Welcome back, my neophyte hackers! There are innumerable ways to hack a system. We must not overlook any of the possibilities if we want to "own" the system. As systems become more and more secure, we need to be vigilant in our search for weaknesses. In this hack, we'll look at abusing the trust that a user innately has for software updates to install our own listener/rootkit on their system.

All of my hacks up to this point have been operating system hacks. In other words, we have exploited a vulnerability usually in an operating system service (SMB, RPC, etc.) that all allow us to install a command shell or other code in the target system.

Fallout has always had some great references to Pulp Science Fiction, especially seeing as the art style is very much based off of that old 1950's Pulp Sci-Fi feel. To spice things up a bit and give yourself a unique look, you can find a rare Space Suit complete with helmet at the REPCONN Test Site! Check out this video where you can find the location of the Space Suit in the REPCONN Test Site's basement in Fallout New Vegas!
This Dreamweaver CS4 tutorial takes you on a step by step process for installing an automated comment box system for your website. The system is a great way for communicating and interacting with your website users. It has a great feature that automatically sends you an email everytime someone comments in your website. Also it will allow you to post a reply by email.

This video from ESPN walks you through the different draft modes available for picking a fantasy football team using the ESPN fantasy football site. The different draft modes available are:

Back in Fallout 3, when they released the Broken Steel DLC, once you completed the main mission and finished the training simulation, you were allowed to take some pickings from the weapons and armor vault, one of which was the Tesla Canon, a sniper-rifle meets awesomesauce, high damage gun! Well, Obsidian did one better, and you don't even need to get DLC! This is the Tesla-Beaton Prototype, and you can find it at a crashed Vertibird site there in Fallout New Vegas in the south Mojave Desert...

