Posture and etiquette for professional modeling is crucial to maintain a poised character both on and off the runway. Learn pro modeling posture and etiquette with this free high fashion video series.

In this series of instructional videos you'll learn how to cut and style hair into a retro 1960s hairstyle. Expert hairstylist Jan Cuni shows you step by step how to pump up the volume in your hair with a combination of a haircut and styling secrets. You'll learn how to cut your hair, use a blow dryer to add volume, and pick the right styling products to maintain your new funky retro 60s look.

Everything from disposed of drugs to hormones and disease-causing bacteria — anything that is rinsed or flushed down the drain — can contaminate wastewater.
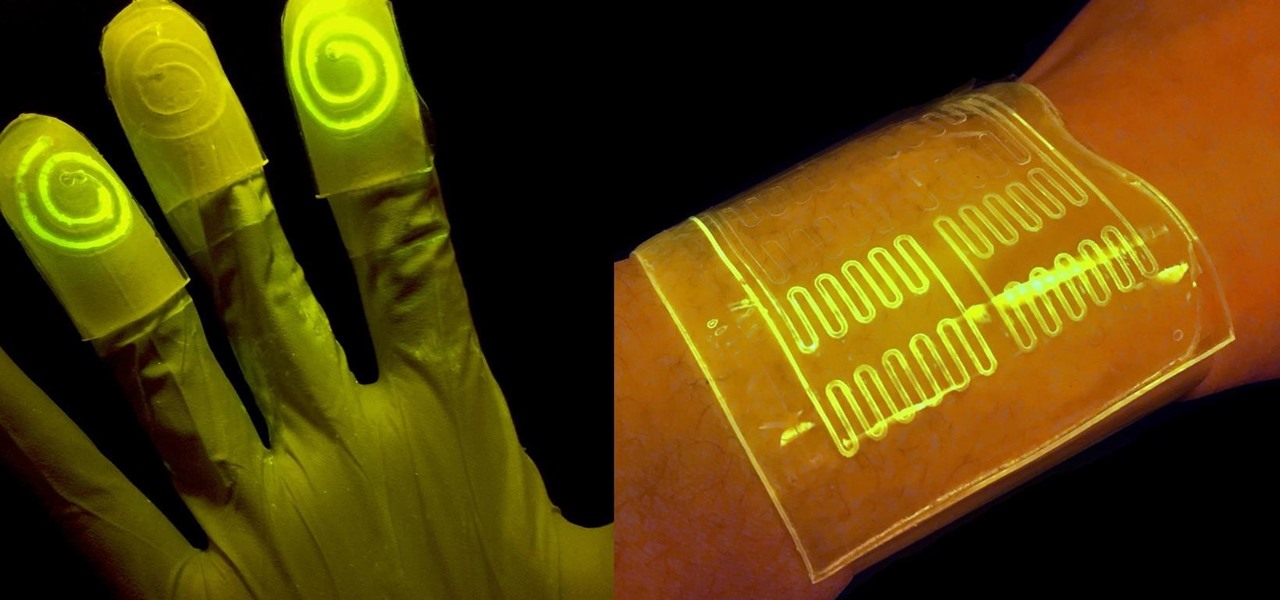
While at work, you notice your gloves changing color, and you know immediately that you've come in contact with dangerous chemicals. Bandages on a patient signal the presence of unseen, drug-resistant microbes. These are ideas that might have once seemed futuristic but are becoming a reality as researchers move forward with technology to use living bacteria in cloth to detect pathogens, pollutants, and particulates that endanger our lives.

There are a lot of things on your computer that can reveal information about you when you are surfing the Internet. If you are like me, then you will do anything to maintain your privacy and prevent those little leaks of information from happening. Here's a list of a few of the "threats" that can reveal information about you:

Love fresh garlic but don't have the outside space or right climate to grow it? Not to worry! This video is here to show you how to grow your very own fresh picked garlic indoors. Follow these easy steps and you'll have a delicious seasoning in a couple of weeks, and full grown heads of garlic in a couple of months!

Your first bank account can be exciting and confusing at the same time. Check out this video and learn how to manage your money and accounts so you don't wind up in the red. You don't have to earn an MBA to make good financial decisions; this video offers plenty of suggestions to keep your accounts on track.

