Elie Krieger from Food Network bakes up a scrumptious chicken pot pie. Her version will give you a healthy boost because she added extra vegetables and cut down on the fat. This southern dish is sure to warm up tummies everywhere and you can customize the ingredients based on your family's tastes. For example, you may want to use turkey instead of chicken, or possibly beef. Maybe your family likes different vegetables. This particular recipe uses chicken, onions, carrots, celery and green bea...

Take a look at the first place winner's tutorial on making a dress out of old tees for the Generation-t tee recon contest! Follow along with the steps in this fashion design video and make your very own quick and easy dress.
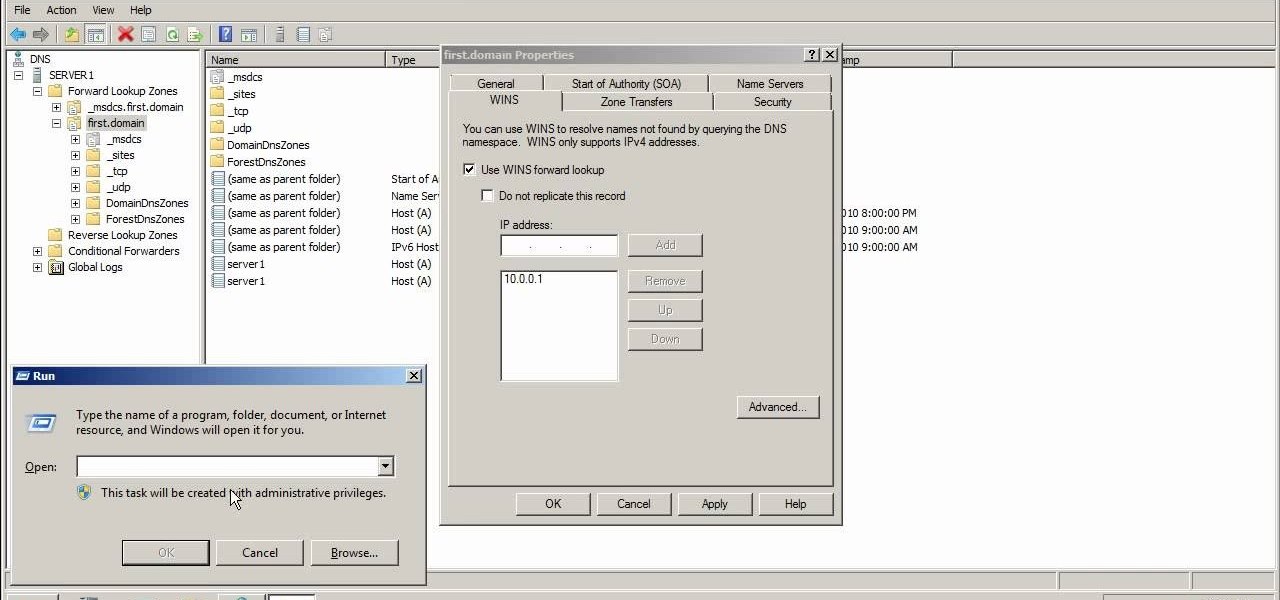
This video explains how to modify your DNS server to perform WINS lookups. Using Microsoft Windows Server 2008, you can perform WINS lookups across several networks which can resolve to a common resource. While Server 2008 cannot act as a WINS server, Server 2003 can.
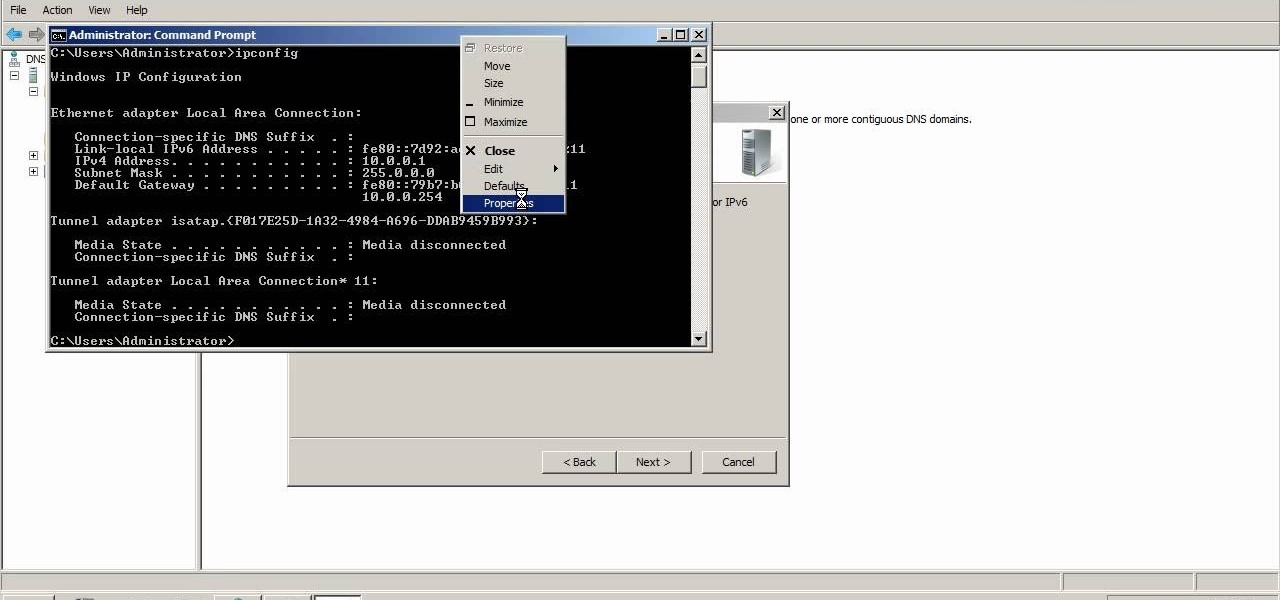
A reverse lookup zone will allow you to translate IP addresses to fully qualified domain names (FQDN). This can be a tremendous help against phishing in large organization. Keep your network secure by creating a reverse lookup zone in Windows Server 2003 or 2008.
In this tutorial, you'll learn a few standard methods for resolving less common and more complicated wireless network problems. It's an easy process and this video presents a complete guide. For more information, including a full demonstration and detailed, step-by-step instructions, watch this helpful home-computing how-to.

