
News: Patent Applications Offer Closer Look at Magic Leap One & How It May Work
Eventually, even the most private company has to file its patents and unveil its tightly-held secrets, and Magic Leap is no exception.


Eventually, even the most private company has to file its patents and unveil its tightly-held secrets, and Magic Leap is no exception.
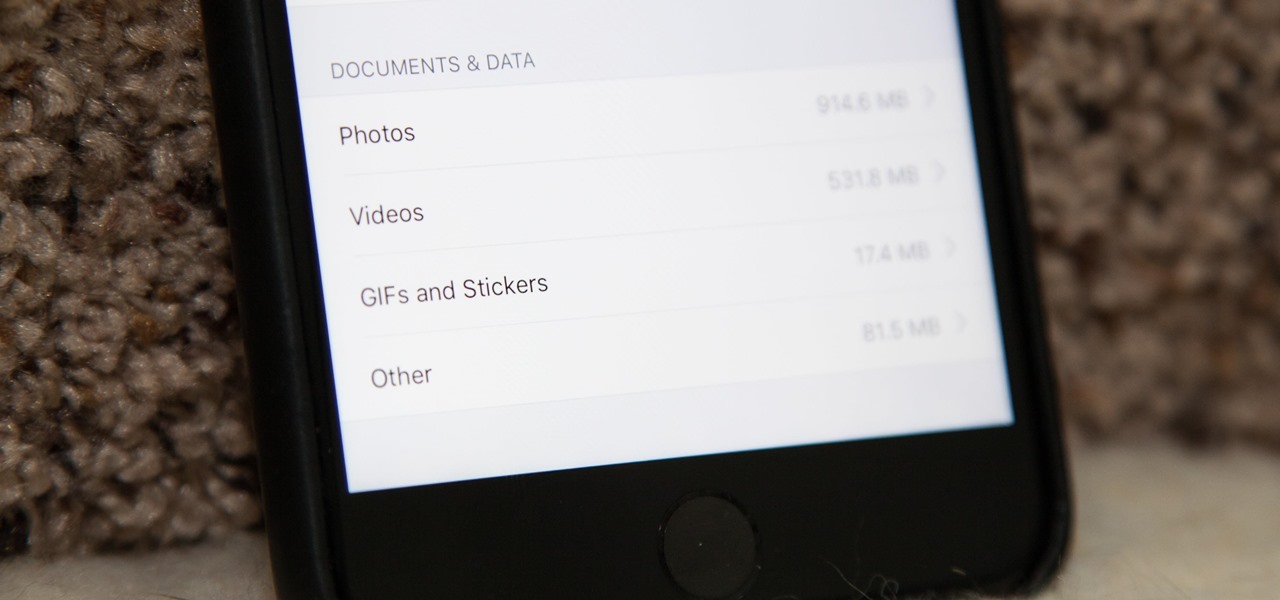
One major iOS 11 improvement that Apple skimped out on during its WWDC presentation was the redesigned storage management system, which makes it easy to view storage consumption in greater detail on your iPhone — and even easier to free up storage space with surgical precision.
To contemporize a popular quote, "A cluttered desk(top) is a sign of a cluttered mind." Of course, it's difficult to maintain a tidy desktop... as you read this, mine is cluttered with screenshots, folders, Word documents, videos, pictures, and apps.

