Honeywell recently completed successful testing of virtual window technology that enabled drivers to maneuver an otherwise windowless combat vehicle on rough terrain at speeds exceeding 35 miles per hour.

In the previous section of this series on dynamic user interfaces for HoloLens, we learned about delegates and events. At the same time we used those delegates and events to not only attach our menu system to the users gaze, but also to enable and disable the menu based on certain conditions. Now let's take that knowledge and build on it to make our menu system a bit more comfortable.

Hacking from a host machine without any form of proxying is reckless for a hacker, and in a penetration test, could lead to an important IP address becoming quickly blacklisted by the target. By routing all traffic over Tor and reducing the threat of malicious entrance and exit nodes with a VPN, we can configure Kali to become thoroughly private and anonymous.

After previously learning how to make the material of an object change with the focus of an object, we will build on that knowledge by adding new objects through code. We will accomplish this by creating our bounding box, which in the end is not actually a box, as you will see.

In 2013, Offensive Security released Kali Linux, a rebuild of BackTrack Linux derived from Debian. Since then, Kali has gone on to become somewhat of a standard for penetration testing. It comes preconfigured with a collection of tools accessible by a menu system, tied together with the Gnome desktop environment. However, Kali Linux isn't the only penetration-testing distribution available.

A developer has previewed a pair of potential applications built on ARKit that can be triggered by Alexa, the resident voice assistant of the Amazon Echo.

Move over, Spike Jonze; Microsoft has published a mixed reality music video featuring holograms of Reggie Watts filmed through a HoloLens.

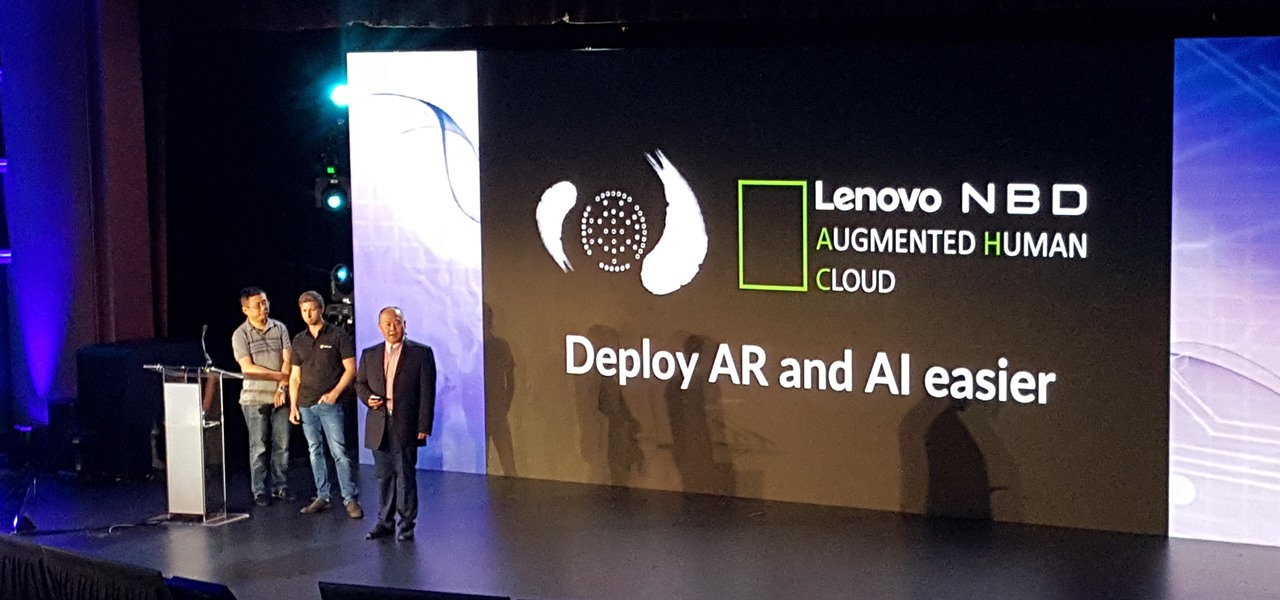
Lenovo has partnered with Wikitude to develop a cloud-based platform for delivering industrial-focused augmented reality content, the companies announced at the Augmented World Expo today in Santa Clara, California.