Splits are popular in dance and cheerleading, do you think you can do one? Practice, practice, practice and check out the helpful tips in this video to avoid injury.

Learn to make this easy mini paper Uzi gun for gaming with your friends! Supplies: Scissors, Scotch tape (Note: DO NOT USE MASKING TAPE OR DUCT TAPE; IT WILL NOT TURN OUT WELL), lots of paper. 1. Take one piece of paper and roll it up from top to bottom to make a short tube. Tape it. 2. Take another sheet of paper and do the exact same thing that you did to the first one and tape it as well. 3. Take a sheet of paper and roll it up from side to side (long ways). Make the hole in the middle abo...

Hallmark Christmas ornaments are a great collectible item for the whole family to enjoy. Learn how to maintain, store, repair, and buy Hallmark ornaments in this free video series about Christmas collectibles.

As NASA nears the launch of another mission to the Moon in 2024, and a subsequent mission to Mars in the 2030s, augmented reality is increasingly being woven into the normal space operations to test various capabilities.

One of the most popular things to do on Snapchat is to earn a Snapstreak. This occurs when you and one other friend have sent snaps (not chatted) to each other within 24 hours for at least three consecutive days. One you've passed the three-day mark, then you and your friend will receive a fire emoji next to your names.

With new diet and health claims coming at you everyday, it's sometimes hard to know what to believe. Well, here's a bright spot: A pair of studies confirm that whole grains are healthy for you, and for the diversity of microbes living in your gut.

Six people have died from fungal infections in Pittsburgh hospitals since 2014—that fact is indisputable. The rest of the situation is much vaguer. A lawsuit has been filed against the hospitals on behalf of some of the deceased patients, alleging that moldy hospital linens are to blame. While the lawyers argue over who's at fault, let's look at how this could have happened.

Before I continue with a topic on strings, we first require some fundamental understanding of how memory works, i.e. what it is, how data looks in memory, etc. as this is crucial when we are analyzing vulnerabilities and exploitation. I highly suggest that your mind is clear and focused when reading the following article because it may prove to be confusing. Also, if you do not understand something, please verify all of your doubts, otherwise you may not completely understand when we touch on...

With over two billion websites floating around cyberspace — only 400 million are estimated to be active — you need every tool you can get to stand out. Great design, fonts that capture attention, and SEO placement are all necessary ingredients to success.

Just because augmented reality is the technology of the future doesn't mean it can't reach into the past of computing.

The New York Times has made a habit of publishing augmented reality stories throughout 2018, and now the media giant's magazine is getting into the act, too.

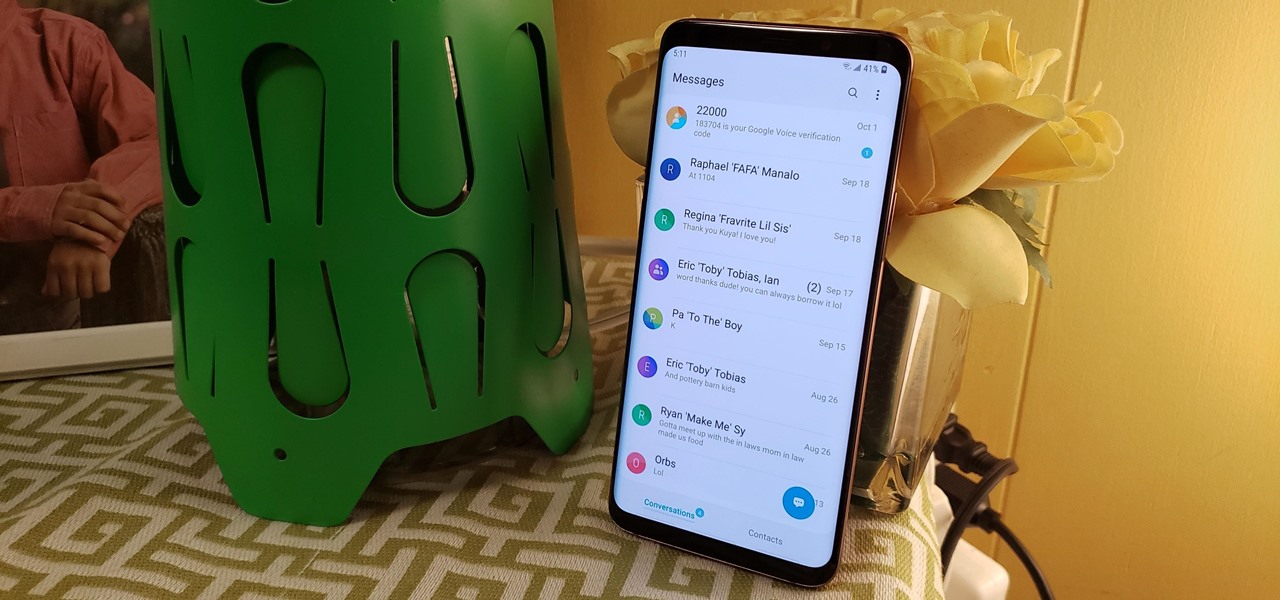
Samsung's version of Android Pie has landed on Galaxy handsets like the Note 9, S9, and S8, though we've known what to expect thanks to leaked beta versions of the software a few months back. The newly dubbed One UI has plenty of new features and improvements, but some of the first you might notice are the visual improvements to the default messaging app.