I dabble in video editing, and when working on even the shortest of motion graphics clips, the exported files take up quite a bit of space. For all of you heavy Mac users out there, I'm sure you know my pain.
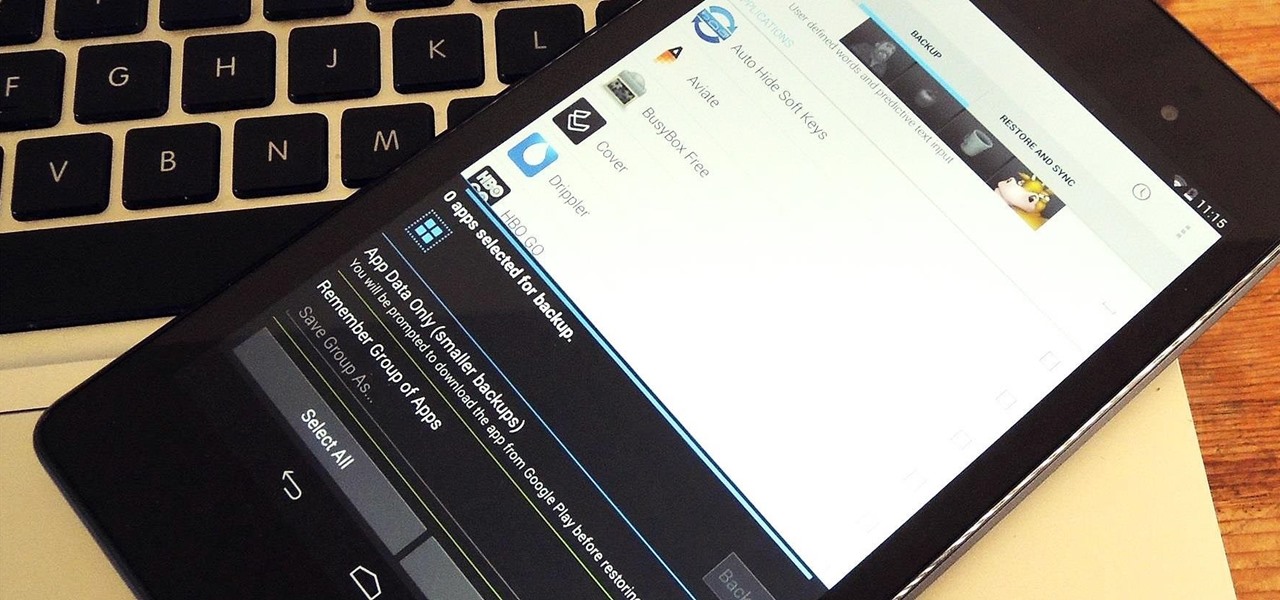
At some point, we all need to back up our device. Maybe it's time to take it in for repairs or maybe you're just cautious and paranoid. Maybe you're trying out a new ROM on your Nexus 7—then you definitely need to back up. The most secure way would be to use a custom recovery like ClockworkMod or TWRP, but if you're not rooted or planning to root, then you'll need an easy alternative.
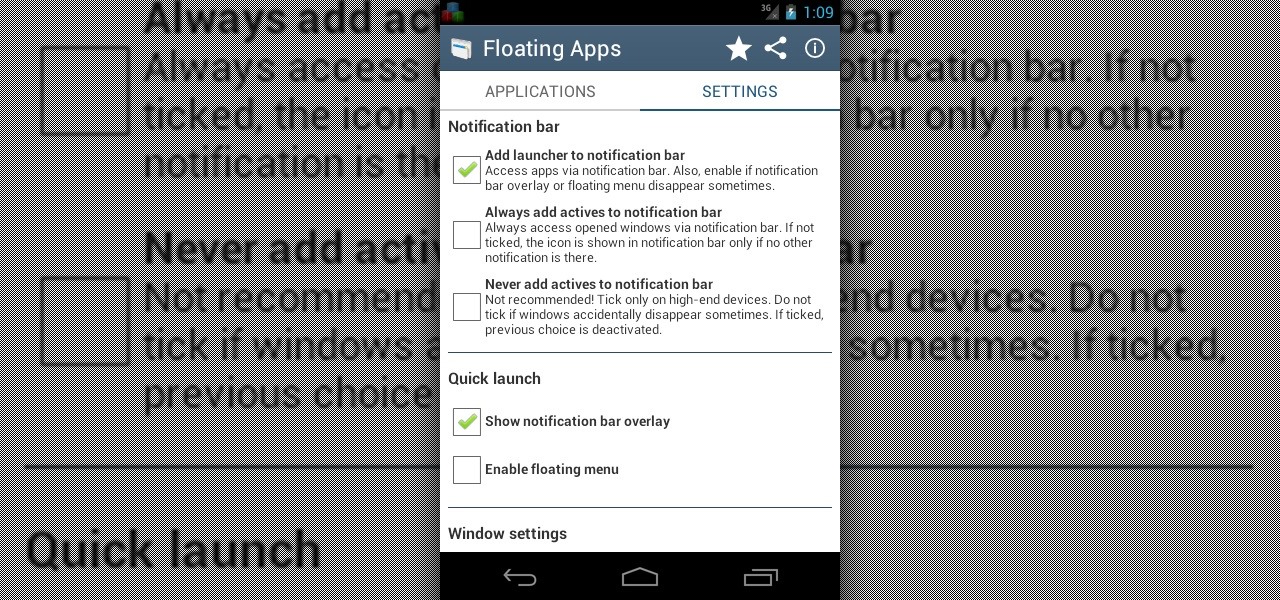
Sometimes, it's very useful to be able to use more than one app on Android phone or tablet. For example, if you want to watch a movie while surfing or if you need calculator, find some contact, write a note, search web or wikipedia for some facts, etc.

Managing multiple applications on an iPhone is as simple as double-tapping the home button, long pressing the app you want to close, and tapping on the minus sign in the red circle. If you're using Mac OS X, the dock at the bottom of the home screen plays the role of the multitasking bar on the iPhone, just not as sleek or simple.

Syncing photos onto your iPhone using iTunes can be a bit of a hassle. You have to connect the iPhone, create a folder with the pictures you want exported, and wait until it all syncs onto the phone. This is not only time consuming, but annoying with having to do it every time you want to transfer a picture.