Earlier this month, Edgybees was the first game developer out of the gate with an augmented reality racing game for DJI drones called Drone Prix AR. Now, as the month closes, they are crossing the finish line with the first gaming app for Epson Moverio BT-300 Drone Edition smartglasses.

Kings Dominion, an amusement park located in Doswell, Virginia, just announced a mobile augmented reality game for park visitors. Gameplay in The Battle for Kings Dominion — available on May 19 for iOS and Android devices — follows the playbook designed by Niantic through Ingress and Pokémon GO.

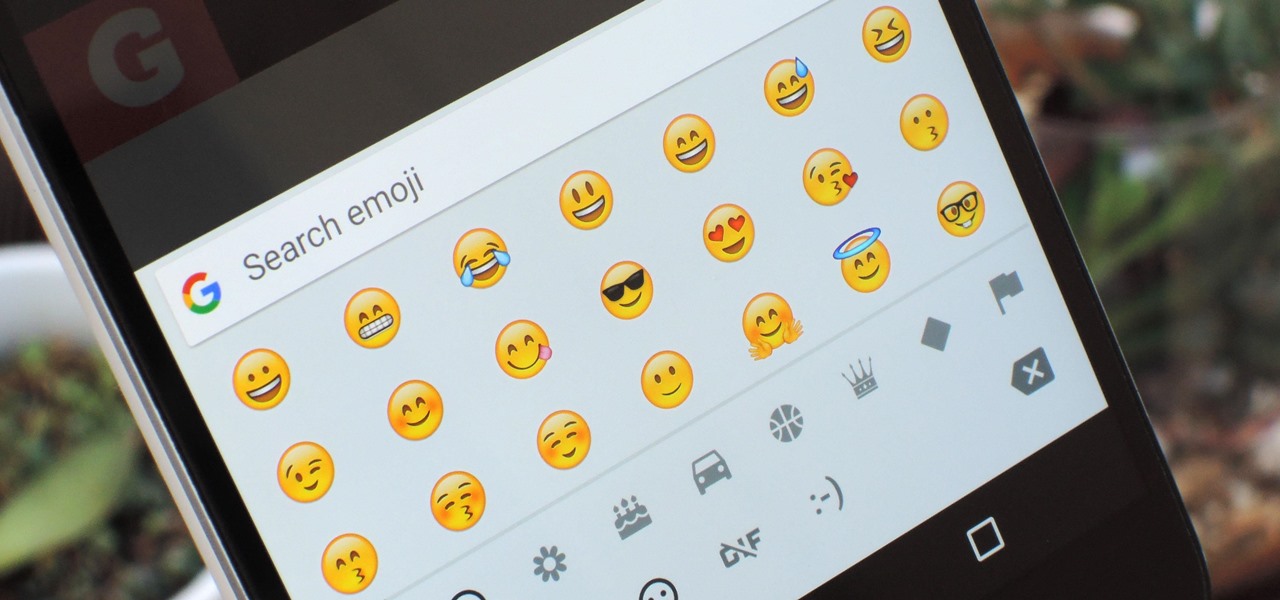
Everyone loves emojis, but some folks aren't quite happy with the way the little yellow guys look on their particular phone. In order to replace them, however, your device needs to be rooted, and you'll usually need to perform some complicated procedure that ends up making your phone hard to update since it modified a ton of files on your system partition.

While the world is only recently becoming aware of its existence, augmented reality has been around in some form or another since the '90s. In the last decade, with the advancement and miniaturization of computer technology — specifically smartphones and tablets — AR has become far more viable as a usable tool and even more so as a form of entertainment. And these are the people behind mobile AR to keep an eye on.