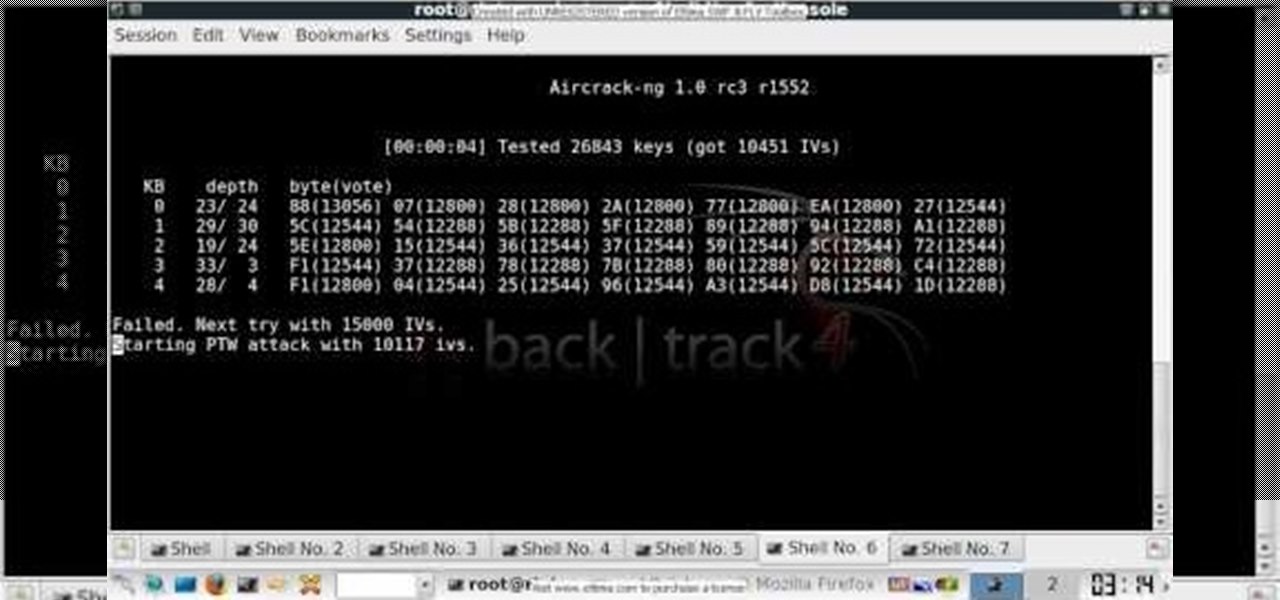
Learn how to use the Backtrack Linux distro and the Aircrack-ng WiFi security app to crack a WEP key. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