Android has released a new application called ezNetScan, which is a free app that scans the wireless network you're connected to and gives you a full log of all of the devices connected to that network. This isn't new for smartphone users, let alone Android users. Fing has been around for a while and does practically the same thing that exNetScan does. It gathers information such as the IP and MAC addresses, device vendors, and ISP location. But while Fing is a great program, it does lack a f...

There's a million web games spread throughout the internet now, and if you like to play them, you probably want to play them all the time. And if you play one flash game, you probably play another, maybe 10 or 20. But what if you don't have an internet connection one day? What if you can't play those web games anymore? Well, you can, and all you have to do is download them to your computer. Watch to see how to download and play web-based flash games on your computer without web access.

Ipad is a revolutionary device from Apple with some amazing features. One of the major functions of Ipad is to serve as a E-book reader. Apple provides an application called Ibooks using which you can read ebooks on your device. You can also browse and purchase new ebooks using this applications. Launch Ibooks from your applications menu and it will take you to the collection of books that you already have on your device. Click the store button to visit the books store. From the store you can...

Have a new app that you want to pin to your home screen on your Android enabled mobile device? Slapping the application on the home screen is simple on any Android phone. Best Buy has answers. The Best Buy Mobile team explains how simple it is to add apps to your home screen on an Android cell phone.

Want to forget about always pulling out your credit card to purchase something on your BlackBerry? There's a little application that can do it all for you? But how? Best Buy has answers. The Best Buy Mobile team explains how to use the BlackBerry Wallet application. This application can store personal information such as credit card information and shipping addresses on a secure website for easy access when shopping online.

Looking to fix your iPhone home button? Do you have a broken HOME button on your iPhone? In this video, learn how to get around it with an application called "mquickdo", formerly known as iHome for jailbroken iPhones. This also works for iPhone 1G or 2G and iPod 1G or 2G. Mquickdo allows you to use a series of finger swipes to function as the home button. This includes putting your iPod to sleep, going back to the home page, the double tap music menu, exiting an application, and more.

We love ponytails - for yoga class. They're ridiculously easy to throw together, which is why they're great for on-the-go hair management. But just because the ponytail is a practical, functional look doesn't mean you can't dress it up and wear it to formal occasions like cocktail parties and work.

