Unlike many browsers, Firefox gives a lot of control to the user. By default, Firefox does a great job of balancing security and performance. However, within the app's settings, you can modify options to shift this balance in one direction or another. For those looking to shift it toward security, here are few suggestions.

JavaScript is one of the most common languages used on the web. It can automate and animate website components, manage website content, and carry out many other useful functions from within a webpage. The scripting language also has many functions which can be used for malicious purposes, including stealing a user's cookies containing passwords and other information.

Maybe you thought sitting behind a Mac gives you special protection when it comes to getting hacked. Thanks to a a new report from Check Point, you can kiss that theory goodbye. The cyber security company just uncovered the latest strain of malware — OSX/Dok — infecting all versions of macOS (previously Mac OS X).

Welcome back, my tenderfoot hackers! A short while ago, I started a new series called "How to Spy on Anyone." The idea behind this series is that computer hacking is increasingly being used in espionage and cyber warfare, as well as by private detectives and law enforcement to solve cases. I am trying to demonstrate, in this series, ways that hacking is being used in these professions. For those of you who are training for those careers, I dedicate this series.

Apps that have no business accessing the internet can share your location, device ID, and other personal information with potentially malicious data snatchers. If you're connected to the internet on your Nexus 7 tablet, you're a potential target for cyber threats.

Welcome back, my budding hackers! I've written several listener guides on creating a malicious PDF or malicious Word document that would carry in it a payload with the Meterpreter, or reverse shell enabling you to own the system. One of the hurdles to using these techniques is the antivirus (AV) software on the target system. For instance, if you try to email a malicious PDF or Word doc, it's likely that the victim system will alert the victim that it contains a virus or other malware.

Former Vice President Dick Cheney was so fearful of attacks, he had his heart defibrillator re-calibrated to block incoming wireless signals so that highly skilled hackers couldn't send him into cardiac arrest.

New to Windows? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to protect Windows from viruses without an antivirus software.

This is a video tutorial in the Computers & Programming category where you are going to learn how to kill boredom with weird and random websites. This video lists 11 such websites and explains what each one does. The 1st one is Zigzagphilosophy. This site allows you to make a lot of zig zag lines on the screen by moving your mouse. #2 omglasergunspewpewpew. On this site you use the mouse to control a squirrel on the screen and use the left click to shoot a laser. The #3 site is allemande and ...

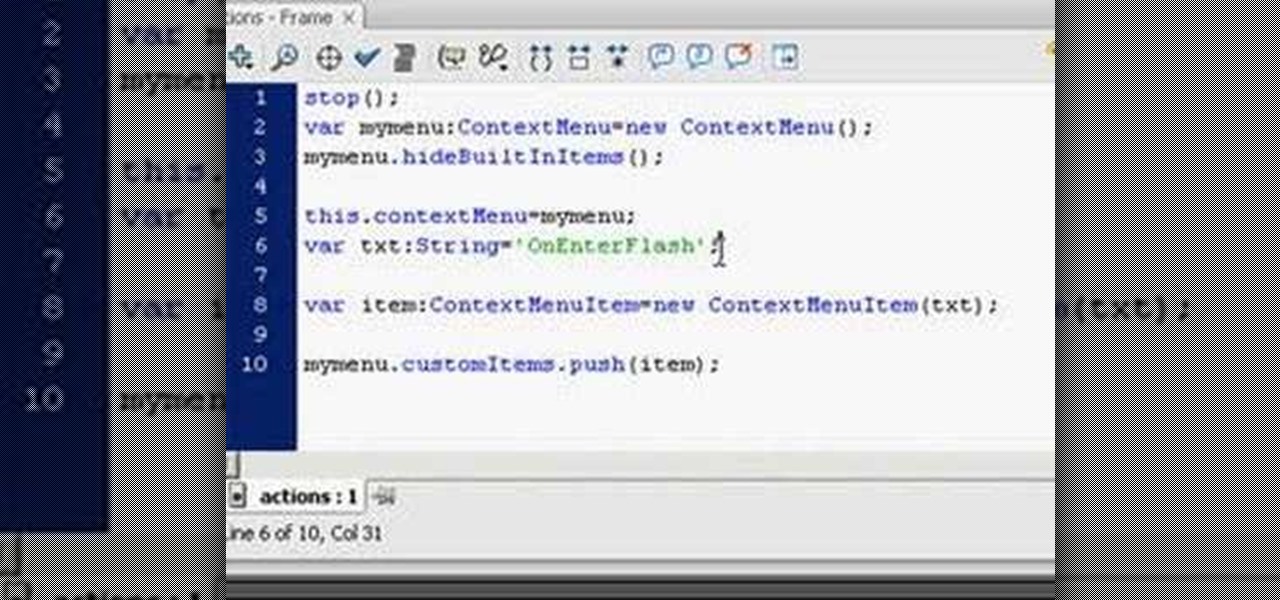
Web users are for the large part nosy, spoiler-loving folks who refuse to let websites and other users keep secrets from them. Thwart these trolls! This video will teach you how to use Actionscript 3 to hide the context menu from your site's users, preventing them from skipping to further parts of your slideshow or game and ruining the continuity of your work. You will also learn how to create a link that will show up in user's context menus when they right-click on objects. These two tools w...

