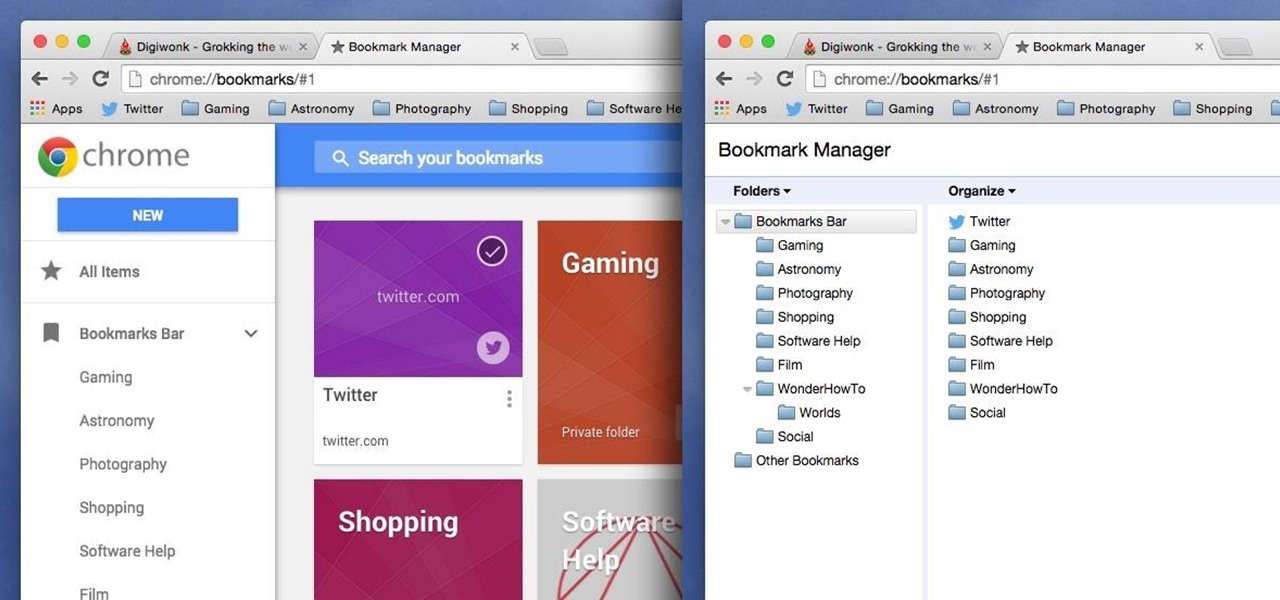
Chrome has been pushing out a lot of new changes lately, but not all of them are as good as they think they are. Earlier this year, there was an update that changed how user profiles worked, which made it harder to actually switch profiles. Luckily, there was a way to get back the old profile management interface, but now there's another "improvement" that you might want to change—Chrome's new Bookmarks Manager interface.
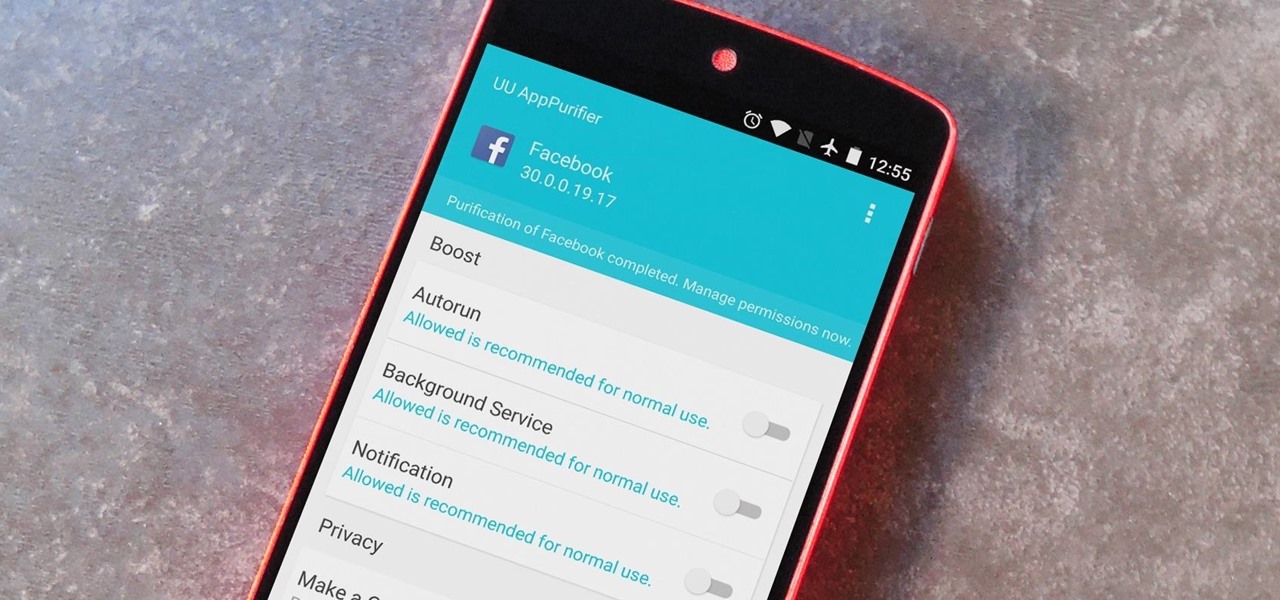
When it comes to app permissions, Android takes an "all or nothing" approach. You have no granular control over what data apps can access, so the only way to prevent an app from seeing your location or starting up on boot, for instance, is to not install the app in the first place.