Curtis Smith provides information on how to use chickens to control garden pests. Using chickens keeps the use of pesticides to a minimum and keeps plants healthier. In the organic garden, chickens are used because they'll eat any insect as well. The process is known as Integrated Pest Management, Curtis explains that its basically knowing your pest. It also reduces the amount of feed that has to be purchased for the chickens because they're eating the insects in the garden. It also controls ...
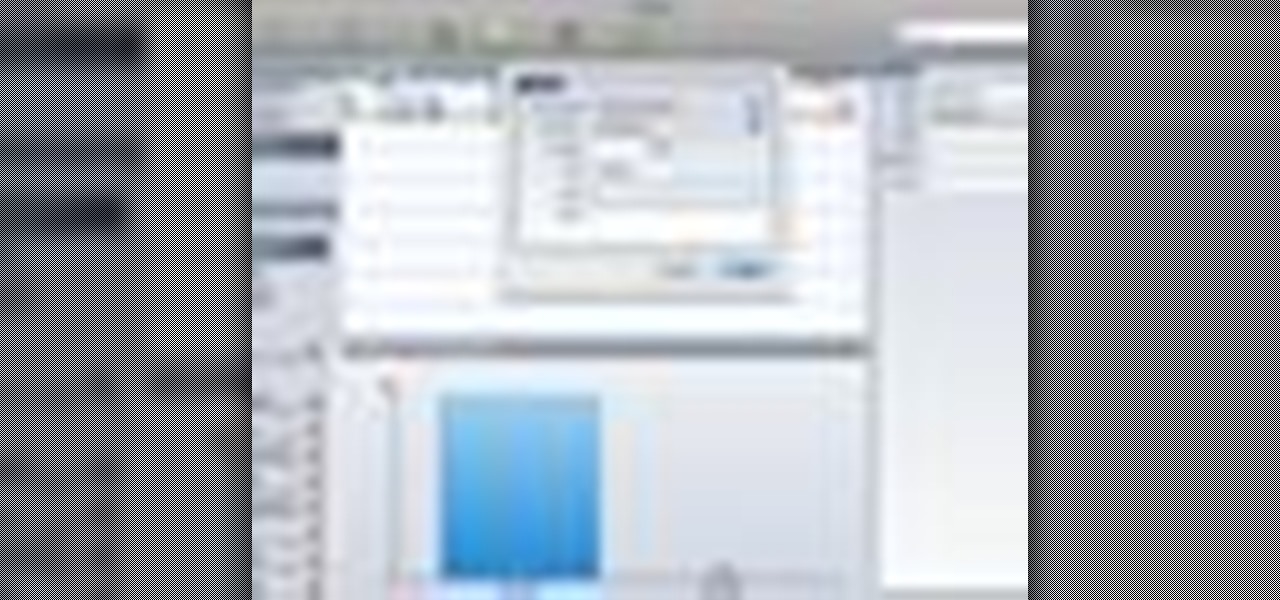
Transferring money can be quite tricky, but keeping track of it can be even trickier. MoneyWell makes