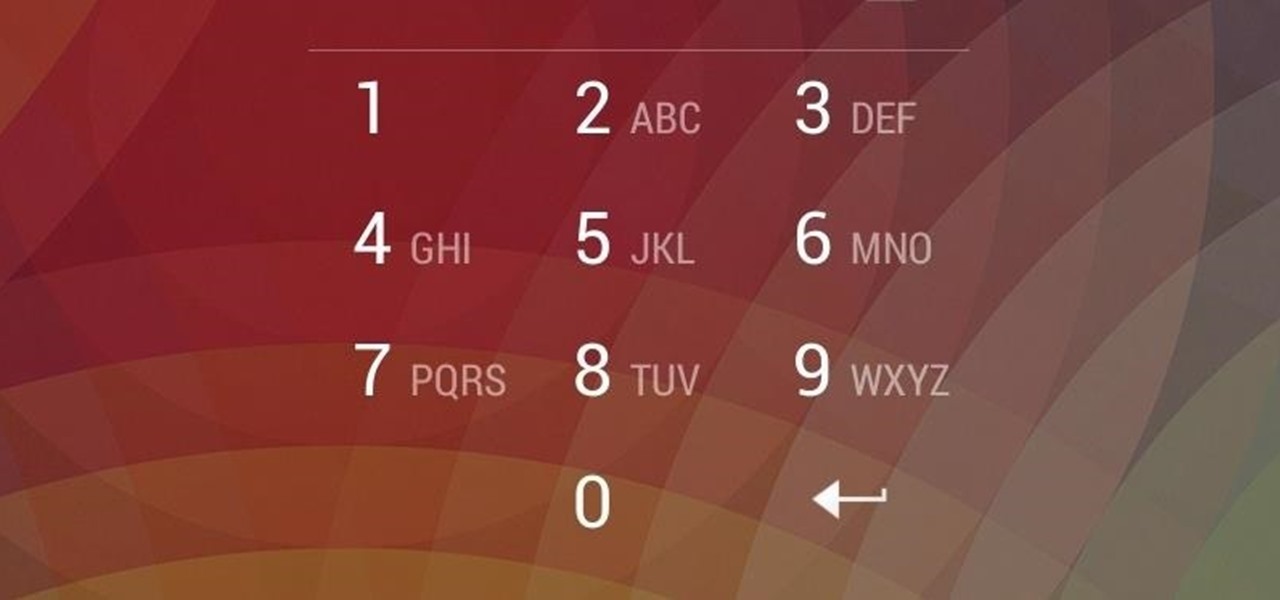
It happens to everyone: you set a lock screen password in a hurry and cannot remember it the next day. To unlock your device again, you need to reset the password (or PIN, pattern, etc). There are two official methods of doing this.

There wasn't really anything too special about the S Pen on the Samsung Galaxy Note 2, with its limited capabilities and finicky sensitivity. Luckily, the S Pen was greatly improved on the Note 3, the biggest enhancement being Air Command, a floating menu that appears when the S Pen is removed that gives quick access to all the new features.

We have shown you how to get CyanogenMod on your HTC One and Samsung Galaxy S3 in only a matter of minutes. But when modding your phone by installing custom ROMs, you'll often lose your access to Google Apps. Since Google's Apps are very useful (Gmail, Chrome, and Maps to name a few) most people will prefer to have these apps on their custom ROMs. While you can scour the internet searching for individual .APKs, it's hard to find the correct versions to work with your particular system (and do...

No offense to T-Mobile, but if you head over to their support page for the Samsung Galaxy Gear, you get the information below on how to take a screenshot of your smartwatch. Oh, thank you for that.

In a previous softModder guide, I detailed how to get the Jelly Bean 4.2 Photo Sphere Camera and Gallery on your HTC One running Sense 5, but that was quickly outdated with the release of the new Google Play Edition HTC One, which has a newer Camera that works great with our hardware.
Programs that run automatically every time you start your computer can slow down your boot time—or just be plain annoying. Many of these programs are rarely used and don't even need to be running for your computer to function properly. So, if you want to disable these auto-run programs and increase your computer's startup speed, here are a few ways you can do it in the new Windows 8.

