
How To: Copyright a book
You've written the great American novel, and you want to make sure that your story stays yours. Register your copyright and preserve your intellectual rights. In this video, learn how to copyright produced material.


You've written the great American novel, and you want to make sure that your story stays yours. Register your copyright and preserve your intellectual rights. In this video, learn how to copyright produced material.
The days of Skype 2.8 for Mac are over! Mac users can now rejoice and make calls with ease using the new beta version: Skype 5.0 for Mac OS X (available here). It was well worth the wait, with a revamped look and feel that simplifies navigation and provides a more Mac-like experience.

In this video tutorial, viewers learn how to read Google email offline. Begin by logging onto your Google account. Then click on Settings and select the Labs tab. In the Offline headline, click on Enable. To not grab all your emails, go to the Offline tab and select which messages will be synchronized with your computer, based on labels and time frame. This video will benefit those viewers who use Google mail, and would like to learn how to read their emails offline in case their internet con...
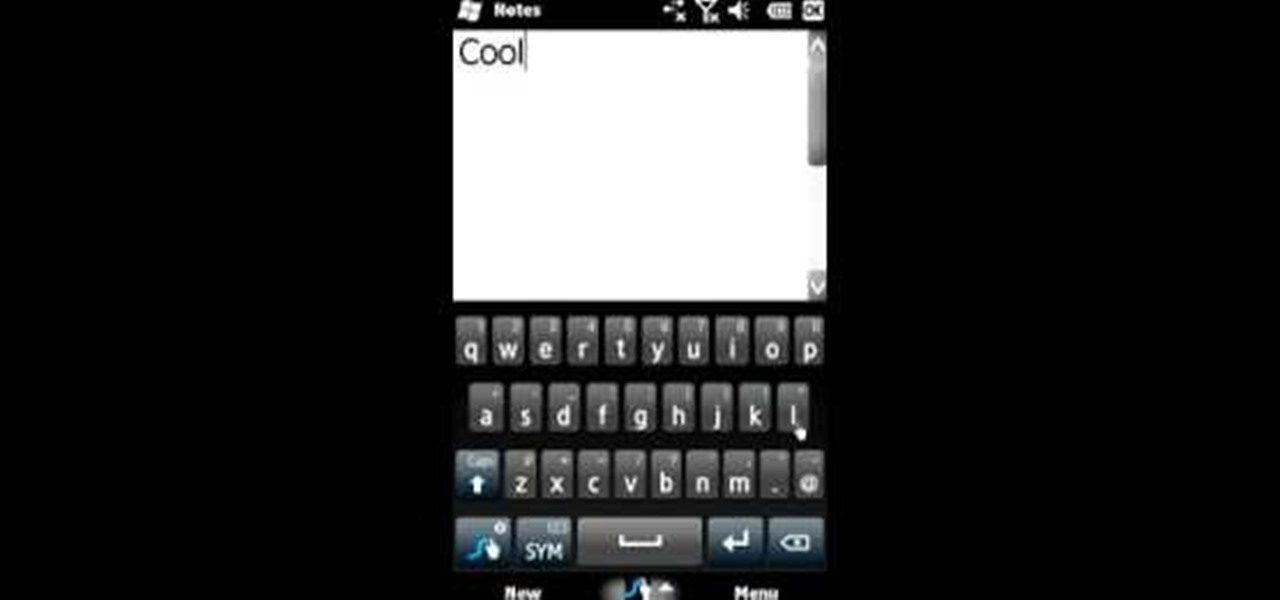
Using Swype - the new lightening fast way to text message from your cell phone - and need to type a word like "juggle" or "bubble" or something else with a double letter? No problem! In this tutorial, from the creators of the Swype app, learn how to add words like these to your texts and e-mails with ease.

In this Electronics video tutorial you are going to learn how to magnify to edit text on an iPhone. This video is a part of a series of tips on iPhone finger tips. This is very simple and easy to do and takes practically no time to complete. If you wish to add something to a list or change an email, go to the springboard and click on the ‘mail’ icon. Then scroll and find the text you want to edit. Now simply touch and hold your finger on the text. This will bring up the magnifying glass. Now ...