transferring money from one account to another incredibly easy. This video tutorial for beginner users shows you how to work with transfers in the budgeting software.
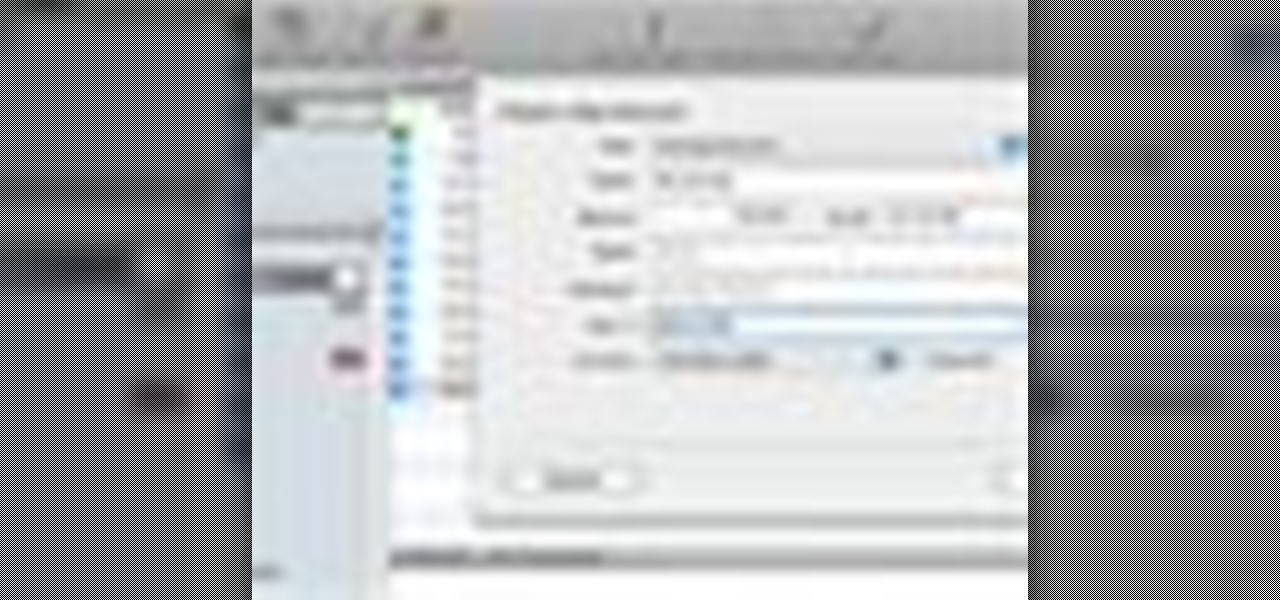
Keeping your money in check can be quite difficult. That's where MoneyWell comes in. This is a video tutorial on getting started with MoneyWell, so watch and learn the basics and see if it's right for you.
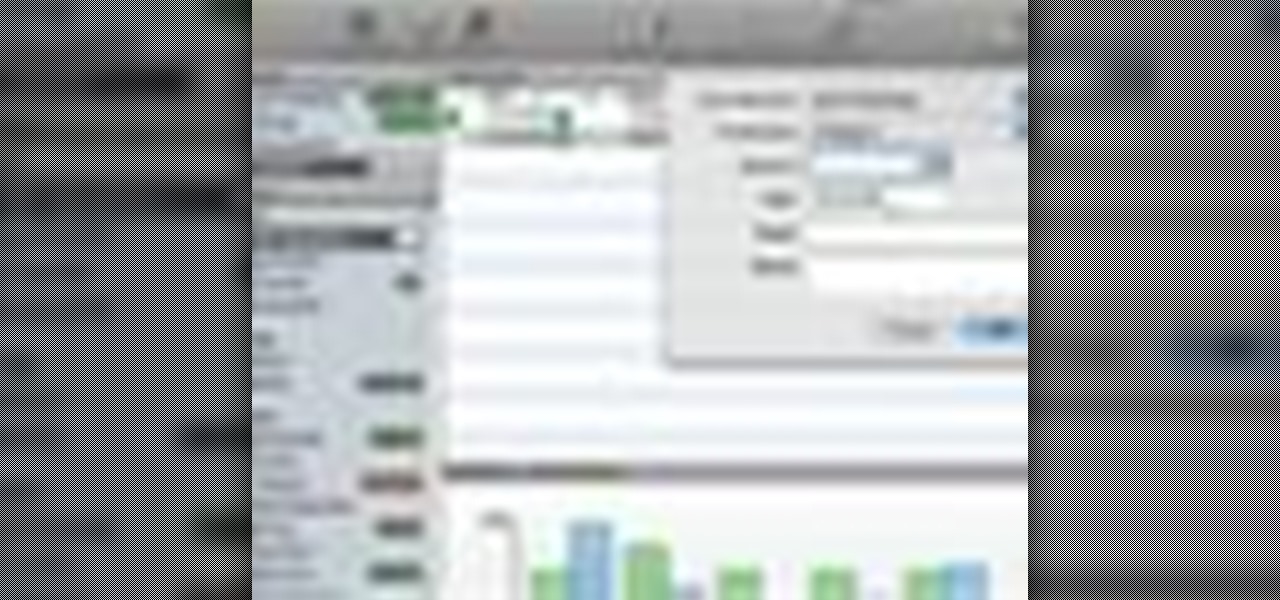
One way to keep your budget in line is with MoneyWell. This video tutorial for beginner users teaches you the ins and outs of setting up credit cards accounts, and how to manage them.

