Hacker Defender is one of the most widely deployed rootkits in the world. It is a user-mode rootkit that modifies several Windows and Native API functions, which allows it to hide information (files, processes, etc.) from other applications. In addition, Hacker Defender implements a backdoor and port redirector that operates through TCP ports opened by existing services. This means it is not possible to find the hidden backdoor through traditional means, like launching a remote port scan agai...
Mike Lively of Northern Kentucky University demonstrates how to create a 3D plotting program for the sinc math function. Part 1 shows how to convert a Flash Package into a Flex application. Part 2 shows how to get the sinc function running and add different textures. Create a cool interactive 3D plotter in thie Adobe Flex Builder 3 and Papervision3D tutorial.

A PDF file is a great way to share your documents with anyone. Both Macs and PCs can read them and it's very easy to create them in Mac OS X. From any application that you can print from, go to File–Print–which will open up the print dialogue box–and find the PDF button in the lower left corner. To learn more, and for a complete walkthrough of printing to PDF in Mac OS X (as well as information on using the handy Web Receipts) feature, watch this video tutorial.

Pop/R&B singer Ashanti is the basis of this pretty silver and grey eye look. This how-to video demonstrates how to replicate this look that will really define your eyes. The cosmetic products used to create this look are Studio Fix Fluid Foundation, Makeup Forever HD Powder, Mineralize Skinfinish Duo in “Medium Dark,” Mineralize Blush in “Pleasantry,” Cream Color Base in “Pearl,” Painterly Paintpot, Platinum Pigment, Concrete e/s, Kid e/s, Brule e/s, White Frost e/s, Blacktrack Fluidline, Lor...

Just a few years ago, Britney Spears was considered hot. Regardless of what you think of her now, this how-to video recaptures her glory days via makeup. The cosmetic products used to create this look are MAC Studio Fix Fluid mixed with Covergirl Trublend, Bare Escentuals Foundation, NARS Laguna Bronzer, MAC Warm Soul Blush, MAC Cream Color Base in “Pearl,” MAC Blackground Paintpot, 88 Shimmer Palette from Coastal Scents, MAC Black Tied e/s, MAC Blacktrack Fluidline, Urban Decay 24/7 Eyeliner...

Three point lighting is the standard used to illuminate a subject for amateur film, video, and even theater application.

For a decade, Microsoft Azure has been transforming businesses across the globe. The cloud-computing service is leading the way in software as a service (SaaS), platform as a service (Paas), and infrastructure as a service (IaaS) protocols.

Choosing which programming language to learn next can seem like a nearly impossible task, regardless of whether you're a novice developer or a seasoned coding pro with years of experience creating apps and websites. But if you haven't already learned Python, look no further.

Adobe sets the standard for graphic design. Since launching its subscription-based Creative Cloud in 2011, Adobe has consistently updated its suite of applications to serve the needs of the modern designer.

This week's Apple earnings offered a report of solid performance and guarded optimism about future iPhone sales, which may be impacted later this year by issues around the current coronavirus epidemic in China.

After drawing attention from nostalgic Gen Xers for its Motorola Razr reboot with a foldable screen, Lenovo has a new augmented reality smartglasses concept that the company hopes will also turn some heads.

After North cut the base price of its Focals smartglasses, Vuzix is now testing the waters of a lower price point for its Blade smartglasses.

Cross-site scripting is one of the most common vulnerabilities found on the web today, with repercussions of this type of flaw ranging from harmless defacement to sensitive data exposure. Probing for XSS can be tedious and time-consuming for an attacker, but luckily there are tools available to make things a little easier, including Burp Suite, Wfuzz, and XSStrike.

Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.

Unlike on Android, you can't easily hide your iPhone apps. Sure, you can nestle them away in folders labeled "junk," but they're supposed to be omni-present somewhere on your home screen. That is, until one day they're just ... gone. The fact that some of your apps disappeared only makes it more frustrating because there's no logical reason why they should have, right?

