Learn how to do the one handed neck wrap using a mace with this tutorial. This is an advanced move for a drum major or baton twirler. Watch this how to video and you will be able to do the one handed neck wrap with a mace.

Learn to do the thumb roll using a mace with this how to video. This is an advanced technique for drum majors or baton twirlers. Watch this tutorial and you can do the thumb roll with a mace.

Learn how to do the palm spin using a mace with this how to video. This is an advanced move for a drum major or baton twirler. Watch this how to video and you will learn how to do palm spin with a mace.
Check out this Blender video tutorial all you wannabe digital animators out there to see how to use paths and dupliframes in your 3D modeling.

Painting a ceiling may seem like a daunting task, but you can easily get it done without making a major mess. Find out the best way to paint a ceiling in your home.

This video shows you three of the major causes for blisters and how to prevent them from occurring.

This pattern is a great fly to use for fly fishing when fish are feeding on the bottom. Crawfish are a major part of a trout's diet, and hence this pattern is one to use when you want a "go to" fly to produce results.

An intensive analysis of the "blue third," a quarter-tone that lies somewhere between the major and minor third and is a key constituent of the blues scale that all harmonica players must master. With Satan & Adam harpist Adam Gussow.

Are you serious about becoming a bonafide hacker? Then you simply must learn how to hack SSL passwords using ARP poisoning. ARP poisoning, also known as ARP spoofing, involves attacking an ethernet wireless network by looking at the data frames on a LAN (local area network). Resultingly, you can sniff plaintext passwords, SSL passwords, and even manufacture denial-of-service attacks.

The Locrian mode has the formula 1, b2, b3, 4, b5, b6, b7. Its tonic chord is a diminished triad (Bdim in the Locrian mode of the diatonic scale corresponding to C major). This video explains how to play scales in the Locrian mode on the piano and also gives a great breakdown at the end of each mode in C.

There are many tools out there for Wi-Fi hacking, but few are as integrated and well-rounded as Bettercap. Thanks to an impressively simple interface that works even over SSH, it's easy to access many of the most powerful Wi-Fi attacks available from anywhere. To capture handshakes from both attended and unattended Wi-Fi networks, we'll use two of Bettercap's modules to help us search for weak Wi-Fi passwords.

The venture arms of Samsung and Verizon Ventures, along with Comcast, are among the strategic investors backing startup Light Field Lab and its glasses-free holographic displays in a $28 million Series A funding round

With CES in full swing, it seemed like Magic Leap would have little to announce at the major tech event, but it turns out that one of its partners has weighed in with a rather substantial update regarding the company.

When it comes to attacking devices on a network, you can't hit what you can't see. Nmap gives you the ability to explore any devices connected to a network, finding information like the operating system a device is running and which applications are listening on open ports. This information lets a hacker design an attack that perfectly suits the target environment.

Smartphones and laptops are constantly sending Wi-Fi radio signals, and many of these signals can be used to track us. In this guide, we'll program a cheap IoT device in Arduino to create hundreds of fake networks with common names; This will cause nearby devices to reveal their real trackable MAC address, and it can even let an attacker take over the phone's data connection with no warning.

Wi-Fi devices are continually emitting "probe frames," calling out for nearby Wi-Fi networks to connect to. Beyond being a privacy risk, probe frames can also be used to track or take over the data connection of nearby devices. We'll explain how to see nearby devices emitting probe frames using Probequest and what can be done with this information.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

Sharing your Wi-Fi password is like giving an unlimited pass to snoop around your network, allowing direct access even to LAN-connected devices like printers, routers, and security cameras. Most networks allow users to scan and attempt to log in to these connected devices. And if you haven't changed the default password on these devices, an attacker can simply try plugging them in.

Wi-Fi signals have limited range, so if you live in a two-story house or work in a larger office, you may have set up multiple routers or repeaters to ensure full wireless coverage. Sadly, Android handles the transition between networks pretty poorly.

How to Draw Misa Amane of Death Note coming model who had an immense crush on Light Yagami, which quickly became a major obsession,to the point where she would do anything for him. For the full tutorial with step by step & speed control visit: how to draw

It's been almost a year since all major banks blockaded WikiLeaks from recieving funds. It's their only source of actual revenue, so help out if you can.

Jean Grey was one of the five original X-Men, and is old enough to have gone through some major changes in her career. She's more recently been called Phoenix and Dark Phoenix, and that's what she's known as in her appearance in Marvel vs. Capcom 3. This video will show you the basics of how to fight with Phoenix / Dark Phoenix in the game, including combos and special moves.