Learning to highlight transferable skills on your resume is good for recent college graduates or if you are new to a job field because it shows that you have good characteristics that can be applied to your new job. For example, showing your communication skills is very important. Research planning is also critical. Show that you set goals for yourself and that you have clear ideas. Also, giving examples of when you used teamwork in past work experience in your life or in your career is benef...
Instead of using Photoshop, why not give Apple's Aperture a try? Aperture is designed more for post-production work for professional photographers, letting you cull through shoots, enhance images, manage massive libraries, and deliver stunning photos.
Instead of using Photoshop, why not give Apple's Aperture a try? Aperture is designed more for post-production work for professional photographers, letting you cull through shoots, enhance images, manage massive libraries, and deliver stunning photos.

Get your dose of the coolest Adobe Lightroom tutorials, tips, time-saving shortcuts, photographic inspiration, and undocumented tricks with Matt Kloskowski from Photoshop User TV. Photoshop Lightroom is the leading photo management software solution. See what leading photographers use to manage their photos, and how.
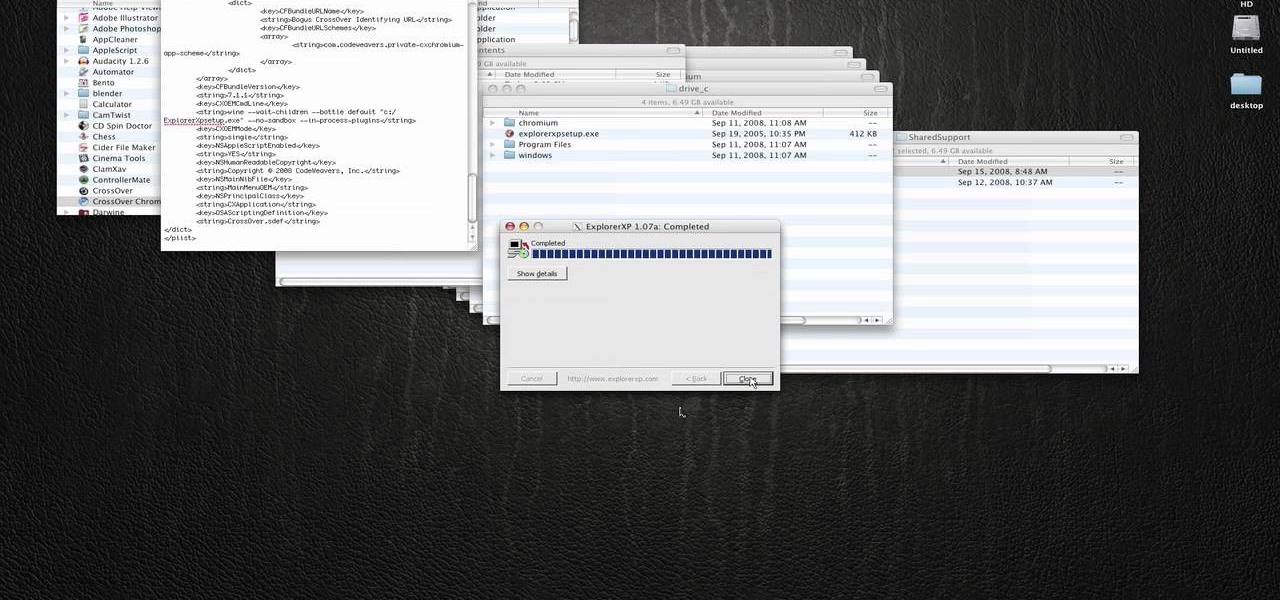
In this how to video, you will learn how to run Windows programs for free on a Mac using Crossover Chromium. You will need to download Crossover and install it by downloading it and dragging it into the applications folder. You will also need Explorer XP. Go to the applications folder and show the package content of Crossover. Go to shared support as you will need a file here later. Open Chromium, go to support, Chromium, and Drive, and then drop Explorer XP into the folder. Open the info fil...
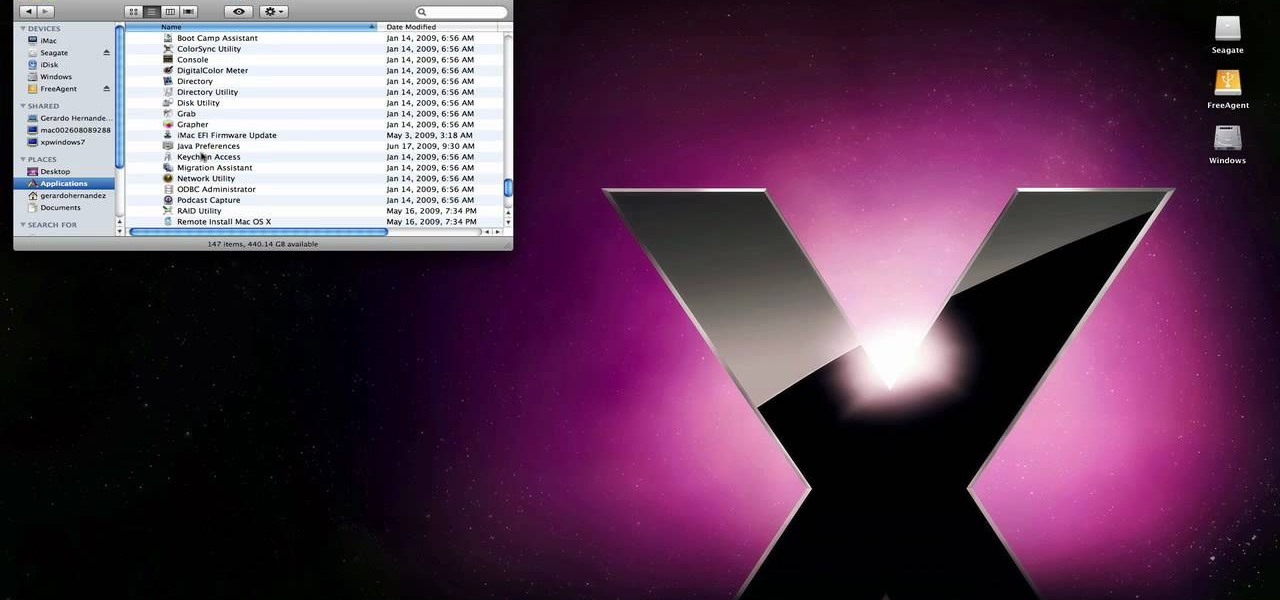
techstuff1227 narrates an HD-quality educational video about how to remove a Windows partition from a Macintosh computer using the Bootcamp software. To accomplish this easy task: open the Finder application, view your installed Applications, browse to the Utilities list and expand it to view the Disk Utility. Open the Disk Utility application. Once the hard drive information is displayed, click on the Windows partition, click on the minus (-) button, and a confirmation dialog will appear. Cl...

