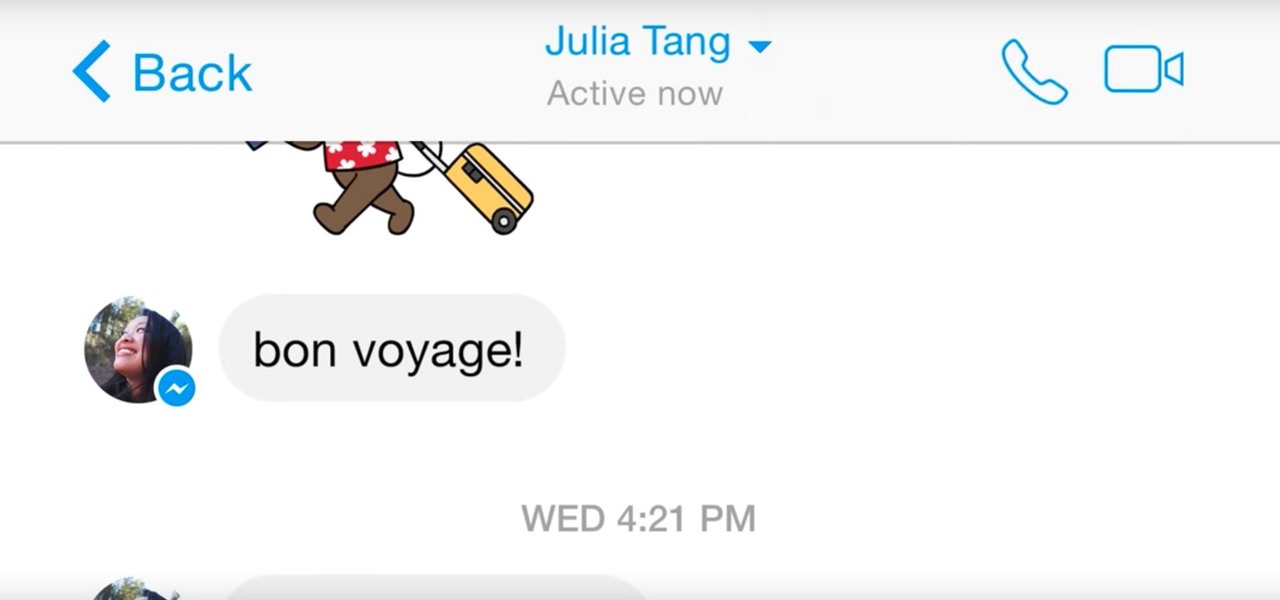
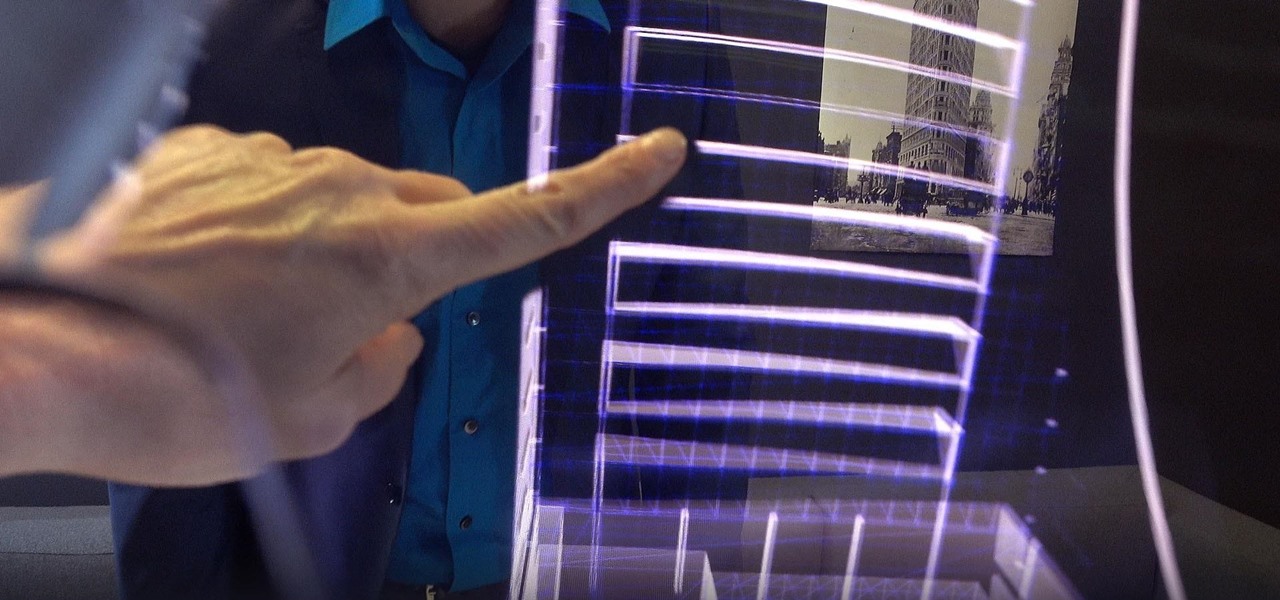
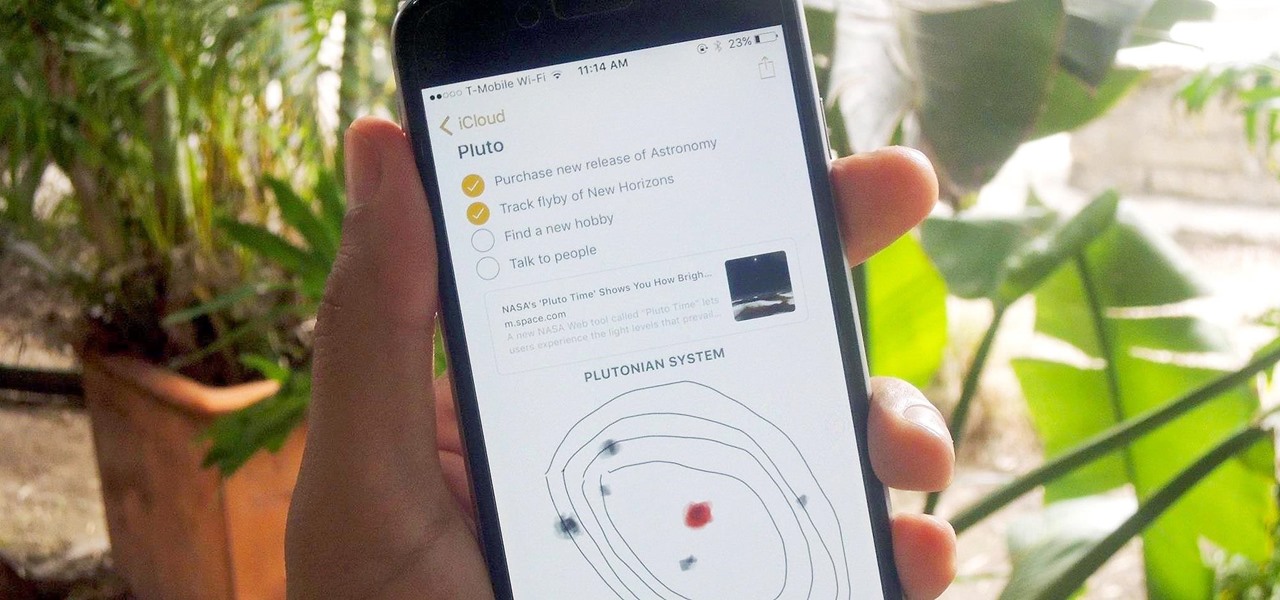
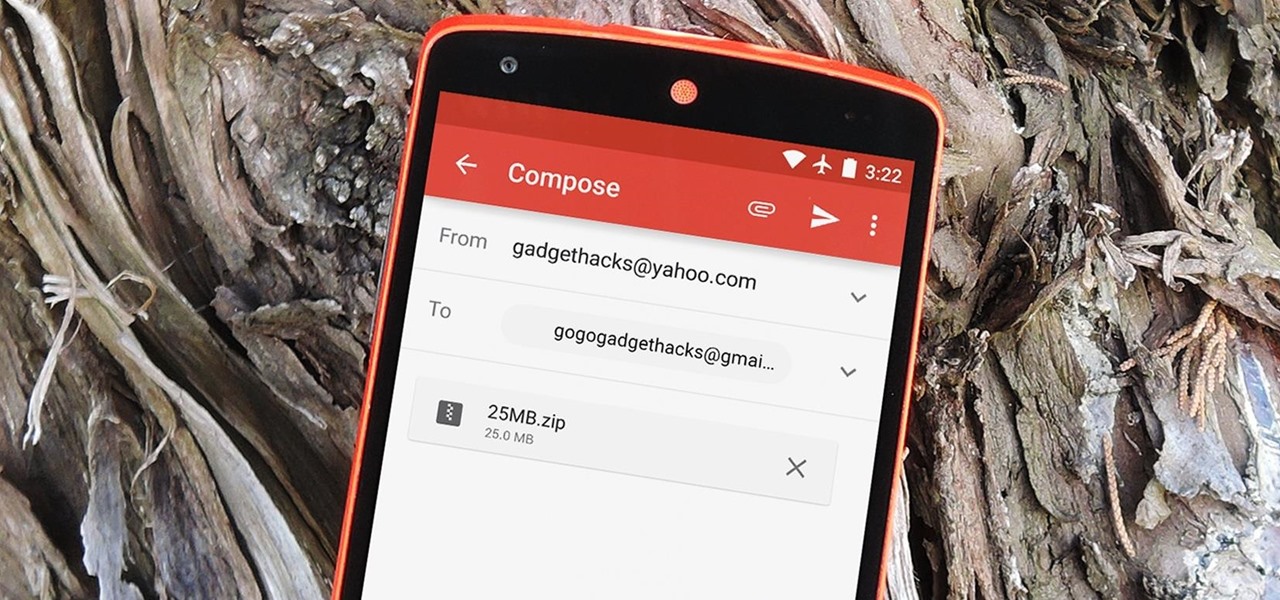
The gig economy is thriving, and if you aren't already making money with your phone, you could be missing out on easy residual income. Some people just want extra cash, and some even manage to completely ditch the 9–5, enabling them to work at their own pace and set their own hours.

