The photo-centric Instagram app is a great way to share "evergreen" pictures and videos when compared to Snapchat and Facebook's new Messenger Day feature. But like all social media, keeping the account secure is an essential aspect, as it restricts unwanted viewers from seeing your content and can prevent unauthorized users from accessing your account. Instagram has several methods for locking down the account including a new two-factor authentication (2FA) mechanism.

Xiaomi phones run a skinned version of Android known as MIUI, which, over the years, has been a popular custom ROM. One of the standout features Xiaomi has added to the mix is something called Quick Ball, which lets you navigate your phone by swiping inward from a small circle that resides on the edge of your screen.

While there are many uses for augmented reality in the automotive industry, adoption has been slow. With the plethora of makes and models on the road today and rolling off assembly lines tomorrow, developing and deploying knowledge bases that utilize augmented reality to dealerships and garages can be costly and difficult to scale.

If you have stuck volume buttons, it can be a real pain to adjust sound levels since your only other option is to use the volume menu in Settings. But even if your volume rocker is working fine, it's still a little weird to have to click a mechanical button to control one of the most central aspects of an operating system that is otherwise entirely touch-based.

Android's notification system is quite robust, especially now that Google added bundled notifications and quick reply features to Android 7.0 Nougat. However, things can still get quite cluttered when you have several unread messages, which fills your status bar with icons and makes your notification tray take up half of the screen by itself.

Everyone loves sharing pictures and quick video clips with Snapchat, but while the service itself is tons of fun, the Android app is one of the worst on the market. For one, Snapchat takes terrible photos even on high-end Android phones. And to make matters worse, the app is a notorious data-sucking battery drainer.

The Pixel XL reportedly uses the same exact display panel as the Galaxy S7 Edge, but according to third-party testing, Samsung's flagship gets at least ten percent brighter than Google's. The same can be said of the regular Pixel, which tops out just shy of its bigger brother's brightness rating.

In 4.74 seconds, I can barely bend over to tie my shoes, and somehow this guy managed to crush the human world record for solving the Rubik's Cube in that time exactly.

Few companies have maintained such intense secrecy, in the face of such extreme hype, as Magic Leap, but the closer their mysterious Mixed Reality product comes to mass production, the harder it becomes to hide the details. Hopefully we'll find out way more details soon, as a Magic Leap job posting for a supply chain manager hint that they're readying for release in the next couple years.

As the first phones to be made by Google, the new Pixel and Pixel XL have several slick customizations that you won't find on any other Android device. There's tons of functional stuff like the new Google Assistant and a much-improved camera app, but also a few aesthetic tweaks to help class up the joint.

Google's new Pixel and Pixel XL smartphones are available for pre-order right now, but the general public won't start to get their hands on these devices for another week or two. Tech reporters got some hands-on time at Google's launch event on October 4th, but camera testing wasn't allowed, and the Wi-Fi coverage at the event was too flooded for real-world performance reviews.

While Leap Motion and Microsoft are looking to capture natural human motion with cameras, Enflux figured out how to do it with a shirt and pants that feel completely natural.

When it comes to hacking guides, most are written from the perspective of a Linux user. There are a few outliers, but it's mainly Linux, which leads to the idea that Linux is the only OS that's viable for hacking. This couldn't be further from the truth. A properly set up Apple machine can do quite a bit of heavy lifting.

Microsoft has the HoloLens and Google has their money on Magic Leap (as well as their own Tango and Cardboard, among others), but we've heard next to nothing about how Apple plans to enter the virtual/augmented/mixed reality space. A new patent offers some clues.

