
News: What Google's Upcoming Andromeda OS Means for Android & Chromebooks
Google is working on something so big they had to name it after an entire galaxy: A new operating system that merges Android and Chrome OS into one unified front.


Google is working on something so big they had to name it after an entire galaxy: A new operating system that merges Android and Chrome OS into one unified front.

An average user's smartphone tinkering doesn't go much further than taking their phones out of the box, signing into their account, and installing apps. But some of us want more functionality and customizability than the basic experience provided by Android and iOS.

Since its purchase by Microsoft in 2014, Minecraft has regularly been pushed to new platforms such as Windows 10, Wii U, and Fire TV. In that spirit, Microsoft-owned Mojang has been developing virtual- and augmented-reality versions of the blocky sandbox game.

When performing something such as a mass mailer attack on a company, sending executables usually isn't the best option. That's why, in this tutorial, I'll be teaching you how to code a VBA script macro into a Word document in order to compromise a system. Combined with a little social engineering, this can be a very effective technique.

Hello fellow training hackers. I do not know if many of you are familiar with ruby, but since it is a useful scripting language, that hasn't been covered too much here on Null Byte, I thought why not do some How-tos about it now and then.

Who doesn't love the world of Game of Thrones? Whether you're a fan of the hit HBO show, or can't wait for George R. R. Martin's next novel installment, it's a story loved by nearly everyone. It's an excellent source of inspiration for Halloween costumes too, ranging from the disturbed to the beautiful. Lady Stoneheart, Catelyn Stark risen from the dead, is the perfect scary choice—bloodied, battered, and carrying a desire for vengeance.

Last time in how to train you python, we covered the basics of variables and output. While we were covering variables, we talked briefly about strings. "String" is just a fancier way of saying "Word". A string is simply a set of characters encased in quotations, this lets python know that it is a word. Sometimes when we do things with strings we'll need to change them in order to do something. Python is case sensitive, for example "Null-Byte" is not the same as "null-byte". This is where mani...

Greetings My Fellow Aspiring Hackers,
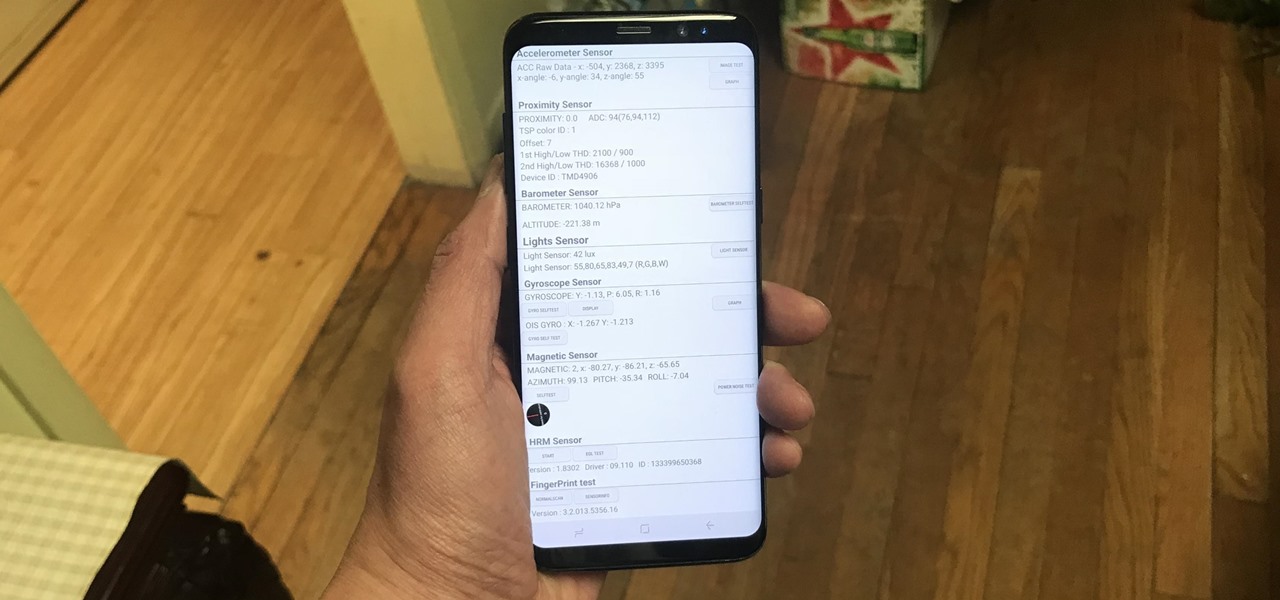
Besides obvious features like a touchscreen and biometric sensors, the modern smartphone comes with an array of state-of-the-art hardware in the form of various sensors that help your device sense the environment around it. And if you have a Samsung handset, chances are, you have a handy feature built in that enables you to check if these sensors are functioning 100 percent.