Want to disguise your URLs so that they appear suspicious? In the style of websites such as Tiny URL that take your original URL and give you a shortened one to post on your blog or twitter feed, Shady URL takes your original URL and gives you one that might convince people not to click it. Go to Shady URL and paste the URL you wish to disguise. Click submit, and on the next page it will give you a URL that looks, well, shady. It might include something about a mail order bride or an investme...

Taking screenshots in Windows isn't as easy as taking screengrabs in Mac OS X, but Microsoft sure is trying to resolve this issue. Their idea -- Snipping Tool. The Snipping Tool is available for both Windows Vista and Windows 7 operating systems.

When you're a Windows OS user it's very easy to send out attachments on emails as .doc documents, made in Microsoft Office or Excel. But just because you're a Windows user doesn't mean your friend or coworker is. Or say that you're a MAC user and your friend keeps loading you with Microsoft Office documents. What do you do, other than telling him to stop already?

The Nokia N900 smartphone comes with a wide variety of apps including e-mail, a browser, and more. Browsing, opening, and switching between these apps is an easy task when you know the right gestures and taps to make on phone's screen.
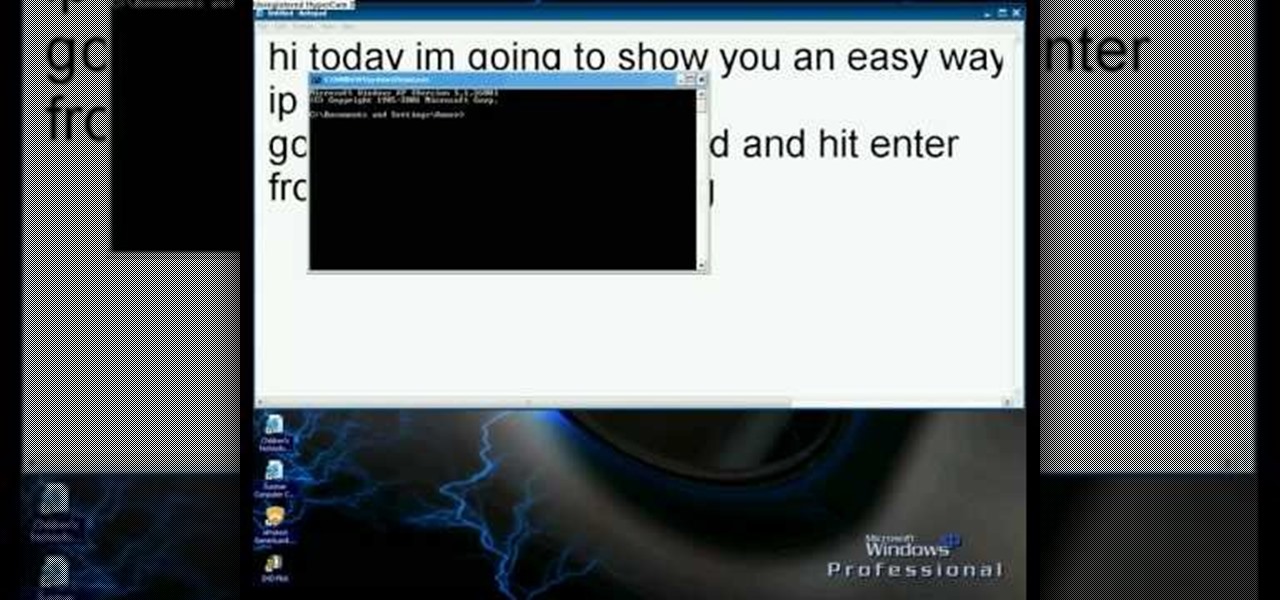
In this video we learn how to find your IP address with the Command prompt. First, go to the start menu on your desktop. Then, find the run box and type in "cmd". After this, hit "enter" and then a black command prompt will show up on your screen. Next, type in "ip config" and then hit the enter button again. Now, a list of information will appear on the black screen. Look down the list to find the IP address listed on the page. Once you have this, you should write down your IP address and th...

