Last Friday's mission was to accomplish solving HackThisSite, realistic 1. This is the first in a series of realistic simulation missions designed to be exactly like situations you may encounter in the real world. This first mission, we are asked to help a friend manipulate the website voting system for a Battle of the Bands vote count in his favor.

Your BIOS, or Basic Input Output System, is the firmware on your motherboard responsible for initializing your computer's hardware when it is first powered on. It probes for video adapters, RAM, the whole works. The BIOS provides a small library of basic input/output functions used to operate and control the peripherals such as the keyboard, text display functions and so forth, and these software library functions are callable by external software such as the OS and system software within sai...
The days of entering left, right, left, right, up, down, up, down, a, b to cheat your way through a video game are long gone. With achievements and trophies in existence, game developers have, for the most part, removed cheats from video games.
JavaScript is the language of the internet. It is what allows us to create dynamic, interesting webpages that are fast, web-based applications and so much more. The primary use of JavaScript is to write functions that are embedded in or included from HTML pages and that interact with the Document Object Model (DOM) of the page. This is the magic that allows all of what we see to happen, and for our browser to be manipulated.

This is the first of a multi-part series on steganography techniques. Steganography, the art of hiding things in plain sight, has existed for a long time, and in many forms. When you manipulate the alphabet to have your own cipher and decipher, this is considered steganography.

In this Null Byte, I'm going to teach you about Null Byte Injections. Null Bytes are an older exploit. It works by injecting a "Null Character" into a URL to alter string termination and get information or undesirable output (which is desirable for the malicious user).

Fatherhood is difficult, especially when you're an octopus. That is the moral of the 2011 IGF Student Showcase winner Octodad, available for free from its website. This hilarious little title was created by a team of interactive media students at DePaul University in Chicago, and is the latest in a stream of successful indie games to come out of collegiate video game design programs. In fact, it's so successful that a sequel is in the works.

(Difficulty Level: from Newby to Expert) Digital cameras can produce freaky sharp images—it’s one thing that sets them apart from film cameras. A DSLR doesn’t have grain, it has noise—and that sounds a lot less charming for a reason. If you shoot at a low ISO, high f-stop and fast shutter speed, you can wind up with a super sharp image that might look great even on a billboard. But sometimes, sharp isn’t everything.

Video games and art have somewhat of a sticky relationship. Many video games have large teams of talented artists doing amazingly creative work, and yet the art community is only just beginning to utilize video games as art (sometimes). Perhaps if video games were shown not just as a medium of expression, but as a means of creating great art as well, the art community would be forced to consider it differently. The third part in the Hacked Kinect series will focus on the artistic possibilitie...

I'm pretty sure that it's a universal dream for everyone in the world to retire early. Who wants to to be stuck with the rest of the country and retire when you're almost 70 years old? You heard me right, 70! Most people can't go out and do the things they love to do by the time they're 70, unless they've been practicing good health and exercise their entire life.

Welcome to the 10th Community Byte session for coding in Python and completing the challenges presented to us by HackThisSite. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, from novice programmers to aspiring hackers.

Having bills to pay is one of the worst parts of life, especially around the holidays. And if you're extremely unlucky, you might also have to pay some hefty medical bills. This can put a heavy damper on plans, wants and needs. What's worse? The people that you owe money to are pushy and always bother you to pay in a more timely fashion, or worse, pay bigger premiums.

In light of this week's Giveaway Tuesdays Photo Challenge, we've posted a thorough guide to experimenting with bokeh photography. Most of the resources require a DSLR camera, and an intermediate understanding of some of the more technical components of photography.

GRAMARYE n pl. -S occult learning; magic 64 points (14 points without the bingo)

Cross-Site Request Forgery (CSRF, pronounce "sea-surf") is a common web exploit. However, for unknown reasons it's not used very often. It plays on a given website's trust in a web browser by executing another website's form action, for example, sending money to another person. It's usually placed in abnormal places like HTML image tags.

Foldit is definitely a niche game. The sole gameplay mechanic is attempting to fold complex proteins into smaller and more efficient shapes following the rules of molecular physics and biology. Points are awarded based on how small one can make the protein. Online leaderboards track players' relative progress and allows them to view and manipulate other players' completed designs. It's original, certainly, but no developer is going to ship a million units of a game about molecular-level prote...
To go Open Source or go proprietary? There is a common conception that open-source is unsafe and insecure and therefore companies should rather go for proprietary solutions. They think that because software is termed "open-source", that the world can see the vulnerabilities of the software and might exploit it, and less informed people tend to think that open-source software can be modified while it is running.

Nothin's better than freshly homemade popsicles in these hot summer months. Design Sponge has posted three delicious-sounding recipes by Ashley of Small Measure.

PDF files are awesome because they're easy to share and they prevent the format on your document from being messed up, no matter what system or program it's opened in. Their biggest downside, though, is how difficult they are to edit or change once they're made.

Dreams are like an internal human holodeck. Inside your mind, anything is possible, from your grandest wishes to your worst nightmares. This is all well and good, but what if you could control your dreams and become the omniscient god of a handpicked reality whenever you go to sleep? Inception took this idea to the logical extreme by invading other people's dreams.

Brainwashing is something that happens to us every day, whether you believe it or not. It doesn't take fancy tools or space-age technology. Even if our country didn't intentionally brainwash people (believe me, they do), our country's media is brainwashing people nonstop. Just sit back and think about it for a second—about the way things work in the world and media. But before you do that, let's learn what brainwashing really is.

This week's FIGRR is all about games that are old-new (or new-old, if you like) school. Each celebrates a different vital, yet largely taken for granted, aspect of video game history in the decidedly new-school world of indie games. Their titles betray them. Blocks That Matter is all about blocks. Recettear: An Item Shop's Tale is all about item shops. Neither are particularly sexy aspects of gaming, but both are ubiquitous elements of great games that can stand on their own.