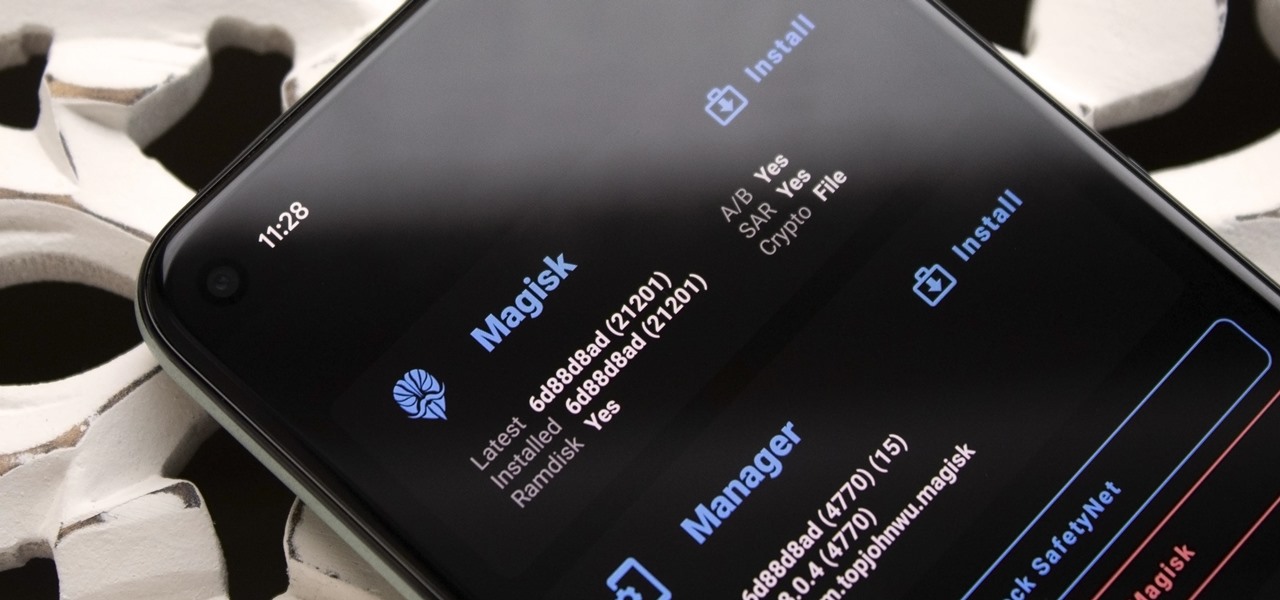
Okay, so you rooted your Android phone .... now what? There are a few ducks you need to get into a row, like backing up your stock boot image, getting SafetyNet sorted, and improving security with biometrics. But there are also awesome root mods waiting for you — just don't get ahead of yourself.

On Android, there is a vulnerability that Google doesn't seem to want to fix — anyone can open the Quick Settings panel on your lock screen. GPS, Wi-Fi, and Bluetooth, all toggles accessible in this menu, are vital tools for locating your phone in case it is ever stolen. But thanks to Xposed, you can eliminate this potential risk.

The Windows 10 desktop and microphone can be livestreamed without using Remote Desktop Protocol (RDP) software and without opening any ports on the target computer. A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in real time no matter where they are. Hackers are watching and listening, and there are few ways to protect yourself.

The Watch Dogs video game series came out in 2014, enamoring audiences with the idea of a seemingly magical smartphone that could change traffic signals, hack web cameras, and even remotely control forklifts. This may sound like science fiction, but The Sonic uses a customized flavor of Kali Linux to allow you to unleash the power of Kali from any smartphone — all without the need to create a hotspot to control it.

A new technological movement without the technology itself is just an idea sitting and waiting. Once the technology is present in the equation, movement forward can begin. This is how many of us see the head-mounted displays (HMDs) and smartglasses that have recently entered the augmented and mixed reality market — or are coming out in the next few months. This is a movement that will sweep over the world, changing everything in its path, and these are some of the people behind it.

