It has not been a good year for Apple, as far as software scandals are concerned. From autocorrect nuisances to secret slowdowns of aging iPhones, Apple has had a lot to answer for. iOS users now have another issue to worry about — it's being called "chaiOS," and it's wrecking havoc on iPhones with just a simple URL.

Welcome back, my amateur hackers! With Halloween right around the corner, I thought you could have a little fun with your newfound hacking skills using a hack that is guaranteed to freak out your boss, teacher, coworker, friend, etc.

Though you can use the Social Engineering Toolkit to clone websites, this way is much more customisable.
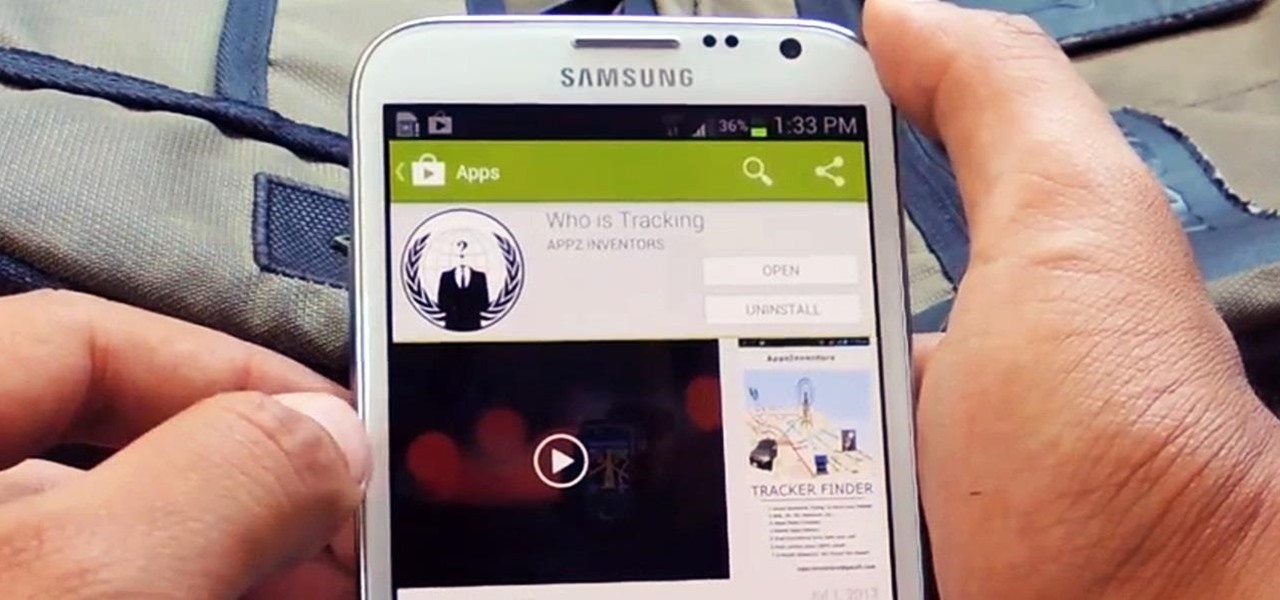
A wave of shock and anger swept across the country after Edward Snowden released private documents recounting the U.S. government's secretive mass surveillance programs. Although some of the fear was unwarranted (they don't read your emails or listen to your calls), many scrambled to find privacy of new heights for protection from the all-watchful eye. While the government may not be tracking you down, there are a myriad of other candidates that fill that Big Brother role—and I'm not talking ...

Welcome back, my newbie hackers! We've already saved the world from nuclear annihilation and covered our tracks afterwards, but the world is still threatened by a malicious, megalomaniacal dictator with missiles and nuclear weapons.

UPDATE: A patch to fix the exploit has been released. Download it here.

Looking for a primer on how to protect your Mac OS X desktop computer or laptop from malicious software? This clip for Apple amateurs will show you precisely what to do. You'll find it's easy. So easy, in fact, that this home-computing how-to can present a complete overview of the process in just over a minute and a half. For more information, including step-by-step instructions, take a look.

If a virus infects your computer you want to do everything in your power to avoid having to reformat your system. Instead of running an automated removal program, it is possible to manually remove the malicious software.

You may not know what HTTP is exactly, but you definitely know that every single website you visit starts with it. Without the Hypertext Transfer Protocol, there'd be no easy way to view all the text, media, and data that you're able to see online. However, all communication between your browser and a website are unencrypted, which means it can be eavesdropped on.