One of the leading chipmakers for smartphones is getting ready to announce a new processor made specifically for augmented and virtual reality headsets.

The conversation of which operating system is most secure, macOS vs. Windows, is an ongoing debate. Most will say macOS is more secure, but I'd like to weigh in by showing how to backdoor a MacBook in less than two minutes and maintain a persistent shell using tools already built into macOS.

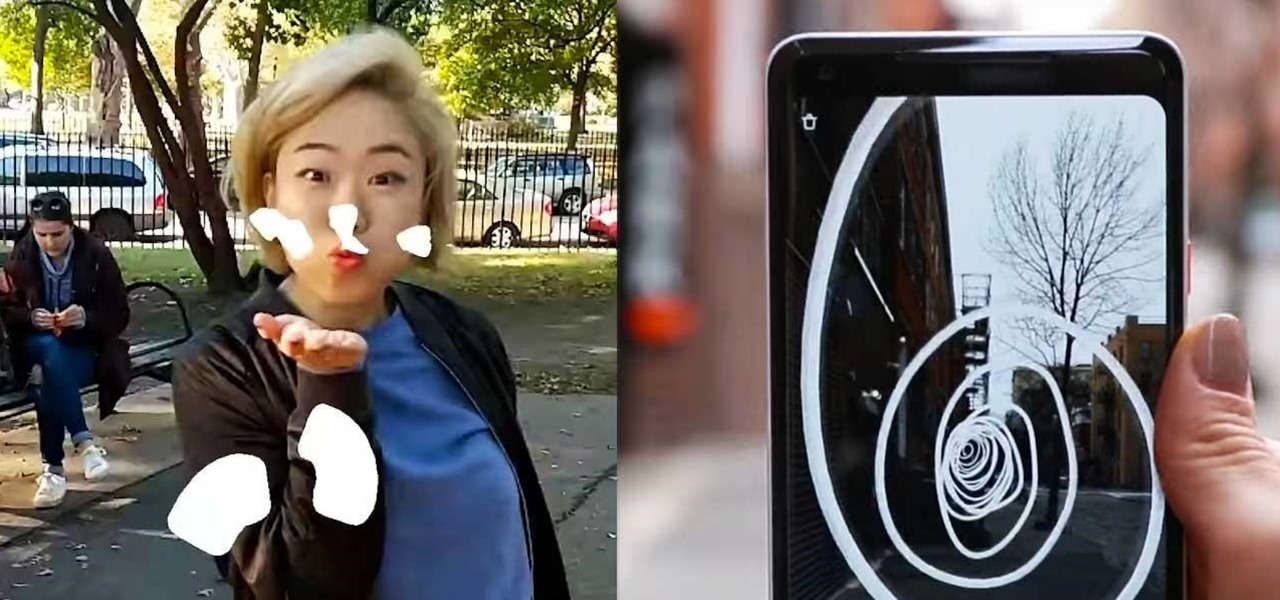
As part of its ARCore push this week, Google has promoted Just a Line from one-time AR experiment to a full-fledged app.

The same approach to augmented reality that some companies use to improve workforce productivity could also make it easier for car owners to operate and maintain their vehicles.