The Play Store hasn't been the most secure place for apps lately. A quick Google search for "Play Store malware" will give you a taste of some of the malicious apps that snuck their way onto Android's official app store. Google is aware of the problem and they're tying to fix it, but their new Play Protect program doesn't have a great track record, so you might want to look elsewhere.

If you're a regular reader of Next Reality, you're more likely to spread the joy of augmented reality than most others. But it can be difficult to introduce newbies into the AR fold if you don't give them exactly the right starting point in terms ease-of-use and affordability. But fear not, oh gift-giving AR pioneer, we're here to help!

Clumsiness is the great equalizer when it comes to smartphones — it makes no distinction between the most expensive flagship handset and cheaper mid-range models. A hard drop onto pavement will usually result in a shattered screen, regardless of how pricey your device is. And with a smartphone breaking every two seconds, we're truly our own handset's ultimate nemesis.
Now that we have installed the toolkit, set up our prefabs, and prepared Unity for export to HoloLens, we can proceed with the fun stuff involved in building a dynamic user interface. In this section, we will build the system manager.

On your iPhone, your phone number and Apple ID email address are the default ways in which somebody can contact you on FaceTime. While you can't remove your phone number as an option, you can withdraw your Apple ID email account. More importantly, you can add any other email addresses you'd like to the list, so you never have to worry about a friend, family member, or coworker not being able to audio or video chat with you.