In this ASP.Net video tutorial, Chris Pels will show how to use nested master pages to create individual master pages that represent different standard content layouts for a web site. First, see how several major commercial web sites use a standard set of content layouts. Next, see how to nest a master page within another master page, and use the design time support in Visual Studio 2008. Then, learn the considerations for establishing a “page architecture” which represents the major types of...

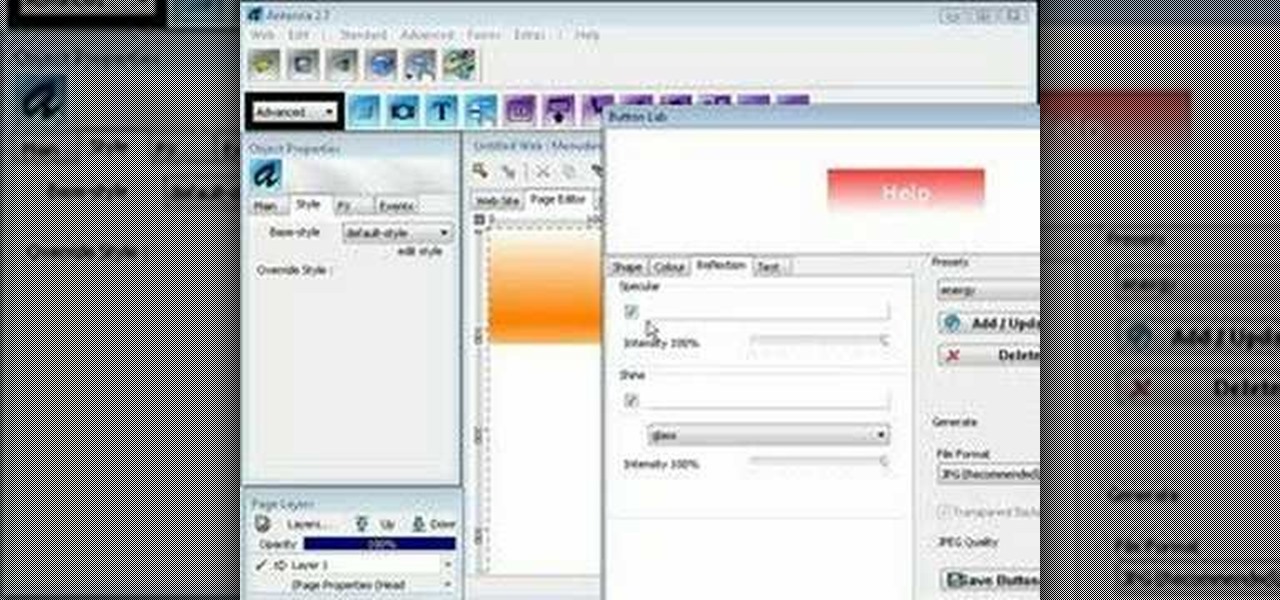
Looking for a stylish design for your web site's menu? You can use Antenna web design studio to create buttons that change color when the cursor rolls over them, a nice way to let people know where they are on your site.