In this clip, you'll learn how to share web pages by email on an Apple computer running the Mac OS X operating system. For more information, including a complete demonstration of the process and detailed, step-by-step instructions, watch this home-computing how-to.
This is how to hack a computer for educational purposes. First you need its IP address, radmin viewer 3.3 or later, and an open port scanner. Okay so first you need the IP and scan the IP address of the computer. Now find what open port it has. Ok then open up radmin viewer and put in the IP address and open the port you found. Now right click after you enter the computer's IP address and the open port. Select full control or view only and there you go. The computer has been successfully hack...
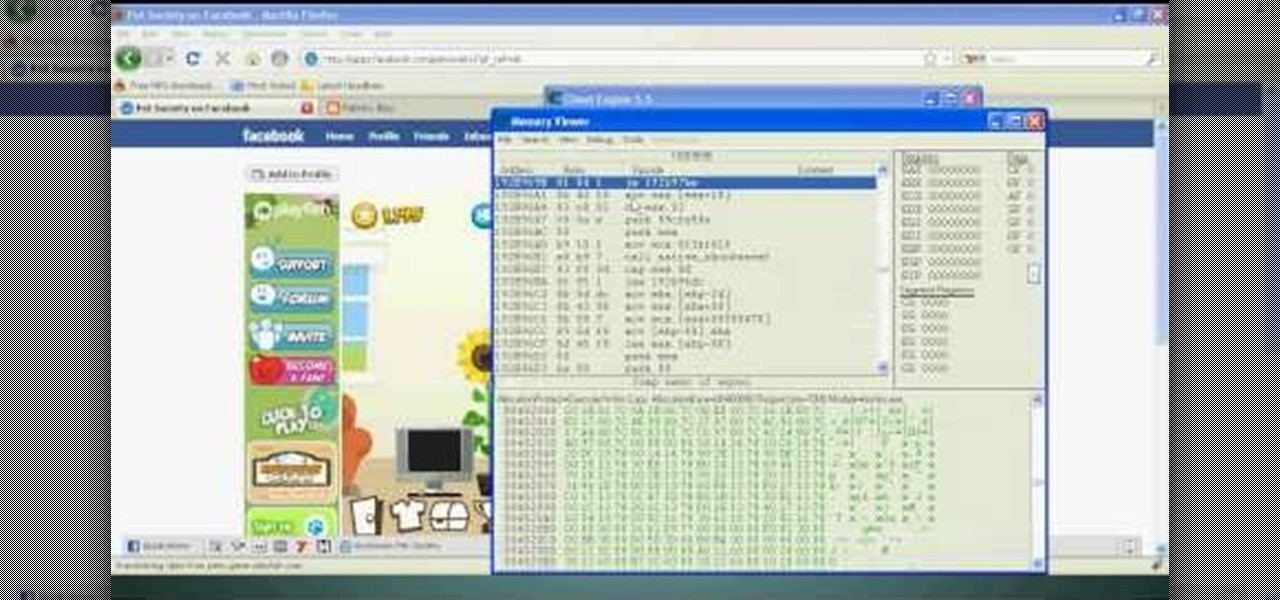
you will need :firefox , cheat engine 5.5 and adobe flash player 9.0 and you can get them from : http://www.mozilla.com

This video tutorial, designed for users of the Windows XP and Vista operating systems, offers instructions for creating a preview button in Microsoft Outlook Express or Windows Mail. For step-by-step instructions on disabling the automatic preview pane, watch this handy how-to.

Want to send a 100MB file via e-mail? How about 1GB? This how-to video can help you do it, and it will cost you nothing. Watch this helpful internet tutorial video to learn how to email large files for free.

This video will teach you how to make an incredibly cute Valentine's Day card. This card tucks in itself to serve the purpose of both envelope and card, although an envelope should still be used for mailing it. All your valentines will know that you love them when you make this adorable card.

Watch this tutorial video to learn how to get your work e-mail on your iPhone using the latest firmware upgrade. New iPhone users will find this how-to video particularly helpful because it shows an easy way to set up Exchange email on Apple's iPhone.