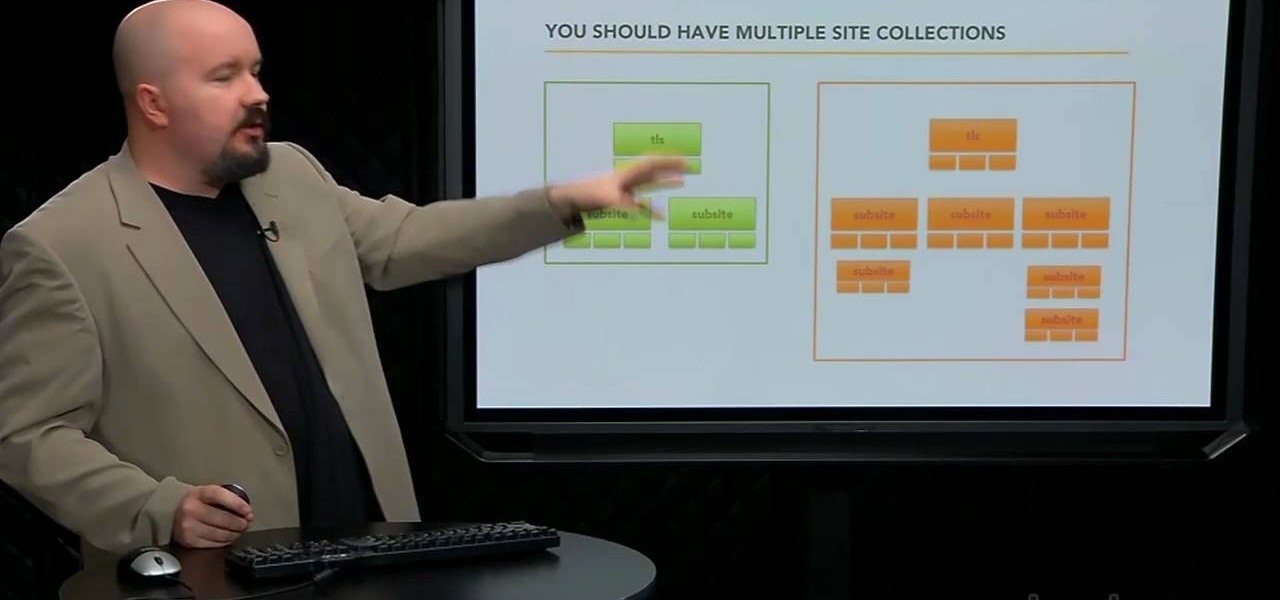
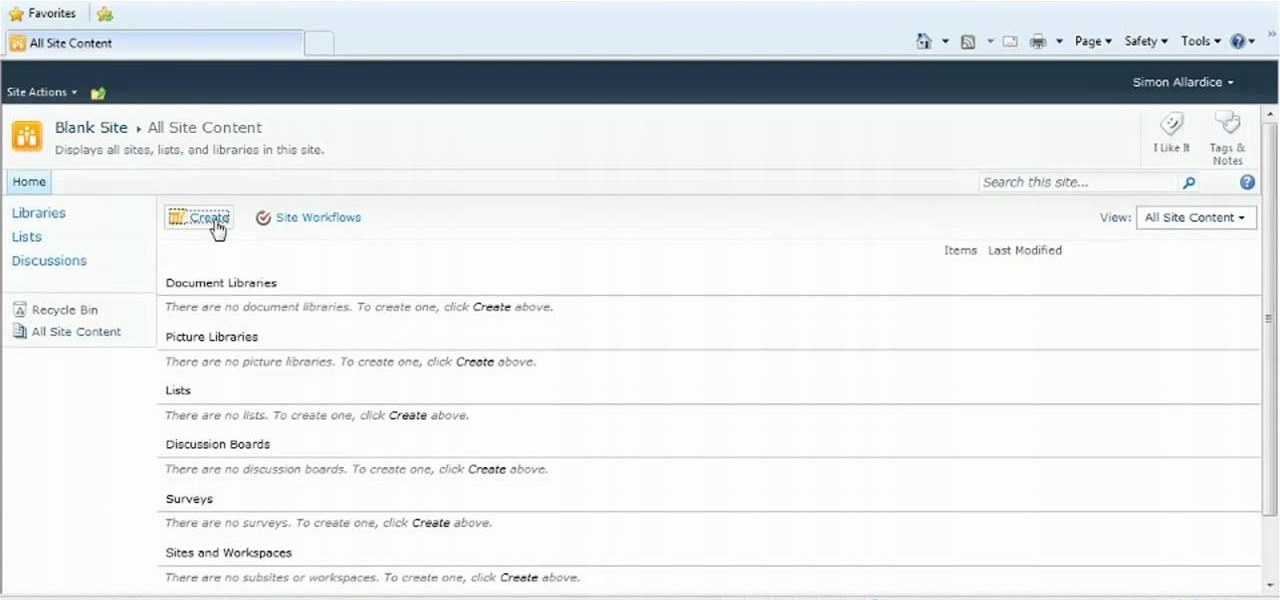
Interested in creating a site collection within Microsoft SharePoint 2010? This guide will show you how it's done. Whether you're new to Microsoft's popular content management system (CMS) or a seasoned MS Office professional just looking to better acquaint yourself with the SharePoint 2010 workflow, you're sure to be well served by this video tutorial. For more information, including detailed, step-by-step instructions, watch this free video guide.

Want to create a site within Microsoft SharePoint 2010? This clip will show you how it's done. Whether you're new to Microsoft's popular content management system (CMS) or a seasoned MS Office professional just looking to better acquaint yourself with the SharePoint 2010 workflow, you're sure to be well served by this video tutorial. For more information, and to get started using SharePoint yourself, watch this free video guide.

Having large images on a website is a great way to slow down your site and make it much less appealing to your users. This video teaches you how to use Flash CS4 to load images dynamically, which dramatically decreases the size of your images and will make your site run much more smoothly, especially if you have a lot of images or videos.

Got banned from a website you love to torment? Well, there's a way to keep it going. You can get back onto a site by changing your IP to get past the servers. This will only work if your IP is banned. If your username is blocked directly, you will have to find another way.

Follow along through the creation of a fictitious customer portal to learn about master pages, themes, membership, roles, site navigation, user profiles, and the Web Site Administration Tool in this ASP.Net video tutorial.

In this video tutorial, Chris Pels will show how to create a web service in ASP.NET and then call the service from another ASP.NET web site. First, learn how to create an .asmx component which represents a web service in an ASP.NET web site. When creating the web service learn how to control several aspects of the web service functionality with web service attributes. Next, see how to test the web service in the Visual Studio web service test page. Then learn how ASP.NET allows many .NET data...

After you've published your site, you might decide you want to add additional pages over time. To add an additional page to my site, all I have to do is click the "Add Page" button in iWeb.