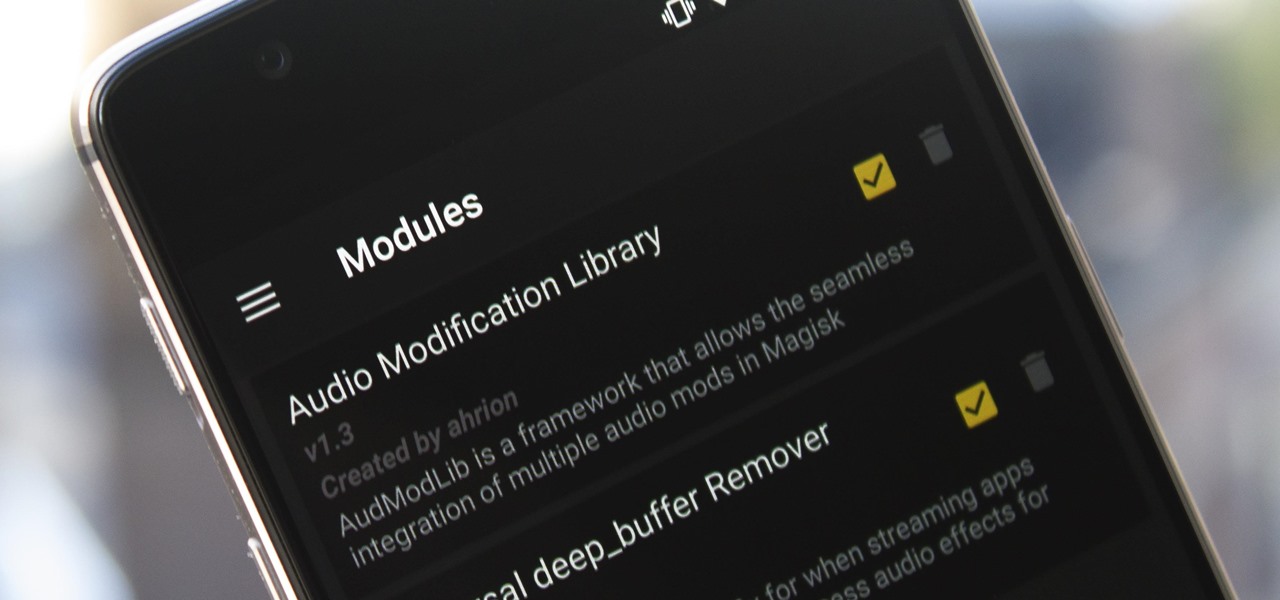
Most music streaming services will either use the stock Android equalizer or their own built-in equalizer. A couple of apps, such as Spotify, bring both to the table. Spotify has a built-in equalizer which kicks into play when a system or third-party equalizer isn't detected. However, other apps such as SoundCloud and Pandora don't use the installed equalizer even if it's a system-wide one.

OnePlus just unveiled a new version of their popular OnePlus 3T—a limited edition all-black "colette" version for the boutique's 20th anniversary today. The slick device will feature the iconic colette logo on the back.

In response to the flurry of doubtful headlines about Magic Leap today, set off by an unflattering article from The Information, Magic Leap CEO Rony Abovitz released a short blog post quickly detailing what to expect from the company over the next year. The gist comes down to this: big things are happening in 2017.

With some of the groundwork out of the way in getting a Mac set up for hacking, it's time to start looking at toolboxes. Our first toolbox is Git, which will be used throughout future tutorials.

If you own a Samsung Galaxy S7 and use the Samsung Gear VR, you may have woken up yesterday to an unpleasantly hot surprise. But don't worry—your phone isn't going to explode (probably). The problem is with a stubborn update to the Oculus apps.

Sure, sites like SeatGuru can show you which seats are the best—but in a 2D graphical form that doesn't really show you what the plane actually looks like inside and out. Aircraft Explorer contains 3D models you can peer inside of to check out what the next plane you catch will actually look like.

When you hand your unlocked iPhone to somebody so they can use the internet real quick, check out some cool photos, or do whatever, there's a possibility that they could snoop around where they don't belong. If you have some secret recipes, login credentials, intellectual property, or other sensitive information in your notes, you'll want to add some protection to them.