As someone with a pretty nice TV, I've never found the allure in purchasing a projector. While they're certainly smaller and sleeker than a television, and more portable, they can be pricey and produce a less than stellar image. And who really buys a projector anyways? They're for school, they're for work, they're for theaters, but they're not really for my apartment, right?

Desktop users have taken advantage of dual-booting operating systems for decades now. If your core system software is lacking in any regard, dual-booting a secondary OS can give you access to those features that you're missing out on.

This year's biggest film certainly didn't come as a surprise: with another incredible comic book creation, Marvel's Guardians of the Galaxy wowed audiences more than any other movie. With its unique team of heroes, Guardians provided a set of ready-made Halloween costumes.

Welcome back, my hacker novitiates! A short while ago, I introduced you to regular expressions. Regular expressions are a language that is particularly useful for finding complex text patterns in streams of data.

Casting Angelina Jolie as Maleficent was a no-brainer on Disney's part. No one else could project beauty, elegance, and fear simultaneously just like the animated villain in Sleeping Beauty did. But what sets the character apart from other evil witches, or any other Disney character for that matter, is the sinister, yet gorgeous-looking horns and headdress. And with news that a Maleficent sequel is currently in the works, this will surely be a great Halloween costume this year.

Emojis have transformed the way we laugh and cry, tell stories, give responses, and express excitement to get a drink after work — without any actual text required. Heck, in an incredibly meta move, the Oxford Dictionary even named the "Face with Tears of Joy" emoji as their word of the year at one point. So how could you not want to be an emoji character for Halloween? Emojis are everywhere. The ubiquitous symbols are already on smartphones, tablets, and social networks, so why not help them...
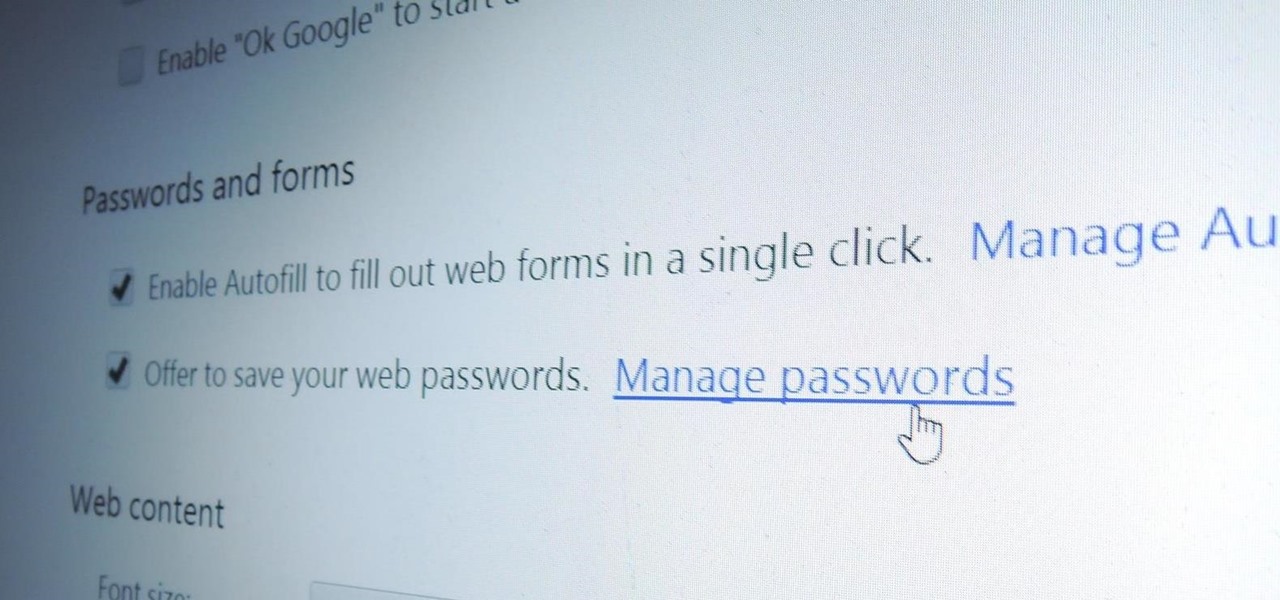
Chrome, Firefox, and Safari all provide built-in features that allow you to save your username and password for your favorite sites, making the process for entering your credentials a breeze when you revisit them.