Today, I want to share a tutorial on one of the most useful but old methods which you could use to hack websites, that is using the Dot net nuke (DNN) vulnerability . I know some of you already know about this method.

Are you a follower or a leader? No matter how you respond, we all know that leader is a more desirable position to hold. Great leaders typically share a few qualities—confidence, intelligence, and strength, to name a few—but one of the most intriguing is their appearance. With the right facial structure, and some well-rehearsed expressions, you can trick others into thinking you're leader material.

The importance of body language is stressed from an early age: watch those around you, and you'll know what they're thinking. While you might be skilled at deciphering the messages of crossed arms, slouched sitting, eye movements, and hand gestures, the key to understanding those around you is a little less obvious.

iCloud Drive is Apple's new solution to file management syncing across iOS and Mac OS X. If you've upgraded to iOS 8 and you have an iCloud account, you can use iCloud Drive to store files for certain apps. While you won't really be able to benefit with file syncing between iOS and Mac apps until you get Yosemite, you can still access your iCloud Drive documents online.

In 2012, VideoLan published a beta release of their wildly popular desktop media player, VLC, for the Android platform. However, because the non-profit development team did not have access to popular North American Android devices, they opted to exclude the USA and Canada from their initial release. That is, until now.

If you keep sensitive data on your phone, you've surely considered a "lockout" app before. There are many such apps that can add an extra layer of security to other apps within Android. For instance, you can require a PIN or password before anyone is able to launch a particular app.

Imagine that you're the last person alive. After losing all of your loved ones, you thought you'd never see another human being in your life. Then, they arrive. The hoard of 15-year-old zombies looking for a cute British YouTuber so they may feast on his brains.

Multitasking has traditionally been one of Android's strengths. As the first mobile operating system to introduce true multi-process management, it even took things a step further after version 4.0 by dedicating a button to your recently-used apps.

Welcome back, my greenhorn hackers! Lately, much of the discussion here on Null Byte has revolved around evading detection and not getting caught hacking. Several of you have written me asking for a series on evading detection and forensics, and while I began a series 5 months ago on just that, we have changed hacking platforms from BackTrack to Kali, which has a much more highly developed forensic toolset.