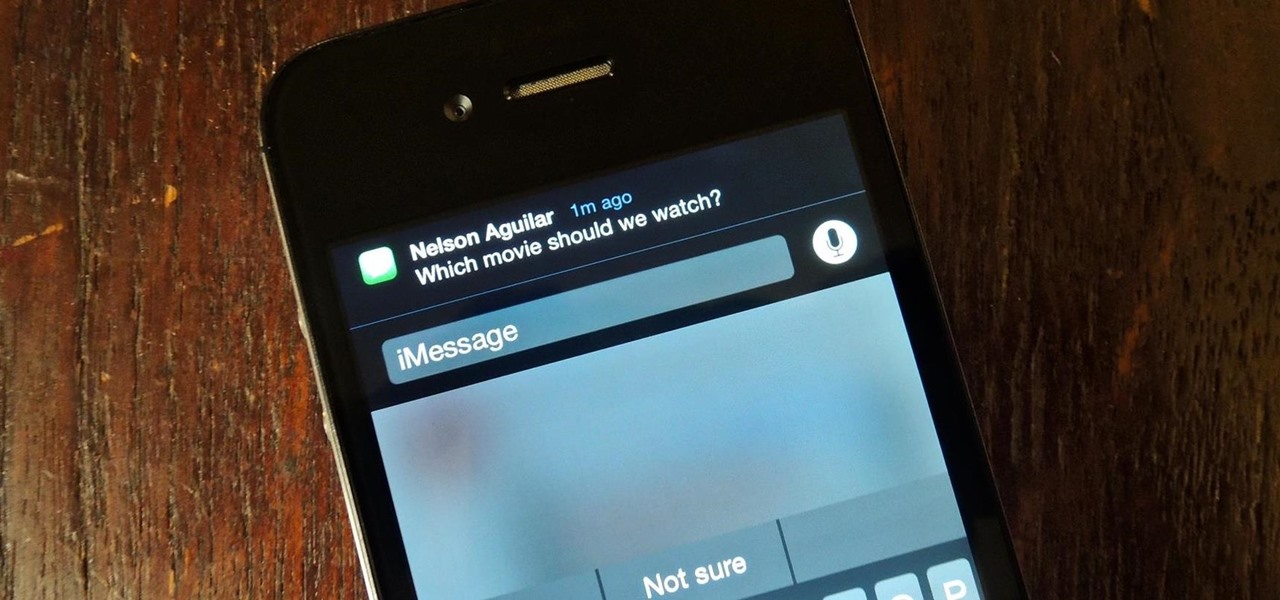
M — Facebook's AI-powered assistant unveiled to the public in April — is now better than ever. The latest update to M now allows it to provide three more suggestions: a function to save content to view later, birthday wishes, and call initiation.

While two augmented reality companies were recently recognized for their innovative technologies, other companies have turned to augmented reality to innovate in their respective fields. Over the past week, use cases have ranged from selling snacks and video games to raising awareness for public health issues.

Uber CEO and co-founder Travis Kalanick is taking an indefinite leave of absence from the company, as Uber's recent upheaval has far overshadowed any developments in its driverless initiative during the past few days.

We're almost there to completing the setup of your Mac for hacking! Now that we have Git and Homebrew under our belts, it's time to take on something fairly easy, but very important for our hacking needs.

When you think of all the fun and games smartphones have to offer, it's easy to forget that they also make a great tool for getting things done. With utilities like document scanners, calendars, to-do lists, office apps, and password managers, that little computer you carry around in your pocket has the potential to increase your productivity levels in all aspects of life.

In this how-to we will be sending an email with an image we get from a php script after running some fishy code. What you'll need

In this article I will show you how to obtain victim's credentials without cracking any hashes. There are a couple of ways to perform this task (for example dumping the SAM file and cracking the NTLM hashes), but here I will explain how to do it using PowerShell and a bit of social engineering. We are going to create a fake login popup.

If you purchased something from iTunes, the iOS App Store, iBooks Store, Apple TV App Store, or the Mac App Store and it doesn't work, didn't download, is buggy, or wasn't what you thought it was, you can get a full refund from Apple—you just have to know how to ask.

Welcome back! In the last round of python training, we talked about tuples and dictionaries. We'll be diverging again and talking about logical operators as well as membership operators. These are used very similiar to booleans, so if you haven't read that, I suggest you do so first.