This is a short tutorial on how to use spam assistant in order to avoid spam mails using cPanel. This video is provided to you by Scandicsoft.
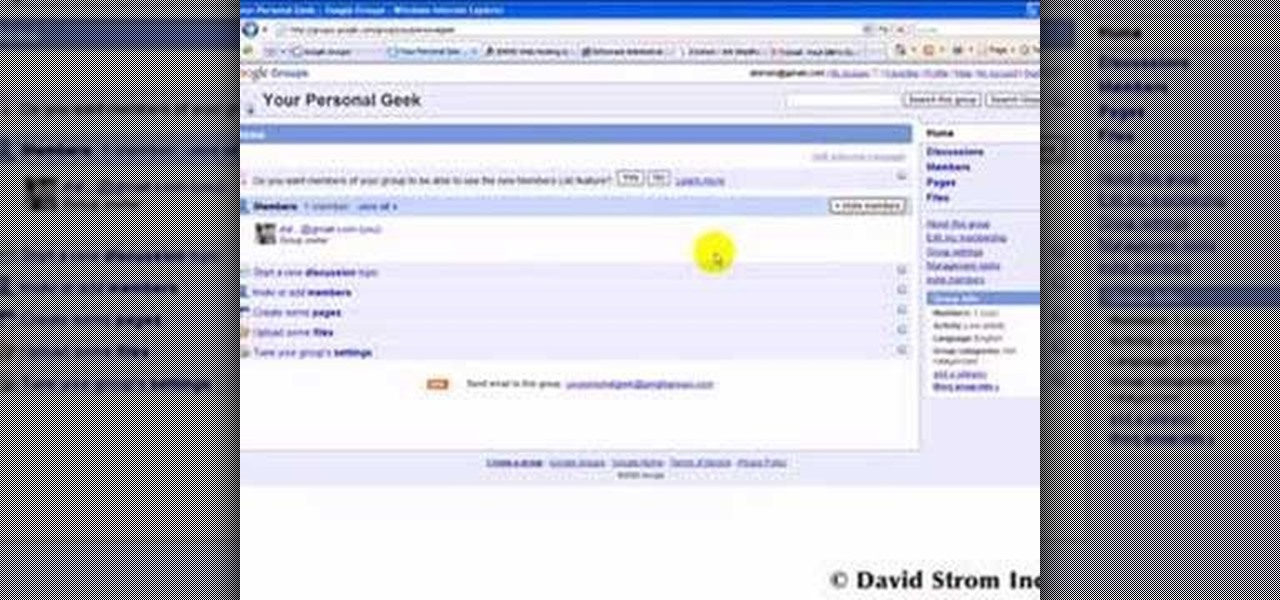
David Strom shows you how to pick from aong Google Groups, Mailman hosted by EMWD.com, and iContact and how to get started with your own mailing list
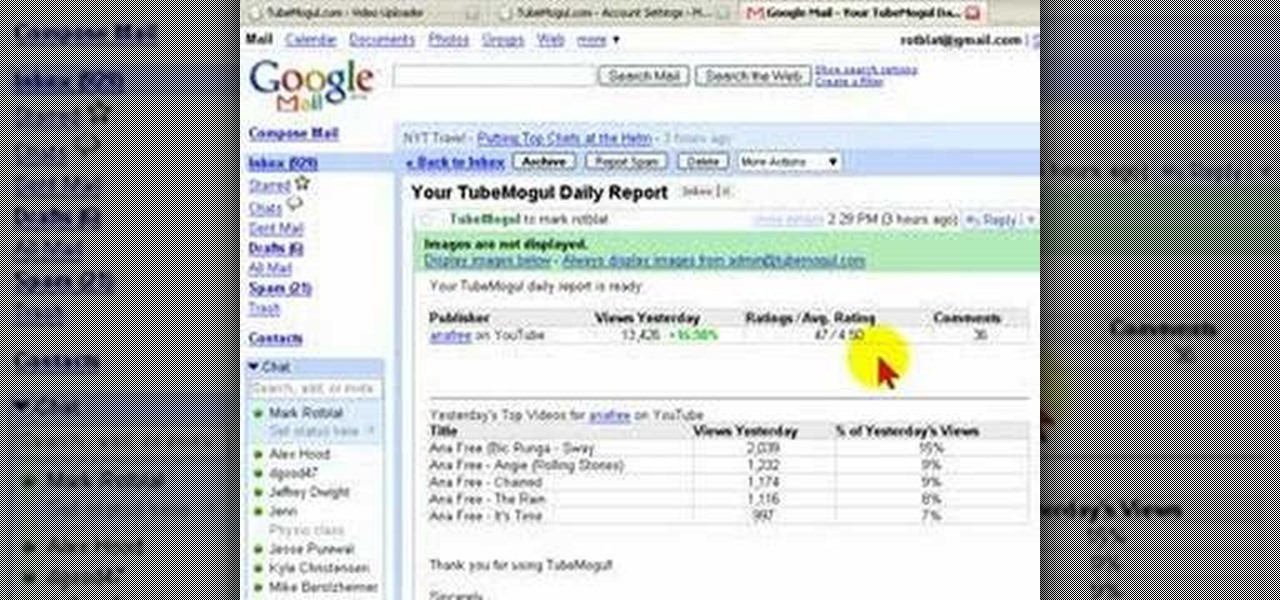