If you are looking to operate a web site from your Mac, MAMP- a package of free web software programs- is an elegant solution. This video will show you how to configure MAMP on your computer, so you can get on your way running your sites.

Looking for a guide on how to beat Mission 10: Crash Site in Black Ops? Look no further! This gamer's guide presents a complete, step-by-step walkthrough of the process. For all of the details, and to learn how to beat Mission 10: Crash Site of Call of Duty: Black Ops for yourself, take a look.

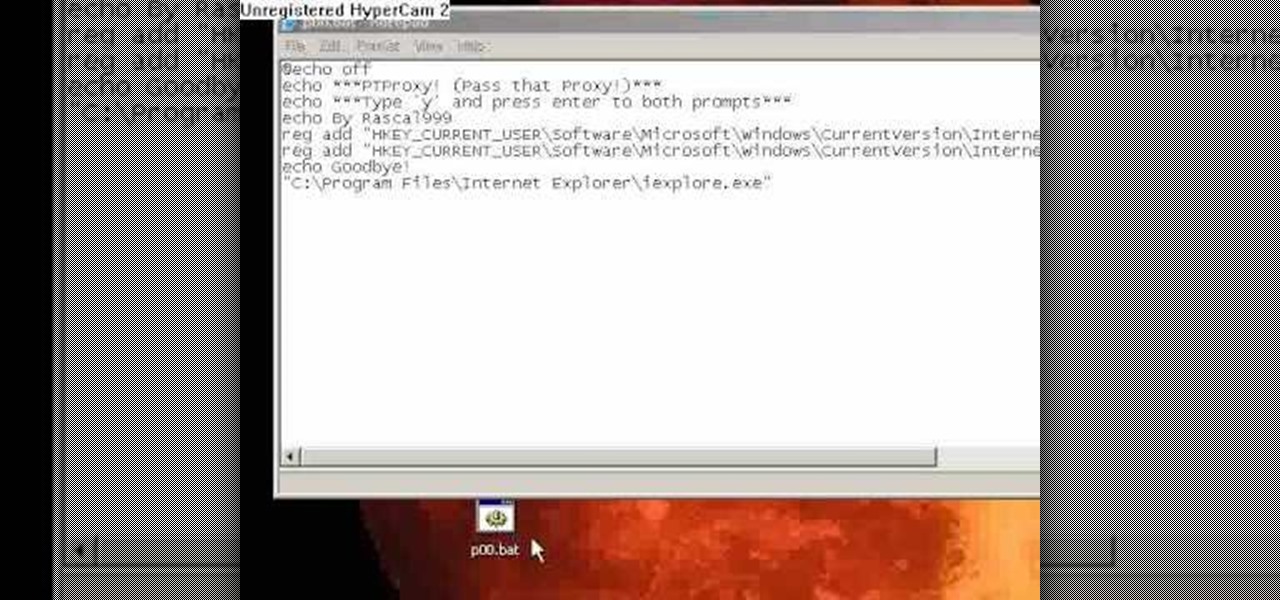
Different ways of using a proxy bypass to access blocks sites is shown with ease in this video. Many places explained to be blocked with internet security such as libraries and schools. Using a search engine such as Google you need to search for a proxy site. After a proxy site has been found you will use it to access the blocked websites through another servers internet provider. The narrator explains that proxies are just a way to bypass internet blocks by avoiding using the blocked compute...

Monitor visitors to your website by using a hit counter. This tutorial shows you how to use PHP and Flash to code a hit counter for your site. You can even use the counter to measure visitors to your site as a whole, or determine the most popular pages on your site.

