The PlayStation Phone is almost here, and the hybrid device from Sony Ericsson is rumored to have Android 2.3 (Gingerbread) as its mobile OS. YouTube user xxmajstor managed to get his hands on what is said to be the Sony Ericsson Zeus - Z1 PlayStation Phone. Below is the spy video of the device in action.

This is my list of programs that I must have on my PC, but I think you can also use them, so here is the list:

Alright, so while I can't claim to be a huge, oh my god there's Steve-O jump for joy everytime a new Jackass movie comes out, fan, I do enjoy watching the show. Now, there's a prank that I would never have the means nor balls to pull on someone I know, but those kind of pranks seem to be the Jackass bread and butter, so here goes nothing.I got this idea maybe a month and a half ago. The first step of this plan would be to somehow make one of your friends unconcious. I'm not asking questions a...

Setting up a home recording studio is daunting, but these tips on software, costs, and equipment are great; learn to build and manage your home recording studio in this free video on recording music. Set up a home recording studio - Part 1 of 15.

As a web developer, I often read articles about hackers (from the lowly to the knowledgeable) infiltrating websites via the dreaded 'SQL Injection' method and completely taking control, changing, gaining access, or destroying the owner's data. As a fellow web developer, I'm sure you want to know how to protect against it. Well, here it is! In this article, you will find out what SQL Injection is, what you can do to protect against it, and additional recommendations that are easy to do and onl...

It's somewhat funny that the HTC ThunderBolt smartphone would be released around the same time as Apple's new Thunderbolt technology. Mainly because HTC's smartphone isn't exactly something I would compare to a flash of lightning, which averages around 60,000 miles per second. But Apple's new interconnect surely deserves the Thunderbolt designation.

New Year's Eve. It will be one hell of a chaotic night. Trust me. The overcrowded streets. Long lines for the urinal. Maxing out your credit card on that shot of Cuervo. You'll be lucky to make it out alive.

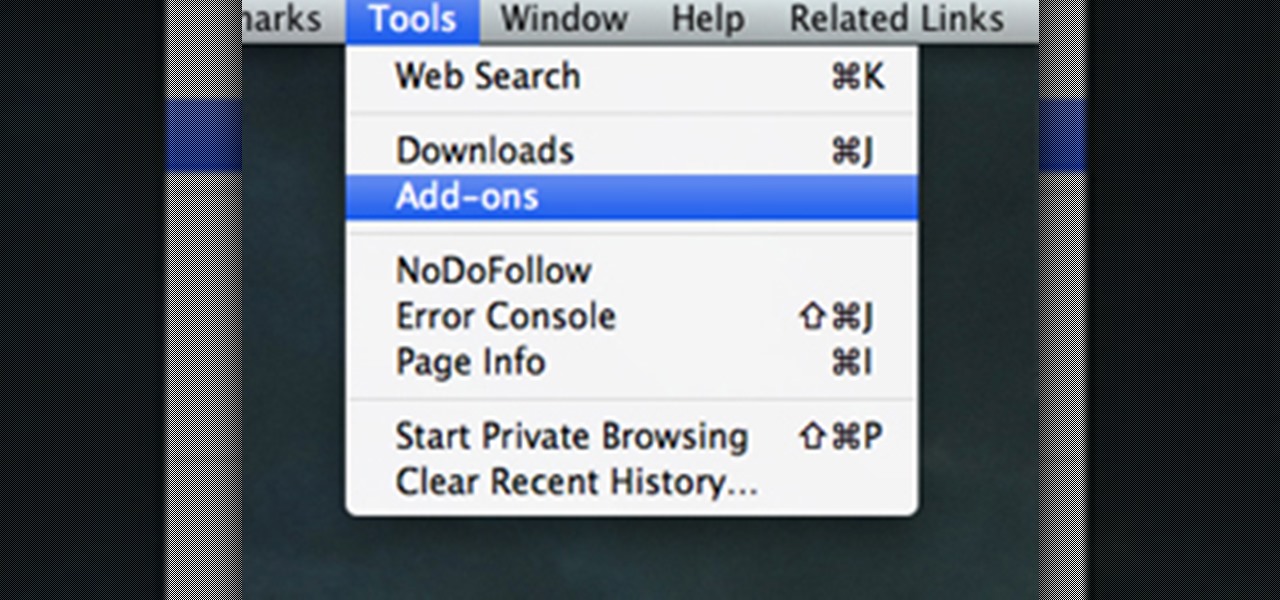
There's a whole lot of brouhaha going on right now about the hidden plug-ins being installed unknowingly in the Mozilla Firefox web browser, with companies like Apple, Microsoft and even Google being named top offenders.