Since Live Photos are nothing more than a glorified, built-in GIF generator on the iPhone 6S and 6S Plus, there's no reason why you shouldn't be able to get this "exclusive" feature on an older iPhone. While taking a Live Photo does eat up a lot of processing power, which the A9 chips can handle perfectly, older iPhones can still manager fairly well—no 3D Touch needed. You just need a jailbroken iPad, iPhone, or iPod touch to do it.

With the gargantuan size of the Samsung Galaxy Note 4, it's no surprise that some of you might have trouble taking advantage of all the features using only one hand. One such feature is the newly-added fingerprint scanner, which allows you to swipe your finger on the Home button to unlock the device, among other things.

Anyone who has rooted their Android device has likely used a tool called Android Debug Bridge, better known as ADB, at some point during the process. For most, that is their only interaction with the ADB, but to be a true Android power user, you need to really know the tools at your disposal.

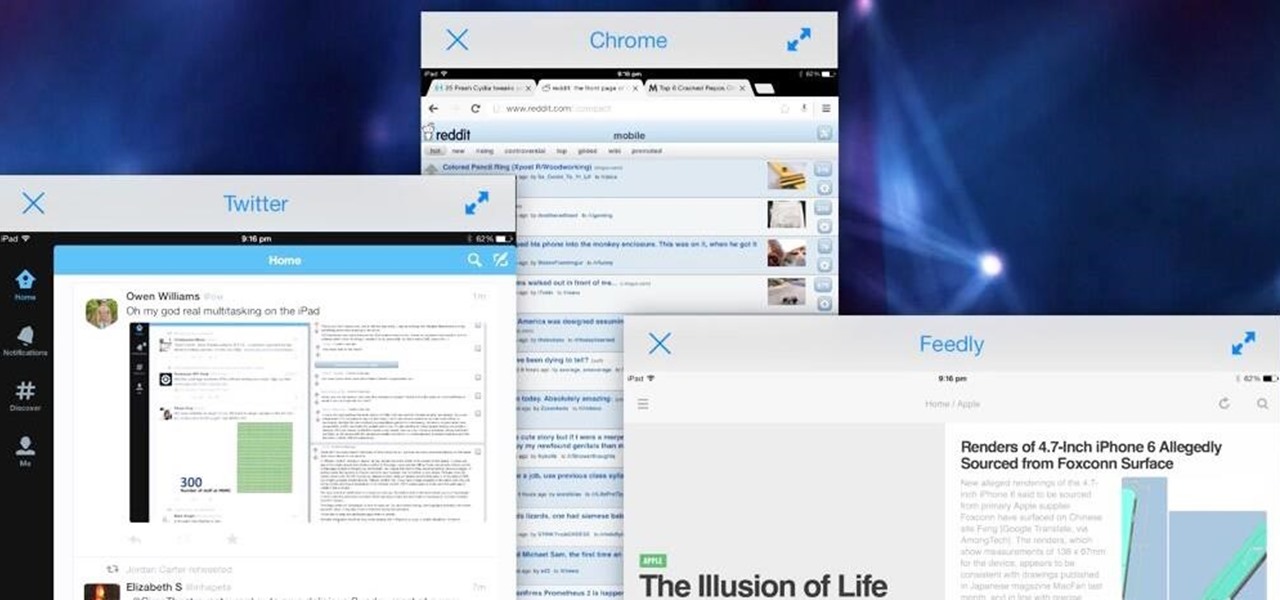
Samsung and Microsoft do it out of the box, Google does it with a little tweaking, and they all do it well—multitasking. While we can hope for better (or simply any) multitasking integration for the next iteration of the iPad and iPad mini, a new jailbreak tweak eliminates the wait.