Here, Mark Rotblat of Tubemogul shows how simple and easy it is for you to e-mail your tracking reports to yourself and other people.
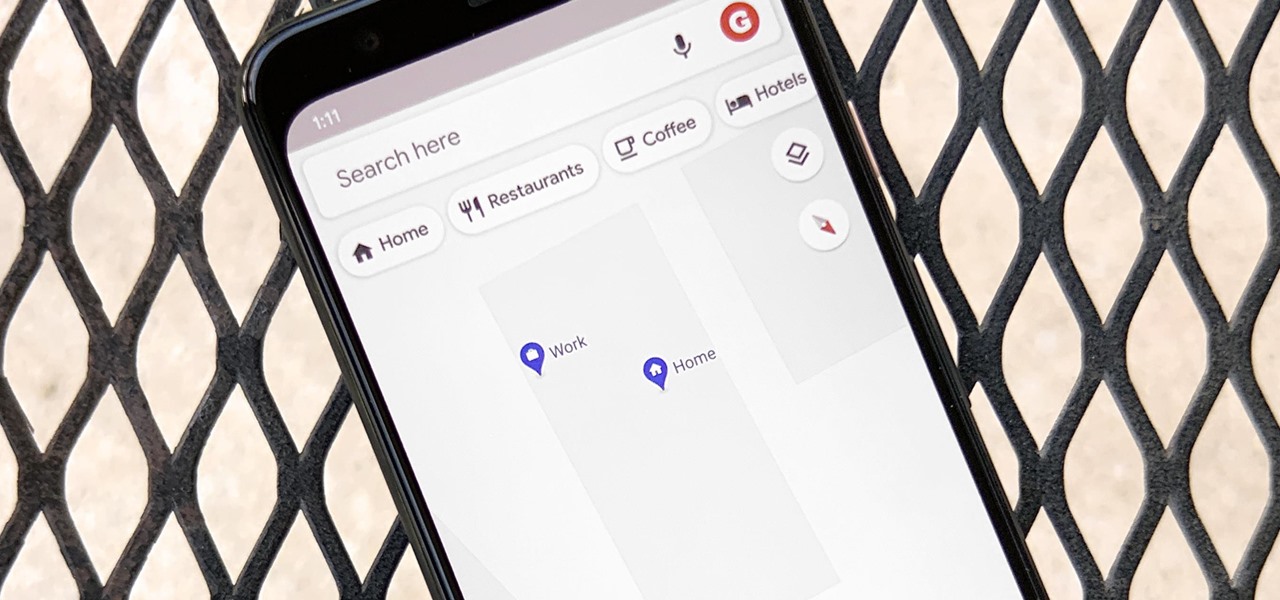
Google Maps lets you set home and work locations for quick access to navigation. In fact, these two locations are so central to the Maps experience that if you don't have both saved, the app can be a little naggy about it. But if you work from home, there's just one address to use, so what are you supposed to do?