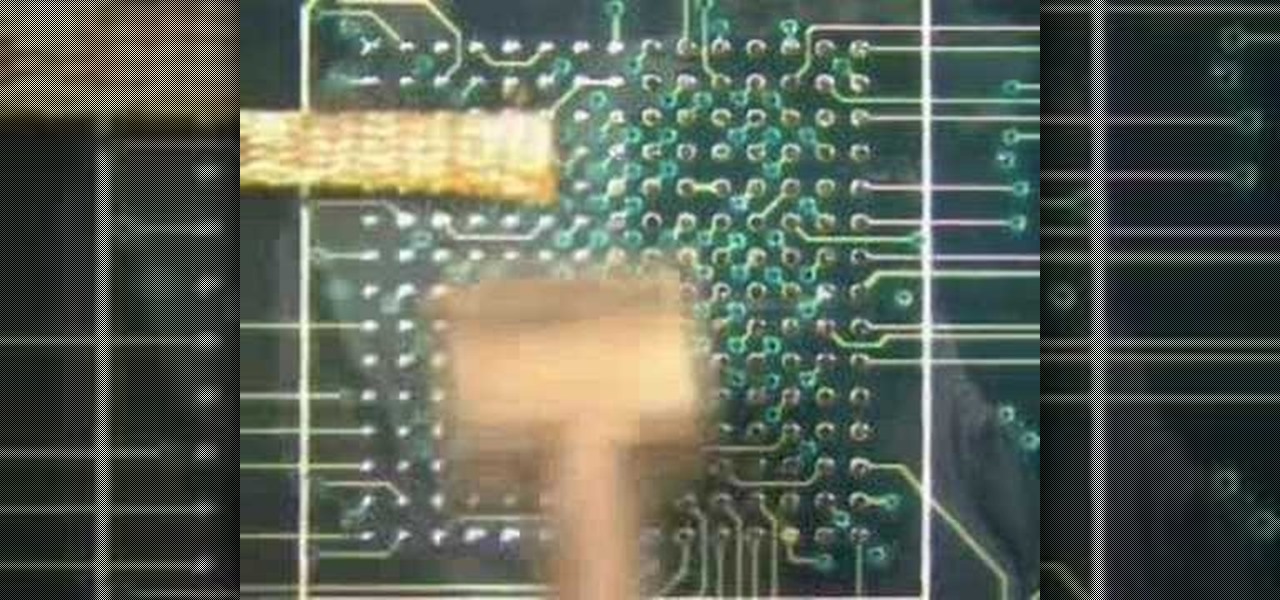
In this soldering tip video brought to you by BEST, Inc. Norman Mier demonstrates site preparation for BGA placement.

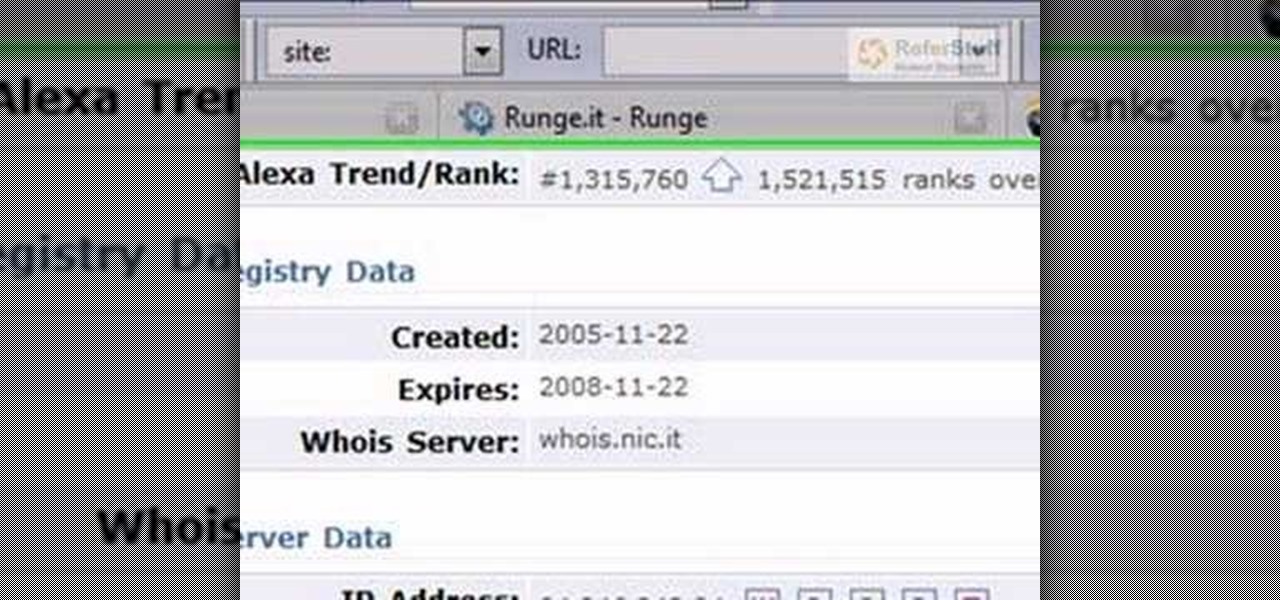
In this video from richardfallah we learn how to track a scam email. You can tell a scam from an email that looks a bit funny. So if it's an email that looks like it's from Bank of America, you might see a link to click that actually would take you to another site which is an exact clone of the Bank of America website, but it has a different web address. This is NOT Bank of America! They will try to steal all of your information if you type in your personal information. Whois is a great tool ...