Hello fellows nullbyters, first of i will start saying that im addicted to this community, i feel the challenge growing up so fast, all the newbies, amateurs,advanced and professionals hackers around trying their best to help the community, badly but we got some script-kids too but anyway, today we are going to learn how to install and use clanAV in kali linux.. INTRODUCTION

If you've just ditched your Android phone for a new iPhone, you're in luck, because Apple has a way to make your transition as simple as possible with their Move to iOS app for Android. To help make things even easier on you, we've outlined the process of using Move to iOS to transfer images, messages, contacts, mail accounts, calendars, and more over to your iPad or iPhone running iOS 10.

This is second post in my series of posts for finding hacked accounts online. Please do read the part 1 of the post at http://null-byte.wonderhowto.com/how-to/find-hacked-accounts-online-part-1-0164611/

Though you can use the Social Engineering Toolkit to clone websites, this way is much more customisable.

No matter how fresh, sharp, or clean a razor is, it can still create an itchy, inflamed trail of razor burn bumps. When razor burn appears, it's unpleasant, and can even affect your next shave.

Notes on iOS has never been a particularly great app due to a lack of overall features compared to other note-taking apps like Evernote or Microsoft OneNote.

The Gmail app recently became stock Android's central hub for all of your email accounts. Instead of being limited to just Gmail accounts, the app can now handle POP3, IMAP, and exchange service email accounts, making it a one-stop shop for all of your emailing needs.

Welcome back, my hacker novitiates! In an earlier tutorial, I had introduced you to two essential tools for cracking online passwords—Tamper Data and THC-Hydra. In that guide, I promised to follow up with another tutorial on how to use THC-Hydra against web forms, so here we go. Although you can use Tamper Data for this purpose, I want to introduce you to another tool that is built into Kali, Burp Suite.

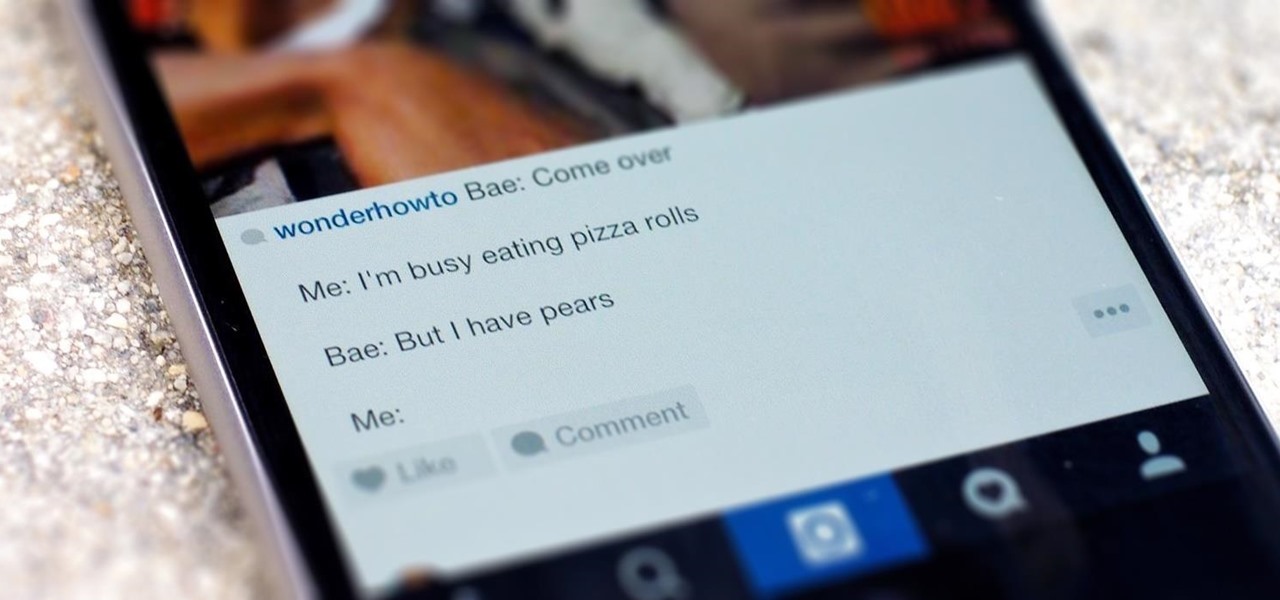
Line breaks signify not only the ending of one line of thinking, but the beginning of another. We use them to emphasize points, to fragment information, to shift tone, and more. They're important in getting our message across properly, which is why I'm always disappointed when I can't insert a line break into my masterful Instagram caption.