Smartphones and other Wi-Fi enabled devices send radio signals called probe frames to locate nearby wireless networks, which makes them easy to track by listening for their unique MAC address. To show how this kind of tracking works, we can program a NodeMCU in Arduino to sniff the air for packets from any device we want to track, turning on an LED when it's detected nearby.

After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.

Whether you're white hat, black hat, or some shade in-between, navigating through a network is a core part of hacking. To do that, we need to be able to explore a network to discover the addresses of gateways, interfaces, and other attached devices. When ifconfig just isn't enough, you can steer your way around a network with a convenient tool called Ship, the script for everything IP.

Hello everybody. I'm back with Part-2 of this series. In this part we will be programming in C our server and i will be explaining one more "key concept" so everybody got a better understanding on this.

This tutorial video will provide an idea how to cancel or undo a Gmail sending. You will get a few seconds to undo the sent mail in Gmail. So please Watch the video and follow the steps. Employ the technique in your Gmail account.

It seems like every other day there's a new security threat or data leak in the news. Whether it's your credit card PIN or your smartphone's apps leaking your email address, no one wants their personal information out there, especially passwords. And if you use the same email address and/or password for more than one site, the effects of someone getting hold of your credentials can be catastrophic.
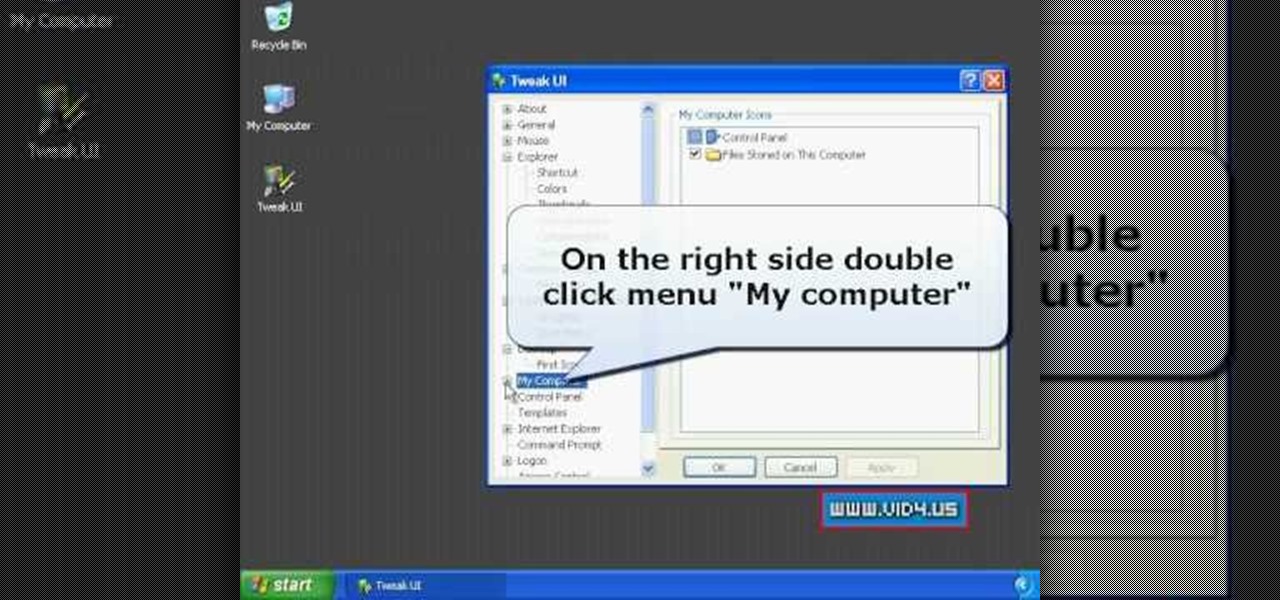
Firstly download the TweakUI into your computer, which is free. Fire up TweakUI and click on menu "Explorer", uncheck menus: "Allow help on start menu"; "Allow log off on start menu" and so on play with the settings however you like. And select "Light arrow", next click on "Thumbnails" menu and drag the slider all the way to the right, increase the size of thumbnails to 120 pixels. Next double click menu "Common Dialogs" and uncheck all three menus. Next double click menu "Taskbar and start m...