Amongst the trove of high-end features on the Galaxy S5, the display may be the most impressive. Sporting a 5.1-inch Full HD Super AMOLED (Samsung's version of OLED) display with 1920 x 1080 resolution and 432 pixels per inch, Samsung's flagship has one of the best smartphone screens currently on the market.

Team Win Recovery Project (TWRP) is a custom recovery for Android devices and the one used by most softModders, mainly because it has touch-based actions, as compared to the more time-consuming button-based approach that ClockworkMod (CWM) uses.

It can be a pretty exasperating ordeal to hunt for one image on your tablet when you have hundreds and hundreds of photos in your gallery. Luckily, there are ways to make this a pain-free process on your Nexus 7, as well as make sure it's never a problem in the future.

As far as lock screens go, your Samsung Galaxy S4 and other Android phones offer quite a few options. You can use the classic PIN unlock, the novelty facial recognition, or the reliable pattern lock. But what if you get tired of entering the same old PIN or pattern every day?

Welcome back, my neophyte hackers! In today's hack, we're going to have a bit of Halloween fun. Have you ever had a boss who made you miserable with his micro-management and nagging? Maybe you thought he unfairly fired your friend/colleague? Well, now here's your chance to get a bit of revenge and keep him or her off your back!

A man once told me to never complain about gas prices. With the average price of regular unleaded gas at $3.34 a gallon, it's hard not to, even if it is the holiday season. Since my car averages about 22 mpg, the man offered me this proposition: "If I offered you $3.34, would you walk 22 miles?"

Of all the places you'd think to check for bed bugs, I doubt that library books would be at the top of your list. As odd as it sounds, though, libraries and library books are some of the most common places for bed bug infestations. Libraries all over the country have reported bed bug problems this summer, and some have even had to temporarily close to take care of the problem. But before you vow to never set foot inside a library again, here's a little primer on how to check your books for be...

When you enable Low Power Mode on your iPhone, it's not always clear what measures it's taking to reduce battery drain and conserve power. Changes to energy-hungry features you use daily may be immediately noticeable, but some things you frequently use may be disabled or reduced without any apparent indicators.

Microsoft Excel is one of the most useful tools you can bring into your professional life. However, as useful as Excel is, it can also be difficult to learn on your own. The All-In-One Microsoft Excel Certification Training Bundle is an incredible tool that will take you from Excel beginner to Master for $33.99, on sale for 98% off.

Whether you work in sales or want to become more persuasive and better at selling yourself, the art of selling can be transferred to nearly any career path or walk of life. Whether the gains are monetary or interpersonal, being a great salesperson is one of the most invaluable skills you can ever learn.

Have you ever admired those individuals that get so much accomplished in a day and wonder how the heck they do it? Now's your chance to learn their secrets. The Productivity & Motivation Master Class Bundle brings you everything you need to life-hack your way into leading a more productive lifestyle at home and work.

Amazon Web Services (AWS) offers over 200 services, including networking, computing, storage, analytics, blockchain, mobile, and developer tools. Not surprisingly, numerous companies rely on AWS's massive infrastructure. Instead of building their own server farms, they rent space and computing power from AWS's secure and robust system.

It's a common and unfortunate myth that you need to work in web or app development if you have a knack for coding and design. In fact, more and more development pros are entering the exciting and increasingly lucrative world of game design, thanks to a growing demand for strategy games that can be played on multiple platforms.

In the not-so-distant past, cloud computing was thought of primarily in terms of online storage platforms. Now, however, massive cloud infrastructures are used by virtually every major business to reach clients, manage data, and deliver services.

The career prospects for talented and trained IT professionals are nearly endless. As the world becomes more interconnected by the day, companies of all sizes are looking for people who can install, maintain, and troubleshoot a wide variety of networking infrastructures and web-based platforms.

The built-in Files app on your iPhone has only gotten better since it was introduced in iOS 11, with small improvements after each new iOS version. You can manage files on your internal storage as well as in iCloud Drive, but one of the best features is being able to manage media and documents from all of your cloud storage accounts in one place.