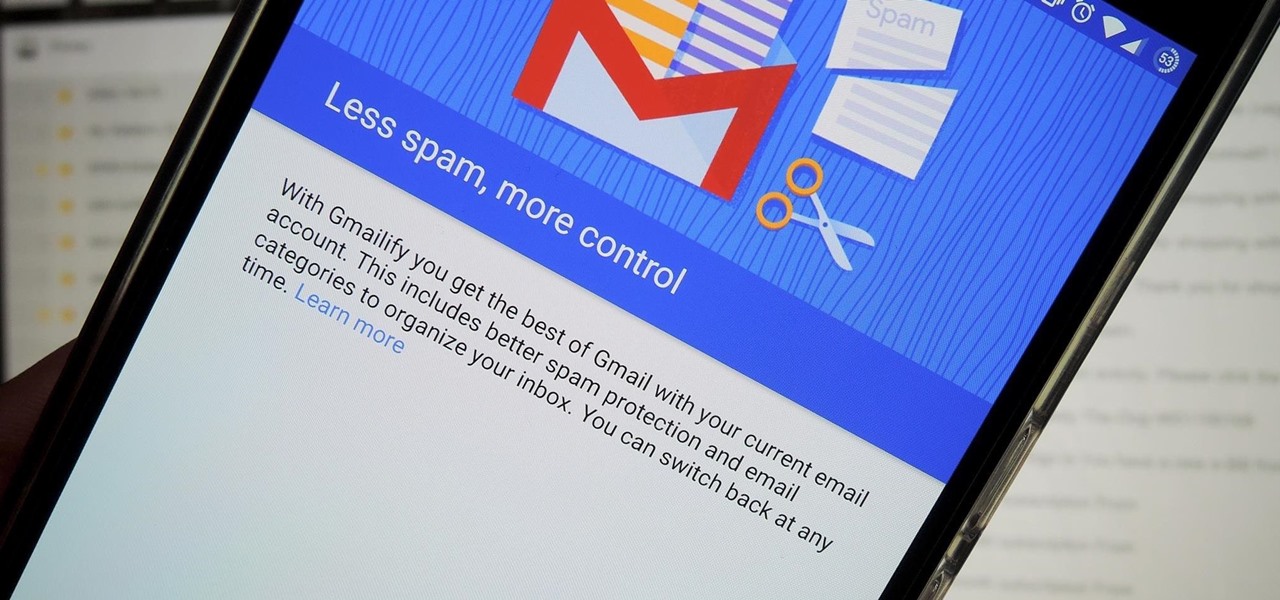
Gmail has been the email standard for quite some time now, and for good reason: it's a free service provided by one of the largest tech companies in the world that offers users an amazing feature set to manage, send, and keep track of all their important emails.

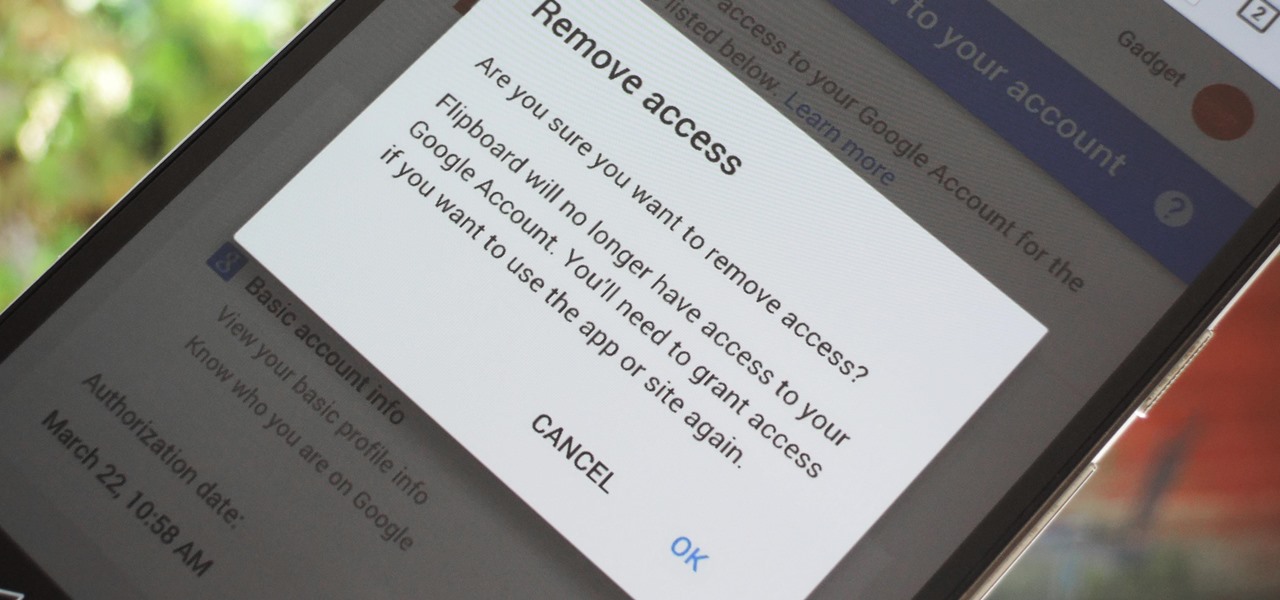
Many apps and services that are available for Android can only work if they have access to your Google account. While you're setting up one of these apps, you'll see a popup that says something like "This app would like to access your Google account," and the options are "Accept" or "Cancel." Of course we tap "Accept" here to ensure that the app will work properly, but what are the long-term repercussions of doing that?