When it comes to passwords, the longer and more complex they are, the better the security. Even professional hackers say so. But if you've ever tried to type in such a password, you've surely noticed that it can be a bit of a pain. Mistype one character, and you're probably going to have to clear the field and start all over again.
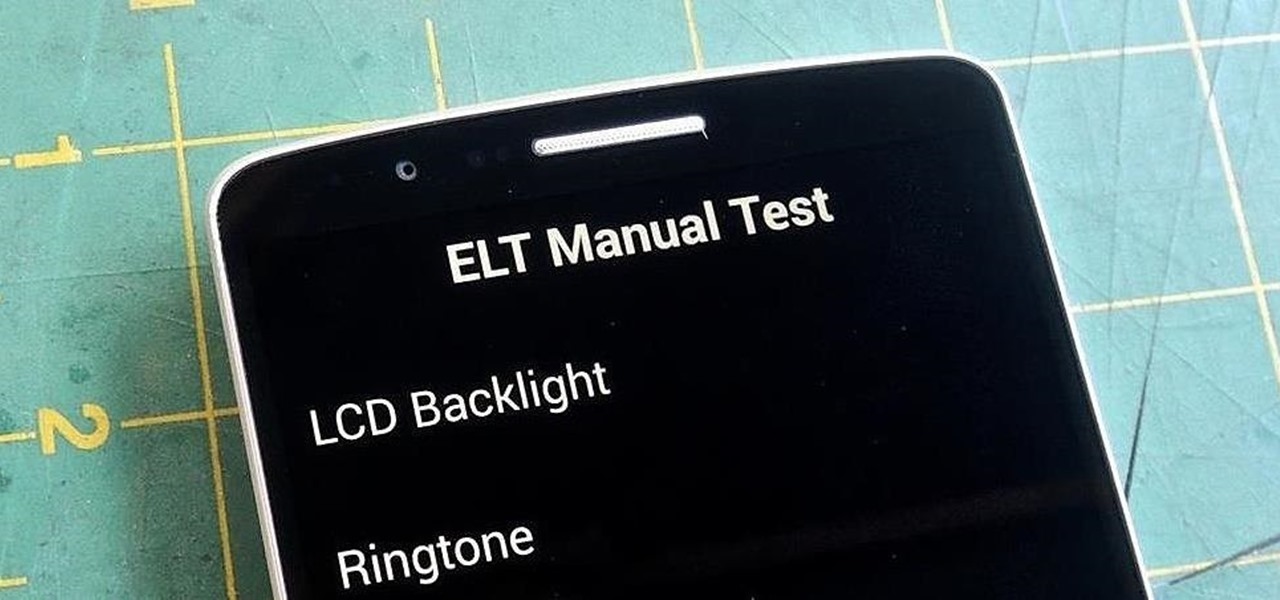
If you notice any issues with your LG G3, pinpointing the culprit can be an arduous task. It could be a hardware issue, a resource-heavy app, or a bloatware-infested operating system.

As we near the one-year anniversary of its release (and the inevitable unveiling of its successor), the Samsung Galaxy Note 3 remains a device that packs quite a punch when it comes to hardware. It boasts a 2.3Ghz CPU and was the first mobile phone ever to house 3GBs of RAM. Suffice it to say, it can handle any software you throw at it with no discernible lag. Even Samsung's notoriously bloated TouchWiz ROM seems lightning fast.

