If you're tired of Google tracking you, but love how Chrome works, CyanogenMod has you covered. Their browser is called Gello, which is based off Chromium, Chrome's open-source counterpart. It's basically a souped-up version of Chrome—without all of the intrusive Google stuff. So if you're uncomfortable with Google displaying personalized ads based on your browsing history, or using your location to bring the "Physical Web" to your phone, you won't have to worry about any of that with Gello.

Microsoft's HoloLens is certainly a leap into the future of mixed reality interfaces, but it's not without drawbacks.
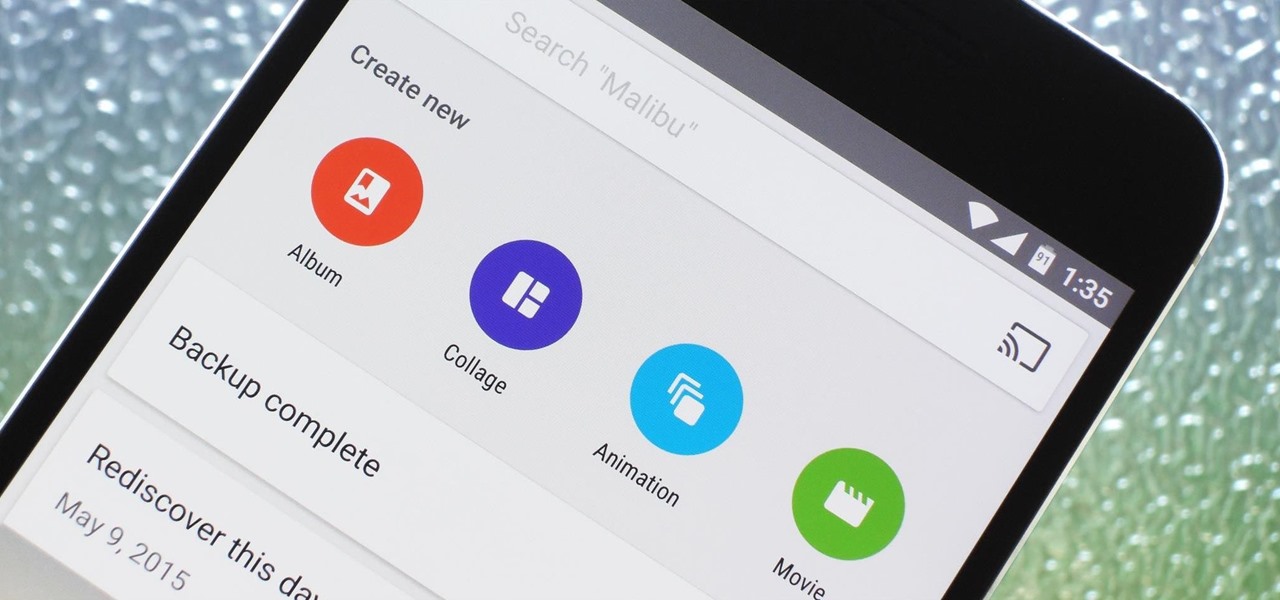
Google Photos is one of the best photo management services out there. It allows you to back up an unlimited amount of high-quality images without ever paying a dime, the photos and videos sync flawlessly across all of your devices, and its neural network-powered visual search feature seems like something that was pulled directly out of a Sci-Fi movie.

Having your phone on during a movie is a major annoyance to the majority of moviegoers, a fact that some theaters learned the hard way. One major film release is taking a different approach, however, and actively encouraging you to turn on your smartphone—during the end credits, at least. That film would be The Angry Birds Movie, and it's hitting theaters on Friday, May 20th, 2016. Rovio and Sony have been heavily promoting this upcoming 3D animated comedy, and the two worked closely together...

Images of the newest Moto X flagship phones surfaced over the weekend, and it looks like Motorola has a cool new feature in store for the handsets, which are tentatively titled Vertex and Vector Thin.