So you finally decided to make the switch from iOS to Android, huh? Well first off: welcome to the world of tomorrow. And secondly: good call, mate.

This time it's serious. Really. The largest web security vulnerability of all time went public on Monday, April 7th, 2014, resulting in widespread panic throughout the Internet as system administrators scrambled to secure their websites from the OpenSSL bug known as Heartbleed.

Switching phones has never been easier. Google backs up most of your app data on the cloud, which can then be restored onto your new phone. Sadly, Signal doesn't use this feature since it could compromise your security. Instead, Signal stores encrypted backups locally, requiring a bit of work to restore these messages.

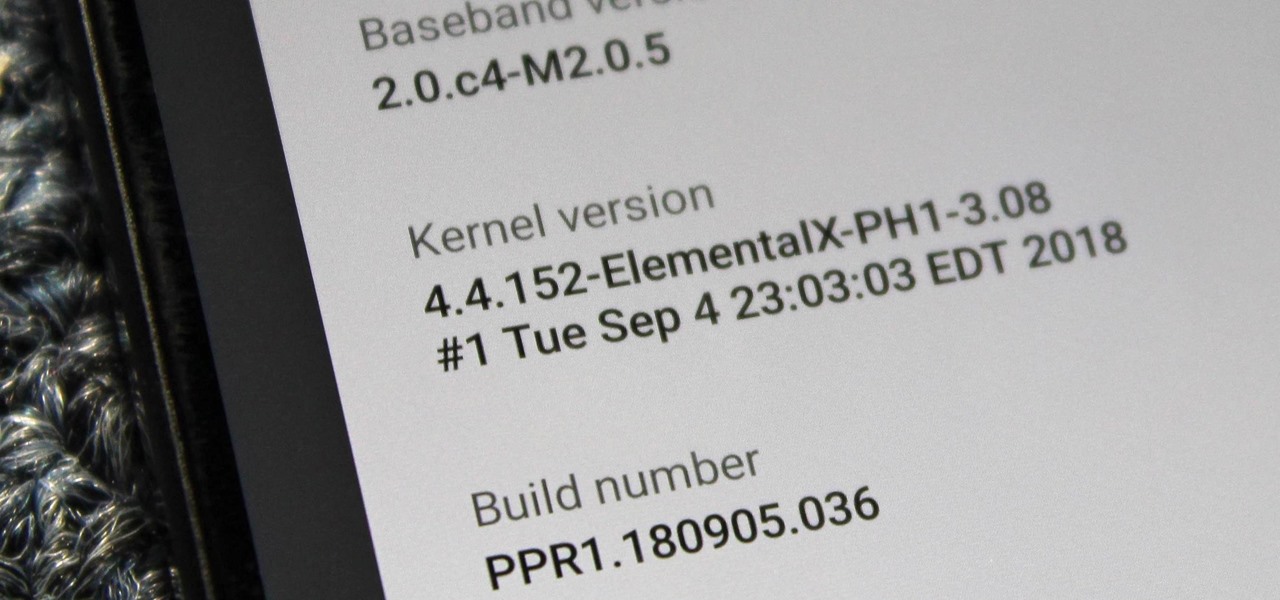
When you unlock the bootloader on your Essential PH-1, you open your device to a host of new possible tweaks. One popular modification is a custom kernel, which can not only speed up your phone, but give you new features that wouldn't be possible otherwise.

If there's one strength of Apple's that iOS and Android fans can agree on, it's the company's dedication to user privacy. With each new iteration of iOS, Apple builds upon these foundations, enhancing and increasing each iPhone's ability to protect its user's data. In iOS 12, Apple has added many new features to Safari, most of which have their own unique way of keeping you safe online.

When building anything of a social nature, be it a local roller derby or softball team, a club dance night for chiptune, or building new technology markets, the community around those ideas are an important factor in helping these things not only come into existence but to grow into something that enlightens everyone involved. The community around an idea can actually make or break these new ventures — and this applies to augmented and mixed reality as well.

