
How To: Kali Is Your New Pet; The Ultimate Guide About Kali Linux Portability.
Did you know Kali 1.0.8? You probably did, and you probably know about the EFI boot option that has been added.


Did you know Kali 1.0.8? You probably did, and you probably know about the EFI boot option that has been added.

Unless you're a high-schooler building a nuclear fusion reactor, the hardest part of a science investigatory project often is coming up with a good idea. You want it to be cool yet feasible, novel but still useful.

In this video music lesson, an expert jazz musician will demonstrate how to read through a fake book composition in A major for beginners. He will demonstrate how to play the various measures and sections of the fake book composition on piano, as well as how to improvise while playing.

It's that time a year when winter storms begin causing havoc across the United States, and when "rotating outages" are common to help sustain the electrical grid during intense cold periods. That means pretty much anybody with snow and ice in their backyard can succumb to power outages. And no electricity means no electric heat.

A new software update for iPhone and iPad fixes a major Apple Books issue that upset users when iOS 16 and iPadOS 16 were first released last September. If you've fled Apple Books because of that blunder, it's safe to return.

While most iOS updates will only improve the experience on your iPhone, some can cause more havoc than good. If an update unexpectedly breaks or degrades certain functions on your iPhone, you may be able to roll it back to the previous software.

By default, your iPhone's share sheet will have a row of contacts iOS thinks you'll want to share the content with. Those suggestions are handy if you frequently share things with the same people, but they also clutter the share sheet, invade contacts' privacy in screenshots, and tell nosy people in eyeshot who you share with the most. Thankfully, you can remove or hide them whenever needed.

If you're a normal, non-corporate video conferencing user, you may not have heard of BlueJeans, but in the corporate world, the software has long been a major staple when it comes to remote meetings.

One of the most iconic architectural landmarks on the planet, the Arc de Triomphe in Paris, France, will become a part of augmented reality history thanks to a new project from Snap.

As if answering Apple's major iPhone event on Tuesday, Chinese mobile giant Xiaomi held its own product launch event the following day.

When it comes to the ever-shifting sands of the augmented reality space, you never know which week will end up being truly historic. Well, this one was one for the history books.

The battle for augmented reality and social media supremacy starts with the people working behind the scenes, and this week Snap pulled off a telling win that could indicate a shift in the AR space.

Some tried to call it a brief cryptocurrency-fueled fad, but it looks like NFTs are here to stay. Now, one of the biggest sneaker companies on the planet, Japan's Asics, is getting into the game with its own set of NFTs, and there's a virtual object component included.

We already know that the US Army will be using its modified HoloLens 2 for special missions, and major businesses are deploying the augmented reality device for enterprise use cases.

The debut of the augmented reality version of Snap's Spectacles came with several examples of how the wearable can allow creators to transform the world around them.
We're still basking in the afterglow of the HUGE Snap Partner Summit last week, where Snap made Snapchat a much stronger augmented reality platform while also unveiling the AR smartglasses version of Spectacles. This week, we got a peek at how Spectacles AR started and got our hands on Lenses from Lego and Disney featured during the keynote.

The surging activity in augmented reality in both the business and consumer sectors is being matched with a wealth of updates and partnerships from Snap Inc.

Ever since the debut of the LiDAR Scanner in the latest batch of Apple's iPhones and iPads, the questions have swirled as to how this would benefit augmented reality interactions.

The era of virtual meetings has been evolving every few months, with augmented reality filters leading the charge in changing the way we interact when chatting via video streams.

Have you ever wondered where you'd come out if you drilled to the other side of the world? Now, if you have an Android device and Chrome web browser, you can find out.

Even as the world continues to grapple with the pandemic, the tech industry continues to chug along, with some looking for ways to present new products, and in some cases continue major conferences that reveal the latest in augmented reality developments.

Google released the first build of Android 12 almost exactly one year after dropping Android 11, which is remarkable in the midst of a global pandemic. But you can tell the Android engineers have been hard at work while quarantining, because the latest OS version is absolutely packed with new features.

Apple just rolled out the of iOS 14.5 to developers and beta testers, and one of the headlining features is the ability to keep your iPhone unlocked when your Apple Watch is nearby. As these things tend to go, Android has actually had this same feature for years, though it isn't quite as polished.

The company augmented reality that Rony Abovitz was trying to build at Magic Leap apparently wasn't working out the way he hoped it would. That company, built on dreams, music, and future-looking entertainment, rather than truly new technology, came with a $2,300 price tag for a device using dynamics most mainstream consumers have never even tried.

The past year has revealed a gaping hole of opportunity in the world of business called virtual meetings. Some existing players like Zoom hopped on that opportunity, while others like Skype seemed stuck on the sidelines, and Google Meet just managed to catch up in time to snag some of the shift in remote work.

The year 2020 was a pivotal span of time during which the word "virtual" took on a brand new meaning. Instead of referring to VR or augmented reality, the term was hijacked to describe meeting across long distances through a variety of software tools, most often through video.

UPDATE: Entries are now closed. Thank you for participating! Next Reality is where we help you literally 'see' into the future of augmented reality, and to help with that mission we're offering three free pairs of Snap Spectacles 3 to three lucky readers who sign up for the Next Reality daily AR email newsletter.