One of Android's biggest strengths is its ability to interact with other operating systems. When you plug your phone into your Windows PC, you instantly see all of the files it holds—and all it takes is a simple syncing app to do the same with Mac. To top that off, apps like Pushbullet and Join bridge the gap even further by allowing you to share links, files, and messages between all of your devices.

Hello everyone! I hope you are having a great day so far. Today, instead of caring about networks we are going to talk about subnetting based on host requirements as promised in my first article about subnetting. Just like in the previous articles we will jump right into the examples because that's the best way to learn.

Without explicit cooperation between Apple and the US government, authorities could still be monitoring Apple users. According to The Information, Apple is worried the servers it has been using might be bugged. We already know the NSA intercepts equipment to install backdoors, so this is a legitimate concern.

For many people, the two main advantages of buying a Nexus device are prompt updates and the ability to root without much hassle. But in a cruel twist of fate, these two features are almost mutually exclusive, since OTA updates will refuse to run on rooted devices.

Welcome back to another tutorial on functions. Last time, we looked inside memory to see what functions looked like in the flesh and all that Assembly was pretty nasty. At least you have some exposure to it. This time, we will be examining how functions work with the stack.

Hello there, reader! If you've clicked on this How-to then it means you are interested in learning some C programming or just generally curious about what this page has to offer. And so I welcome you warmly to the first of many C tutorials!

Smartphones are almost always connected to the internet, so it stands to reason that they can be hacked remotely. Or perhaps a jealous boyfriend or girlfriend got hold of your device physically, in which case they could've potentially installed a keystroke logger, a virus, or any other type of tracking app to spy on you.

Not too long ago, Sony was looking to create a method for theming the interface of their Xperia smartphones and came up with a framework called Runtime Resource Overlay (RRO). They then contributed this framework to Android's main code base, and Google has since taken over the development of RRO as a way for manufacturers to implement themes in their skinned versions of Android.

Hello, my web huggers! In today's tutorial we will learn how to use the Google Hacking Database (GHDB) developed by Exploit Database, to find vulnerable web servers and "juicy" information.

In this day and age, maintaining your privacy is a perpetual battle, and doing so with an internet-connected device like your smartphone is even more of a struggle. Every website you visit, every app you install, every message you send, and every call you make is a potential vulnerability that could expose you to prying eyes.

You're smashing your keyboard to increase your screen brightness, yet it won't go any higher, but you know you've been able to set it higher before. Angered by this, you get up and move your laptop, only to suddenly notice that the display does in fact get a lot brighter.

When it comes to smartphones, the biggest complaint voiced by most users is battery life. Sure, it's unrealistic to expect your Android device to run for weeks without a recharge, but many folks struggle to even make it through the day without having to top off their battery.

To use Apple Pay in iOS 8, you had hold your iPhone to the card reader first, and then you could either switch to a different card or pay with your default one. Now, in iOS 9, you can access your Wallet (which replaces Passbook) on the lock screen before you get to the reader.

With an Android device, you can replace almost any default app with a third-party offering. Don't like your home screen app? Replace it. Tired of the text messaging interface? Upgrade it. The same can be said for Android's lock screen. But while many third-party lock screen apps are available, so far, only one has been designed with the Samsung Galaxy S6 and its fingerprint scanner in mind.

OR rather How to make the Backdoor Persistent: Hello, my Cold and Merciless Hackers,

We live in world where it is hard to stay positive all of the time. I know at times it gets hard to see the bright side of things and sometimes you just want to give up and let life pass you by. This kind of thinking is usually indicative of a deeper psychological problem which requires professional help, but what about when you can't go see a therapist?

Show your significant other just how much you love them by surprising him or her with one of life's most precious, romantic gifts—bacon! Best thing is, this passionate treat works for any day of the year (Valentine's Day, a first date, anniversary, etc.), since love and bacon go hand in hand.

