The Library of Congress video archives brings this late nineteenth century dance lesson demonstration. Follow along with the performers as they show off their traditional moves, dancing a German cotillon dance. It might take a bit of dance practice, but grab your partner, put on some music, and follow the steps. Watch this video traditional dance tutorial and learn how to do a late nineteenth century German dance, also known as cotillon, German cotillon, "Blind Man's Buff," Le Colin Maillard,...

In this sports how-to video, Farmington HS boys basketball coach Shane Wyandt and team demonstrate the shell 5 defense drill. The five man shell drill is an effective way to train defensively for basketball. Follow along with this video demonstration and learn the shell five drill.

A video about bushcraft skills is probably the last place you'd expect to find anything about men's grooming and shaving, but here we are. If you can use a cutthroat razor, you can master any blade.

Young boy shows us how to play the intro to Piano Man. Demonstrate step by step and note by note. Notation not available, but kid recounts seemingly by memory or ear.

So you've made it this far, and there's only one man that is standing in your way, and that's the masked butcher. If his exploding barrels, or grapple attacks, are causing you more than a little bit of an ache, don't worry, it's easy to beat him. In this video you will learn the strategy you will need to be victorious!

Checking your circuit breaker is so easy, a cave man could do it! (I smell a lawsuit) With this easy to follow video, you'll learn how to check the voltage with a multimeter to determine if there is a problem regarding your circuit breaker.

How to set up a Bee Hive" presented by The FruitGuys Farm Steward Program.Your purchase of organic fruit delivery supports projects helping small family farms nationwide.

A boutonniere is a body flower worn by a man on his left lapel to recognize him for a particular function. Watch this video tutorial for instructions on how to make a boutonniere.

This video will show a very easy and also fun way to draw a nice dog. Drawing a dog might be a little bit of a challenge, but after you've watched this How-To Instructional video, you will find it easy to draw a very nice dog, and also do it quickly and in a very funny way. You will also learn the story behind the trick on how to draw the dog, and the story begins with a stick man!

Garry's Mod is an excellent utility for those who are creating Machinima, or who enjoy seeing Half-Life 2 characters perform funny movements. This video shows you how to move a ragdoll around using the mysterious G-Man as a dummy.

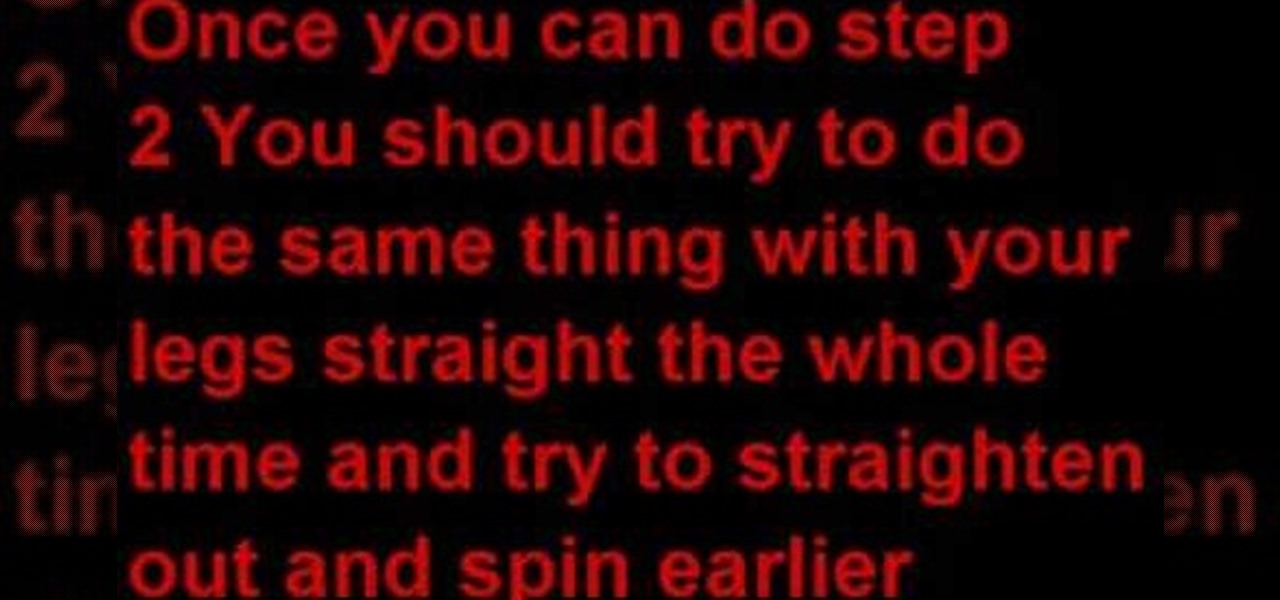
A tutorial for those who don't know how to spin with a front flip or for those who go crooked or do it improperly. This

See how to mod your Nerf Magstrike clip to make it shoot faster and farther then normal. All you need to do is cut the out the x-shaped air restrictors out of the clip to allow more air to shoot into the darts, making them fly faster than ever. Your Nerf gun will be the best on the block.

Watch this video to cook salmon and cod with Dave. Dave is cooking fish. OH MAN this looks good!!

Scottish sculptor and painter Alan Herriot shows how he made the life-size bronze sculpture of a man, titled The Ancient Mariner.