Ike, from Ike's Outdoors.com gives basic information on Sighting a Bow. He explains a few things he does before he even goes out and shoots. He explains how to line up the site with your arrow whether you are left handed or right handed and then gives pointers on "following the arrow" with the site to get the best results. He recommends shooting at a closer range and with 2-3 arrows before making any adjustments in case of error on your part, and adjusting the site accordingly before moving b...

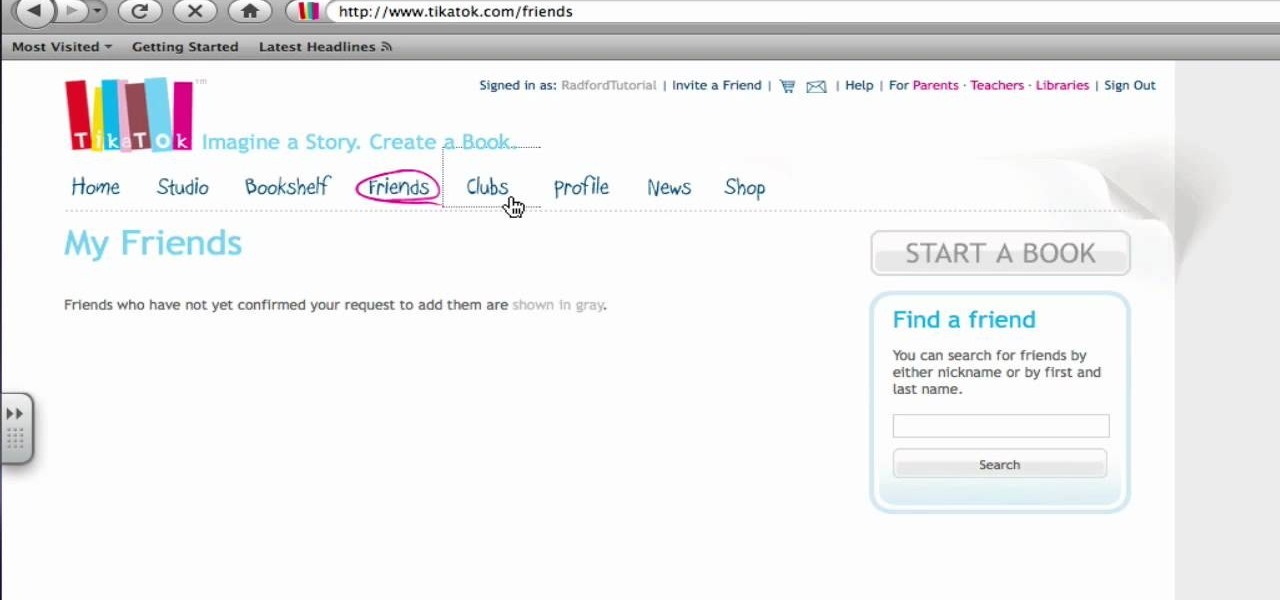
If interested in writing a story this two part tutorial will introduce you to Tikatok. You will learn the basic navigation and setup of the web site. Tikatok allows you to create and publish your own storybooks online. This program is ideal for allowing anyone to be creative and come up with their own ideas for stories.