In this video Patricia Stark shows how to display voice mail confidence. Studies show that it takes only three seconds for somebody to size you up over the phone. You can know a lot about the person speaking on the other end of the phone and so you need to sound very confident while speaking to other persons. It is proved that when you smile when you are speaking on the phone it changes the whole delivery of your tone and if you are sitting there carelessly it will be reflected in your voice....

You can learn to make a beautiful chain mail bracelet by watching this video. The bracelet is easy to make and affordable too. Start by sliding two silver jumper rings onto a paper clip. Two copper jumper rings are passed through the silver rings and twisted to complete the loop. Next, two silver rings are passed through the copper rings and twisted to complete the loop. Next, place the silver rings on either side of the copper rings and pull them up from between the copper rings, as shown in...

Clueless when it comes to styling those unruly bangs of yours? Face fringes are cute and fashionable but need extra attention to keep them looking fresh. In this video, learn how to style those bangs easily and with style.

Have you ever had someone make you feel better with a simple act of kindness? Now it’s time to bank some good karma and make someone else’s day.

In this video you are shown how to use proxies and why they are important. Proxies are useful because they shield you and make you anonymous over the internet, it also prevents websites from logging your IP address. To see how important it is to prevent this go to whatismyip.com. It will show you your IP, click on it and go to 'look up'. It will show you all the personal information that can determined from your IP address. The easiest way to proxy are VPN's, which stands for virtual private ...
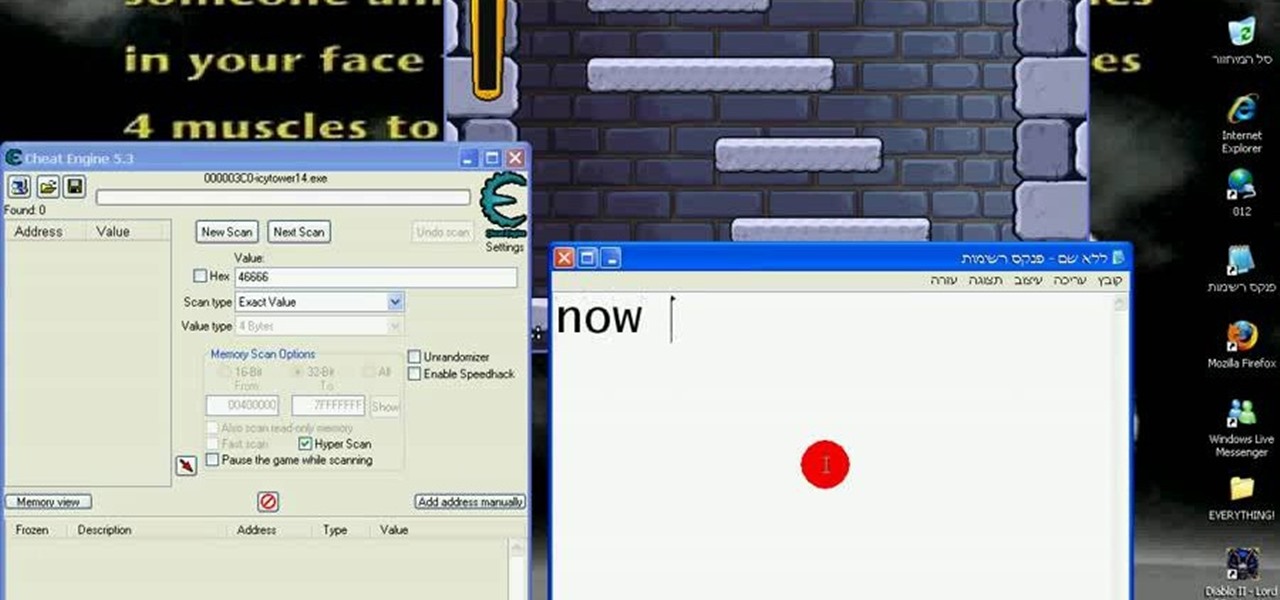
The cold time of Christmas is upon us, and Icy Town is a winter-ific game you can play… and hack. With Cheat Engine and a little patience, you can hack and unlock floors in the game easily.
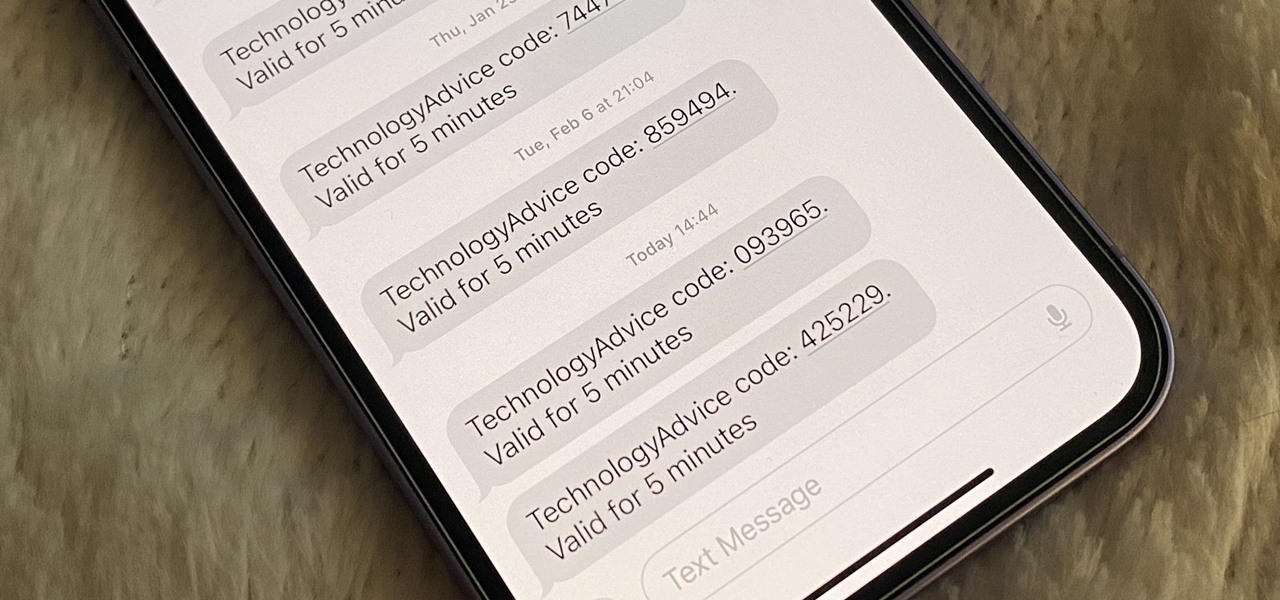
Many of your accounts online likely require two-factor authentication (2FA) or two-step verification (2SV) to confirm your identity when logging in, and there's a good chance the second factor or step for each is a one-time email or SMS verification code. If you get a lot of email and SMS codes, it can clutter your Mail and Messages apps with junk if you don't delete the messages after signing in.