The fingerprint sensor on the Samsung Galaxy S5 gets a little flack for its functionality, and that's mainly because the setup instructions ask you to swipe your index finger over the sensor to unlock your device or make mobile payments (and of course, because it was already hacked).
There has been much talk about how unsecure the cloud is because of PRISM’s newfound ability to demand all of your data without any resistance. This has spin doctors in the Cloud Storage industry losing their mind. They suddenly went from a central hub for 10GB of your files, to an easy window for Big Brother to track you through. Centralized cloud storage is no longer a safe way to keep your files, but we still need a way to access our files anywhere we go.

With the release of the Samsung Galaxy S4 right around the corner, us Galaxy S3 users also have reason for excitement. We already know that many of the S4 features will make their way to our devices, but who knew it would be this soon!

Samsung bucked the trend and threw hard keys onto the Galaxy S3 while most manufacturers are going the soft key route. This hack will add on-screen buttons to your TouchWiz-based ROM. You'll need a root file manager with a system writable text editor—I recommend ES File Explorer for this, but feel free to use whatever you want. If using ES, hit Menu, Settings, go down to Root Settings, and check Root Exploerer, Up to Root, and Mount File System.

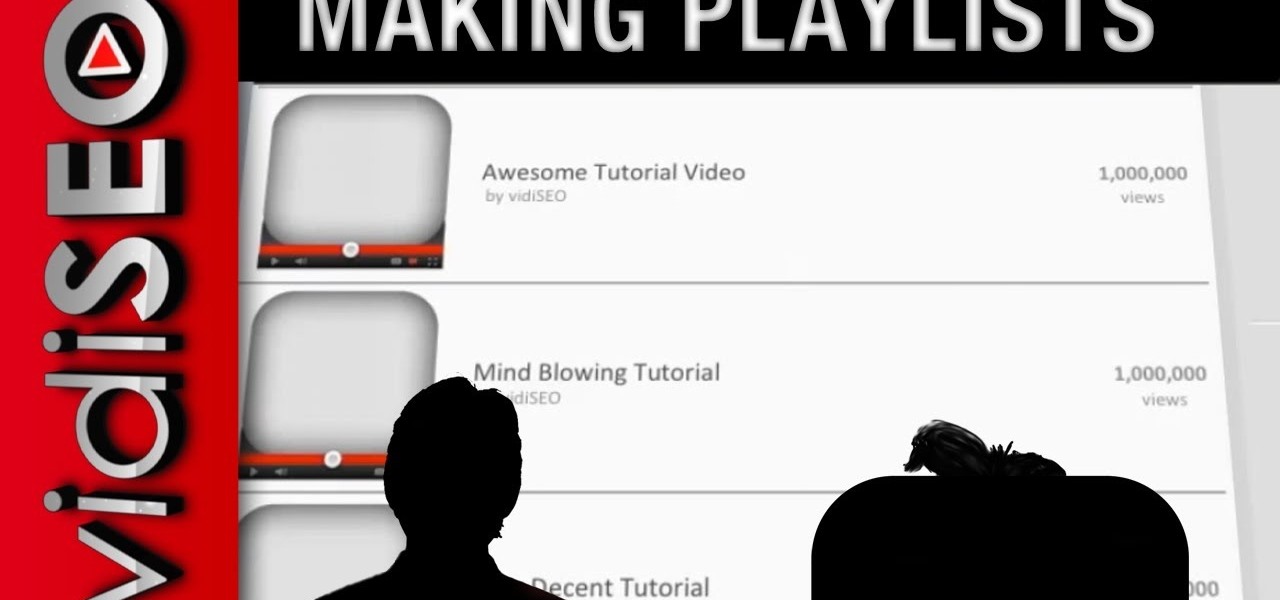
Playlists are a great way to organize and share groups of videos on YouTube. Playlists can consist of your videos, someone else's videos, or a combination of the two.

