Last month, Dr. Sung-Hoon Hong, Vice President of Samsung Electronics, announced at the Virtual Reality Summit in San Diego that Samsung would be moving into the augmented reality market. According to a recently published patent application, that move has begun.

Using mathematical modeling, researchers suggest weather and warming created the "perfect storm" that drove the Zika outbreak in 2016.
Skype is one of the most popular messaging and video chat services for a good reason—it's packed to the brim with tons of cool features. But one bit of functionality that Microsoft left out is the ability to block friend requests from people that aren't in your contacts, which can lead to a lot of unwanted notifications from spammers and bots.

Microsoft's HoloLens may the coolest new advancements in technology we've seen in quite some time, and anyone (with deep pockets) can buy one right now. But so far it's been an isolated platform where you experience mixed reality alone and others watch you air tap nothing but air. Developers are working to change that, and we're seeing the first examples crop up online already.

Few companies have maintained such intense secrecy, in the face of such extreme hype, as Magic Leap, but the closer their mysterious Mixed Reality product comes to mass production, the harder it becomes to hide the details. Hopefully we'll find out way more details soon, as a Magic Leap job posting for a supply chain manager hint that they're readying for release in the next couple years.

Seriously, what's with all of the candy corn hate? I don't care what anyone says, candy corn is and always has been the perfect Halloween snack for me. Only recently did I realize that not everyone gets as hype as I do about small, sugary vegetables.

It's no surprise that the Microsoft Kinect can provide far better motion tracking than the HoloLens currently can on its own, but at least one developer didn't want to wait for the company's own eventual implementation. Kyle G, founder and CEO of Wavelength Studios, projected his movements using a Kinect into a holographic zombie.

The future of augmented and mixed reality offers many possibilities, mostly because we're still figuring out everything it can do. While Meta is open to exploration, they've spent a lot of time thinking about what the future of this technology will be.

LG announced their latest high-end device on September 6 and its specs are pretty amazing: The new V20 sports three cameras, two displays, three microphones, four DACs for high-end sound, and it's all powered by a removable battery.

The mighty toaster oven may be the most useful small appliance ever, whether you're a college student who needs to heat up your Bagel Bites or a professional looking for a quick way to warm up a frozen pizza after a long day. But that toaster oven is no one-hit wonder. With this smart hack, you can give it double-duty superpowers to heat up not one, but two frozen foods at the same time.

You might not think a mixed reality headset could help kids eat their vegetables, but that's the exact premise behind Habit.at—the app that won the "Social Good" category at the 2016 HoloHacks competition in Los Angeles.

The new Google phones, which are rumored to ditch the Nexus moniker for Pixel, will most likely come with an Android feature that 7.0 Nougat doesn't currently have—a new set of navigation keys.

The new lock screen in iOS 10 is a lot different than previous versions, but one thing that stuck around is the quick access camera shortcut. The only real difference aside from aesthetics is that now you don't have to swipe up from the camera icon. Instead, you can simply swipe to the left from right side to quickly snap a picture.