Welcome back, my novice hackers! Before we try to attack a website, it's worthwhile understanding the structure, directories, and files that the website uses. In this way, we can begin to map an attack strategy that will be most effective.

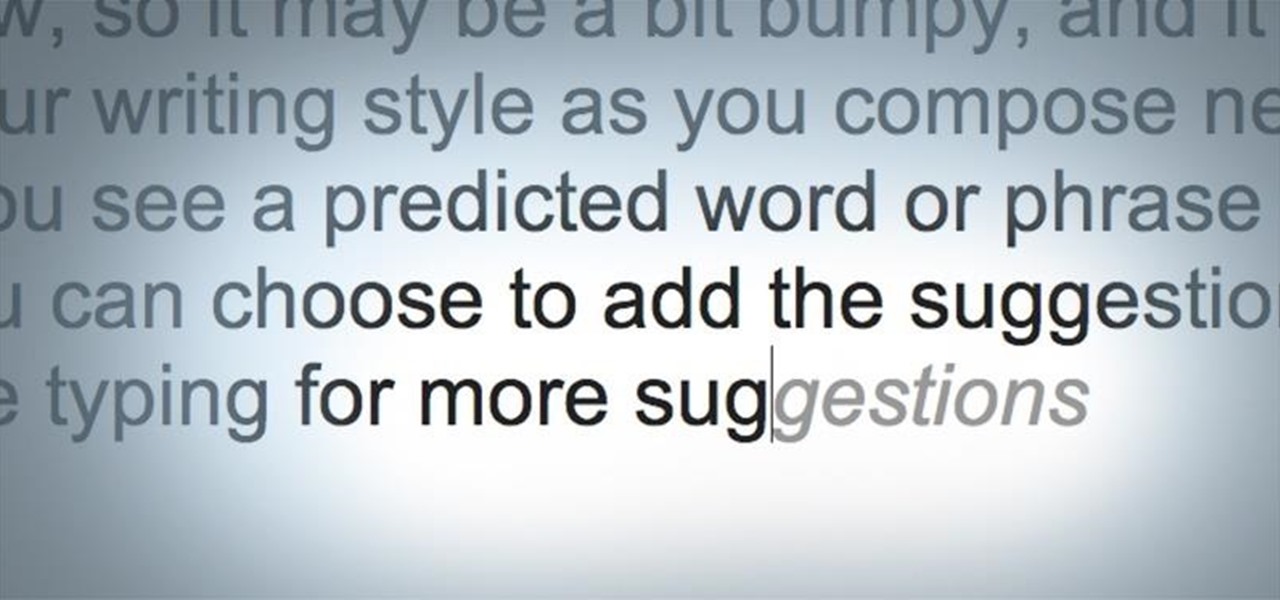
Android has had predictive text for a while now, both with stock and third-party keyboards such as Fleksy, SwiftKey, TouchPal, et al. Apple is even getting on board, with stock predictive text and third-party keyboards for iOS 8, slated for public release later this year.

Welcome back, my hacker novitiates! In previous guides, we have used one of the most powerful hacking platforms on the planet, Metasploit, to perform numerous hacks. They ranged from exploiting Windows XP and Windows 7/8 vulnerabilities, to installing a keylogger and turning on a webcam remotely. We have even been able to save the world from nuclear annihilation, see if our girlfriend is cheating, spy on suspicious neighbors, evade antivirus detection, and more.