Android's permission system doles out access to certain system-level functions. Without it, our favorite apps wouldn't be able to perform their most basic operations. Picture a camera app that didn't have permission to access your camera sensor—now that wouldn't be much fun at all.

We've previously covered an app called YouTube Floating Popup Player which let you watch YouTube videos anywhere on your Android device, but it has since been removed from the Google Play Store due to infringement of certain policies.

Maps is great for making sure you always get to your destination, until you miss that critical turn because you couldn't hear the turn-by-turn directions.

While it's currently impossible to go back in time, there is something wonderful about being able to undo the stupid stuff that you just did. While this is only really possible in the digital world, it does save you from real-life repercussions. If you've ever sent an email to the wrong person or sent some not-so-genius text messages, you know exactly what I'm talking about.

Being in a band, I exposed myself to years of extremely high volumes, so I can't hear as well as I once did. I'm not concerned about going deaf or anything, but I tend to have the volume raised to the max, beyond the "high volume" warning, whenever listening to music on my OnePlus One with headphones.

Dulce de leche is a beautiful, caramel-like spread that you can slather onto bread or use to flavor cakes, cookies, or flan. You can also use it as a drizzle for ice cream, chocolate candies, and pastries. It tastes like heavenly toffee, translates roughly to "milk candy," and is popular all over Latin and South America. A version of the confection is also popular in the Philippines, in Russia, and is known in France as "confiture de lait." The traditional way to make dulce de leche is to slo...

We're a little butter-obsessed here, and that includes topics on why butter should always be browned, the rationale behind clarifying butter, and even how to make a DIY butter candle. And while some may consider the problem strictly one for the first world, we're always very interested in ways to spread cold butter on toast without ripping the bread to shreds. If you read that post, you know the ingenious solutions are many and range from grating your butter to buying a heated butter knife.