In this clip, you'll learn how to use the Backtrack Linux distro and the Aircrack-ng WiFi security app to crack a 64-bit WEP key. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

In this clip, you'll learn how to crack a WEP or WPA key on a GNU/Linux computer with GRIM WEPA. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

In this clip, you'll learn how to use the Backtrack Linux distro and the Aircrack-ng WiFi security app to crack a WEP key. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

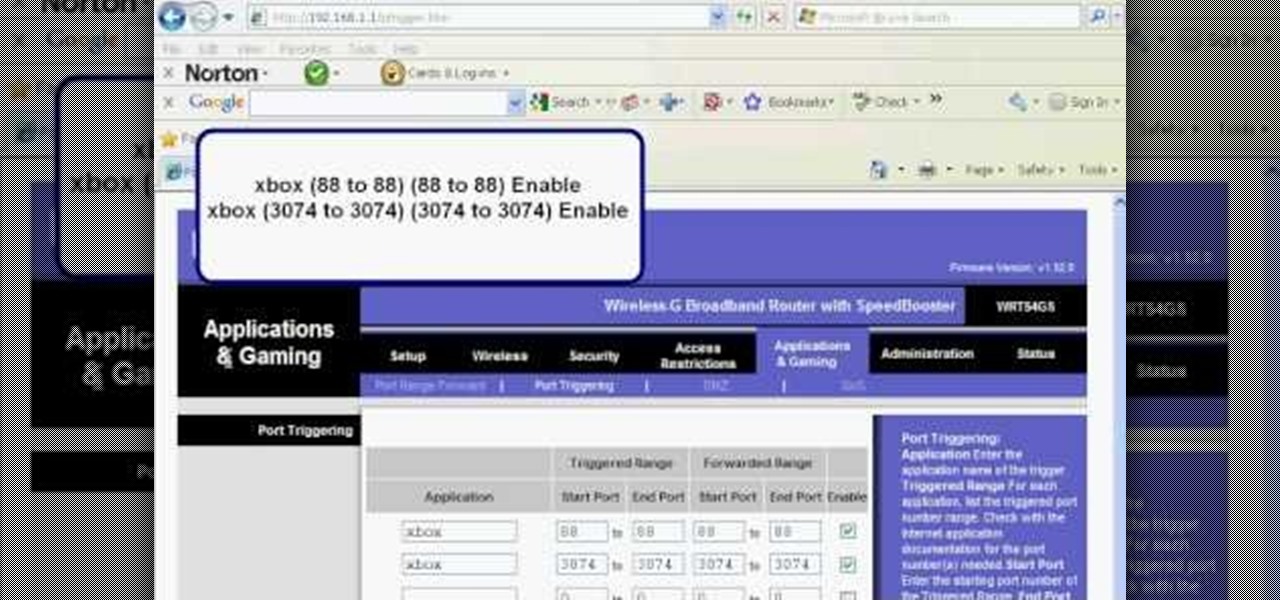
Before you can use Xbox Live 360, you'll have to allow your console to use certain ports that, by default, it may be blocked from using. One way to open up those ports is with port triggering. This helpful home networking how-to will walk you through the process of getting triggering set up in your own wireless router.

Overcome hardware differences in just a few simple steps- share files between your mac and PC and make your network truly seamless.

Use an old PC that has been setup as a server to perform helpful tasks such as backing up computers on your network, storing media files in a central location, share one printer with every computers computer in the house.