Taylor Swift is one of the most talented and most beautiful musicians to grace the pop stage in quite some time. Her latest single "Mine" lives up to the legacy of her past hits by being insanely catchy and having really clever, deep lyrics. If you liked the makeup look she rocked in the music video, watch this. It will show you how to recreate that look yourself. No word on how to replicate the blonde guy though...

Combination locks are a major part of life for people High School, the Armed Services, and enough other places to make this video very useful to a lot of people. It will show you how to open any twisting combination lock (like a Masterlock) with using math or any other sophisticated skills or tools. All you need is a sharp knife and your fingers. Now you won't have to wonder whether Person X has your picture up in their locker or not anymore.

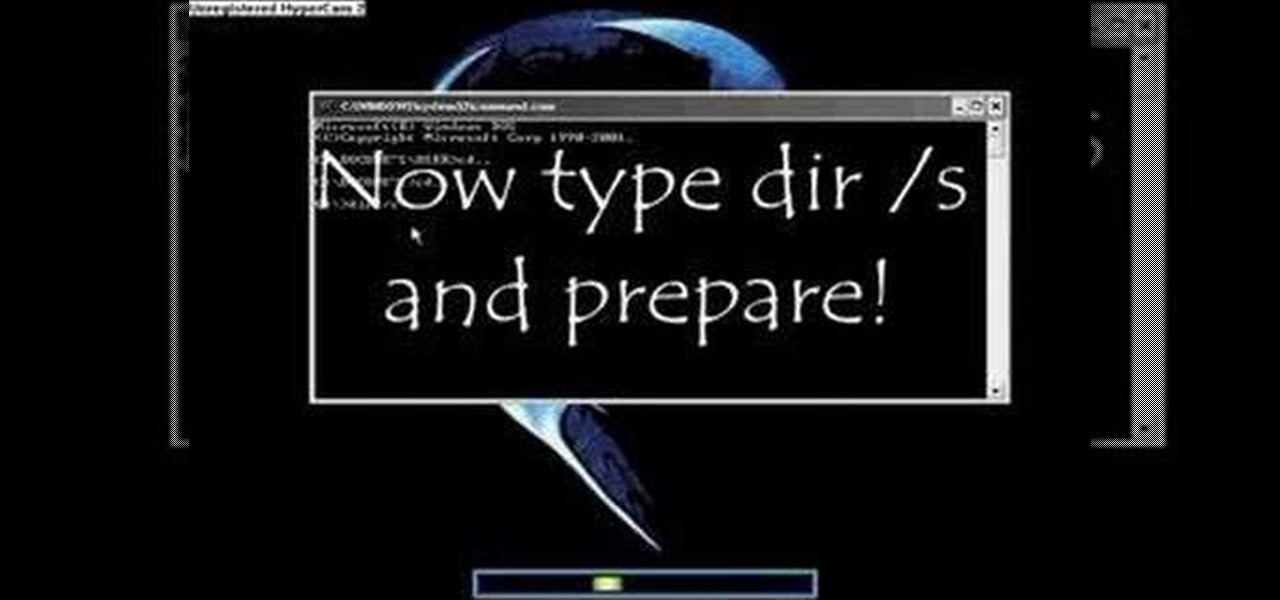
DOS may be a distant memory for most computer users at this point, but for many it will always be the first thing that pops into their head when they ponder PC computing. Nowadays, the only time most people see anything that even looks like DOS is if they're playing old PC games in a shell or something has gone very, very wrong with their computer. With this prank, you can make your friend believe that the latter has happened to them! All you do is open the DOS command program (Windows XP or ...