It seems like custom Google Now commands are a dime a dozen these days. With Commandr for Google Now giving non-rooted users their first taste of custom voice commands just a couple weeks ago, you may wonder why we're covering this subject again.
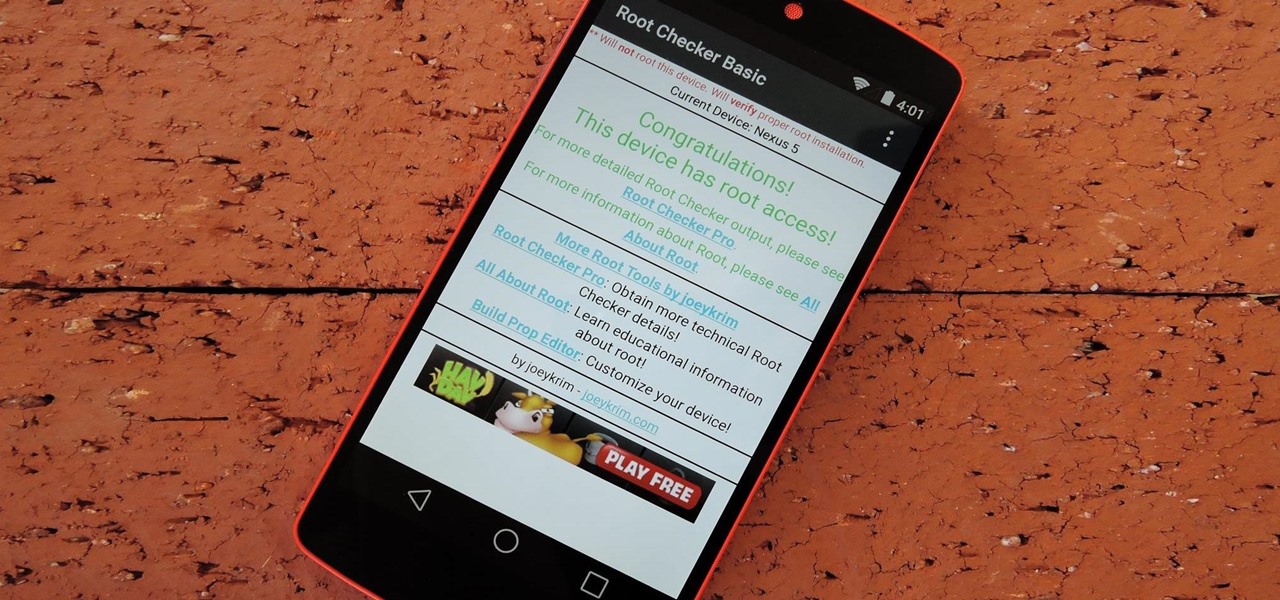
While the preview images for Android's upcoming "L" release just came out yesterday, the new firmware has already been rooted, as is standard with its openness. So if you were feeling reluctant to try Android L because it didn't support existing root methods, then you might want to reconsider.

Welcome back, my aspiring hackers! In recent tutorials, I have made reference to the name and location of the Linux devices in the file system, such as sda (first SATA or SCSI drive). Specifically, I have mentioned the way that Linux designates hard drives when making an image of a hard drive for forensic purposes.
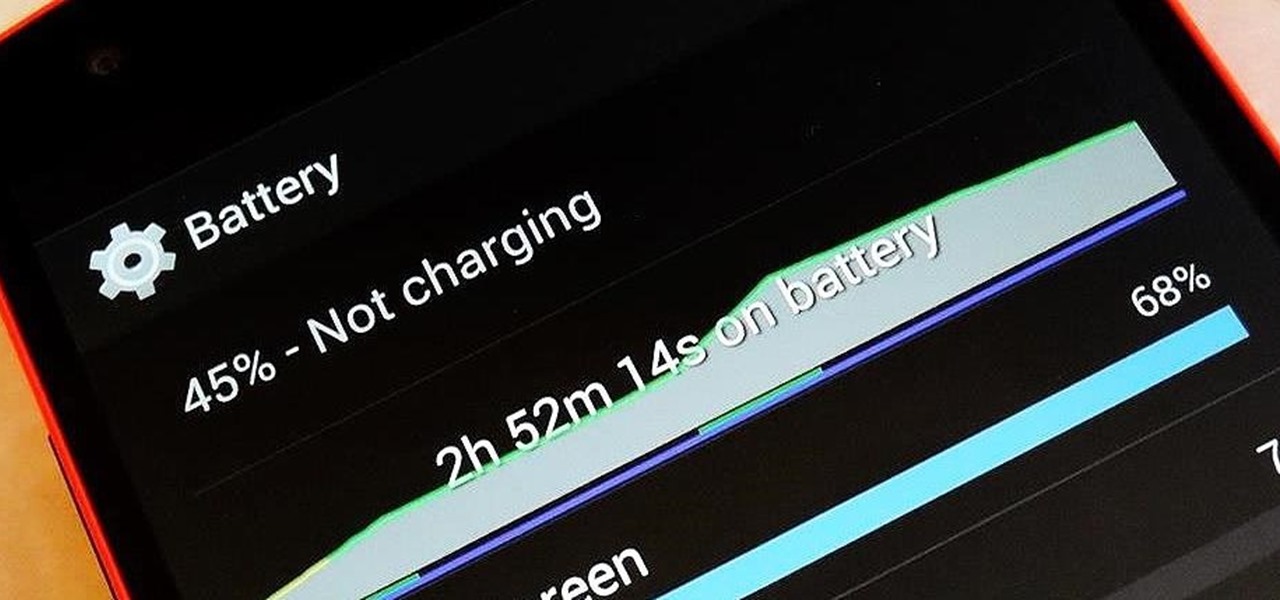
There are so many things to love about the Nexus 5, from timely updates to newer versions of Android to a terrific blend of price and specs. But while mobile phone tech keeps churning along, battery technology isn't quite up to snuff yet, and I find myself wishing that my phone's battery lasted longer on a single charge.