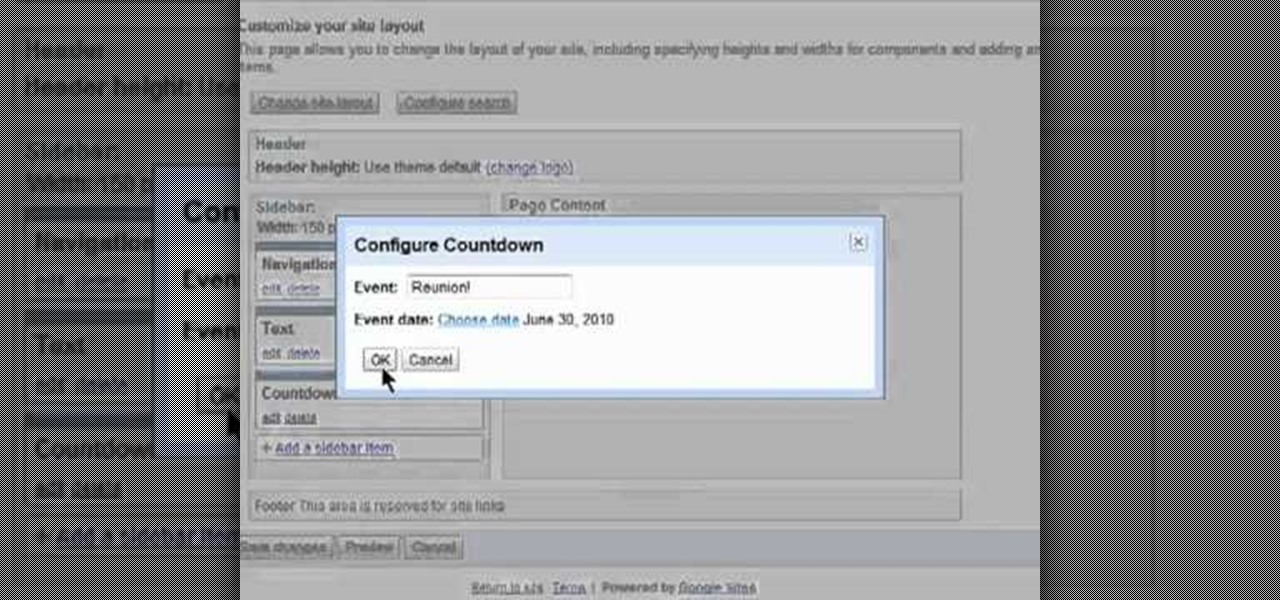
Want to alter the look and feel of your Google Sites website? It's easy. And this brief video tutorial from the folks at Butterscotch will teach you everything you need to know. For more information, including detailed, step-by-step instructions, and to get started managing your own web pages with Google Sites, take a look.

Interested in editing your Google Site webpage? It's easy. And this brief video tutorial from the folks at Butterscotch will teach you everything you need to know. For more information, including detailed, step-by-step instructions, and to get started managing your own web pages with Google Sites, take a look.