The new lock screen in iOS 10 is a lot different than previous versions, but one thing that stuck around is the quick access camera shortcut. The only real difference aside from aesthetics is that now you don't have to swipe up from the camera icon. Instead, you can simply swipe to the left from right side to quickly snap a picture.

HTC's newest flagship smartphone, the HTC 10, has been met with nearly universal acclaim despite a weak amount of sales over the last few months. Most reviewers point to the device's gorgeous hardware as its main attraction, but at the same time, it certainly has some nice software to match, as this year's Sense 8 may be one of the best manufacturer skins ever.

Augmented reality (AR) holds much promise for how we'll interact with technology in the future, but we still have many hurdles to clear before that dream fully comes to fruition.

The biggest problem with plastic wrap is also its most useful trait: its incredibly clingy nature. Plastic wrap seems to stick to itself or you before you can get it over the plate, bowl, or food you're trying to preserve. And once you do manage to get it in the right position, it never sticks as well as you need it to. Fortunately, you can combat these inconveniences with two extremely helpful methods—a change in temperature or a bit of added moisture—as Jenny Stewart of CHOW explains in the...

Virtual reality and horror were meant for each other. You'll get all the positive aspects of experiencing a terrifying situation such as excitement and an adrenaline rush, without any of the real-life consequences, like being ripped to shreds by a herd of flesh-eating monsters.

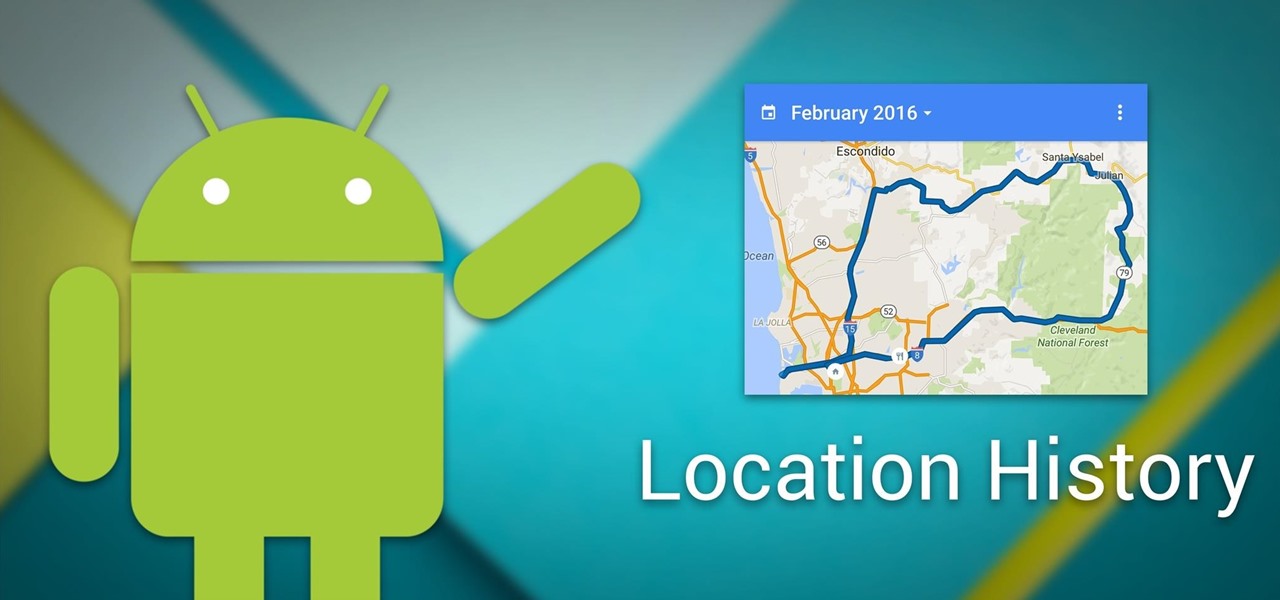
Your smartphone has a GPS chip inside of it that can pinpoint your location down to the nearest 4 meters, and this little device stays in your pocket or purse all day. Combine those two facts and you start to realize that your phone knows exactly where you've been during every moment that has passed since you've owned it.