Why would Magic Leap, a company preparing to launch its first augmented reality headset this year, need a developer for iPhone and iPad apps? It's not as crazy as it sounds.

Magic Leap's recent flurry of patent applications prompted us to look around for any trademark movements from the company, and it turns out that the Florida-based company has been quite busy.

Location services provider Mapbox is giving developers a means for building location-based AR apps and multi-user experiences with its new Mapbox AR toolkit.

Multitasking on a smartphone has never been better, but it still has some ways to go to compete with a desktop experience. Samsung hopes to change that with a new multitasking view on the Galaxy S9, which allows the user to open notifications in a new, smaller window on top of the app they are currently using.

Augmented reality developers are rapidly bringing science fiction tropes into the real world, with the latest example leveraging the TrueDepth camera on the iPhone X to emulate the cloaking technology made famous by movies like Predator and Marvel's The Avengers.

Do you know when you're going to die? Your iPhone or iPad does. That's the premise behind Death Mask, an experimental app developed by Or Fleisher and Anastasis Germanidis.

So after being teased last Christmas with an email promising that the Meta 2 was shipping, nearly a year later, we finally have one of the units that we ordered. Without a moment's hesitation, I tore the package open, set the device up, and started working with it.

With the V30, LG has really delivered an amazing smartphone that hits all the major features consumers want. Amazing camera, beautiful edge-to-edge display, great battery life, water resistance, and smooth performance — there isn't much not to like about the LG V30. Unfortunately, it does suffer from heavy bloatware thanks to the carriers. The good thing is, unlike in the past, you are not stuck with it.

After exploiting a vulnerable target, scooping up a victim's credentials is a high priority for hackers, since most people reuse passwords. Those credentials can get hackers deeper into a network or other accounts, but digging through the system by hand to find them is difficult. A missed stored password could mean missing a big opportunity. But the process can largely be automated with LaZagne.

When Apple announced their ARKit platform in June, they immediately staked the claim to the largest augmented reality hardware platform, with millions of iPhones and iPads compatible with iOS 11 becoming AR devices this fall.

While IKEA is collaborating with Apple for its ARKit furniture app, Marxent is ready to help the rest of the interior decorating and home improvement crowd with their apps.

Data for mapping and other applications is the lifeblood of machine-driven cars, and so far, Tesla has taken a definitive lead in information it has gathered ahead of other driverless players, including Waymo.

Screen mirroring app iDisplay has arrived for Vuzix M300 Smart Glasses. With the app installed on the M300 and the companion software running on a Mac or Windows computer, users can mirror or extend the computer's desktop to the headset's display, which is connected to the computer via Wi-Fi or USB cable. The app does not yet appear on Vuzix's app store.

Lenovo has partnered with Wikitude to develop a cloud-based platform for delivering industrial-focused augmented reality content, the companies announced at the Augmented World Expo today in Santa Clara, California.

Sometimes it's impossible to concentrate — let alone direct your personal assistant Siri — when someone is blasting music on their phone or talking to thin air. I mean I'm loud, but not that loud.

Now, you can prevent Donald Trump from building that idiotic wall from the comfort of your smartphone. Well, in theory, you can, thanks to a hilarious new gaming app called — wait for it — Trump's Great Wall.

Apple made headlines last month when it announced it would acquire the popular application Workflow. Now, the company should be making waves again with the news that they will reimburse customers who purchased the app.

With a predicated increase in the number of Lyme disease cases in the coming spring season, new research endorses the use of bait boxes to control ticks on the rodents that serve as their hosts.

A market research report, posted on February 27, 2017, forecasts that the image recognition market will grow to nearly $40 billion worldwide by 2021. The market, which includes augmented reality applications, hardware, and technology, generated an estimated $15.95 billion in 2016. The report estimates the market to grow by a compound annual growth rate of 19.5% over the next five years.

This year's Game Developers Conference, better known as the GDC, is underway at the Moscone Center in San Fransisco, California, and lasts until March 3, 2017. More importantly for us here at NextReality, the Virtual Reality Developers Conference (VRDC)—a new GDC sub-conference geared toward augmented, mixed, and virtual reality—has begun.