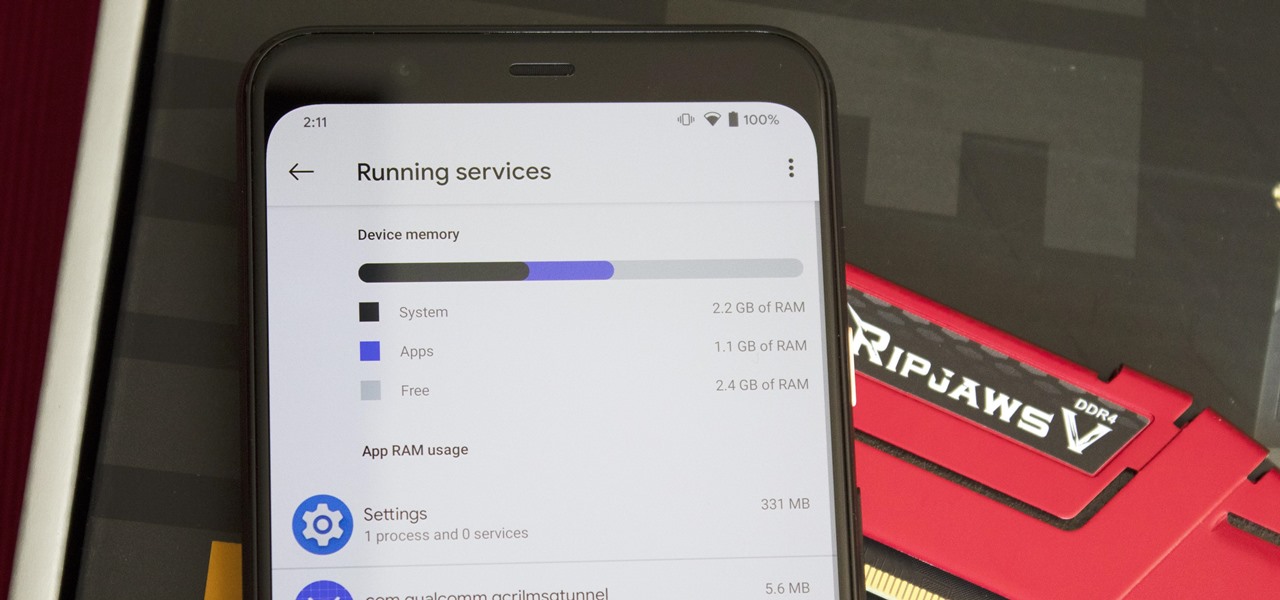
Not every app is designed well. With nearly 3 million apps on the Play Store and countless more that you can sideload from other sources, there are bound to be a few stinkers. And many of them do a terrible job using RAM.

OnePlus is known for making a quality products with their line of smartphones, but as with most, they have their own specific customizations that you can't get anywhere else. Font types, boot animations, sounds, and proprietary apps — they are all unique to each different skin of Android. The good news, though? There's an effortless way you can grab some of that OxygenOS goodness right now.

Well before Magisk was in our lives, the Xposed framework was where all the mods and magic happened. Magisk was built on a similar concept with the ability to customize your system via modules. We can thank Xposed for where we are today in terms of root-related mods, but it's not done just yet — it's still very much alive and kicking after all these years.

Rooting. As an Android user, I'm sure you've heard the word once or twice. According to Kaspersky, 7.6% of all Android users root — but for the 92.4% who don't, we wanted to talk to you.