Just about a year ago, Google launched an update to the Gmail app for Android that let you link accounts from other email services to Gmail, allowing you to read and respond to everything in one place.

So yeah. Its AugustFackYou and I felt like posting today and being an active member of the community. After reading this please tell me if you have any comments on what I can do better or if this method is bad. Anyway today I will be showing you how to get root on a mac. I managed to become an administrator at my school with this and one other method.

In my last tutorial I very briefly introduced Zanti , but in this tutorial I will start to show its many features. The first step on hacking is recon . You could use Nmap , but the problem with Nmap on Android is that by itself, in order to gain full functionality your phone must be rooted. Thank goodness for a few geniuses in Zanti's dev team whom managed to implant full fuctionality of Nmap in Zanti without rooting your phone. With that being said, boot up your Android phone and lets start ...

All across the web, you'll find guides on setting up various apps and mods for your Android device—but while these are certainly useful, they all seem to be working under the assumption that the reader has a certain level of knowledge about Android. For someone that's just getting started with the world's most popular mobile operating system, the basics of Android simply aren't covered as well as they should be.

What's up, peeps? In this quick tutorial, we will be looking at structs, a special kind of data type.

Most people are familiar with the fact that vinegar adds sourness to a dish, in varying degrees from light acidity to puckering acid. However, vinegar can also be used in lieu of salt when seasoning the final touches to sauces, soups, and stews.

Managing hard drives in Linux is crucial to understanding your system and its operation as well as understanding the system you are exploiting or conducting a forensic analysis on. Linux has numerous commands that can provide us with information, control, and management of hard drives, and in this tutorial, we will examine a number of the most important ones.
Basically, this article is a true life experience writing from the introspective mind of the writer and do share more knowledge on how to deal with introvert lifestyle.

The Fire TV Stick, as well as the Fire TV, may be limited by Amazon's fight on piracy, but after a quick sideloading of Kodi, the floodgates are back open with the freedom to stream just about any video or song you want.

