New to the Mac OS X platform? If you've just switched platforms, you'll want some help accimating to your new operating system. In this tutorial, you'll learn how to use the OS X dock as well as how to use and manipulate windows in Mac OS X. For more on getting to know the Mac OS X operating system, take a look!

While editing databases with DreamCoder for Oracle, you may find that you want to manipulate master-detail. This minute-long how-to video will walk you through the process in DreamCoder for Oracle. Take a look.
If you are struggling with the paths tool and drawing vector art in GIMP, you can import other people's paths and manipulate them for your purposes! This tutorial will show you how to find sources at DeviantART.com and start using those in GIMP.
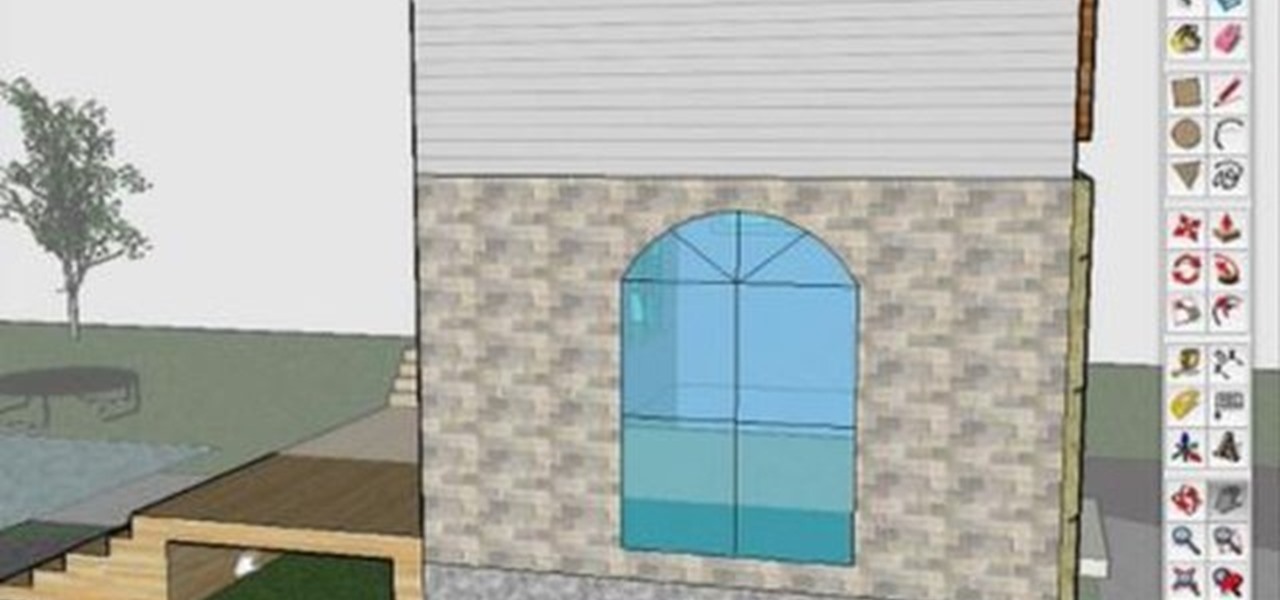
John continues his introduction to Google SketchUp with a third installment. In this episode we look at how to change the look/view in SketchUp using the styles and section plane to manipulate a pre-made house.

Do you have a rubber band and nothing to do with it? Here is a neat little trick you can show to your friends. Learn how to manipulate a rubber band and impress your peers with your magic skills.

The future is here with a new demo made with Apple's ARKit and LeapMotion. Typically, since ARKit works through your iPhone, in order to move augmented reality objects that are appearing on your screen, you have to drag them with your finger. However, developer Arthur Schiller is now playing around with how you can move augmented reality objects on your phone with gesture recognition, rather than by touching.

If you want to appreciate the value of microbes, look no further than a chunk of cheese. Because cheese roughly traces back to the Neolithic Era, we might say the earliest cheesemakers were the first humans to manipulate microbes—without even knowing it. Now, thanks to microbiologists and the long tradition of cheesemaking, we know a lot more about the microbes that make our favorite types of cheese possible.

Welcome back, my nascent hackers! We have spent a lot of time in previous tutorials focused on hacking the ubiquitous Windows systems, but the vast majority of "heavy iron" around the world are Linux or Unix systems. Linux and Unix dominate the world of Internet web servers with over 60% of the market. In addition, Linux and Unix servers are the operating system of choice for major international corporations (including almost all the major banks) throughout the world.

If you don't know Clay, you're probably going to want to. According to their website, Clay VR's goal was to not only expose users to the world of AR/VR, but fully immerse them in it. Clay does this by allowing users to feel like they were touching the objects in virtual worlds in order to make the virtual worlds feel more natural and real.

Meta CEO and founder — and Next Reality 50 member —Meron Gribetz unveiled a new operating environment for augmented reality called Meta Workspace for the audience at the Augmented World Expo (AWE) in Santa Clara, California, today.