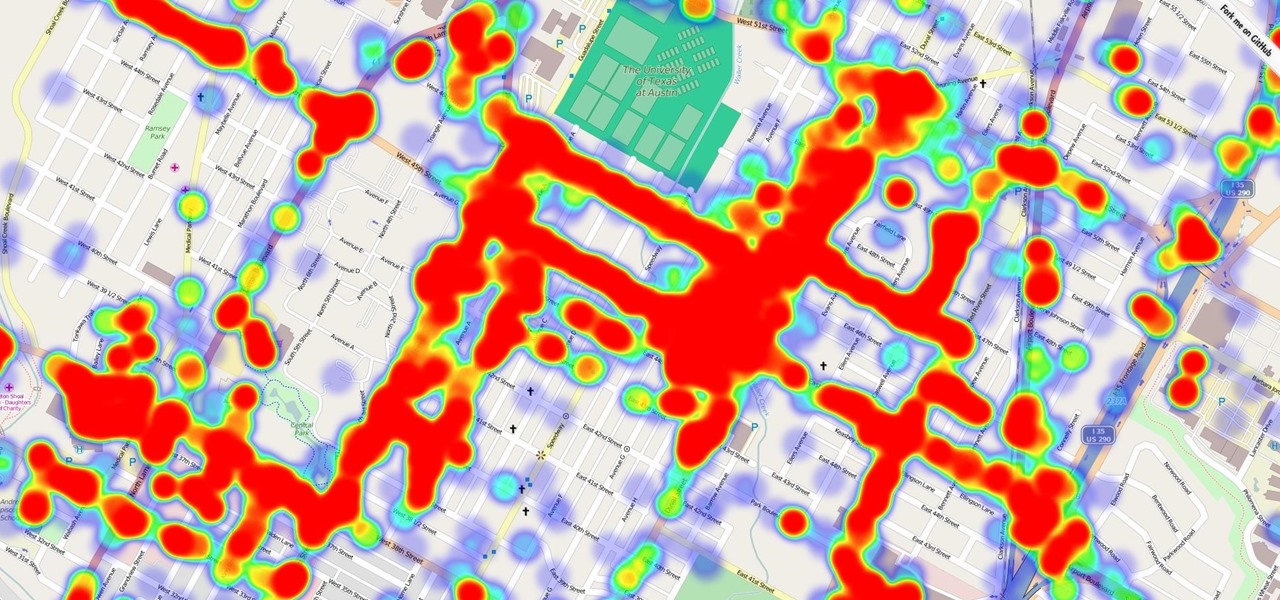
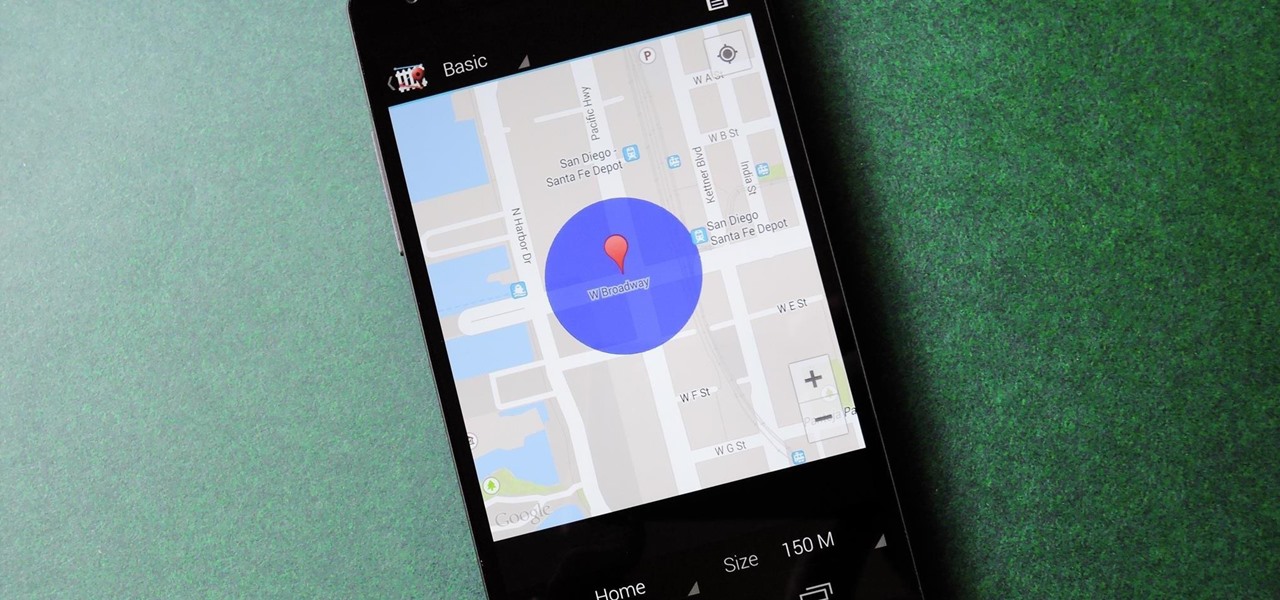
With an Android device left at its default settings, your location history is automatically recorded. You can view and manage this data, but the simple interface of points plotted on a map leaves a lot to be desired.

Eating healthy poses a challenge nowadays with so many options that taste great but aren't really good for you. Nutritionists have made it their life's work to understand what actually does a body good. Here's how you can follow their example.

Many Android games use large, storage-heavy OBB files to store supplemental data. Generally, games with high-end graphics download these extra files when you install them from the Google Play Store.

There's a never-ending selection of app launchers that want a permanent spot on your Android device. While some keep the stock-Android look with beefed-up versions of Google's launcher, Blur is relatively new on the scene, with a unique approach to app management that sets it apart.

The Galaxy S5's fingerprint scanner feels like something straight out of a sci-fi movie. Giving you the ability to lock your device without having to fuss with a PIN or password every time you go to use it, the feature is definitely one of the device's main selling points, especially now that you can use it to unlock individual apps.