Web applications are a prime target for hackers, but sometimes it's not just the web apps themselves that are vulnerable. Web management interfaces should be scrutinized just as hard as the apps they manage, especially when they contain some sort of upload functionality. By exploiting a vulnerability in Apache Tomcat, a hacker can upload a backdoor and get a shell.

While consumer-grade smartglasses are the holy grail for tech companies, smartglasses maker Vuzix knows where its bread is buttered, and that's in the enterprise segment.

No operating system is stricken with as many vulnerabilities as Windows, and it's often a race to release the latest patches to fix things. From an attacker's point of view, knowing which patches are present on a Windows machine can make or break successful exploitation. Today, we will be covering three methods of patch enumeration, using Metasploit, WMIC, and Windows Exploit Suggester.

Investment in augmented reality remained robust in 2019. For the third consecutive year, we looked back on the biggest funding deals in the AR industry this week, and a familiar name came out on top.

The week in AR business news started out with a bang with two bombshell reports that cast a shadow on the AR industry as a whole.

Correctly identifying the underlying technologies that run on a website gives pentesters a considerable advantage when preparing an attack. Whether you're testing out the defenses of a large corporation or playing the latest CTF, figuring out what technologies a site uses is a crucial pen-tester skill.

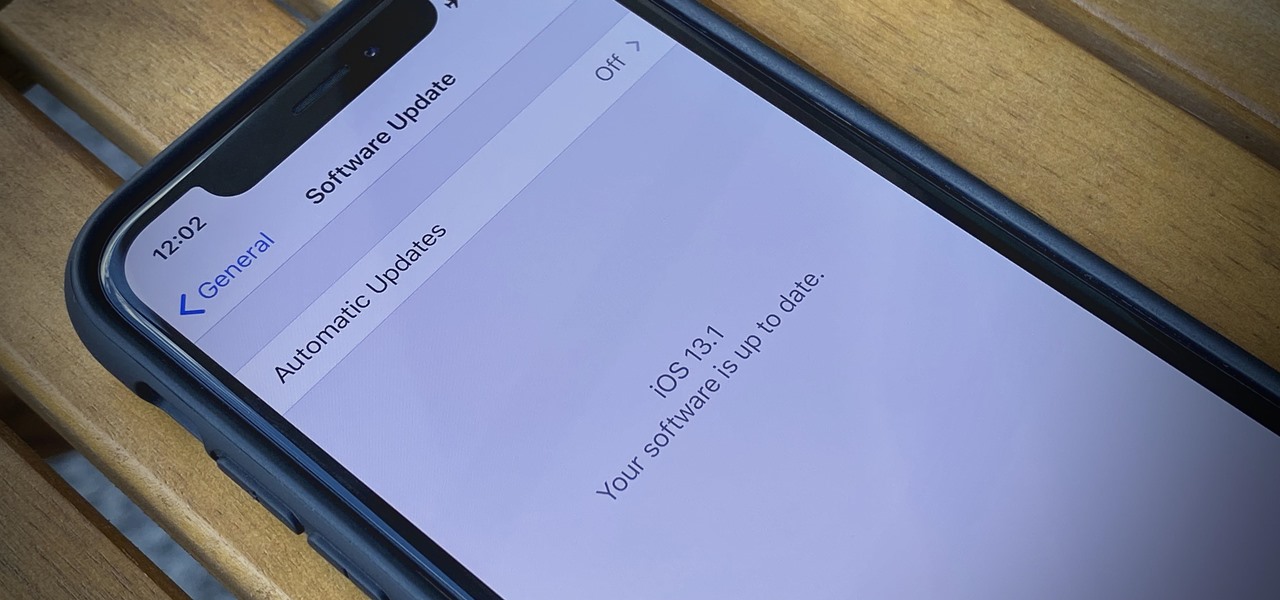
If you're still working your way through the hundreds of features and changes that iOS 13 brings to your iPhone, you might be a bit surprised to learn that your device is now out of date. While Apple only dropped the big update for iPhones on Thursday, Sept. 19, the company has already released its successor. All iOS 13-compatible iPhones can now update to iOS 13.1, out today, Tuesday, Sept. 24.