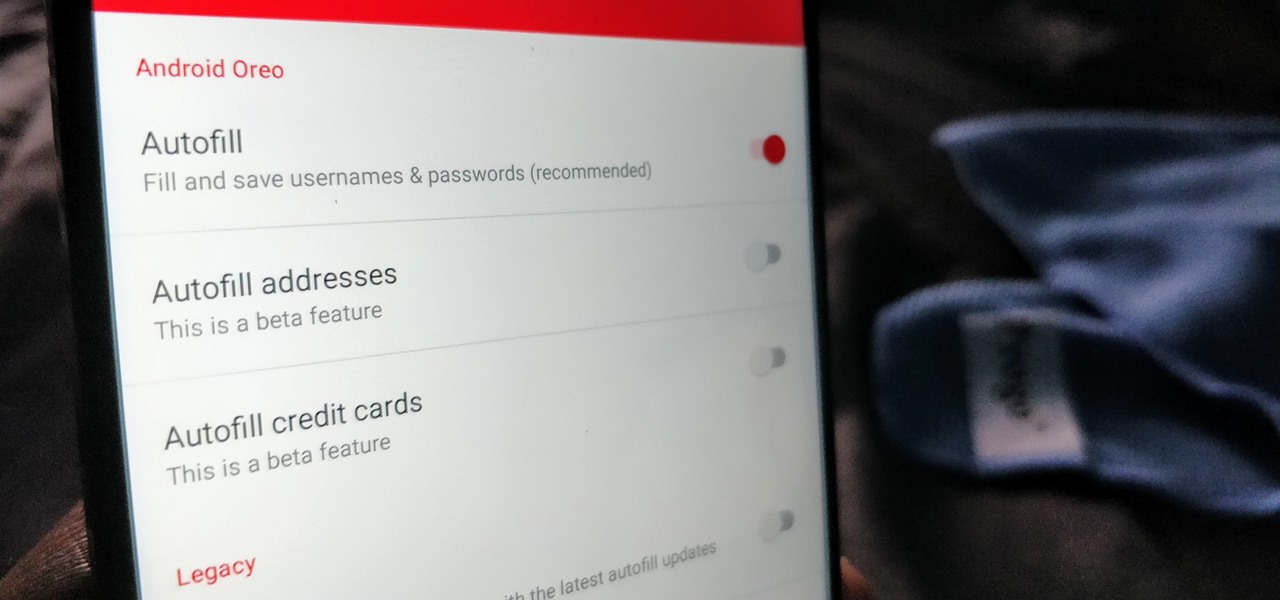
One of the more exciting features in Android Oreo is the Autofill API. With this tool, third-party password managers can autofill login information into other apps. LastPass added this feature to their beta app a while back, but now, Autofill is finally available in the official stable version of LastPass.

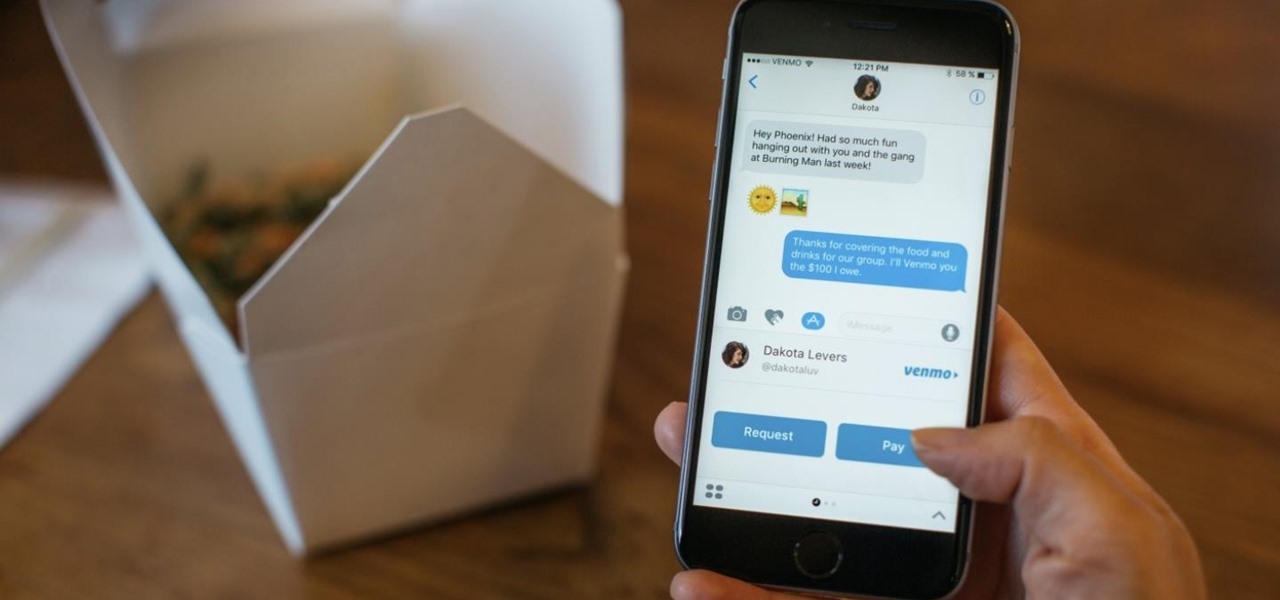
For $0.25 per transaction, PayPal will soon be allowing you to transfer money through their app that will get delivered within seconds rather than days.