Depending on who you ask, internet connectivity should be a basic human right. With Google recently embarking on a project to provide internet capabilities to remote corners of the world using balloons and satellites while Facebook attempts to do the same with unmanned drones, the concept of free web access is steadily gaining steam.

With Safestrap bringing custom recovery functionality to the AT&T and Verizon Wireless variants of the Samsung Galaxy S5, it's high time we covered this process for all other versions of the GS5.

Just the fact that you own an Android device means you're privy to an entire world of third-party development. Many of the mods you'll see here on Gadget Hacks can be performed fresh out of the box, but with root and Xposed, the list grows longer. But to truly be able to take advantage of all that Android's massive development community has to offer, you'll need to have a custom recovery installed.

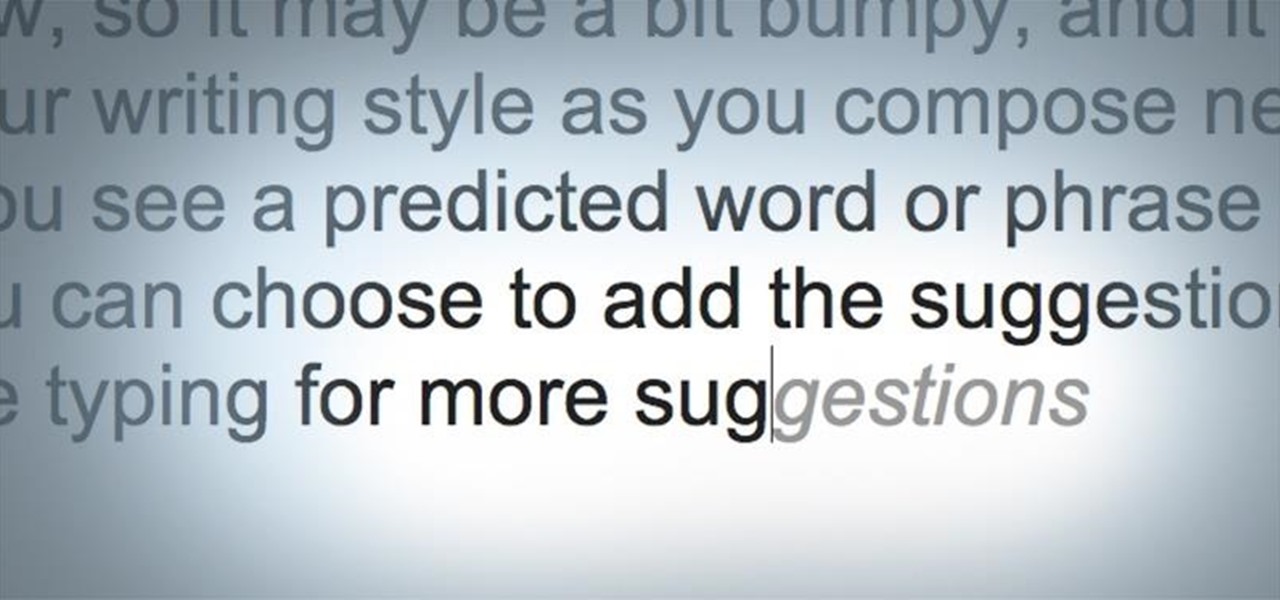
Android has had predictive text for a while now, both with stock and third-party keyboards such as Fleksy, SwiftKey, TouchPal, et al. Apple is even getting on board, with stock predictive text and third-party keyboards for iOS 8, slated for public release later this year.

One of the coolest features of the Galaxy S5 is its IP67 certification. This means that the S5 is internally impenetrable to dust and can be submerged in water for thirty minutes at a depth of one meter. It's definitely a handy feature for folks who've lost a phone to a toilet in the past.

We live, work, and play in drastically different environments, so it only makes sense that we'd want our Nexus 5 smartphones to automatically adapt to our needs when in certain locales at certain times.