If you're someone who shares a lot of tweets outside of Twitter, you know the struggle. Twitter's share button, like YouTube's, is proprietary, which means you need to wade through Twitter's own sharing options to find your iPhone's regular Share sheet instead. However, there's a hidden trick that lets you open the stock iOS sharing options right away.

Minecart rides primarily serve two different functions—transportation or entertainment. We rarely see minecart-based transportation systems in Minecraft these days because most servers support warps or allow users to set multiple homes that they can simply teleport to. That leaves the primary purpose of entertainment.

In my Wireshark article, we talked a little bit about packet sniffing, but we focused more on the underlying protocols and models. Now, I'd like to dive right back into Wireshark and start stealing packets.

No doubt you've seen some of the hack logs being released. One part that stands out over and over again is the heavy database usage. It used to be early on that virus and hackers would destroy data, usually just for lulz. However, with the explosive commercial growth of the Internet, the real target is turning into data theft. You should learn how this happens so you can protect yourself accordingly. Let's take a look at what makes this possible and dare I say, easy.

What is a burn? It's a form of injury to body tissues which is caused by heat, corrosive substances or friction. There is another form of burn, which is known as scald; it results from exposure to hot water or steam.

Google+ has managed to double their user count from three months ago, now standing at over 90 million Google+ accounts created. But how did it get so many so quick? By tricking people who are signing up for Gmail or a regular Google account into setting up a Google+ account, too.
Sergio Peralta Advisor: Jessica Davis

If you've read Alex Long's last two articles in this series (Part 1 and Part 2), you know by now that making money rarely is risk free, and generally plays out to be a high risk-high gain/loss scenario. The best way to make money is to have money, so for this article, lets assume a financial backing of about $10,000 dollars. For the sake of simplicity, I'm going to be working with online trading systems in this article. Some stocks are traded on exchanges, where buyers meet sellers and decide...

Skyrim really took the cake this year. With its awe-inspiring gameplay, much improved combat and leveling system, and a fresh new look, it's no wonder the game has already received a Game of the Year award. But for hardcore gamers, the fun may be over. You've played the game for thousands of hours, and have exhausted the entire game's main and auxiliary quests. You need more.

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server.

By now, most of you have updated to the new Xbox look. Just as expected, it's got some great new features. The dashboard looks great and Bing integration is awesome, but I'm very unhappy about the new Netflix interface. It's awkward, slow, and half of the items don't even load correctly. I can't even play some movies. And the instant play feature is kind of annoying. When I first chose a video, I was hoping when it instantly started playing that it was a trailer, à la Zune. Alas, no.

Now that it's been a week since Google+ rolled out pages, we've gotten over our euphoria at finally getting the feature after a long wait, and reality is starting to sink it. It's not as flexible as a Facebook page, it seems to be time consuming, and you can't even get a unique URL. On the other hand, your Google+ page will show up in Google searches, and help bump you up a bit. Here's how the search stacks up when I search for "WonderHowTo" in Yahoo! vs. Google (Note: I've turned on private ...

Kaplan University nursing alum Debra Eppley was already working in the nursing field when she started her RN-to-Bachelor of Science in Nursing completion program (RN-to-BSN program). Kaplan University’s flexibility and support offered her the opportunity to complete her degree online while continuing to work. Once she completed her Bachelor of Science Nursing online, she was able to make a career move that not only increased her salary, but also her level of job satisfaction.

One of the primary goals of a social network is for you to share what you find interesting with your followers and friends, but on Google+, sharing has so many layers that it can be confusing for most people to really take advantage of it properly. Some of the tools in place that enable you do deal with spam and manage your privacy aren't very clear, so this week's round up is all about how you can share what you want with who you want on Google+.