The Process & Form Of Brian Craig- Wankiiri By Adam Reeder

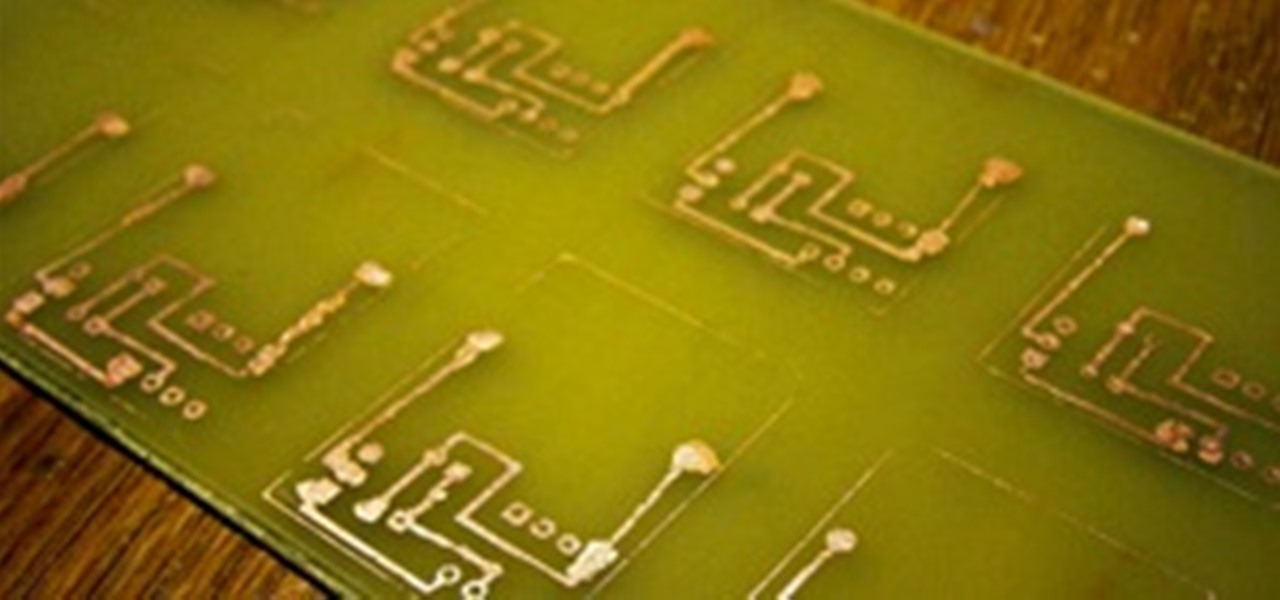
Homemade circuits are amazing. You can build any kind of circuit on a simple perfboard, as we have seen in previous projects. However, some projects require very tiny circuit boards. We could special order some boards from a printed circuit board (PCB) factory, but that will most likely involve a high price per board and a few thousand miles of delivery service to pay for.

Industrial espionage, social engineering and no-tech hacking are all very real and there are simple precautions that you can take to protect yourself, which this article will discuss. Whether you are a high-profile businessman or a housewife (or husband), keeping information you want to keep private, private, should be important to you.

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. There are many amazing redstone builds, but probably the pinnacle of redstone technology is the redstone calculator. The ability to turn simple game mechanics into a real-life calculator is one of genius, pioneered by some very clever Minecrafters many months ago.

Pumpkins, murderers, vampires, zombies, ghosts, witches, death… these are all the subjects of last week's Scrabble Bingo of the Days, which focused on words associated with Halloween and horror movies. Did you know there was actually a name for someone who suffocated another person? Did you know that Frankenstein, vampires, and ghosts can all be considered one thing? Did you know that there was actually a word for rotten dead flesh?

Sometimes an iDevice is best used for idle, pointless fun. Today's segment of Making Art on Your iOS Deviceis a mixed bag of time-wasting cool effects and random, but useful art-making tools. Below, 10 apps for creating anything from erratic hand-shaken digital effects to your very own DIY Andy Warhol prints.

Banksy, Cope2, Invader, Retna, Mr.cartoon, They all have a few things in common. Firstly, they are all extremely talented and well known urban artists. Secondly, they all have very memorable and very, very cool names.
Setting up shadows takes just as much time and attention as setting up lights. You can think of all of your illumination as one half of your lighting design, and shadows as the other, equally important half. Shadows can add richness to the tones and shading of your image, tie elements together, and improve your composition. Besides their artistic importance, rendering shadows is a key technical area to master. This chapter will explore both the visual and the technical sides of shadows and oc...

No doubt you've seen some of the hack logs being released. One part that stands out over and over again is the heavy database usage. It used to be early on that virus and hackers would destroy data, usually just for lulz. However, with the explosive commercial growth of the Internet, the real target is turning into data theft. You should learn how this happens so you can protect yourself accordingly. Let's take a look at what makes this possible and dare I say, easy.

Does your text box look cramped with the text too close to the box's edges? In this QuarkXPress video tutorial you will learn how to pad the inside of text boxes and how to manipulate the block features. Make sure to hit "play tutorial" in the top left corner of the video to start the video. There is no sound, so you'll need to watch the pop-up directions. Pad the inside of text boxes in QuarkXPress.

You can manipulate other objects beside human figure objects in Poser. In this Poser video tutorial you will learn how to link imported objects to models using the Change Parent menu. Make sure to hit "play tutorial" in the top left corner of the video to start the video. There is no sound, so you'll need to watch the pop-up directions. Link imported models to Poser figures.