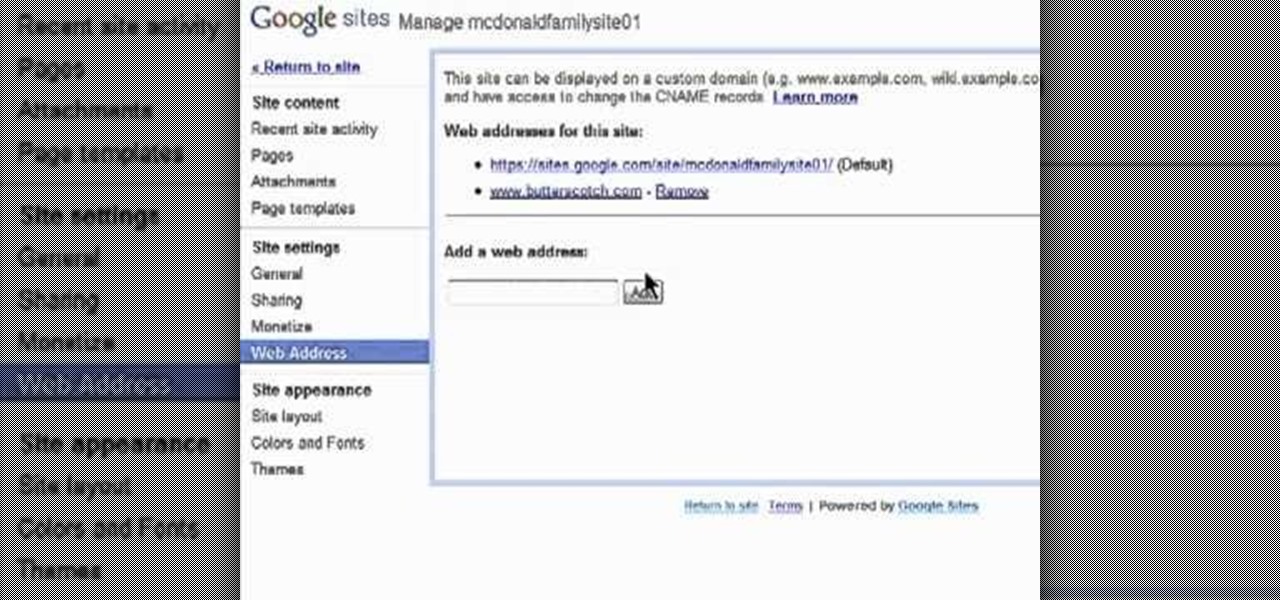
Want to direct your personal domain to your Google Sites page? It's easy. And this brief video tutorial from the folks at Butterscotch will teach you everything you need to know. For more information, including detailed, step-by-step instructions, and to get started managing your own web pages with Google Sites, take a look.

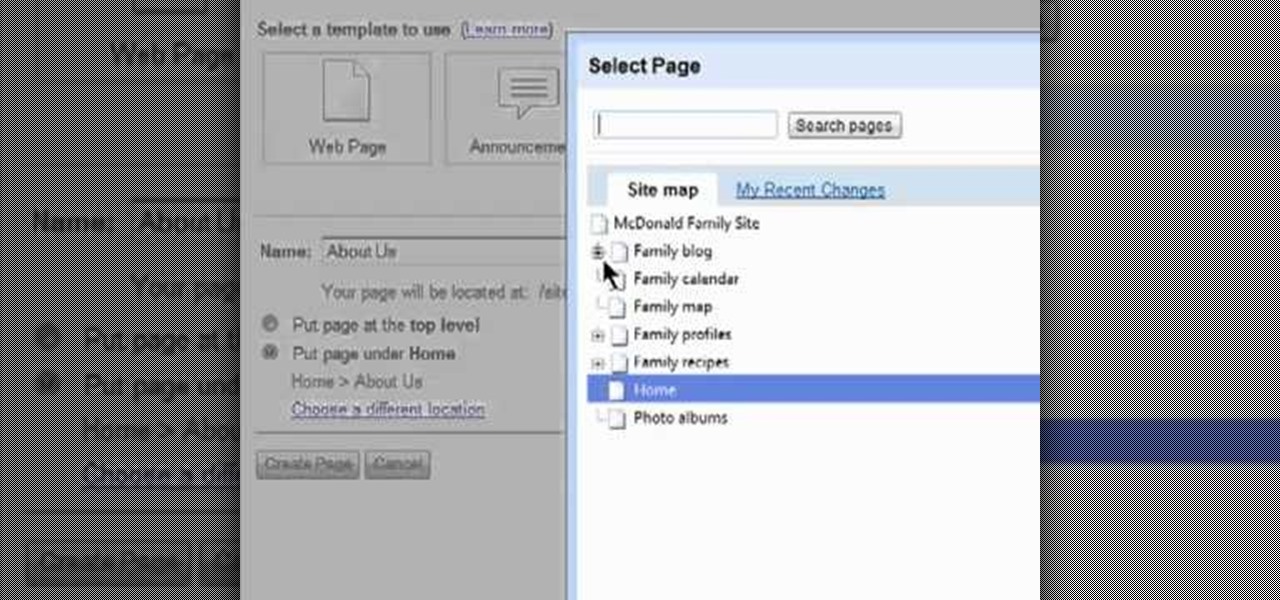
Need some help figuring out how to add a new page to your Google Sites website? This brief video tutorial from the folks at Butterscotch will teach you everything you need to know. For more information, including detailed, step-by-step instructions, and to get started adding new content to your own Google Sites webpage, take a look.