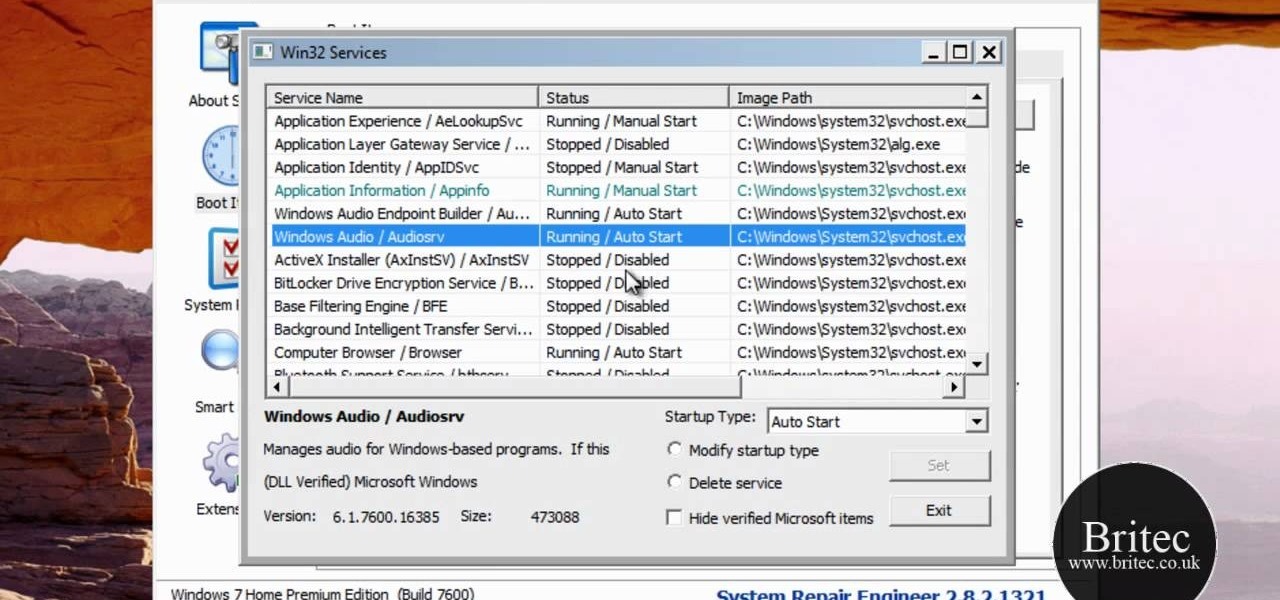
Your Windows computer may be experiencing some issues, and those issues may be a direct result of computer viruses and malicious software from the internet. One of the simplest ways to find these issues and repair them is by using a freeware program called System Repair Engineer (SREng). But that's not all it can do… check out the video to see a basic overview for using SREng.

If you're worried about having your private information taken away from you by hackers and other malicious people, this tutorial may help you. This tutorial will help show you how to easily use and understand the phishing filter in Internet Explorer 8. It only takes a couple of clicks to activate and can be the difference between making sure your private information is secure or out in the open for others to use. Good luck and enjoy!

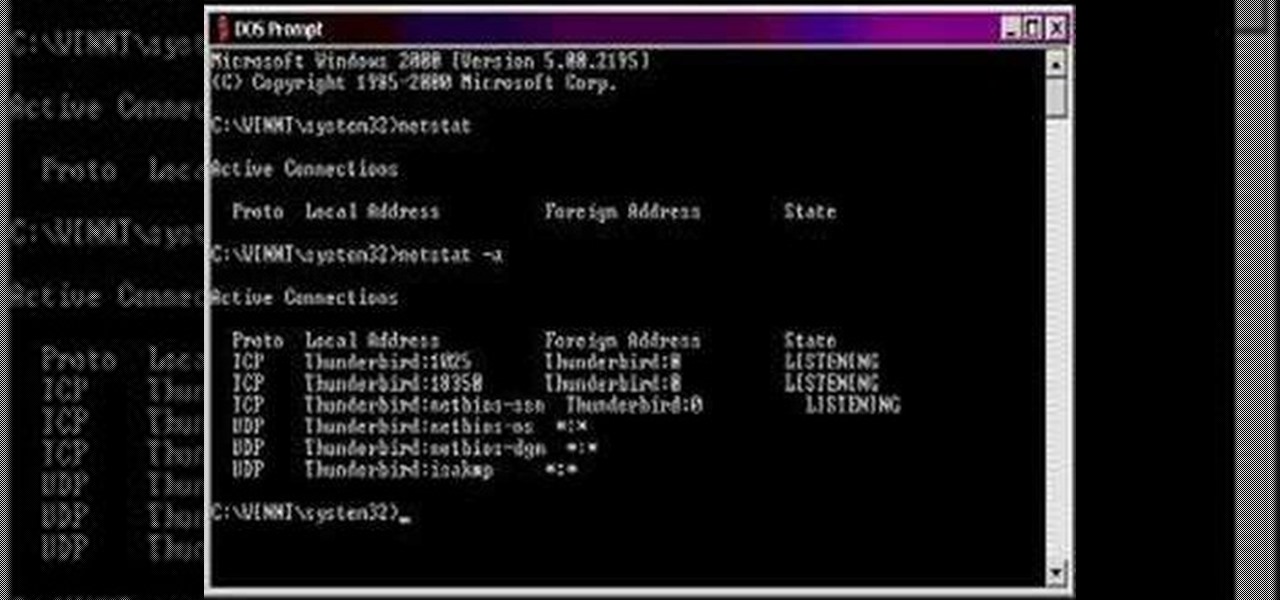
In this how to video, you will learn how to keep your Windows operating system secure by look for and closing open ports. First, you will need to run the program called Net State. Once this is open, type in netstat -a. This will list main connections. Next, type in netstat -an. This will give you the numbers of ports that are open. Some may be used for file sharing and anti-virus programs. If you want it completely secured, you should only have one running. This video shows you how easy it is...