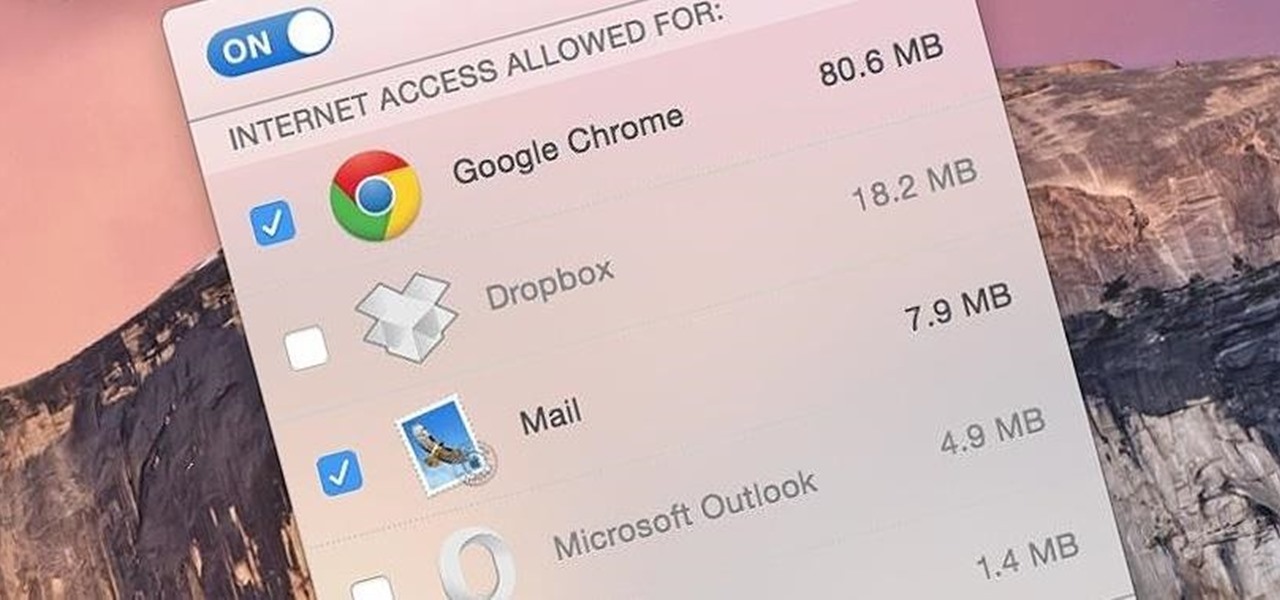
If you exceed your monthly mobile data limit, your cell phone bill can skyrocket pretty quickly. This is why a lot of people vigilantly monitor internet usage and even uninstall apps that use too much background data.

Hackers are claiming money for a security flaw in Apple's new update. Quick Summary:

I'm lucky enough to have internet access on my laptop practically everywhere I go because of my mobile hotspot plan. All I have to do is enable the personal hotspot feature from my iPhone and I can surf the web on any Wi-Fi enabled device. But of course, there's a catch.

Hackers have stolen over 225,000 Apple user's account information from countries all over the world—including the United States, China, and France—in what many are reporting to be the biggest known Apple hack in history.

MagicTree is often the go-to tool for data collection and reporting for many pentesters. It organizes data in nodes in a tree-structure which is very efficient at managing host and network data. Reports can be completely customized to meet the user's needs. Also, MagicTree allows you to import XML data and has XSLT transforms for Nessus, Nmap, OpenVas, Burp, Nikto. MagicTree comes pre-installed in Kali.

The Ring/Silent switch on the side of the iPhone has always had one purpose—to toggle ring mode/silent mode. But in iOS 9, Apple gave us another choice, and that's locking the orientation of the screen.

The Galaxy S6 Edge comes with a useful feature called Information stream that allows you to view quick tidbits of info with a quick back-and-forth swipe on the edge of your display while the screen is off. Apparently, Samsung left the door open for third-party plugins to use this feature, and now we're starting to see an influx of useful additions.

Accessing and getting in touch with your favorite contacts has never been easier thanks to the "Friends" feature on the Apple Watch. However, this only applies to users who are running watchOS 2.2.2 and lower. When Apple issued watchOS 3, the "Friends" option was completely removed. So if you're running watchOS 3 or higher, you won't be able to follow these instructions.

Today we are pleased to announce the end to the Apple vs. Android war. About a year ago, our Gadget Hacks team started working on a top-secret project to dual-boot both Android and iOS on the same phone—and we couldn't be more proud to announce that we've finally succeeded! Your phone can now run both iOS and Android—whenever you want. Right now.