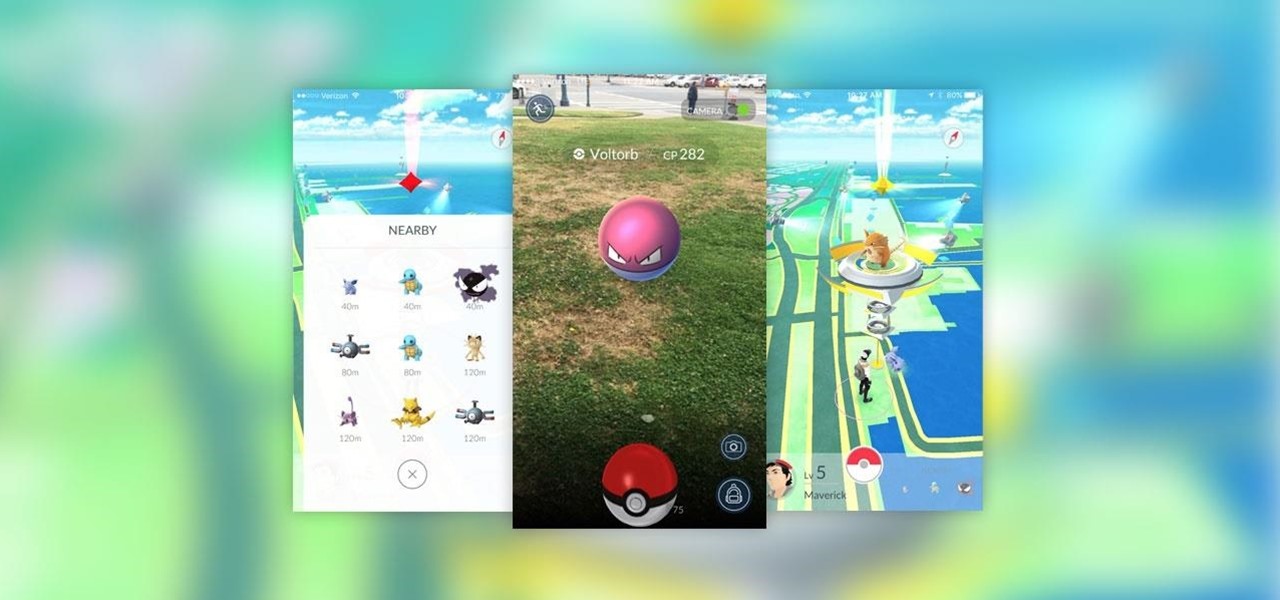
Pokémon Go takes the popular franchise and brings it into the real world through augmented reality, allowing us to play the game while exploring our physical environments at the same time. It doesn't just put pocket monsters into a more realistic context, but it changes the game in some major ways that may delight some players... and upset others.

With the FBI getting access to iPhones, and apps like Waze being used to track people's locations, you've got to wonder just how safe and secure your smartphone is... or isn't. When you consider everything you do on your phone, from taking and sharing pictures to mobile banking, keeping your information safe is a crucial step that may seem out of your hands.

It's a given that if you're driving, you or someone you know has Waze as a go-to on their smartphone. The Google-owned crowdsourced navigation app is one of the best for avoiding traffic, roadblocks, and even cops.

The biggest corporation we know today is called Google, I bet you've heard of it yeah? How Google Tracks You:

When it comes time to buy a new smartphone, the sheer amount of options on the market can make you feel overwhelmed. There are Android devices of all shapes and sizes with different functionalities and price points, and now, even Apple has three unique iPhone models to fit various budgets.

After months of speculation and sifting through rumors, Samsung finally unveiled its Galaxy S7 and S7 edge flagships, and they're pretty much what we had been anticipating. But just because there weren't any major surprises doesn't mean that it's not still exciting. Let's have a look.

Android TV devices have had those beautiful Chromecast background images as their screensaver for quite a while now. Envious of this feature, Apple copied the idea for a similarly-styled screensaver in their newest Apple TV, but with one big twist—they used videos instead of still photos.

Apple's once flawless mobile operating system has seen its fair share of bugs recently. From Messages and Wi-Fi settings crashing to having your photos and contacts exposed, iOS has been standing on shaky ground for a while now.

For many people, the two main advantages of buying a Nexus device are prompt updates and the ability to root without much hassle. But in a cruel twist of fate, these two features are almost mutually exclusive, since OTA updates will refuse to run on rooted devices.

The VLC media player just celebrated its 15th birthday in February 2016, marking a decade and a half of hassle-free video playback for hundreds of millions of users on virtually every major operating system. The free and open-source player is so powerful and easy to use that it has almost completely vanquished all would-be competitors in its rise to the top.

Sony's Xperia smartphones are some of the most beautiful Android devices out there—but unfortunately, they're rarely promoted in the U.S. and are seldom available through major carriers (aside from the new Xperia Z5 devices), so not many Americans are aware of how awesome these devices really are.

Hello, my fellow hackers. My name is cl0ck. I am a senior majoring in Computer Engineering with an emphasis is Security. I have been lurking the site for a while now reading and learning from the great minds that reside here. I, too, have some knowledge that I would like to share with all of you. This post actually comes from a personal problem I faced and had to find a solution for. Without further ado, here it is:

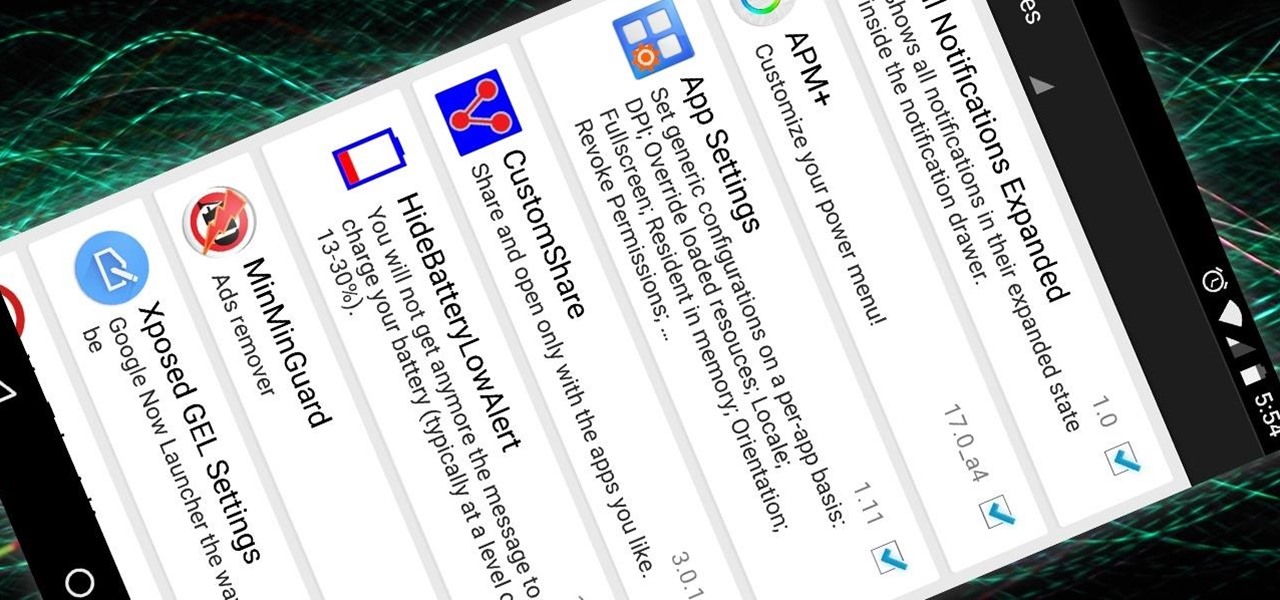
The Xposed Framework was just recently made available for Android Marshmallow, but everything isn't quite back to status quo just yet. Sure, some Xposed modules function properly, but others are a bit buggy, and several don't even work at all. This is mostly a result of changes to the Android system that Lollipop modules relied upon, and such modules will need to be updated for Marshmallow compatibility.

So, you want to become anonymous? well let me give you everything I know (or at least most of it) to you.

A no-carb, gluten-free substitute for breadcrumbs. Sounds and probably tastes like cardboard, right? Unless you're talking about Pork Dust. Yes, you read that right. Pork. DUST.

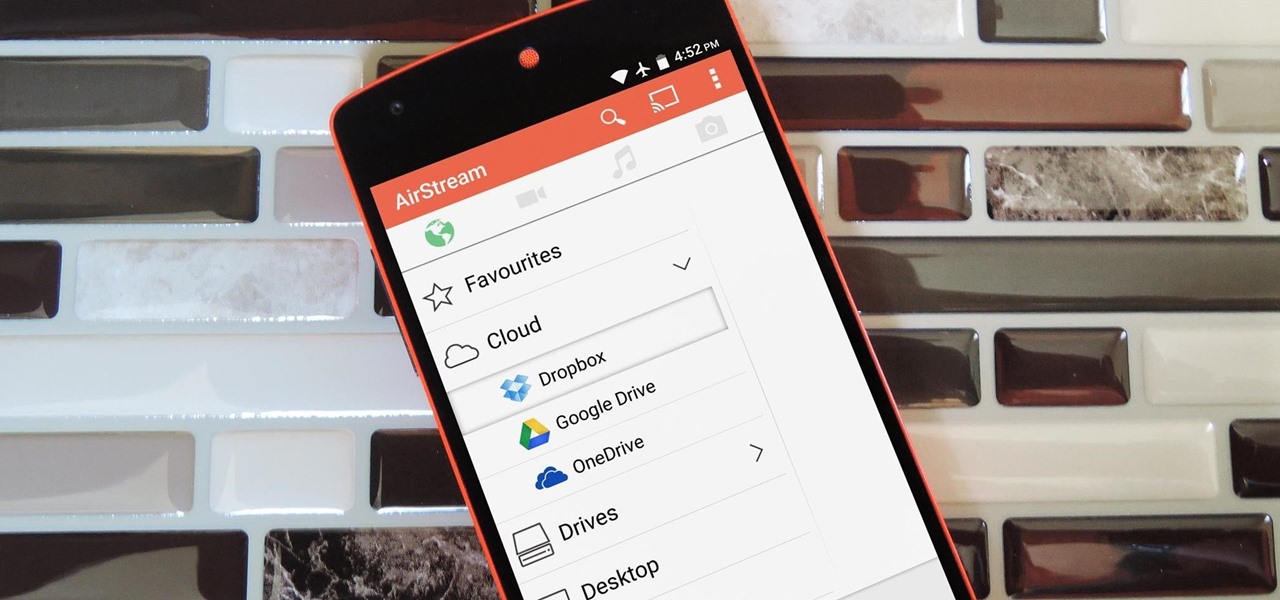
Smartphones generally have limited storage, but counter this issue with an always-on internet connection. This led to the proliferation of cloud storage services, which allow us to store and access our large media libraries remotely.