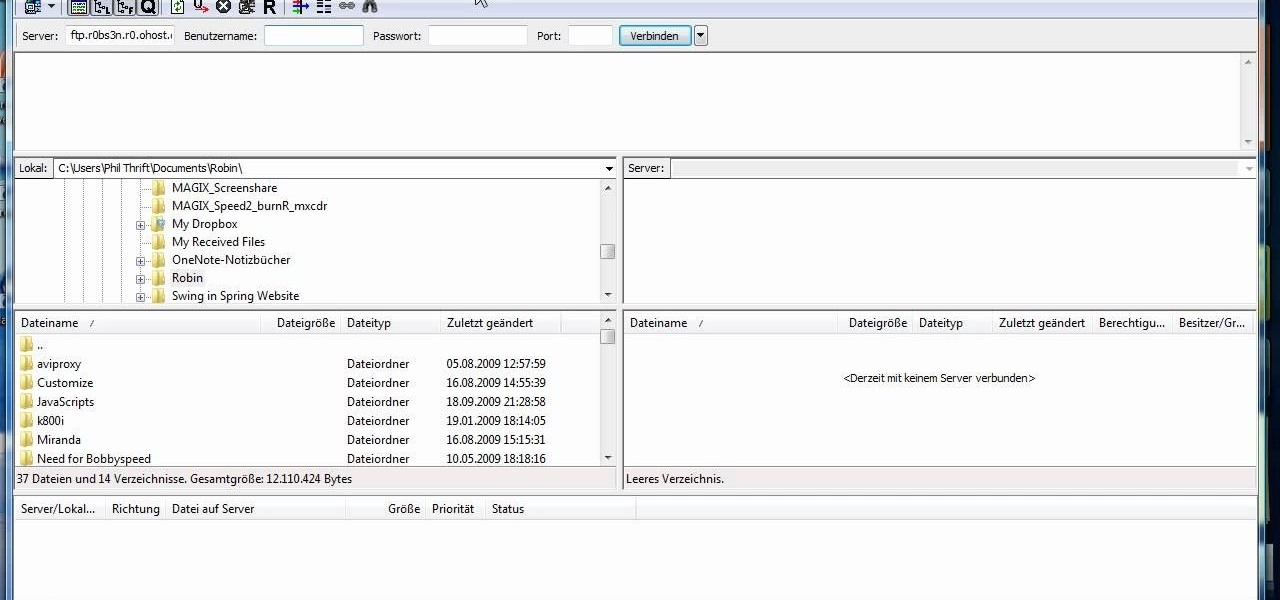
This video tutorial is in the Computers & Programming category where you will learn how to set up an FTP connection using Firezilla. Open up your filezilla program. On the top left, click on the file menu button, and select 'site manager'. In the window that opens up, select 'new folder' and give it a name. Now create a site to store in this new folder. Click on 'new site' and name it. Now on the right hand side, enter the host and the port. The default port is 21. Under server type, select F...

Need to send large files across the Internet? An FTP site is a great resolution to emails that bounce back due to attachment overload. By uploading your file to an FTP site, it will allow your recepient to download the file from the site with ease. In this tutorial, learn how to upload and download files using the FileZilla FTP client.