Notification banners and alerts aren't new to iOS, but the ability to expand and interact with them is. Apple's new iOS 8 has ushered in some small, yet convenient features to the banner and alert notifications that make them truly interactive. The new additions, as you will see, makes it easy to complete simple tasks without leaving the current screen you're in.

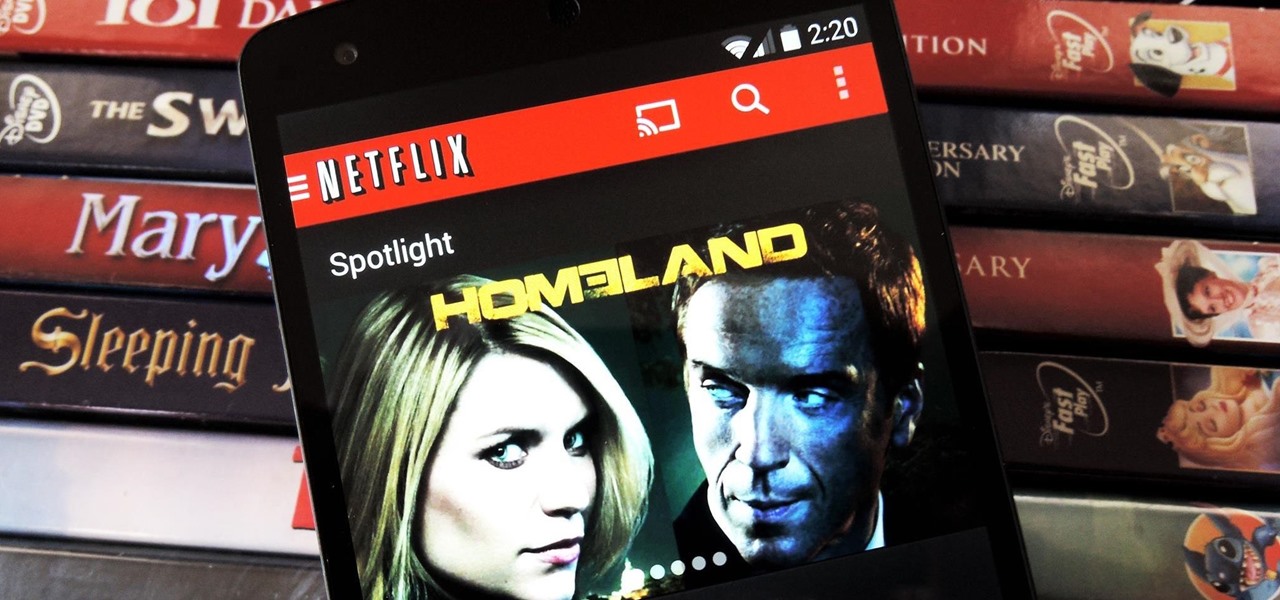
Out amongst the ether of the internet lies a completely different version of the Netflix library you've come to know and love. Because of licensing and rights fees, the streaming media giant maintains separate libraries for each country it services. Ultimately, this means that certain movies and TV shows are only available in certain countries.

If you're spending hours on your phone playing games like Angry Birds and Candy Crush Saga, or posting online to Google+ and Pinterest, you're probably being spied on. The latest releases from NSA whistle blower Edward Snowden reveal that the National Security Agency, and its UK counterpart, GCHQ, are mining the ad networks utilized in these apps to collect a trove of information on you.

During the colder months, it seems like almost everyone wears boots. Even when it's hot out, people can be spotted with knee-highs and westerns. Whether it's for fashion or because you live in a place where 3 feet of snow is common, a good pair of boots (or five) is nice to have.

Do you guys remember those things you hold with your fingers to write stuff down? I think they're called pens, or something like that...

For those of you still using a BlackBerry smartphone, this article will show you the tips and tricks to installing emulators and playing some classic Game Boy Advanced games on your device. You can find a few tutorials and videos out there on getting Game Boy Color or NES games on an Android device, but the most elusive mobile emulator is for Game Boy Advanced (GBA) on a BlackBerry.