HOW TO UNLOCK & USE THE FM TRANSMITTER ON NOKIA N900: Nokia N900 officially has FM Radio receiver but not a transmitter. Here are step by step procedure to enable & use the FM transmitter facility.
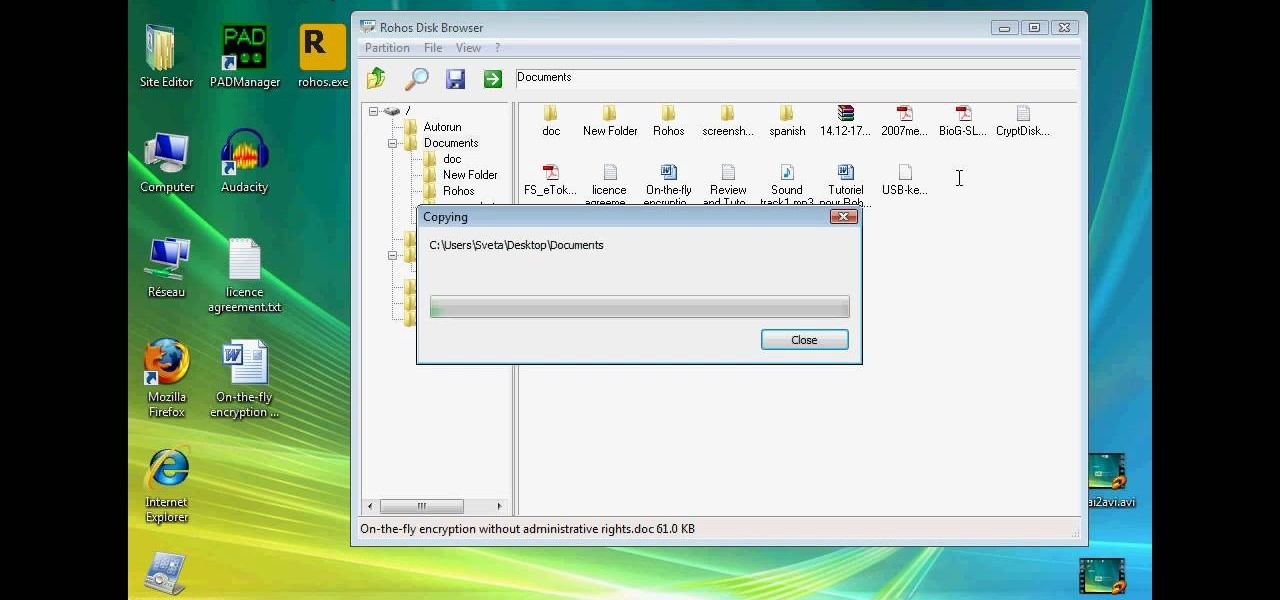
This technical video will show you all about the Rohos Mini Drive. See how you may work with an encrypted partition on a PC without admin rights using this free portable encryption solution. It securely protects your portable data on any USB device. Portable utility Rohos Disk Browser gives you opportunity to work with your sensitive data on a USB drive in the usual way on any PC (even at an internet cafe, where you don’t have admin rights).
The CEC, Canada Experience Class, is a new program to help a person who has held residency in Canada gain permanent residency status. The program realizes that, by going to school or living in Canada while working, many people have the skills necessary to make the transition to live in Canada permanently. To qualify for CEC, you must be a temporary worker living in Canada for at least two years with two years of skilled working experience. A second way you can qualify is by being a foreign gr...

New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to install the latest Wine on Ubuntu Linux.
A CNC router machine is probably the most useful tool a hobbyist can own, but the price for a CNC machine on the market is way more than the average hobbyist is willing to spend. You can build your own CNC with very basic tools, little knowledge of machinery, mechanics, or electronics, but be warned, these machines are inherently dangerous, so wear the proper protection and use common sense. At the very least, read the instructions and precautions on every tool you use.

It's always a good idea to know how an attack works at the very basic level. Manual techniques for exploitation often find holes that even the most sophisticated tool cannot. Sometimes, though, using one of these tools can make things so much easier, especially if one has a solid foundation of how it works. One such tool can help us perform a cross-site request forgery with minimal difficulty.

Web 2.0 technology has provided a convenient way to post videos online, keep up with old friends on social media, and even bank from the comfort of your web browser. But when applications are poorly designed or incorrectly configured, certain flaws can be exploited. One such flaw, known as CSRF, allows an attacker to use a legitimate user's session to execute unauthorized requests to the server.

Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input is not properly sanitized, commands not originally intended to be run are allowed to be executed.

Another piece of Magic Leap's mysterious story has been uncovered thanks to a new patent application revealed on Thursday, March 15.
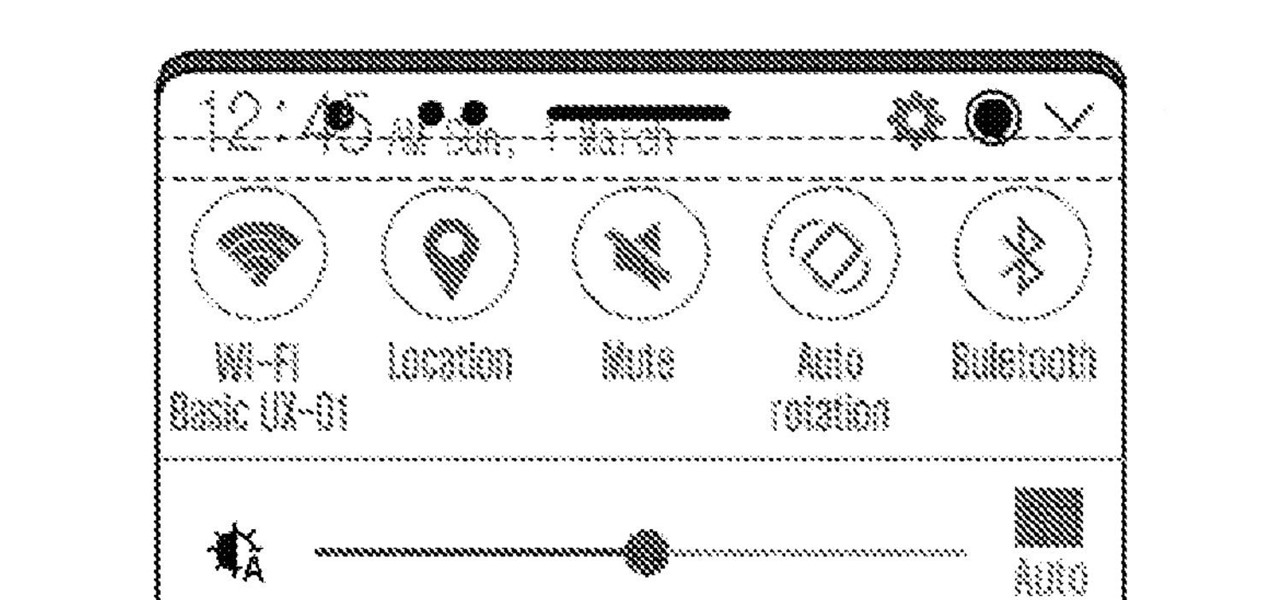
While 2017 saw the rise of "bezel-less" smartphones, none truly lived up to the name. Samsung shrank its bezels significantly, while Apple went with the infamous "notch." However, Samsung seems on the verge of kicking bezels out the door with a new patent application that embeds the front camera into the display.