With a simple social engineering trick, sudo passwords can be captured in seconds without the target's knowledge. The passwords can then be saved to a file or exfiltrated to another computer on the network.

It is often said that the best hackers remain unknown, and the greatest attacks are left undiscovered, but it's hard for an up-and-coming penetration tester or white hat to learn anything unless one of those factors is actually known or discovered. But the end goal here in our SQL injection lessons is to make that statement as true as possible for us when performing our hacks.

The default Camera app got a few more tricks up its sleeves when iOS 11 was released, and the best addition by far was the inclusion of a built-in QR code reader since that meant no more third-party apps just for QR code scanning. However, Apple's built-in QR code scanner did have a vulnerability at one point that would let hackers direct you to a compromised website without you even noticing it.

After numerous scandals like the Equifax data breach and the 2016 US election, cybersecurity has become a significant issue for Americans. Unfortunately, anytime we use our devices, we're open to a cyber attack — especially when we browse the web. However, there are ways that we can make it harder for hackers and data miners.

The pictures we upload online are something we tend to think of as self-expression, but these very images can carry code to steal our passwords and data. Profile pictures, avatars, and image galleries are used all over the internet. While all images carry digital picture data — and many also carry metadata regarding camera or photo edits — it's far less expected that an image might actually be hiding malicious code.

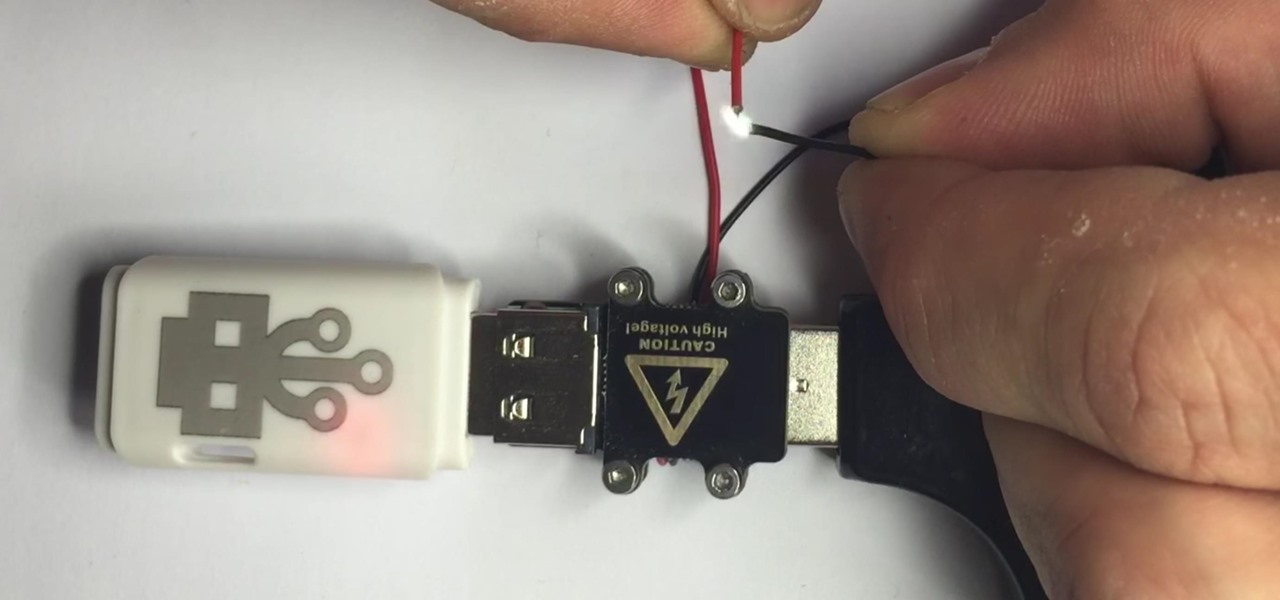
There are two types of bad USBs out there. One lets you trick the computer into thinking it's a keyboard or other USB device, and the other goes straight over malicious into computer killing territory.