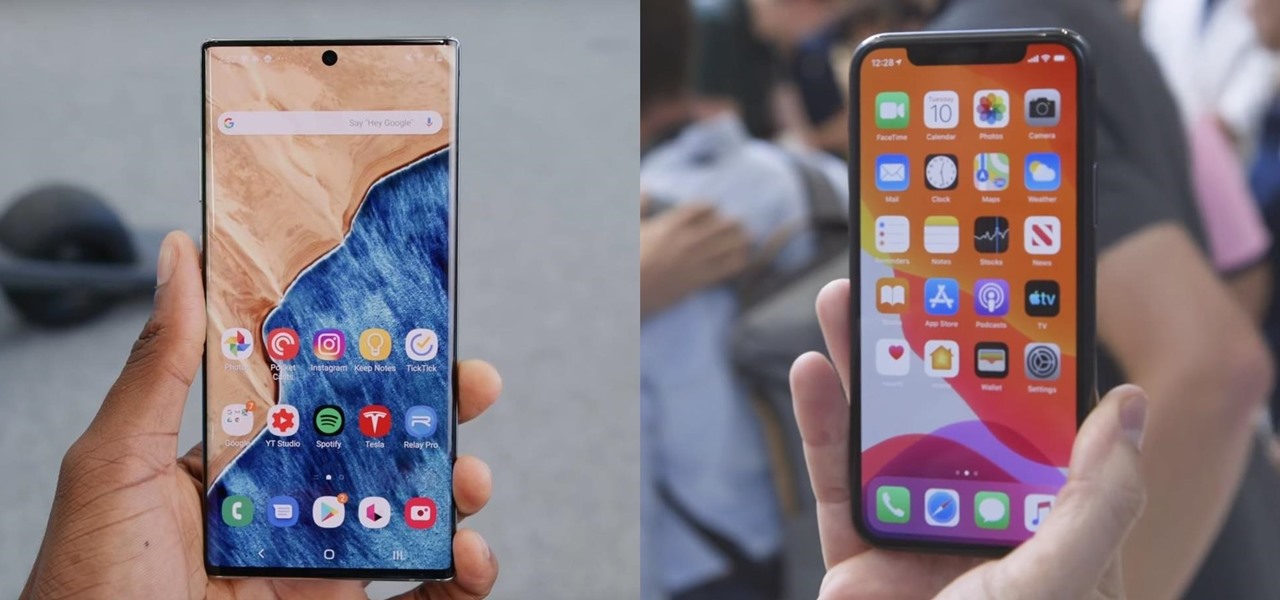
Samsung decided to shake things up this year. In the past, the Galaxy Note series was one large phone. This year, it's two phones: the Galaxy Note 10 and Note 10+. So for the first time in a long time, we can compare the latest standard iPhone, the 11 Pro, to a Galaxy Note device.

Some of the Pixel 3's coolest features are software related, which means you can get many of them on non-Pixel devices. "Flip to Shhh" is a perfect example of this. It lets you quickly put your phone into do not disturb mode by placing it face down, and this can be replicated on other Android phones with the help of a simple app.

The hype around augmented reality has risen to a fever pitch over the past two years, and if this week's selection of business news stories are any indication, the din is about to get down right deafening.

This week, the recurring theme in augmented reality can be summed up fairly succinctly: content is king.

Unless you're completely new to Instagram, it's likely that you've linked your account with a third-party service at some point and forgotten about it. Those services still have access to data such as your media and profile information, so it's important that you not only know how to find these "authorized" apps, but that you know how to revoke their permissions.

Hundreds of Windows 10, macOS, and Linux vulnerabilities are disclosed every single week, many of which elude mainstream attention. Most users aren't even aware that newly found exploits and vulnerabilities exist, nor that CVEs can be located by anyone in just a few clicks from a selection of websites online.