This is one of the coolest applications of Apple's ARKit that we've seen so far. The 3D software product studio gradientspace has created a Minecraft 3D scanner using ARKit.

Augmented and mixed reality developer Arvizio is working on a suite of software solutions for enterprises that will extend HoloLens capabilities as a full-fledged collaboration and conferencing tool. The company will demonstrate its Mixed Reality Studio suite to attendees at the Augmented World Expo, which begins later this month in Santa Clara, California.
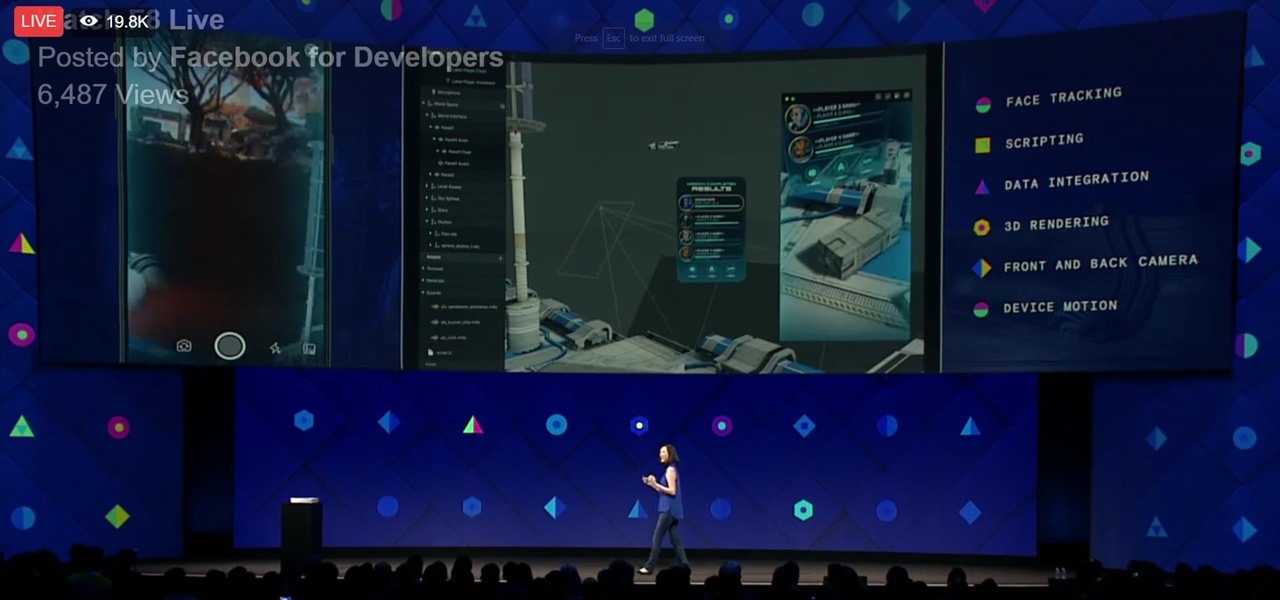
During his opening address on April 18 at F8, Facebook's developer conference, CEO Mark Zuckerberg launched the company's augmented reality platform centered on artificial intelligence-powered cameras.

Asobo Studios, one of the first companies to partner with Microsoft on HoloLens development, is applying their expertise towards building applications for various business verticals through their internal HoloForge Interactive team.

LOOOK, a Seattle-based mixed reality and development studio, can now peer into the future with their new geotechnical engineering visualization application for Microsoft HoloLens.