This video shows the method of getting past blocked sites and opening them using proxy servers. The method shown is useful when the sites are blocked using another site. In this case it is 'www.lightspeedsystems.com'. It can be done using proxy servers. In the case shown it is 'treesniff.com'. The URL is typed and we choose the option of 'Continue to this website'. Press 'No' for the security information. After this the page of the proxy server is displayed. Type the name of the website you w...

Nowadays many schools and colleges have blocked the social community sites from accessing them through school computers. The video shows how one can access to these sites using a command prompt.

SEO is the name of the game. If you want your business or brand to succeed, ranking on the front page of Google is a boon. Getting to the front page of search engines takes work, but it's not impossible when you master SEO best practices.

Apple's Gatekeeper security software for macOS (Mac OS X) is vulnerable to remote attacks up to version 10.14.5. An attacker that's anywhere in the world can exploit MacBooks and other Mac computers by sharing a single ZIP file.

Any internet user will need to download files eventually, and most simply have faith that what they are downloading is trustworthy. This doesn't give much clarity into the contents of the file, but if the file's author published the original checksum, comparing it to the SHA-256 hash of the downloaded file can ensure nothing was tampered with.

Following the most recent election, some argue that increasing political polarization is dividing Americans. A new app, called Read Across the Aisle, is aiming to combat this by encouraging users to read news from media outlets on both sides of the political spectrum.

With the release of the Mirai source code, botnets are back in a big way. In the early days of botnets, zombies (infected hosts) would report to IRC (Internet Relay Chat) channels for CNC (command and control) instructions. Modern botnets have evolved, but they continue to use the same concepts as their predecessors.

Welcome back, my tenderfoot hackers! As hackers, we often are required to get past antivirus (AV) software or other security measures. To do so effectively, we need to have some understanding of how AV software works. In this tutorial, we will take a cursory view of how AV software works so that you can better strategize on how to evade detection by it.

It seems like every day now that we see a new headline on a cyber security breach. These headlines usually involve millions of records being stolen from some large financial institution or retailer. What doesn't reach the headlines are the many individual breaches that happen millions of times a day, all over the world.

The new iPhone 6 and 6 Plus have bigger displays, and that means more overall screen real estate, something that the new Safari app has taken into account by letting you access desktop versions of mobile websites. Even if you're sporting an older device, you'll still be able to request the desktop version of a site online in the browser.

While websites may run smoothly without any noticeable vulnerabilities, there's always the looming threat that any background weakness in the site can be exploited by hackers. Once a site is compromised, it can be difficult to get it fixed without the proper help. Google has recently launched a new series entitled "Webmasters help for hacked sites”, which teaches web developers and site owners how to avoid getting hacked and how to recover their website if it gets compromised in any way.

Video: . Optimize your Marketing with a Mobile Website

One of the most frustrating things on the Internet are sites that make you register just to view content. I'm not talking about paywalls—I mean the sites that make you give them personal information to look at free articles or forum threads. Most people are uncomfortable with this because a lot of these sites either spam you themselves, or sell your information to someone else who will.

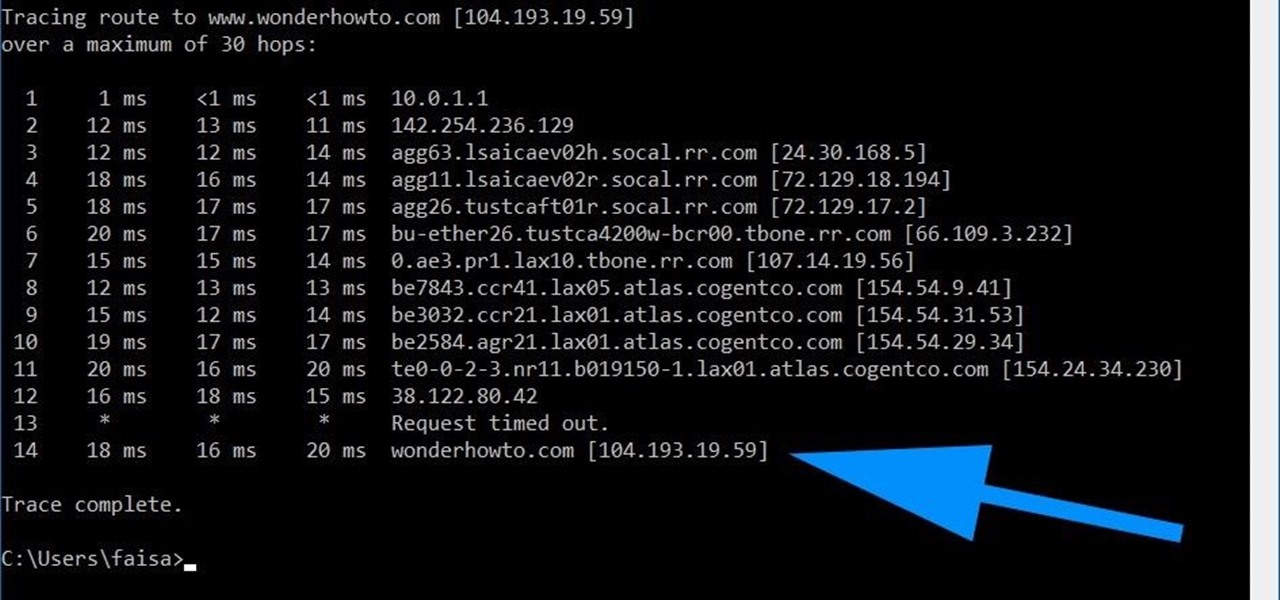
Using a simple trace trick, you can easily look up the IP address and its location for any website. This method uses a command line command to first find the IP address of a given website, and then uses a free online tool to get that IP's location.