Sideloading apps on Android is incredibly easy—you just have to enable "Unknown sources" in your device's Security settings, then you're free to run an APK installer file to get the app installed.

Mother Nature is one creative entity, especially when it comes to fruit. Let's face it: most major supermarkets stock only the most common fruits like apples, pears, and grapes, but they're so basic. Why not explore other options, from the stinky-yet delicious durian to the captivating citrus caviar that is finger limes?

With all due respect to the fine folks at DrinkTanks, it's a little surprising that no one came up with their idea sooner. After all, last I checked, beer was pretty darned popular.

Magic Leap, the virtual-reality software group backed by Google, just released a teaser video on their YouTube channel. In a word, it's amazing.

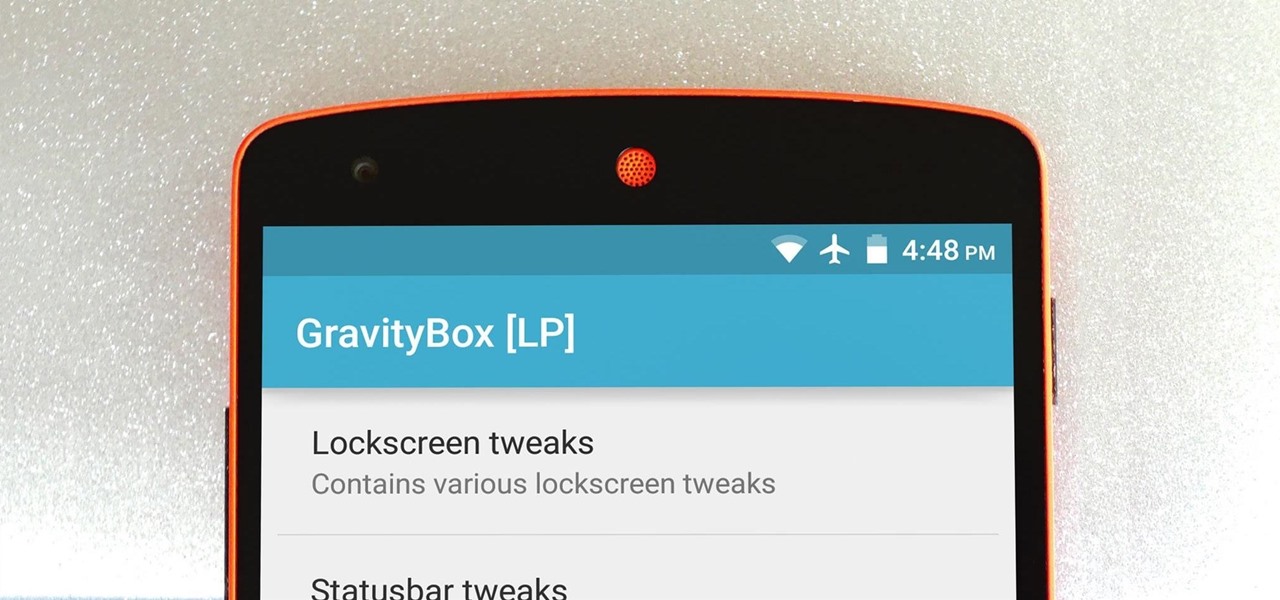
The king of all Xposed modules is alive and kicking on Android Lollipop. GravityBox received an update over the weekend that will bring its bevy of UI tweaks to folks who have installed the framework on their Android 5.0+ devices.