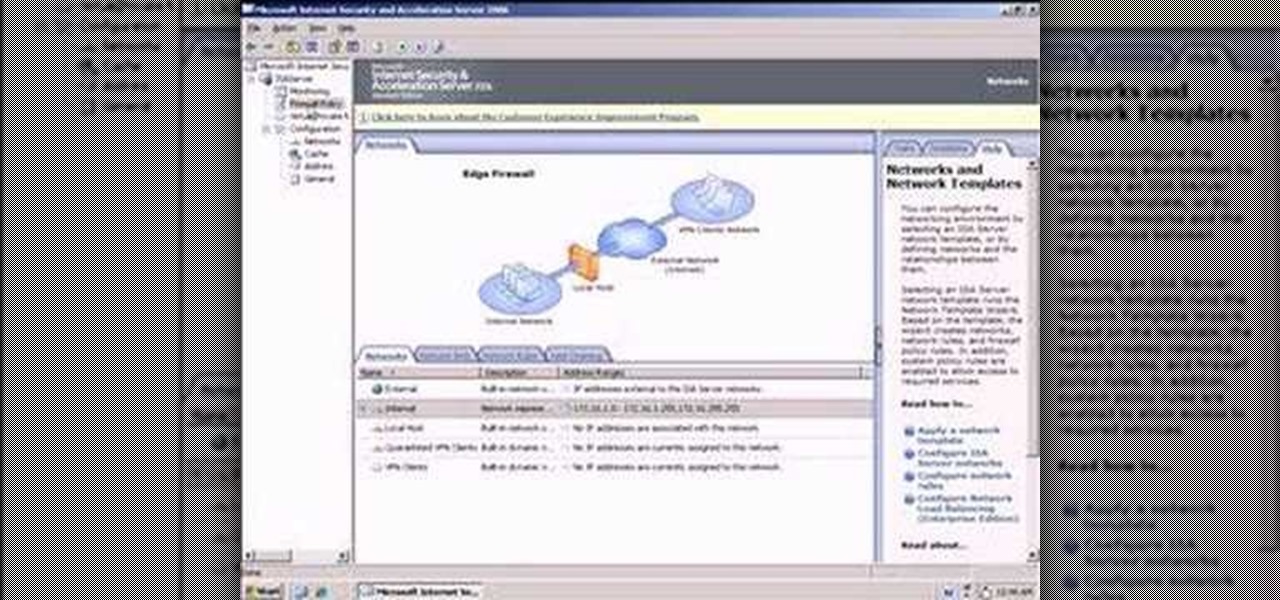
So what exactly is ISA Server? ISA Server, which stands for Internet Security and Acceleration Server, is Microsoft's software-based firewall, proxy, and web caching service/product. Now what does all of that mean? This video helps explain it!

In general, hacking and information security is not just one discipline, but a number of them, and today we will look into some of the networking concepts.

Learn how to set up an Epson printer wirelessly when you bring your new printer home you will want to start by installing the software that came with the new printer. You can set up your printer to work without wires and it will print from all over the house. There are 3 ways to set up the printer including the Epson way, with cables, and WPS. To determine is you need to use WPS, which is more complex, check your router to see if it has a sticker on it that says Wi-Fi Protected Setup. If that...

In many urban areas, GPS doesn't work well. Buildings reflect GPS signals on themselves to create a confusing mess for phones to sort out. As a result, most modern devices determine their location using a blend of techniques, including nearby Wi-Fi networks. By using SkyLift to create fake networks known to be in other areas, we can manipulate where a device thinks it is with an ESP8266 microcontroller.

If you've ever wanted to track down the source of a Wi-Fi transmission, doing so can be relatively easy with the right equipment.

So you want to know what that person who is always on their phone is up to? If you're on the same Wi-Fi network, it's as simple as opening Wireshark and configuring a few settings. We'll use the tool to decrypt WPA2 network traffic so we can spy on which applications a phone is running in real time.

This week's news that Magic Leap's patents had entered collateral limbo, now in the hands of JPMorgan Chase, threw a dark cloud over the company.

With a tiny computer, hackers can see every website you visit, exploit services on the network, and break into your Wi-Fi router's gateway to manipulate sensitive settings. These attacks can be performed from anywhere once the attacker's computer has been connected to the router via a network implant.

A long-standing request for the iPhone has been a way to quickly browse and connect to available Wi-Fi networks and Bluetooth devices without having to dig through the Settings app. With iOS 13, Apple has finally built this essential feature into Control Center, giving you quick access to wireless settings from anywhere, including the lock screen.

NetBIOS is a service that allows for communication over a network and is often used to join a domain and legacy applications. It is an older technology but still used in some environments today. Since it is an unsecured protocol, it can often be a good starting point when attacking a network. Scanning for NetBIOS shares with NBTScan and the Nmap Scripting Engine is a good way to begin.

We already know that Microsoft has something big planned for later this month, and now we have details on how to watch the company's big reveal.

It's common for IoT devices like Wi-Fi security cameras to host a website for controlling or configuring the camera that uses HTTP instead of the more secure HTTPS. This means anyone with the network password can see traffic to and from the camera, allowing a hacker to intercept security camera footage if anyone is watching the camera's HTTP viewing page.