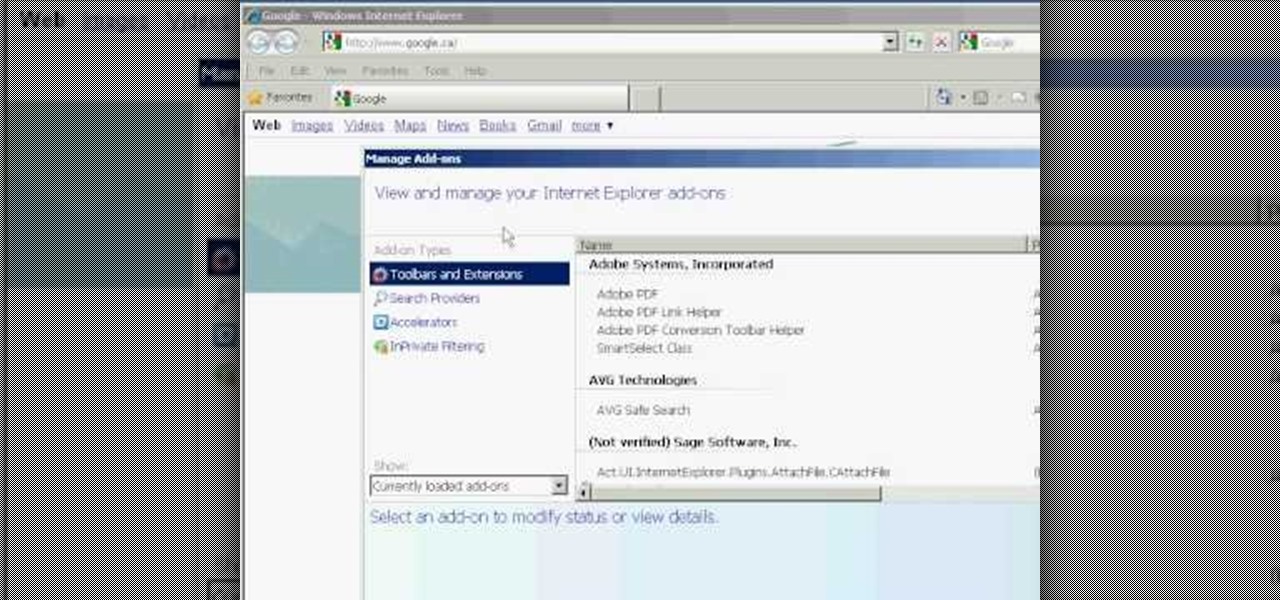
Whethamsolution’s Quick tip walks us through some of the issues caused by use of add-ons in Internet explorer 8 web browser. The video also shows how to manage the add-ons installed in IE8. Add-ons are software’s which enhance the functionality of a web browser. Though most add-ons enhance the browser functionality to a great extent they often tend to slow down the browser drastically. Moreover unwanted add-ons like toolbar's and malicious scripts may cause nuisance to browsing experience...

Big business is on the web these days and you don't have to build a shopping website or blog to get involved.

Steer clear from empty flattery and malicious social engineering with these tips on how to avoid a player.

Don’t you just hate it when you try to go on a website while you’re at work—and find out your boss has blocked it? Here’s how to thwart The Man. With these tips, you'll be able to check your facebook or myspace at work (or whatever sites your employer may be blocked). All you need is access to google. Did you know? According to one survey, 78% of employers block employee access to pornography, 47% block gambling sites, 20% block shopping and auction sites, and 4% block news sites.