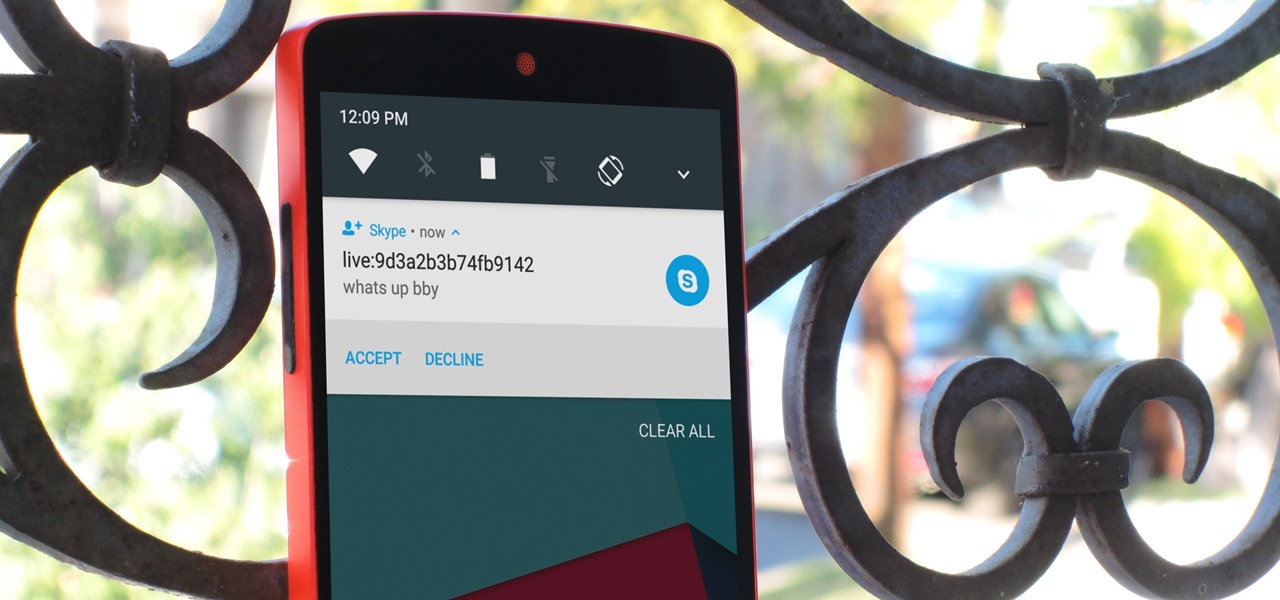
With Android 5.0, Google introduced a new "Heads Up" notification system for incoming calls and messages. While the new incoming call interface seems to be a rousing success, the rest of the Heads Up system has been met with much less enthusiasm from users.

Now that the Xposed Framework has finally been updated for Android Lollipop, we're starting to notice that some modules function properly, while others are a bit buggy or even worse—don't work at all. Most of this is a result of changes to elements of the Android system that KitKat modules relied upon, and such modules will need to be updated for 5.0 compatibility.

When you're on a limited data plan, bumping up against your monthly cap is a major concern. Overage fees are incredibly high these days, and being throttled down to 2G coverage almost renders a smartphone completely useless.

Google+ doesn't have quite the user base of Facebook or Twitter, but for Android enthusiasts, it's definitely the place to be. All of the major developers—such as Chainfire and Koush—make their social media home on Google+, and the Android app sports one of the nicest interfaces of any comparable platform, chock-full of Google's Material Design.

Aside from being able to change the wallpaper and add shortcuts, the Galaxy S4's lock screen doesn't offer much in the department of personalization. The lock screen is efficient and practical, but it's also a little bland.

Welcome back, my nascent hackers! We have spent a lot of time in previous tutorials focused on hacking the ubiquitous Windows systems, but the vast majority of "heavy iron" around the world are Linux or Unix systems. Linux and Unix dominate the world of Internet web servers with over 60% of the market. In addition, Linux and Unix servers are the operating system of choice for major international corporations (including almost all the major banks) throughout the world.