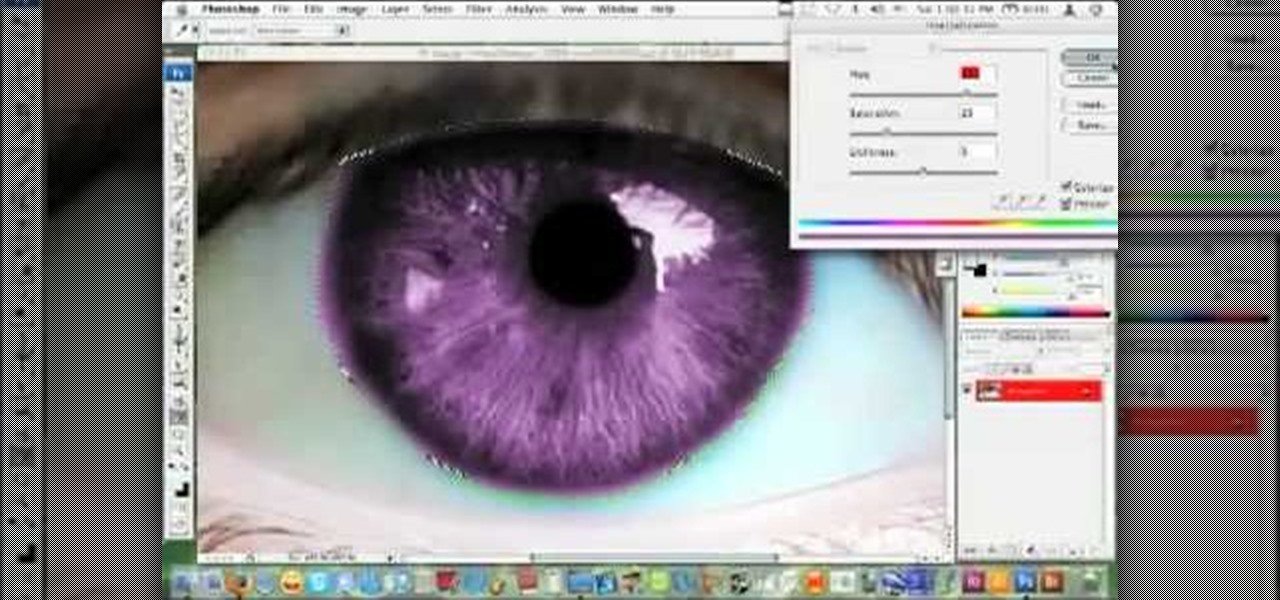
hotarrows223 demonstrates how to manipulate the eye color in a photograph using the masking tool. First, you must open the image with the eyes you intend to work on with Photoshop CS3. Next.], you must zoom in on an eye. You should be at the point where the iris fills up more than half of your screen. After that, you must select the iris, outlining it with the selection tool. Then, select image>adjustments>Hue/Saturation. Make sure all the boxes are checked, then adjust the hue or color bar t...

Learn to steal Kim Kardashian's pin curls and bangs with this video tutorial! Items needed: curling iron, straightener, blow dryer, hair spray, mousse, dual prong clips or bobby pins, comb and medium length bangs.

Photoshop is a great computer software program designed to help people manipulate images and text. Learn how to create a clown picture from an ordinary photo from a Photoshop expert in this free video series.

Here at Next Reality, our typical approach to all things augmented reality involves vision combined with remote control, either via a handheld device, gaze control, or hand/finger tracking.

In the world of analog synthesizers, hitting a key, twisting a knob, or sliding a fader makes a beautiful musical (or not so musical) sound and can be an amazing and downright satisfying experience. Now it's about to get even more satisfying, if you add Microsoft's HoloLens into the mix as a means to twist those knobs virtually instead.

In the last couple of days there's been a lot of speculation about the powers of Microsoft's HoloLens 2, but few have had a chance to get their hands on one to see if the company's claims live up to what HoloLens inventor Alex Kipman showed off on stage.