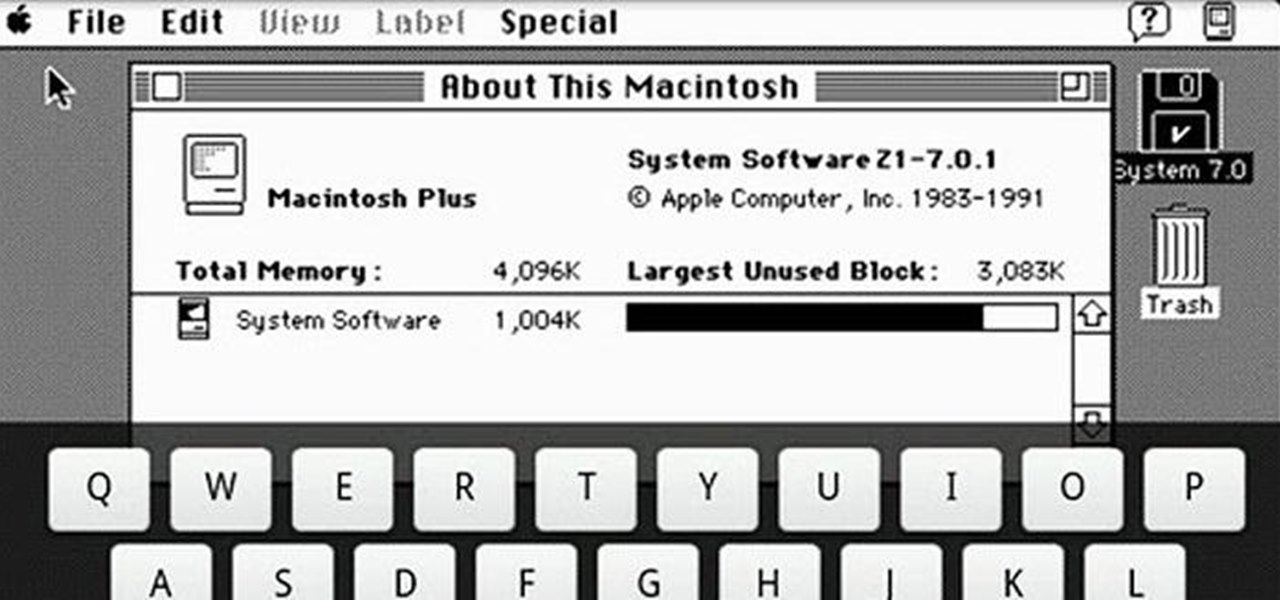
Remember these? Sadly, I don't, but I'm sure someone out there does. Anyone? This monstrosity, called the Macintosh Plus, was introduced in 1986 for the low-low price of $2,599. Wait...what? Almost three grand for that bulky baby?!? With a whopping 1MB of RAM standard?!? Whoa there...

While putting content and information online gets easier every day, it seems like getting it back is only getting harder. In a lot of cases (we're looking at you, Facebook), once you upload something, it's forever in the hands of someone else. That's where The Data Liberation Front comes in. Believe it or not, The Data Liberation Front is a team of Google engineers who work to make it easier for users to take their stuff back whenever they feel like it.

Early last month, Sony released PlayStation Mobile, bringing PlayStation games to the PS Vita and other certified phones and tablets. The list of certified phones isn't as extensive as it should have been, consisting of only Sony devices (a few tablets and Xperia) and a couple of HTC ones. For anyone with a supported device, you can head over to the PS Store for the download and installation instructions.

Samsung's Galaxy Note and Note II phablets have been hailed for their large displays and responsive systems, making them ideal for gaming and movie watching. But if you've recently upgraded to Jelly Bean (Android 4.1) from Ice Cream Sandwich (4.0), you'll be sad to know that some Android devices running Jelly Bean no longer support Adobe Flash Player.

As deeply as smartphones are integrated into our daily lives, it's no surprise that people are finding ways to use them to stay healthy. From detecting cancer and radiation to diagnosing STDs, phones have come a long way, baby.

Enter a password into a password field, and it's a sure bet that black dots or asterisks will obscure the characters. Nearly every website you visit in Safari on your iPhone will do it, but sometimes it helps to see what you're typing or what was auto-filled with iCloud Keychain, LastPass, or a different password manager.