We've been expecting the latest Android Pie update for current Samsung flagships like the Galaxy S9 and Note 9 for some time now, but Samsung's running behind schedule in the United States. Thankfully, it appears that One UI has finally started rolling out for some lucky S9 owners.

When we reviewed the best file managers on Android, MiXplorer easily topped our list with its abundance of features, including tabbed browsing, support for up to 19 different cloud services, file and folder encryption, and much more. The only major complaint we had was the fact it couldn't be installed from the Play Store, but now, that is no longer the case.

Apple released iOS 12.1.3 public beta 2 for iPhones on Wednesday, Dec. 19. Yes, that's confusing, since there was no first beta for iOS 12.1.3, but it indicates that it's the actual successor to iOS 12.1.2 public beta 1. Apple dropped iOS 12.1.2 unexpectedly to fix major issues but did not include everything in the beta, so we're picking up right where we left off.

Applicants looking to attend Magic Leap's first annual L.E.A.P. conference next month in Los Angeles have begun receiving their confirmation invitations, and now we have more detail about some of what will happen at the event.

You may have heard of a signal jammer before, which usually refers to a device that blasts out a strong enough radio signal to drown out the reception of nearby devices like cell phones. Purpose-built jammer hardware is outright illegal in many countries. Still, Wi-Fi is vulnerable to several different jamming attacks that can be done with Kali Linux and a wireless network adapter.

With the opening round of Wimbledon, one of professional tennis's four major tournaments, beginning on Monday, Snapchat is serving up an augmented reality tennis mini-game.

Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, but a hacker can surgically disable a webcam or other Wi-Fi connected device without disturbing the rest of the network.

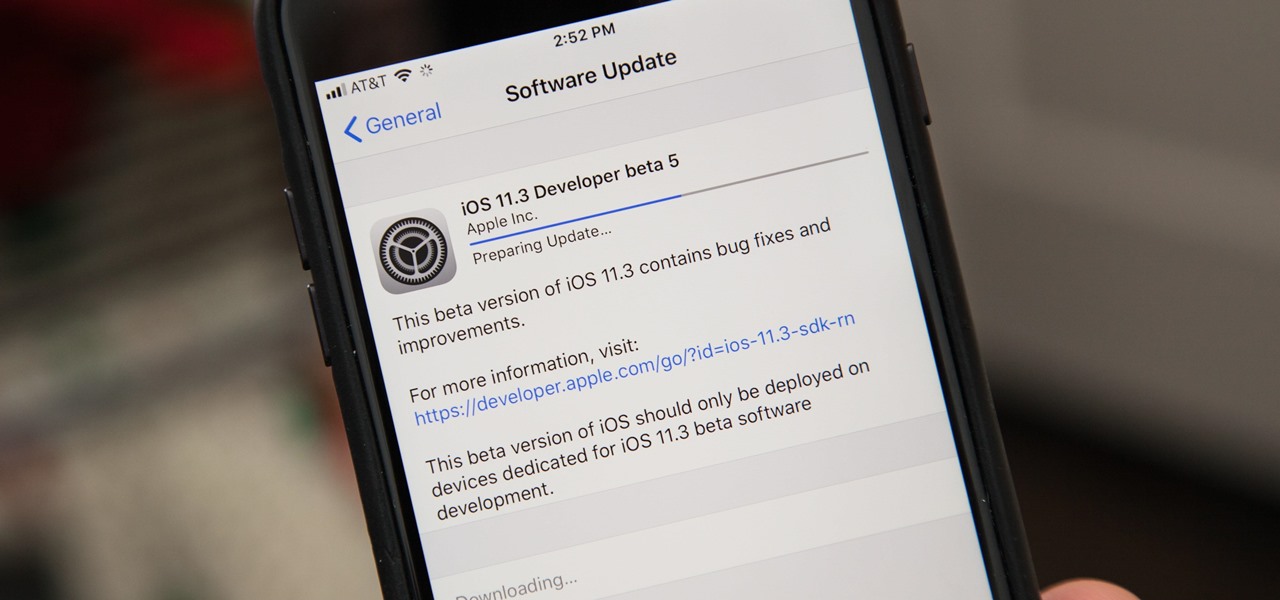
Apple released the fifth build of the iOS 11.3 developer and public beta on Monday, March 12. The update comes exactly one week after the March 5 release of beta 4, which mostly introduced bug and stability patches. At this time, this new beta appears to do much of the same.