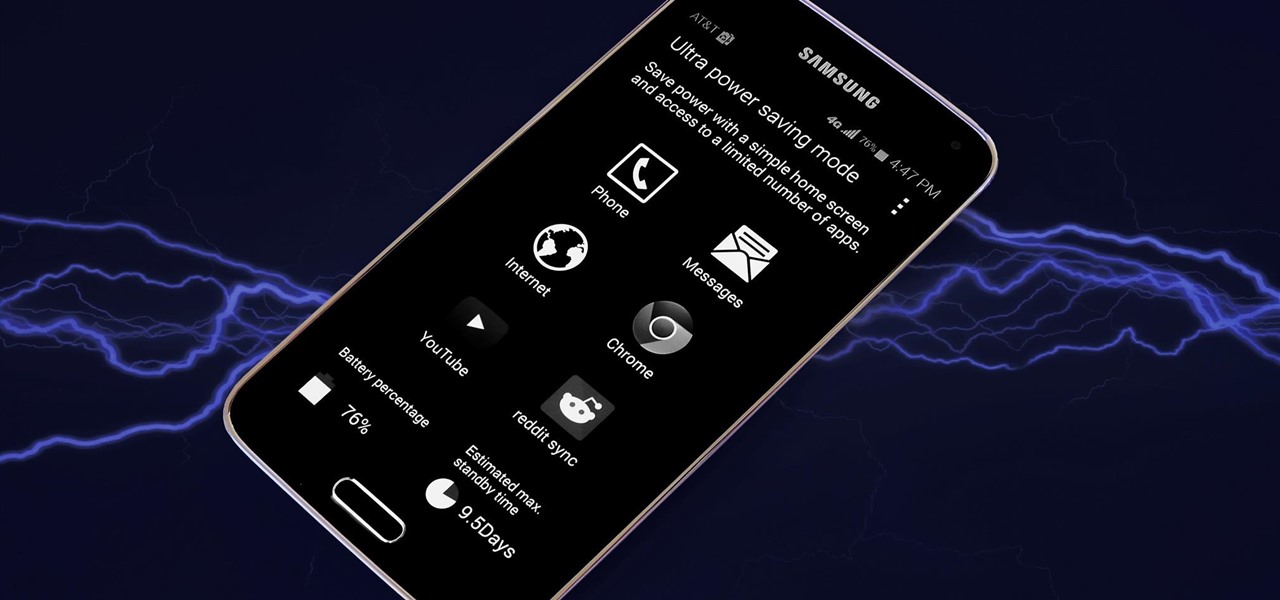
The Galaxy S5 comes with an awesome feature for those times when you're running low on battery life with no charger in sight. Ultra Power-Saving Mode allows you to cut back on non-vital services and convert your phone's display into a juice-saving grayscale mode to greatly extend that last bit of charge.

A few days ago I finally finished my 2 week journey into trying to get OpenVas to work properly. You all may have noticed that you can't just click the setup openvas in kali and have it working properly.

Samsung's exclusive music streaming service, Milk Music, has been making waves across the web thanks to its peculiar name and ad-free stations.