What happens if you unknowingly connect a malicious USB drive and it starts infecting your entire office network? Instead of having a panic attack and working all night to find a fix, you can just put on a mixed reality headset like Microsoft's HoloLens and point.

This tutorial was written with Windows 7 in mind, but the principle applies to all versions starting from 7.

Welcome back, my tenderfoot hackers! One key area on the minds of all hackers is how to evade security devices such as an intrusion detection system (IDS) or antivirus (AV) software. This is not an issue if you create your own zero-day exploit, or capture someone else's zero-day. However, if you are using someone else's exploit or payload, such as one from Metasploit or Exploit-DB, the security devices are likely to detect it and spoil all your fun.

The newest update of the Firefox web browser was released yesterday, and whether you were upgraded automatically or manually, Mozilla is advising that you downgrade to Firefox 15.0.1 as soon as possible. Firefox 16 is Mozilla's latest release, and is apparently extremely susceptible to malicious sites hacking their users complete browsing history.

QR codes are everywhere, from product packaging to airline boarding passes, making the scanners that read them a juicy target for hackers. Thanks to flaws in many of these proprietary scanning devices, it's possible to exploit common vulnerabilities using exploits packed into custom QR codes.

It's always a good idea to know how an attack works at the very basic level. Manual techniques for exploitation often find holes that even the most sophisticated tool cannot. Sometimes, though, using one of these tools can make things so much easier, especially if one has a solid foundation of how it works. One such tool can help us perform a cross-site request forgery with minimal difficulty.

While hackers have taken advantage of numerous vulnerabilities in Adobe's products to deliver payloads to Windows users via PDF files, a malicious PDF file can also wreak havoc on a Mac that's using the default Preview app. So think twice before double-clicking a PDF open on your MacBook — it might just be a Trojan with a rootkit inside.

When it comes to your security, you want the best of the best. Why settle for mediocre service with something as valuable as your protection? Malware continues to make its way onto the Play Store, leaving millions of devices vulnerable. You need an app that will shield your devices from both the latest malware threats and threats nearby. And when it comes to antivirus apps, there is only one choice.

Download a popular, legit app from the Google Play Store. Decompile it. Add malicious code. Repackage the app. Distribute the now trojan-ized app through third-party Android app sites. This is how advertising malware Ewind, what Palo Alto Networks calls "adware in applications' clothing," infects Android users.

Hello everybody Joe here. Today I will be demonstrating how you can find XSS vulnerabilities in a website and what you can do with them

Welcome back, my novice hackers! Previously in my "Spy on Anyone" series, we used our hacking skills to turn a target's computer system into a bug to record conversations and found and downloaded confidential documents on someone's computer. In this tutorial, I will show you how to spy on somebody's Internet traffic.

There are over one million apps in the Google Play Store, and many of them are restricted to certain device types, brands, and Android systems.

Welcome back, my tenderfoot hackers! I recently began a new series on digital forensics to help tenderfoot hackers from being detected and ultimately, incarcerated. In this installment of that series, we will look at recovering deleted files. This is important to hackers because you need to know that even when you delete files on your computer or on the victim's computer, a forensic investigator can usually recover them.

When Google introduced the Pixel 3 on October 9th, one of new additions they briefly mentioned was the Titan M security chip. While they did talk about how it will improve overall security, they didn't expand on the number of changes it brings to the Pixel 3's security. Well, they finally shared more, and it's a pretty big deal.

It's safe to say most of us know the dangers of online security. We know there are people trying to steal our most sensitive information, and we try our best to prevent that theft. But new research is showing what we're doing might not be enough, as the sensors in our phones may be telling hackers everything they want to know.

It seems like a new, dangerous Android exploit is uncovered every month or two. The latest headliners are NightMonkey and Chronos from the list of CIA hacks reported by Wikileaks, which have been billed as gaping security holes in the world's biggest mobile operating system.

This tutorial follows the same idea as my original tutorial for windows, but I've redone it to work with Mac OS X. Here's how to get a meterpreter session from your victim opening a malicious word document:

Do you ever thought that you can't control an Internet disconnected system? I saw a funny video in Chema Alonso's youtube channel (A well-known hacker of my country and creator of Fingerprinting Organizations with Collected Archives among other security tools), and decided to post something similar.

This is my first tutorial and it is about accessing deep web for total beginner,sorry in advance if I make any mistake plz forgive me.
Welcome back Hackers\Newbies!

Well hello dear readers of Null byte, let me start off stating english is not my first language and they will be some grammar mistakes. This also is my first tutorial so don't hesitate to give me feedback :)

If you read my last tutorial on using SEToolkit, you probably know that SEToolkit is an effective way to make malicious actions look legitimate. But, that was only the beginning... the truth is, Metasploit and SEToolkit belong together, and help each other very well.