G+Me is one of our favorite Chrome extensions here at Google+ Insider's Guide. We love it because it's one of the most comprehensive extensions out there. It attempts to address the "noisy streams" issue, with list mode, and collapsible posts and comments. The creator, +Huy Zing, is very responsive to feedback, and he's been quick to address any issues that arise, including privacy concerns. He's even created a G+Me (Paranoid Edition) extension, for the extra careful Google+ user. And if you ...

Both Google+ and Facebook are competing for your time and space, and your commitment to one social network. To make their spaces more attractive to you, they've both made it easier for you to deal with people you don't like or don't care for.

Shadows of the Dammed (360/PS3) is a polarizing game. It's not shy of being crass and crude. Go ahead and judge the game by the following examples (click to enlarge):

When Apple‘s iTunes was introduced back in 2001, it rekindled my interest and purchasing of music. I was so excited by the program that I immediately started converting all my rather large collection of CDs into MP3 tracks. I then sold off my CDs and remaining vinyl albums, and used the money for additional iTunes purchases. iTunes made managing and listening music a wholly different experience. But in the last few years, iTunes has taken a back seat to streaming music services, which I find ...

In many of my articles, I will refer to applications designed to empower Mac users to automate various tasks on their computer. One such application is called Hazel. Like smart folders, smart playlists, and smart albums found in Mac OS X and iPhoto, Hazel can automate the task of moving, copying, or deleting files in folders on your Mac. I recommend Hazel as one of the most essential applications for any Mac user. Let's explore how it works.

No game is perfect. Well maybe except for Super Mario Brothers 3. In the last two posts I've been praising Tera but it's not without its shortcomings.

I've decided to write this post so some of the fledgling street artists who may or may not follow this world in the future are informed about two things in the urban art world that are either not discussed at all, or distorted (intentionally or otherwise) to the point of misinformation. Those two things are, as the title says, the dangers of street art, and the morals of street art.

Sounds like a false promise à la infomercial or typical spammy web headline—how can a 4.8 ounce gadget aid in weight loss? But, in truth, "who" better to act as a dedicated personal trainer and nutritionalist than the iPhone? The smartphone is completely and utterly tethered to the daily life of the average middle to upper class American. It's reliable and exact. All it needs is a charged battery, the right app, and of course, as with every diet and fitness regime, a user with unwavering self...

How to produce strange noises using your mouth and throat. Guttural Noises

By Cal Ripken Jr. Let the players play and the coaches coach !

Kurt Harris, MD, writes about paleolithic nutrition at his highly recommended blog, www.paleonu.com.

What's your training about? Would any of it matter if your life depended upon it? If not, what is your training providing you with?

Hello, everyone. My friend and I recently released a Defense of the Ancients (DotA) map that went viral and thought I should share it with Minecraft World on WonderHowTo since you guys helped me out when I first started making videos! We were featured on Kotaku, RockPaperShotgun, Gamespy, The Verge, Joystiq and many more websites!Exciting!You can see the full details below are head straight here for the downloads.

Welcome to Minecraft World! Check out our tutorials, post to the community corkboard, and come play on our free server!

Injection is an attack vector that involves breaking out of a data context and switching into a programming context through the use of special characters. These characters are significant to the interpreter being used, but not needed for the general user input being asked for.

Wouldn't it be nice to just sit at your buddy's house, plug into his network, and see exactly what he's doing? What if it was as easy as that? What makes packet sniffers like Wireshark such potent tools is that a majority of local area networks (LANs) are based on the shared Ethernet notion.

In my recent Darknet series, I attempted to connect the dots on the Deep Web. I covered the two largest anonymity networks on the Internet today, Tor and I2P. While my initial four articles were meant as an introduction, I ended up receiving a lot of interesting comments and messages asking the technical differences between the two. I'd like to thank all of you for letting me know what was on your minds, as you should always!

Many windows users, if not all, run into a virus infection once in a while. This is unavoidable when using Microsoft's operating system. Without digressing too much, the fact that Windows is such a popular OS with no controlled software sources makes it easy for viruses and malware to spread. And while there's a plethora of antivirus tools for Windows, sometimes infections (such as certain scareware) can disable the install and/or use of antivirus systems and render your OS unusable until cle...