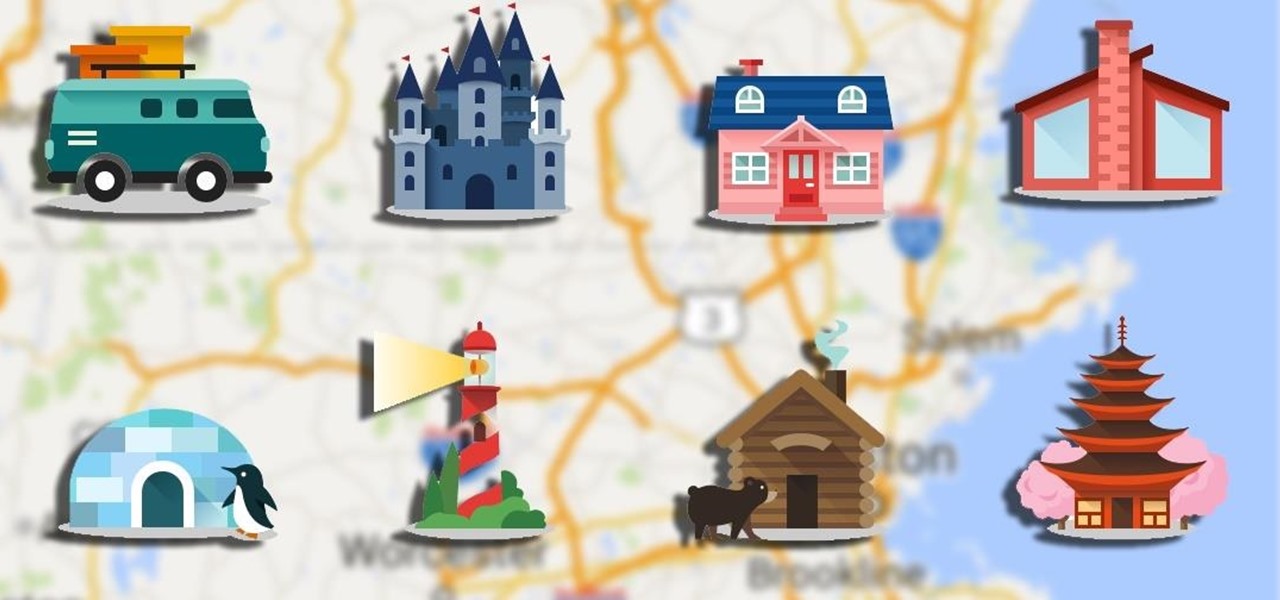
If you're using an up-to-date version of Google Maps on your Android device, there's a little-known feature you can use to apply stickers to saved places, making them visually easier to find while you're looking at the map.

In most cases, when the free trial of software is over, that's it—you're left to either pay for it or find an alternative. But what happens if the trial wasn't long enough to sell you on the product? It'd be nice if there was a way to test it out again without having to whip out your credit card.

Most people have multiple email addresses these days. Gmail is one of the more popular services, but did you know you can access your Gmail account using the Mac OS X mail program? Not only is it possible, but it is incredibly easy!