Dave talks with Tom Frost about what you need to do to get your man-made pond ready for spring: changing the water, hosing down the sides of the pond, and installing a pump and filtration media.

Here is a fun project to do for yourself or with kids! This video will take you on a step by step journey to sculpt toy men from clay.

For Android 11, Google is doubling down on the handy App Suggestions feature that debuted in Android 10's app drawer by expanding it to the home screen dock.

Google's feature drops for Pixel devices have added fun and useful new abilities, such as AR effects for Duo, Call Screen automation, scheduling Dark Mode, and Quick Access Wallet for Google Pay, that are exclusive to the company's line of smartphones.

Thanks to the COVID-19 virus, the whole country is staying home. That means no dining out, no going to bars, no live music, and, sadly, no movie theaters. While you might think that means you'll have to wait to see movies like "The Invisible Man," "Emma," and "The Hunt," think again. Because of the pandemic, you'll be able to watch these movies on your phone earlier than ever.

Despite the fact that over 600,000 Snap Lens filters have been created since Lens Studio debuted in 2017, and Facebook is reporting that more than a billion users have interacted with its Spark AR filters across Facebook properties, social augmented reality filters get a bad rap in the AR industry.

Move over, Star Wars. You're not the only Disney property that can play in the Lenovo Mirage AR headset anymore.

This week, while Apple was the subject of thinly sourced reports that it had canceled development of its oft-rumored smartglasses, the Cupertino was actually laying the foundation for its AR hardware future with a new initiative focused on mentoring Chinese developers in mobile AR development.

During the recent Augmented World Expo (AWE), we had a chance to try out the Lenovo ThinkReality A6 AR headset. Unfortunately, the experience was all downhill from there.

The augmented reality industry had enough twists this week to surprise even M. Night Shyamalan.

ARP spoofing is an attack against an Ethernet or Wi-Fi network to get between the router and the target user. In an ARP-spoofing attack, messages meant for the target are sent to the attacker instead, allowing the attacker to spy on, deny service to, or man-in-the-middle a target. One of the most popular tools for performing this attack is Ettercap, which comes preinstalled on Kali Linux.

For the augmented reality hardware industry to progress towards the consumer segment, display technology needs to get better. Investors recognize that, and they are showing AR display makers the money.

Apple first announced Business Chat, a new way for customers to communicate with companies, at WWDC 2017. While Business Chat did not arrive with the initial release of iOS 11, Apple pushed it out in iOS 11.3 so companies can offer customer service in a whole new way, and it works pretty much the same in iOS 12 and higher as it did back then.

Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing us to intercept and modify network data. This can be dangerous for private data, but also be fun for pranking your friends.

A new study casts real suspicion on the possibility of life on Mars. Why? It seems the surface of the planet may be downright uninhabitable for microbial life as we know it.

There is a reason the Amanita phalloides mushroom is called the "Death Cap." It can kill you. Mushrooms are a type of fungi, an organism that produces thread-like mycelia that often produce spores. Spores allow the fungi to reproduce. Molds, lichens, and yeast are all fungi, but the most visible fungi are mushrooms. Some fungi are delicious, but others can cause disease or, and still others, like Penicillium, can cure it.

Intense exercise can cause problems with our digestive tract. It even has a name — "Exercise-induced Gastrointestinal Syndrome." Simply put, strenuous exercise can damage the gut and let the bacteria that reside there potentially pass into the bloodstream.

Maybe you thought sitting behind a Mac gives you special protection when it comes to getting hacked. Thanks to a a new report from Check Point, you can kiss that theory goodbye. The cyber security company just uncovered the latest strain of malware — OSX/Dok — infecting all versions of macOS (previously Mac OS X).

A recent pathogen outbreak in Illinois is just one of many outbreaks of an underappreciated, but serious, viral infection passed from rodents to humans. These hantaviruses have been cropping up more frequently in the last decade or so, giving us more reason to clean out our dusty attics, basements, and garages.

New weapons are needed to combat antibiotic-resistant bacteria. Instead of drugs, scientists have discovered in an animal study that they may be able to harness vampire bacteria to vanquish pneumonia.

When most people say, "Damn, look at that rock," regarding an engagement ring, they're usually not referencing an actual rock—let alone a space rock.

Watching the NCAA Men's Division I Basketball Tournament without cable used to be easy. As long as you had an internet connection, CBS and Turner (TBS, TNT, and TruTV), which co-broadcast March Madness, let you watch all 67 games online free of charge.

Alright so last time I gave you a homework assignment. This week we're gonna look at my version of the UDP-Flooder.

Super Bowl Sunday is just around the corner. With 111.5 million viewers tuning in last year (112.6 if you count streaming), which broke another record that it previously set for the most-watched television event in U.S. history, it's safe to say that most of us will be watching Super Bowl XLIX on February 1st, 2015, whether via TV, web, or mobile.

You know you've had a long day when you head home with a headache, back pain, and eyes so sore they feel like they might roll out of your head. Turns out your medicine cabinet isn't the only place you can find help—instead of popping painkillers, just open up your wallet for instant pain relief.

Welcome back, my aspiring hackers! One of those areas of Linux that Windows users invariably struggle with is the concept of "mounting" devices and drives. In the Windows world, drives and devices are automatically "mounted" without any user effort or knowledge. Well, maybe a bit of knowledge. Most Windows users know to unmount their flash drive before removing it, but they usually think of it as "ejecting" it.