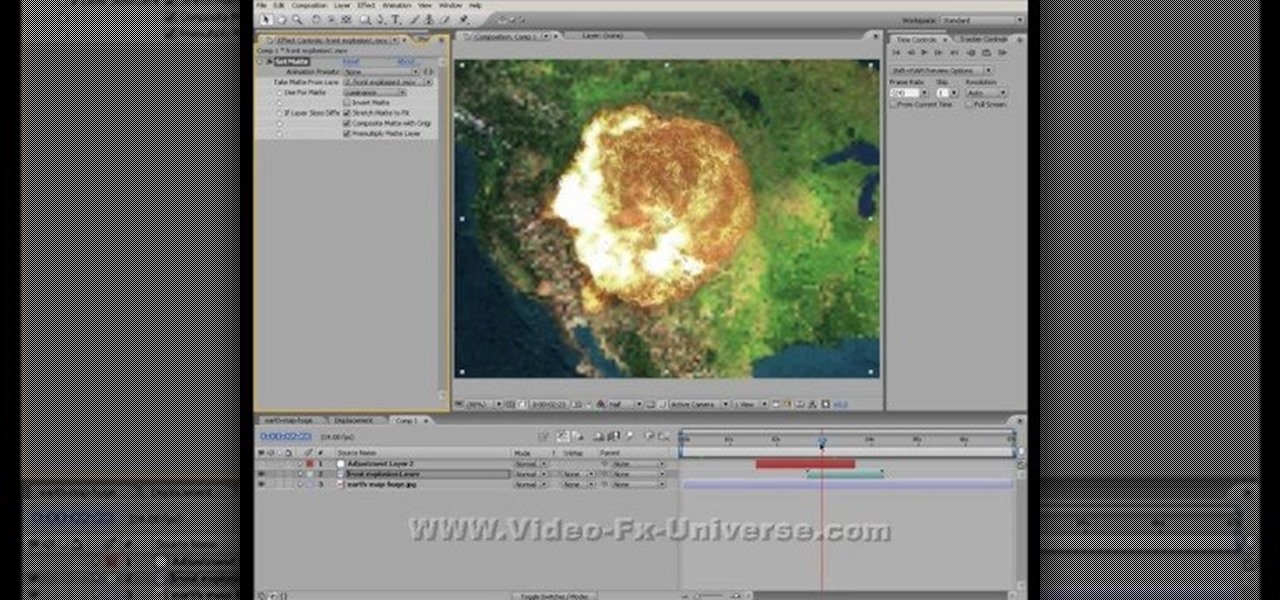
Not TOO many Western people want to see the United States nuked into the stone age. Some do, but not too many. Now you can simulate the effect on your computer! This video will show you how to use After Effects to simulate the effect of a nuclear blast or other major explosive catastrophe on a map of the US in 2D. This effect is used in many video games and movies, so master it yourself and we promise that you'll find cause to use it again at some point.

Work can be a rough place, especially if you're in construction or another laborious field of work, but that doesn't mean that anybody who works (or even doesn't work) isn't susceptible to work-related injuries. The most common workplace injuries are back injuries. This educational video, entitled "Back Your Back: Back & Muscle Injury Prevention" is all about reducing your risk of back problems.

In a wilderness survival situation, someone in your group suffering a major laceration is a catastrophe. Achieving sterility and suturing the wound closed will both be very difficult to achieve. This four-part video series features a detailed explanation and demonstration of how to use a basic first aid kit to suture a wound closed in an austere situation, such as out in the wilderness. Suturing a wound closed in an austere setting is a last resort, but knowing how to do it could keep you or ...

The powerhouse of space exploration, NASA (National Aeronautics and Space Administration), sheds light on Newton's laws of motion as pertaining to drag force on aircrafts. This is a great source for any aeronautics major. The infamous government agency breaks drag down for you.

Watch this tutorial to learn how to draw shock, fear, and terror facial expressions. Make sure to pause the video after each step and look at the screen every few seconds while you are drawing.

Ingredients for Yakitori (serves 2)

Ingredients for Yaki Gyoza (25 pieces)

Ingredients for Hiyashi Chuka (serves 2)

Ingredients for Green Tea Ice Cream (400ml/1.69 u.s. cup)

Stay tuned for the always enjoyable Cooking With Dog. This cooking show is hosted by a DOG named Francis! The show demonstrates how to make popular Japanese dishes.

Stay tuned for the always enjoyable Cooking With Dog. This cooking show is hosted by a DOG named Francis! The show currently focuses on how to make popular Japanese dishes. This video demonstrates how to make vegetable tofu nimono (vegetable tofu stew).

Stay tuned for the always enjoyable Cooking With Dog. This cooking show is hosted by a DOG named Francis! The show currently focuses on how to make popular Japanese dishes. This video demonstrates how to make Katsudon (Tonkatsu Deep Fried Pork and Egg Bowl).

Stay tuned for the always enjoyable Cooking With Dog. This cooking show is hosted by a DOG named Francis! The show currently focuses on how to make popular Japanese dishes. This video demonstrates how to make kakiage soba (mixed tempura soba noodles).

Stay tuned for the always enjoyable Cooking With Dog. This cooking show is hosted by a DOG named Francis! The show currently focuses on how to make popular Japanese dishes. Learn how to prepare Japanese Ichigo Daifuku, aka strawberry Daifuku. This is a Japanese dessert.