Google lets you change the system-wide accent color on its Pixel devices, but the options are a bit muted. If you'd like something more vibrant, developer Tulsadiver created a mod that will give you a wide selection of punchier colors.

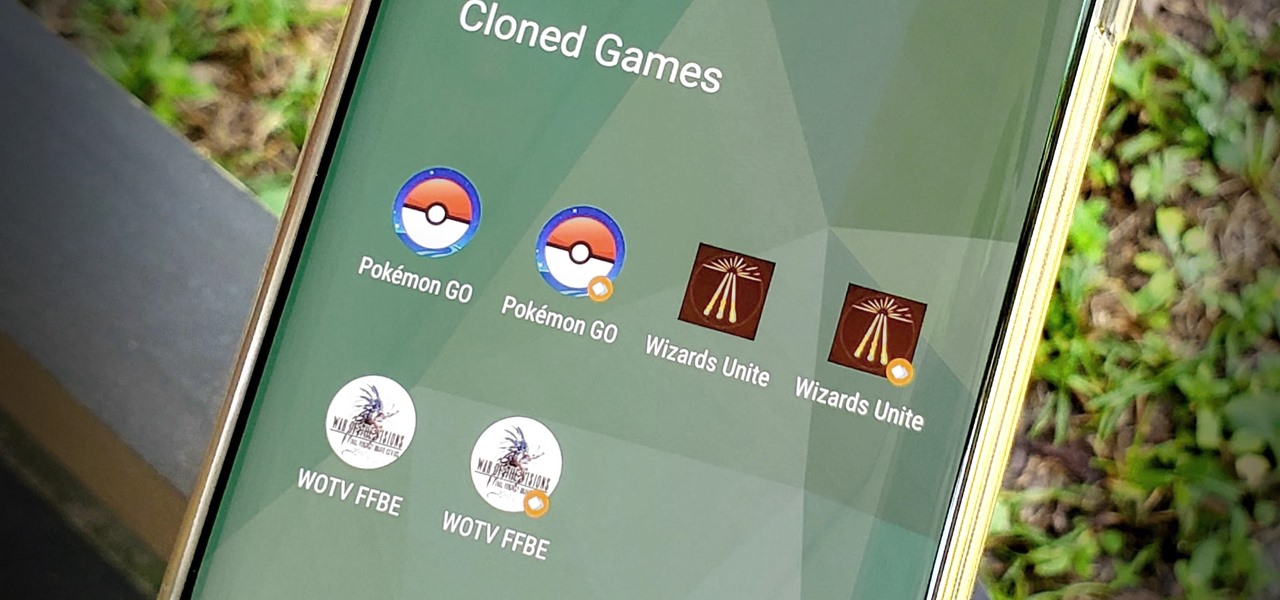
OnePlus offers a variety of features that you don't get with some other Android phones. Parallel Apps is one of those standout extras you didn't know you might enjoy until you've tried it. It allows you to clone compatible apps installed on your device, which means you can use the same app with two different accounts, for example.

With the Wigle WiFi app running on an Android phone, a hacker can discover and map any nearby network, including those created by printers and other insecure devices. The default tools to analyze the resulting data can fall short of what a hacker needs, but by importing wardriving data into Jupyter Notebook, we can map all Wi-Fi devices we encounter and slice through the data with ease.

The Digispark is a low-cost USB development board that's programmable in Arduino and capable of posing as a keyboard, allowing it to deliver a number of payloads. For only a few dollars, we can use the Digispark to deliver a payload to a macOS computer that will track the Mac every 60 seconds, even bypassing security like a VPN.

Whether we like it or not, our personal information and smartphones are tied together at the hip. The former needs the latter to deliver a personalized experience that matches our individual needs. This personal data, however, makes your phone a prime target for thieves of all sorts to turn your privacy into illicit profit.

Smartphones and other Wi-Fi enabled devices send radio signals called probe frames to locate nearby wireless networks, which makes them easy to track by listening for their unique MAC address. To show how this kind of tracking works, we can program a NodeMCU in Arduino to sniff the air for packets from any device we want to track, turning on an LED when it's detected nearby.