This video tutorial is in the Computers & Programming category which will show you how to use the online discussion site Voice Thread. Voice thread enables you to create an online discussion with your students. In this video you will learn how to open an account, how to open a thread and how to post a comment on it. Go to the site. On the right hand top corner you will find a coffee cup. If you click on that, it will ask you for a username, password and email for opening an account. After you...

Wouldn't it be nice to know how many people actually visited your site each day, and how long they stayed there? Google Analytics is a great, free utility from Google that will tell you just that and so much more. In this clip, the Web Guru will show you how to use this program, generate and install an HTML code onto your site so that you can keep track of your visitors and demographics. This is a fantastic tool for advertising purposes and so you can see which content is working best for you...

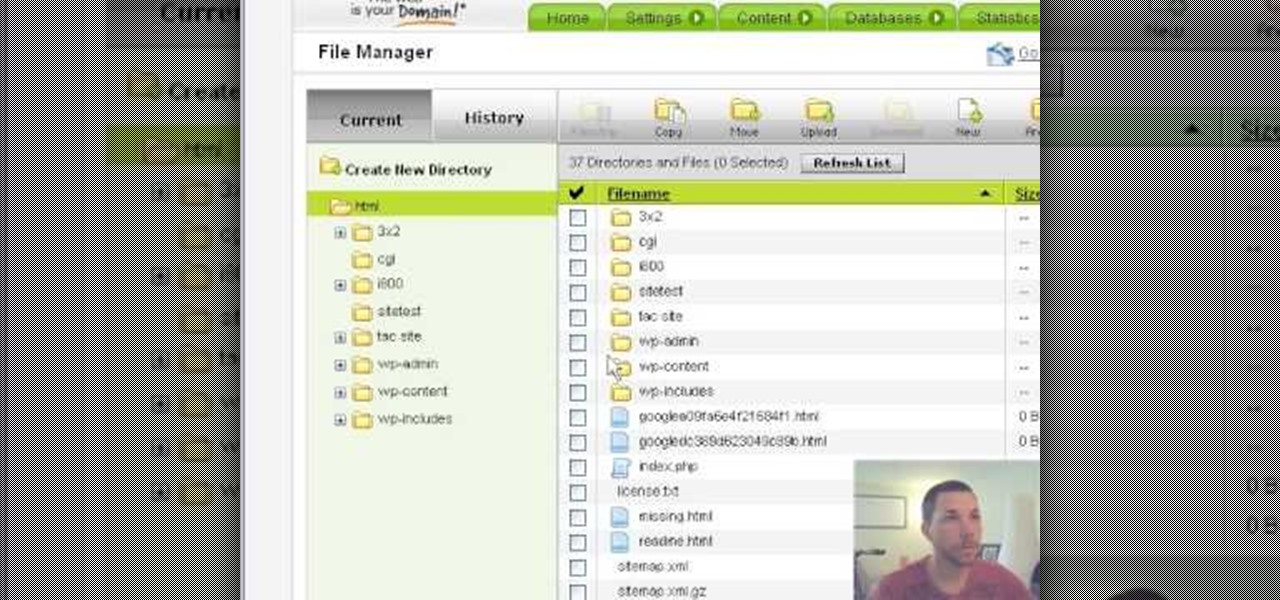
This video shows how to get more value on your GoDaddy account. You have to have a deluxe account to share domains. You have to pay an extra $2 a month to get this account. Once you sign in go to "hosting" then my "hosting account". To add another domain you move it over to a new folder then put the site files in there. To do this, click add domain then go to bulk. Then create a folder and name it what you desire. Sometimes the file folder doesn't always appear immediately, but it is there, i...