Your home has walls for privacy, but Wi-Fi signals passing through them and can be detected up to a mile away with a directional Wi-Fi antenna and a direct line of sight. An amazing amount of information can be learned from this data, including when residents come and go, the manufacturer of all nearby wireless devices, and what on the network is in use at any given time.

In its goal to push the visual quality of real-time rendering to a new level, Unity is starting the new year off right by releasing a sneak peek at its upcoming interactive rendering improvements via a short, three-minute first-person interactive demo called "Book of the Dead."

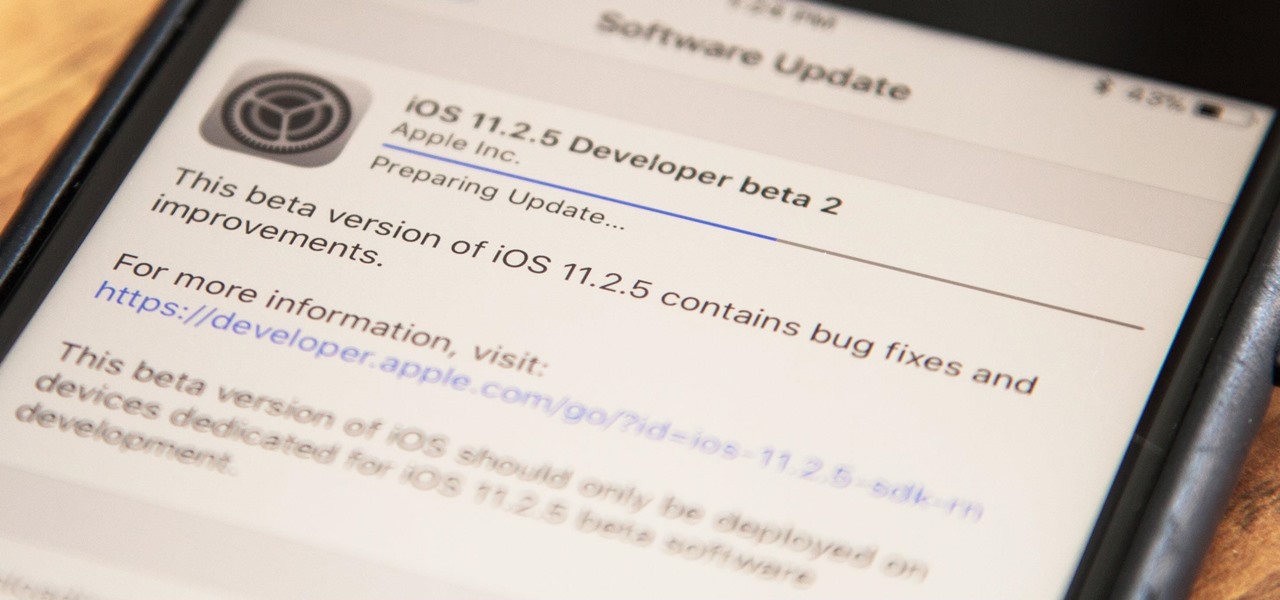
Apple has released the second beta for iOS version 11.2.5 for developers on Dec. 19. The update comes six days after the release of the first 11.2.5 beta which updated the Music app to include a persistent "play bar" at the bottom of the window, along with some bug fixes. Public beta testers received the update on Dec. 20.

Earlier this year at WWDC, Apple made a big show of featuring augmented reality as a central part of iOS moving forward. But since then, other than comments from the company's CEO, Tim Cook, we haven't seen much direct promotion of augmented reality from the company. Until now.

The dark web is an intimidating place for a newbie hacker, but it's a powerful tool once you've learned to navigate it safely. To help you out with that, this guide will cover some need-to-know information for traversing the dark corners of the internet while keeping your identity and data safe. (Hint: Using Tor is not enough.)

According The Venture Reality Fund, the introductions of Facebook's camera platform and Apple's ARKit catalyzed increased activity among companies developing consumer applications.

When you think about preparing for an internship, I'm sure your first thought is to go shopping for professional outfits or to brush up on technical skills. While that's all important, there's so much more for you to think about.

To hack a Wi-Fi network using Kali Linux, you need your wireless card to support monitor mode and packet injection. Not all wireless cards can do this, so I've rounded up this list of 2019's best wireless network adapters for hacking on Kali Linux to get you started hacking both WEP and WPA Wi-Fi networks.