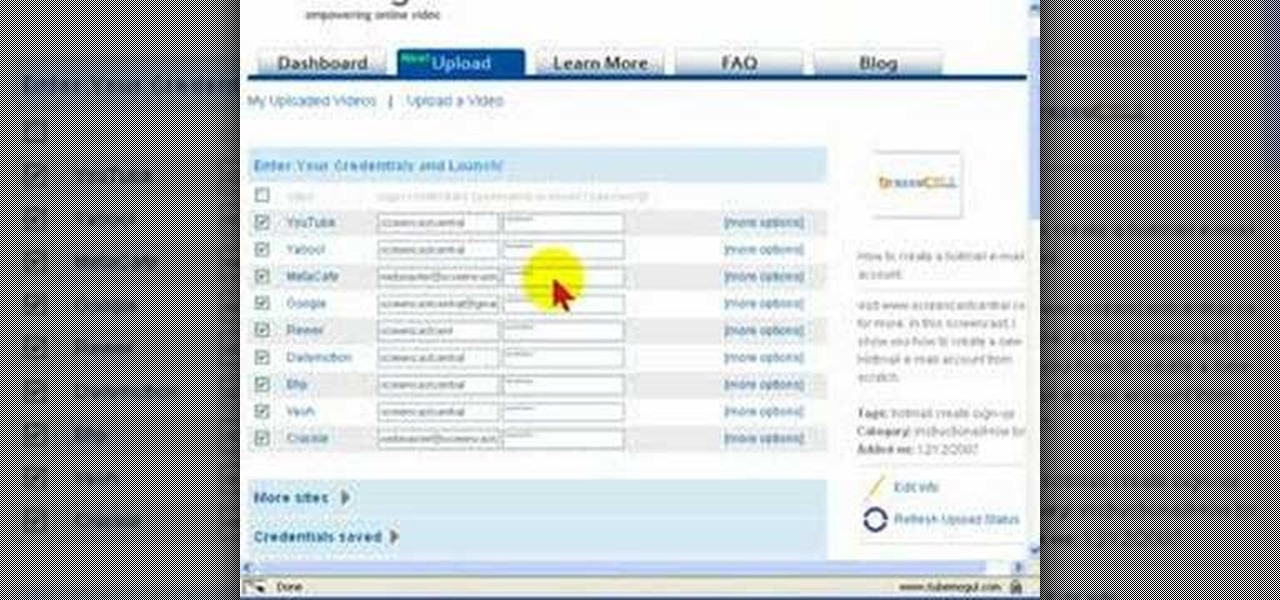
Uploading videos to multiple video hosting sites using Tubemogul.

SEO specialist Aaron Wall demonstrates some on the page search engine optimization techniques that will help your site rank better in Google's search results. The key is to improve your site's SEO while keeping it user friendly.

In Safari for iPhone, as far back as iOS 7, you can request the full desktop version of websites. The process was streamlined starting in iOS 9, but the process remains relatively hidden and easily missed. Now, iOS 13 shines a light on it, as well as adds functionality to set the desktop view for individual websites indefinitely.

A new hack has reopened an 8-year-old iPhone security loophole that Apple thought it had fixed back with iPhone OS 2.2. This is not one of those times when a theoretical attack gets identified and blocked quickly by Apple. On the contrary, it's a hack that actually exists right now, and it can have some serious real-world repercussions, so this is something all iPhone users need to be aware of.

Although there has been much speculation about how much damage could be done if hackers were to take control of a country's SCADA systems, there have been few examples - until a few months ago, with the power outage in Ukraine caused by hackers.

I mentioned in 2015 I wanted to start a 'DoXing' series, and since I havent seen this on Null Byte, I am now going to introduce this to the community.

In part one of this tutorial we found out that your English teacher is a paedophile, by using a Man in the Middle attack to intercept his internet traffic.

Welcome back, my greenhorn hackers! As all you know by now, I'm loving this new show, Mr. Robot. Among the many things going for this innovative and captivating program is the realism of the hacking. I am using this series titled "The Hacks of Mr. Robot" to demonstrate the hacks that are used on this program.

Researchers at the cyber security firm Zimperium have recently uncovered a vulnerability in roughly 95% of Android devices that has the potential to allow hackers to take total control over your phone with a simple picture message (MMS). The gritty details of this exploit have not been made public yet, but hackers now know the general framework for this type of attack, so you can be certain that they'll hammer out the details in no time.

Hi there, Crackers, Welcome to my 7th post (Part-1), this tutorial will explain about the basics of Batch Scripting.

First, I want to give credit to the author where I first found how to do this: Astr0baby's Blog. This article was dated, so I took the script on his page and reworked it to make it work today. (I also included the way to make it hide the cmd line popup.) Requirements

Welcome back, my hacker apprentices! Several of you have written asking me how you can check on whether your boyfriend, girlfriend, or spouse is cheating on you, so I dedicate this tutorial to all of you with doubts about the fidelity of your spouse, girlfriend, or boyfriend.

Welcome back, my hackers novitiates! As you read my various hacking tutorials, you're probably asking yourself, "What are the chances that this hack will be detected and that I'll land behind bars, disappointing my dear mother who already thinks I'm a loser?"

If you've been using Google's hidden App Ops to lock down and prevent some of your Android applications from exposing your privacy, then think twice before updating to the new Android 4.4.2 software.