The true crime genre has long been popular on television and more recently on podcasts with shows like Serial.
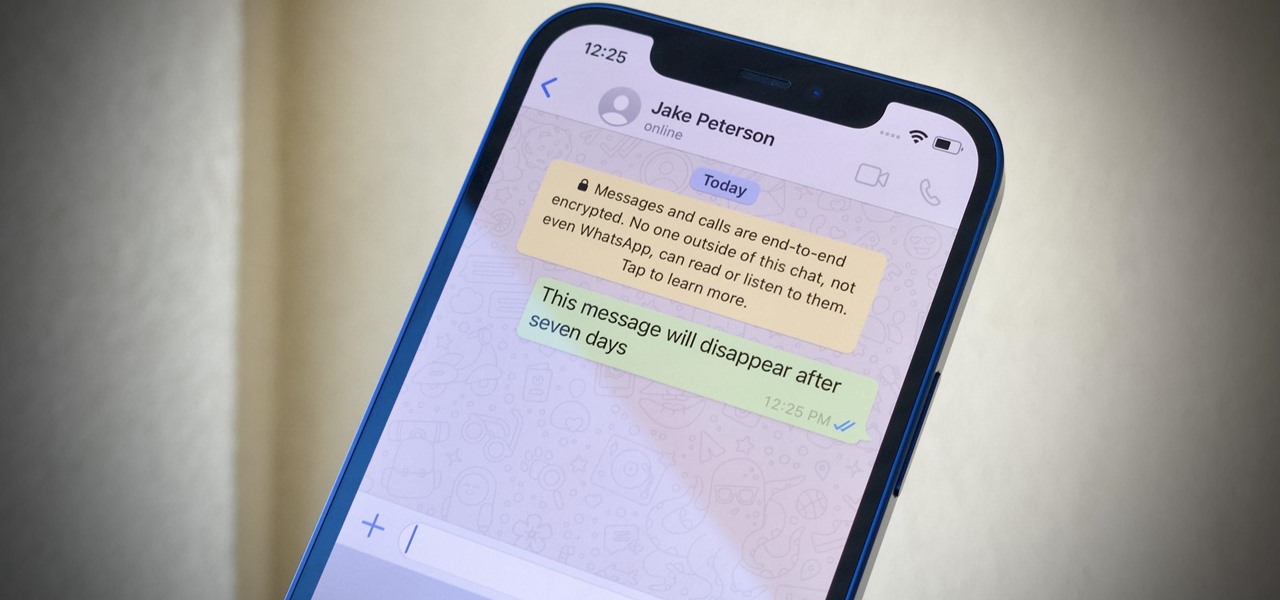
Sometimes, keeping every message comes in handy. Maybe you want to relive fun conversations from months or years ago, or perhaps you need to recall a piece of data such as an address, name, or link. However, not all chats need to stick around forever. Whether you're concerned about privacy or just keeping your threads clutter-free, WhatsApp's "disappearing messages" may be what you're looking for.

If you've ever received an email only to focus on the sender's signature — the hi-res image, the sharp design, the vibrant colors — you're not alone. Humans are visual creatures, and with something as ubiquitous as emails, it helps to stand out.

The gold standard in any business is reaching the front page of Google. You need to get your brand in front of audiences. While it can seem daunting, it's not impossible when you master SEO best practices.

You don't need to work as an executive at Google to understand and appreciate the importance of large-scale data analytics in today's world. Whether you're interested in joining the ranks of a major tech firm or want to improve your company's marketing campaigns through consumer analysis, knowing how to work with large sets of complex data is paramount.
There was a period when Google knew they were switching to gesture navigation, but felt users weren't quite ready for it. The result was Android 9's two-button nav bar that you could both tap and swipe. Android 10 has since brought full-on gestures, and that's the version the Pixel 4 shipped with, so it never had that quirky, fun two-button setup. But you can bring it back, so to speak.
Apple just released iOS 13.6, and while there aren't a ton of new features here, there are some pretty amazing ones to be on the lookout for.

It is well documented that what you say and do online is tracked. Yes, private organizations do their best to protect your data from hackers, but those protections don't extend to themselves, advertisers, and law enforcement.

For all the benefits 5G brings to cellular data, it isn't without weaknesses, the biggest being privacy. Yes, the latest standard comes with breakneck downloads speeds up to 4.3 Gbps, but at what cost? Like with all things on the internet, 5G devices open opportunities for both good and bad actors.

Attacks against databases have become one of the most popular and lucrative activities for hackers recently. New data breaches seem to be popping up every week, but even with all of that attention, databases continue to be a prime target. All of these attacks have to start somewhere, and we'll be exploring a variety of methods to gather information on PostgreSQL databases with Metasploit.

While we haven't covered Amazon Web Services, or AWS, on Null Byte before, Amazon's cloud computing platform is ripe for attack by hackers, pentesters, and cybersecurity researchers. It's also an excellent cloud hosting service to build or use vulnerable-by-design AWS setups and frameworks.

If you've ever wanted to track down the source of a Wi-Fi transmission, doing so can be relatively easy with the right equipment.

Choosing which programming language to learn next can be a truly daunting task. That's the case regardless of whether you're a Null Byter just beginning a career in development and cybersecurity or you're a seasoned ethical hacking and penetration tester with years of extensive coding experience under your belt. On that note, we recommend Python for anyone who hasn't mastered it yet.