We've already seen plenty of shopping potential for mixed reality headsets, from holographic car showrooms to trying on clothes and picking out furniture. Very few of those ideas have been put into actual practice, but we're getting closer, and consulting firm Valorem is making headway. They created HoloTire for the Microsoft HoloLens to demonstrate the advantage of experiencing a product in mixed reality. I'm hard-pressed to think of a more boring product to put on a holographic pedestal tha...

You've likely seen some impressive art carved out of a bush or tree before that looked like it required a lot of work and skill to create. While that may have been the case in the past, software engineer Javier Davalos used the Microsoft HoloLens to turn a bush into a perfect topiarian sphere with no training whatsoever.

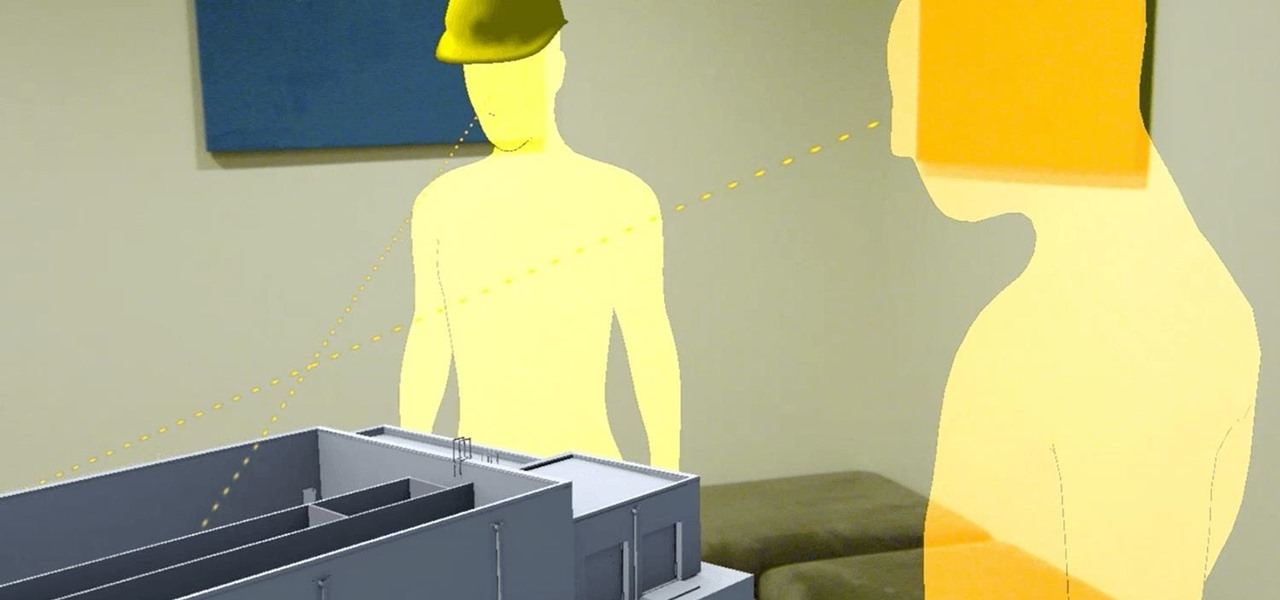
With developers already figuring out how to use the HoloLens for home improvement tasks, it's no surprise that the device has greater applications in construction. Tech blog Digital Trends points out that holograms are a natural evolution of the blueprint, and several other aspects of construction work.

Augmented reality has a variety of applications, but lately the face has been a major point of concentration for many companies. We're all pretty familiar with face swapping by now, but ModiFace employs similar technologies for more practical purposes.

Welcome back, my tenderfoot hackers! As you should know from before, Snort is the most widely deployed intrusion detection system (IDS) in the world, and every hacker and IT security professional should be familiar with it. Hackers need to understand it for evasion, and IT security professionals to prevent intrusions. So a basic understanding of this ubiquitous IDS is crucial.