Probably one of the most sought after features of the LG G2 is its "Knock Knock" capabilities. Rather than dealing with that pesky power button, you simply double-tap portions of the screen to either sleep or wake your device.

From amateurs to professionals, DSLR cameras are the standard weapon of choice for most photographers. If you own one, then you probably know how expensive of a hobby photography can be. A good starter camera can run between $400 and $500. Then there are accessories like tripods, lenses, filters, and memory cards that can slowly empty out your wallet.

With so many cloud storage services out there, many people are starting to keep their important documents online, especially when they know they'll need to view them when they're away from their computer.

Creating a class in Black Ops 2 is kind of like an art form. Every player has an insane amount of options for creating a character for all sorts of situations. Combining perks, with secondary weapons, and attachments allows for a wide range of killing options. But in order to unlock a lot of these perks and attachments, you need to gain XP. Gaining XP and collecting tokens is the lifeblood of the online gaming experience.

One of the more enjoyable parts of Christmas (other than opening gifts of course) is going out to find the perfect tree, struggle bringing it into the house, and decorating it. As the years went by, I realized that our tree looked exactly like every other tree in the neighborhood: the same lights, the same angel at the top, and the same red, green and white ornaments.
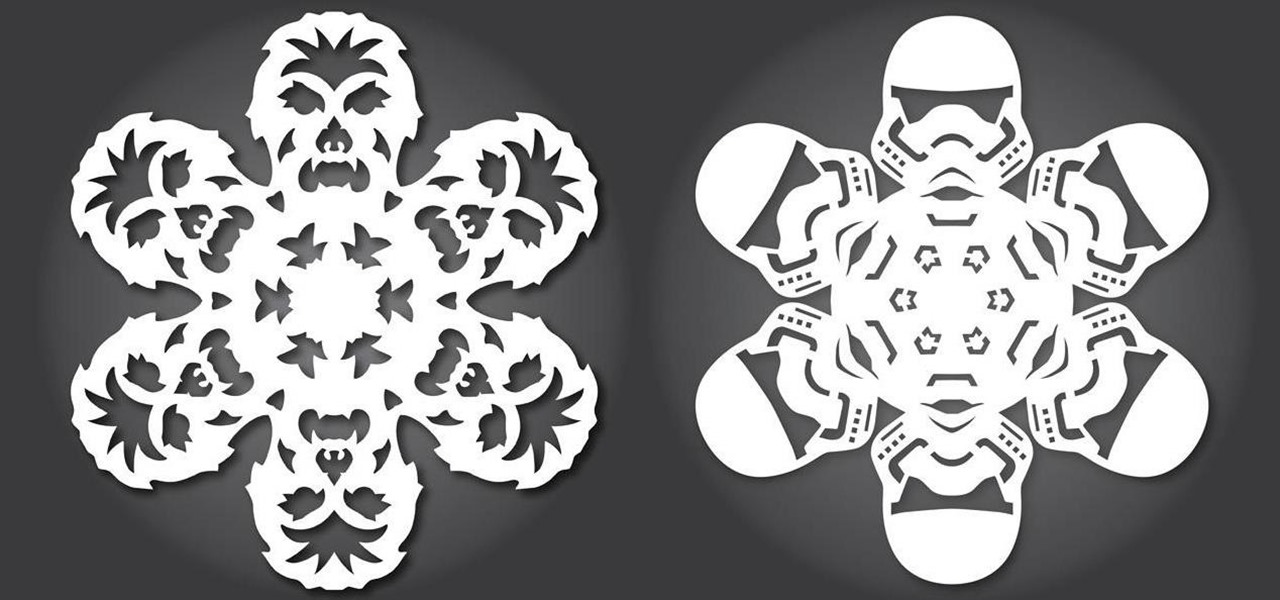
Everyone knows how to make paper snowflakes, but the kind you learned to cut in kindergarten can get a little boring. However, they are free DIY holiday decorations, and they don't have to be a generic snowflake design. They can be anything you want, from nerdy math kirigami to all the Star Wars characters you can think of!