Just days after the launch of Google Poly, the marketplace for 3D virtual objects that developers can use for augmented and virtual reality apps, SketchFab, the current leader in the space, is firing back with a major enhancement to its platform.

Nauto, which develops driver-monitor cameras and algorithms for autonomous vehicles, is among a growing list of driverless startups able to attract tens of millions of dollars in funding after raising $159 million in its latest round of financing.

Earlier this month, Edgybees was the first game developer out of the gate with an augmented reality racing game for DJI drones called Drone Prix AR. Now, as the month closes, they are crossing the finish line with the first gaming app for Epson Moverio BT-300 Drone Edition smartglasses.

Headphone drama has been all the rage in the past year, with Apple killing off the headphone jack and trying to force AirPods upon its users (Apple, stop trying to make tiny, expensive, easy-to-lose earbuds happen. It's not going to work).

It is a beautiful, yet scorching day here in Los Angeles, and the only reason I would ever step outside from my air-conditioned castle would be to grill out by the pool. There's just one problem: backyards are few and far between here in The City of Angels.

Welcome back, my tenderfoot hackers! As hackers, we often are required to get past antivirus (AV) software or other security measures. To do so effectively, we need to have some understanding of how AV software works. In this tutorial, we will take a cursory view of how AV software works so that you can better strategize on how to evade detection by it.

Sometimes it's not the look of a product that makes it unique, but the thought that went into it. That's what struck me about TobyRich's SmartPlane—it isn't the most elegant toy on the market, but its simplicity and function make it a winner.

Welcome back, my greenhorn hackers, and happy New Year! Now that your heads have recovered from your New Year's Eve regaling, I'd like to grab your attention for just a moment to preview 2015 here at Null Byte. I hope you will add your comments as to what you would like to see, and I'll try to honor as many requests as I can.

Automatic brightness adjustments are supposed to make it easier to maintain good visibility on your phone, but it really never works as intended. It usually doesn't adjust properly, leading you to manually pull up the Control Center to adjust brightness via the slider.

Gatorade: its popular red flavor can stain the whitest fabric, and its sweet taste is oddly refreshing after breaking a sweat. If you've ever participated in a sport, you probably spent halftime at games and practice breaks chugging the stuff. Though it made its name as a sports drink, Gatorade is also a well-known hangover helper—but its beneficial and interesting uses don't end there. The brightly colored drink can do so much more than just hydrate you.

Just short of a week after its release, the new HTC One has been rooted thanks to Android devs beaups and jcase, the same guys that brought us S-OFF for the original HTC One (M7).

Cavandoli Macrame (also called Tapestry Knotting) is an intricate form of knotting used to create geometric patterns. The Cavandoli style is done mainly in a single knot, the double half-hitch knot. Reverse half hitches are sometimes used to maintain balance when working left and right halves of a balanced piece.

While websites may run smoothly without any noticeable vulnerabilities, there's always the looming threat that any background weakness in the site can be exploited by hackers. Once a site is compromised, it can be difficult to get it fixed without the proper help. Google has recently launched a new series entitled "Webmasters help for hacked sites”, which teaches web developers and site owners how to avoid getting hacked and how to recover their website if it gets compromised in any way.

In the first part of this series, we took a factual and technical look at the history of the Internet. I explained how all of these wires and servers got here in the first place. Obviously, a firm did not just create and build the Internet around 1995! Now that we know how the Internet came to be, we can get into the really fun stuff—what the Internet looks like now! Well, that's not quite the network design I was talking about, but it does show what the Internet looked like back in 2007 befo...

Every time you make a call or send a text, you're giving the recipient your phone number. This can be quite the security vulnerability, opening yourself up to scammers, spammers, and the feds. In this how-to, we'll look at what a burner phone is, why you might want one, and how to get started using a free second phone number on your regular smartphone.

The software released in the 2015 iterations of the Samsung Galaxy line of devices—the S6, S6 Active, S6 Edge, S6 Edge+, and Note 5—have some pretty neat camera features that give these devices arguably the best smartphone camera on the market today.

Whether you're looking to add a substantial coding foundation to your hacking skill set or want to get a job in programming and development, knowing one or two programming languages just isn't going to cut it.