It's easy to watch Hulu on your Playstation 3 console. Using a free trial version of PlayOn, you can watch a variety of internet TV & movie sites on almost any game console - including your Wii. Who needs cable anymore? This video will show you how to set up your PlayOn account and use it to watch your favorite media sites on the console of choice.

This video tutorial explains how to structure your web site the right way using content silos. But what's a content solo, you ask? Watch this video SEO tutorial to find out. Make structural improvements to your website such that Google has an easier time isolating your keywords with this how-to.

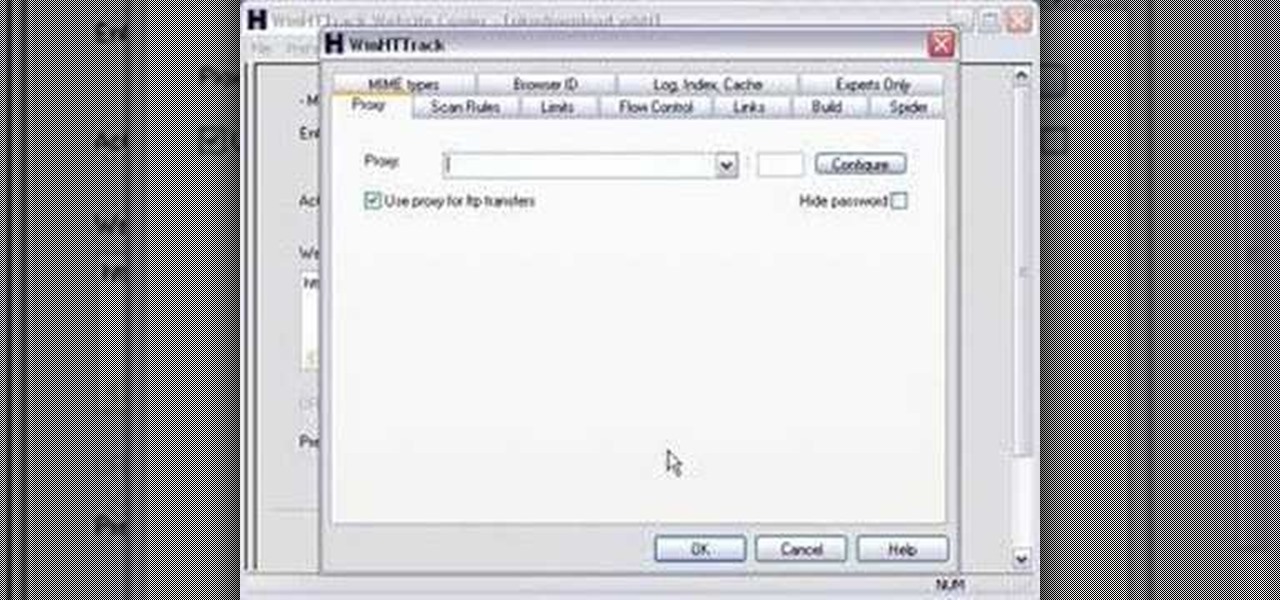
Mike Lively of Northern Kentucky Universtiy demonstrates how to grab a website's resources for reconstruction in Flex using HTTRACK and Wireshark. This tutorial is especially helpful for sites you want to grab that think they are very locked down and secure. All with the free softwares HTTRACK and Wireshark.

Here is a tutorial on using Httrack to download websites for off line viewing.Httrack is a website copier and 99% of the people on the web will use this software responsibly. This tutorial is for that 99%. Using Httrack is a great way to download a site you need to modify when the site server passwords have been lost.

As scammy as this sounds, it's actually a cool site. If you design your own clothes or cloth like items, this site will let you sell them in your own store. That's pretty dang cool. Follow the directions, and learn why Etsy is neato. From Thread Heads.