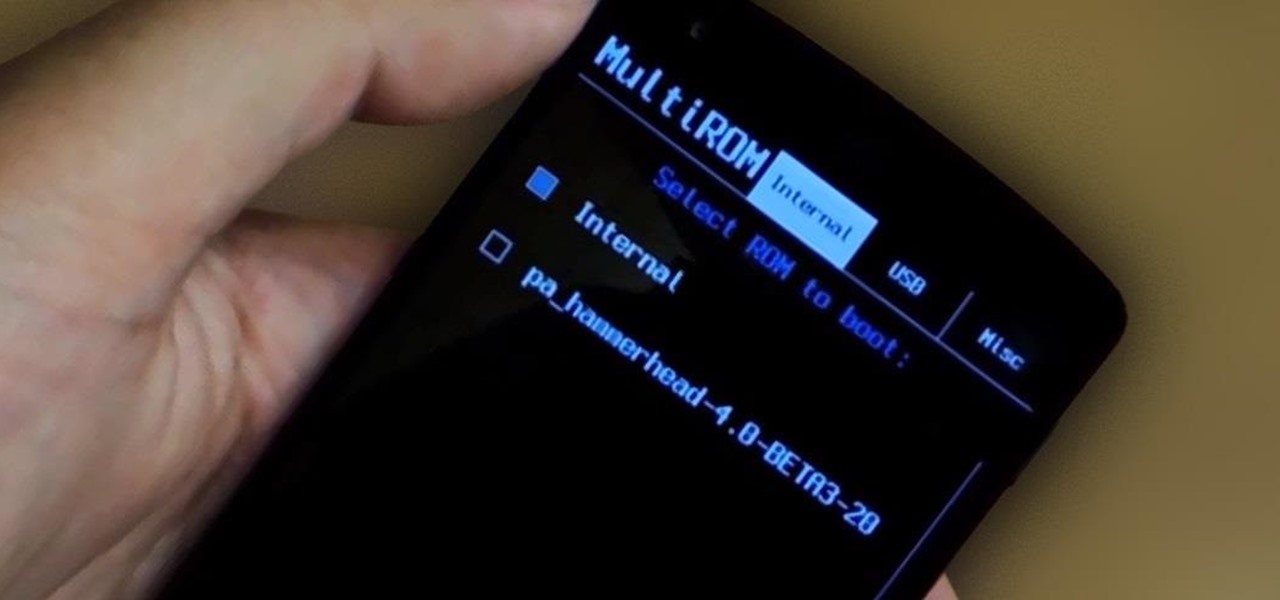
When you enter the softModder realm by rooting your Nexus 5, you open up an exciting world of possibilities and deep customizations for your device. Among other things, it gives you the ability to flash custom ROMs which, individually, act as entirely different operating systems that can vastly alter your user experience.
Although a business plan is a technical document, remember that this first draft will not be. The audience and author of this document will be the owner/manager of the small business. The purpose is to get as much information written as possible so this draft can be used as a starter for versions of the business plan that are crafted for other audiences. It eliminates the possibility of the first business plan you write for other audiences actually looks like your first attempt. Since the lat...