The new Call of Duty: Black Ops 2 is the hottest game on the market right now, and there's no doubt it'll end up being the most unwrapped gaming gift come Christmas morning. The first-person shooter hopes to carry on the tradition of its many predecessors in bringing the most action-packed gaming modes, along with a high-replay value, to its legions of fans.

This video is designed to help deaf people, or those with hearing impairments, learn how to do basic first aid. Specifically, this video deals with sever bleeding and how to stop it, and is taught in sign language.

Deaf people are just like everyone else, and they have a responsibility to save lives just like the rest of us. Those with hearing impairments might not be able to benefit from most online first aid training, but this video is signed to give those with hearing problems the info they need to help out.

Pixel Perfect is the "perfect" show to help you with your Photoshop skills. Be amazed and learn as master digital artist Bert Monroy takes a stylus and a digital pad and treats it as Monet and Picasso do with oil and canvas. Learn the tips and tricks you need to whip those digital pictures into shape with Adobe Photoshop and Illustrator. In this episode, Ben shows you how to create a magical enchanted dagger in Photoshop.

The Library of Congress video archives brings this early nineteenth century dance lesson demonstration. Follow along with the performers as they show off their traditional moves, dancing a Quadrille combination step dance. It might take a bit of dance practice, but grab your partner, put on some music, and follow the steps. Watch this video traditional dance tutorial and learn how to do an early nineteenth century Quadrille step combination for figures balancé and tour de mains.

Learn the French hand gesture for "I was my hands of it" ("je m'en lave les mains").

Here is a video tutorial on making a delicious stuffed pepper. It is easy to make, pure taste, low calories/ low carb, no meat, many varieties possible, & can be a starter, main course, vegetable side dish or snack.

Everyone gets cut every once in a while, but sometimes those cuts can be more serious than expected. It could turn into severe bleeding, and there's a certain way to deal with this type of bleeding in a victim. How would you treat someone who was bleeding severely?

This video shows us how to replace a broken iPod screen. First thing to do for this is to remove the broken screen which is actually connected to the main board. The screen is actually connected to the main board with a very short ribbon cable. Now all you have to do is to pull the screen away but before doing that there is a pen socket, a white colored socket and above this is a black clip which can be clipped open. Using the tip of your finger just push the clip down and it will expose a bu...

Have you ever heard of cricket? No, we're not talking Jiminy Cricket or the wireless cell phone service provider. We're talking about CRICKET. The team sport, nicknamed "the gentleman's game," is the popular sport of choice in places like India, Australia, South Africa, Sri Lanka, England, Pakistan and Zimbabwe, though not America. But guess what? It's very similar to the American pastime we all love so much— baseball.

This is working about working with sources: Quotation, Summarizing and Paraphrasing. Quotation: When directly quoting an outside source, the author's words should be taken verbatim. Quotation can lend the essay credibility. Too much quotation makes it sounds like you, the writer don't have anything to say. Quotes should be used only when the writer needs to be precise, clear, and powerful. You should use the quotes when the person you are calling said in a unique way that really can't be put ...