Steampunk is a tremendously interesting phenomenon because of its reliance on science fiction, and fiction in general. Steampunk can arguably be broken down into two categories: the fiction, and the aesthetic. Sometimes these categories cross over, but they're often more distinct than most people suspect; that said, the aesthetic is firmly based in works of fiction.

Two-letter words are one of the most important parts of playing Scrabble. If you don't know all of the small ones, then you're missing out on one of the easiest ways to score big. Check out How to Score Big with 2-Letter Words in Scrabble and memorize all that you can. Definitions are optional, but you won't need them for this challenge.

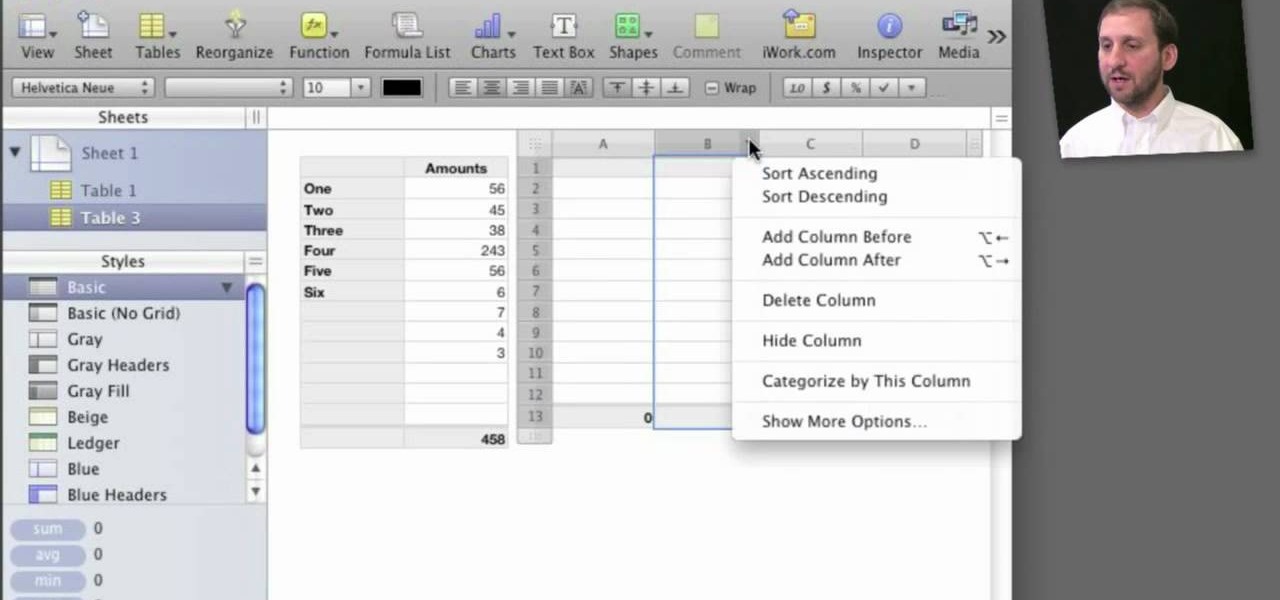
Apple's iWork '09 is full of great features, including a simple and elegant way to add up a column of numbers in a spreadsheet. This detailed video shows you just what to do to get down and add up.

If you're running low on time and short on money this holiday season, there is a way to still give your friends and family presents without having to resort to cliche $5 Russell Stover chocolates from the drugstore.

Use the Excel Vlookup function in Microsoft Excel 2007 to look up data in a table. This tutorial looks up the level and value of a product from a stock list using the Vlookup function in Excel.

Even if you were born with luxurious flaxen strands so gorgeous they'd put spun gold to shame, it's still important to maintain a haircare routine that continually moisturizes and cleanses your strands to keep them in tip top shape.

You know how sometimes you'll look up a recipe from a famous chef, and then when you take a gander at the ingredients list it looks longer than the last "Harry Potter" book? Complex, "high art" dishes sometimes do requires what seems like a million ingredients - and precise stirring and heating times - to accomplish.