Apple's iOS 15.4 and iPadOS 15.4 updates have a pleasant surprise for iCloud Mail users and everybody that use the Mail app as their primary email client for AOL, Gmail, Outlook, Yahoo, and other third-party email services.

Apple just released iOS 14.0.1 for iPhone today, Thursday, Sept. 24. The update features bug fixes for the News widget, default browser and mail apps, and more. In iOS 14, default apps suffer from a bug where iOS reverts back to Safari or Apple Mail when rebooting your iPhone, which defeats the purpose of the feature entirely.

With all the hype surrounding meteoric rise of Bitcoin (BTC), Litecoin (LTC), Ethereum (ETH), and Bitcoin Cash (BCH), it's easy to overlook the fact that you can send and receive cryptocurrencies as a form of payment. And thanks to Coinbase, sending and receiving digital coins couldn't be any easier.

I have gotten comments from my last tutorial on not being able to do anything because of a lack of a monitor. In order to address this problem I'm gonna show you how to connect and control the Rasberry Pi through a SSH client on Linux, Mac, Windows, and Chromebook computers. This will probably we a long tutorial so please bear with me. Anyway, lets get to work.

Welcome back, my amateur hackers! When you are using and administering Linux, it is important to be conversant in the use of the log files. As you know, log files are the repository for much information about our system, including errors and security alerts.