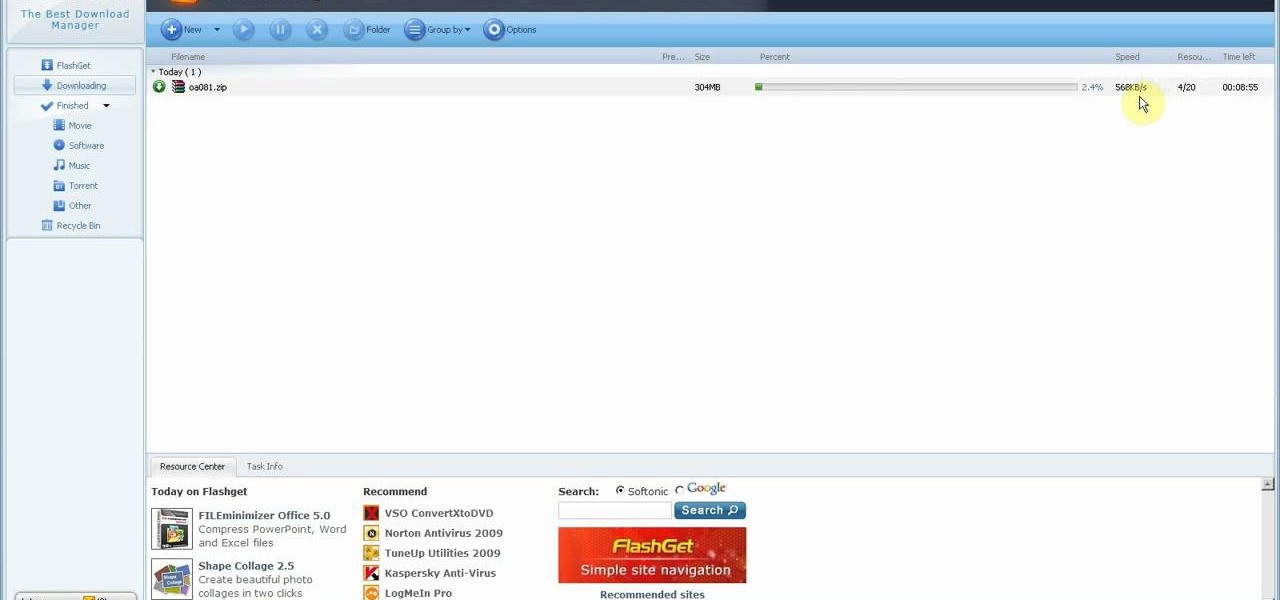
FlashGet 3 is a free high speed download manager that helps you keep track on how much far your downloads have left to complete. FlashGet supports HTTP,FTP,BT,MMS,RTSP and other protocols. It is seamless between protocols and there is no need to operate manually for download switch.

Just because you are using Linux, doesn't mean you have to be cut off from file sharing with those using a regular Windows PC. In this tutorial, learn how to share files between Ubuntu and Windows using a Samba local network. Samba is simple to use and can be obtained through your Synaptic package manager.

This video shows you how to use Windows Task Manager to restart your computer without losing any data.

Greg Lim is a professional handyman and residential property manager. Watch as he gives some helpful hints for how to manage and repair a slow flushing toilet. I must say, these are helpful tips that I had never thought of.

For better or for worse, Google started the race towards smartglasses for everyday use with Google Glass before scrapping the Explorer Edition and pivoting towards enterprise customers.

In many urban areas, GPS doesn't work well. Buildings reflect GPS signals on themselves to create a confusing mess for phones to sort out. As a result, most modern devices determine their location using a blend of techniques, including nearby Wi-Fi networks. By using SkyLift to create fake networks known to be in other areas, we can manipulate where a device thinks it is with an ESP8266 microcontroller.

With Android 10 "Q" right around the corner, now would be a great time to get accustomed to the new system-wide dark mode it's bringing with it. Dark themes not only allow for more comfortable viewing at night, but can also consume less battery at the same time. With a single button tap, you'll be able to enable this new dark theme for all compatible apps without having to jump through hoops.

A new set of APIs for Unity promise to make it easier for developers to publish apps that support both ARKit and ARCore.

After numerous scandals like the Equifax data breach and the 2016 US election, cybersecurity has become a significant issue for Americans. Unfortunately, anytime we use our devices, we're open to a cyber attack — especially when we browse the web. However, there are ways that we can make it harder for hackers and data miners.

We started with our system manager in the previous lesson in our series on building dynamic user interfaces, but to get there, aside from the actual transform, rotation, and scaling objects, we need to make objects out of code in multiple ways, establish delegates and events, and use the surface of an object to inform our toolset placement.

Android has several features built into the platform that improve user experience but require extra attention to prevent a security breach. By modifying these settings, you can drastically reduce the possibility of someone exploiting your device or intercepting information.

These days, that pocket-sized computer we call a smartphone is home to your entire digital life. But with the onset of mobile payments and online banking, the line between your virtual world and the physical realm is becoming increasingly blurred.