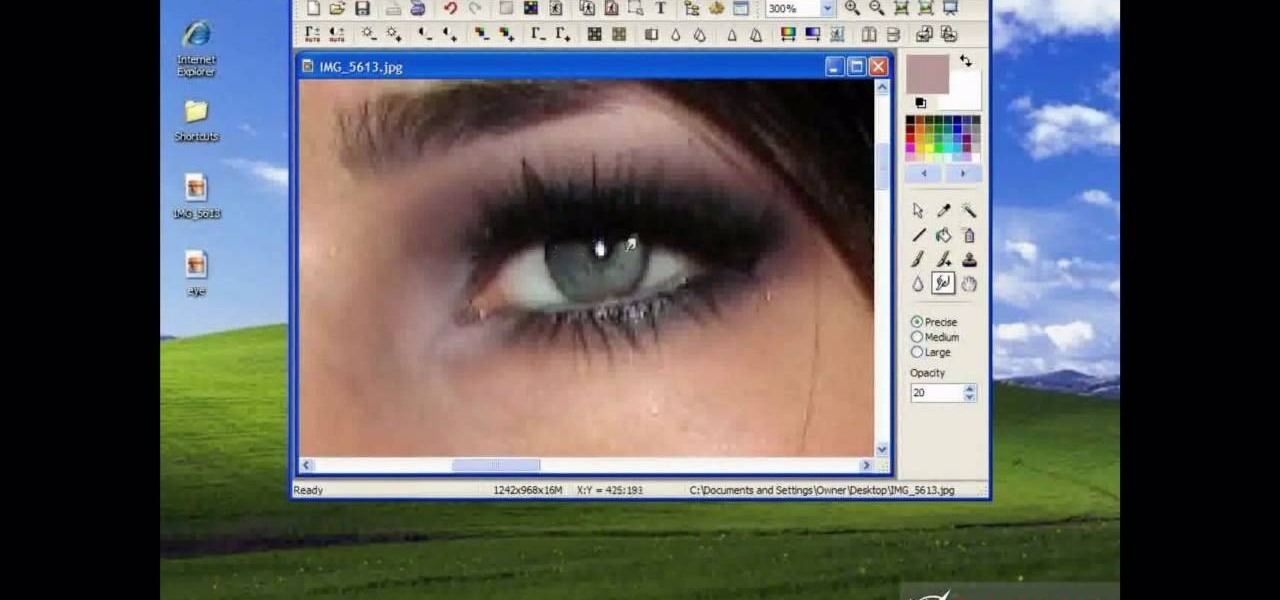
Why waste money on color contacts when you can change your eye color on a software program called Photofiltre? Photofiltre is free and you can manipulate your eye color to whatever shade you'd like in a few easy steps.

During our last adventure into the realm of format string exploitation, we learned how we can manipulate format specifiers to rewrite a program's memory with an arbitrary value. While that's all well and good, arbitrary values are boring. We want to gain full control over the values we write, and today we are going to learn how to do just that.

Hello everybody Joe here. Today I will be demonstrating how you can find XSS vulnerabilities in a website and what you can do with them

Last time in how to train you python, we covered the basics of variables and output. While we were covering variables, we talked briefly about strings. "String" is just a fancier way of saying "Word". A string is simply a set of characters encased in quotations, this lets python know that it is a word. Sometimes when we do things with strings we'll need to change them in order to do something. Python is case sensitive, for example "Null-Byte" is not the same as "null-byte". This is where mani...

No one can deny that Bashar Al-Assad’s regime has been responsible for violence. But in failing to equally acknowledge the fact that NATO-backed rebels have also carried out innumerable atrocities is not only dishonest, it represents a deliberate effort by the press to manipulate the narrative of unfolding events in Syria as a one-sided war crime rather than the truth – which is the fact that Syria is in a state of civil war.

Over the past decade, Marvel Studios has been a dominant force at the box office, raking in more than $21 billion dollars. Averaged out over that span of time, the yearly earnings of those movies outweigh the gross domestic product of some countries.

In the technology space, there are certain brands you grow to depend on. Whether it's due to a long, multi-decade track record of success, or new innovations that blow you away, some tech names accrue a rare kind of brand equity with users that's difficult to earn.

A great many S8 and S8+ users have undoubtedly spent quite a bit of time figuring out ways to unlock their new Galaxy in as few steps as possible. One of the most endearing features of previous Galaxy models was the ability to unlock the phone by pressing the home button and momentarily leaving your finger there for the sensor to do its job, almost instantaneously opening the device — all without having to pick up the phone.

Before you bite into that beautiful tomato in your garden, the tomato fruitworm, or the Colorado potato beetle, might have beat you to it.

Good day to everyone, today I will present some basic and advanced concepts that targets sophisticated attacks on the social basis, also I will write about some steps that can prevent this attacks from occuring, basically we will examine Social Engineering from the angle of attacker and victim, some people who are interested in security and work for middle-sized companys can learn and use something interesting from this post.

Welcome back, my novice hackers! This next subject might seem a bit obscure, but I promise you, this lesson will benefit you significantly either as a hacker or system admin. This tutorial will cover what is usually referred to as a regular expression, or regex for short.

After introducing and launching Reality Composer alongside iOS 13 and ARKit 3 last year, Apple is making it easier for developers to create apps with it.

Apple's iPhone X now has the power to turn anyone into a Japanese anime character, thanks to a new app that harnesses the device's TrueDepth camera.

Space might be the final frontier, but NASA is making a detour into augmented reality first. The Spacecraft AR app, developed by NASA's Jet Propulsion Laboratory (JPL) in collaboration with Google, debuted exclusively for Android this week (an iOS version is also in the works).

In another move that pushes Meta 2 toward becoming a legitimate workplace tool, Meta Company has partnered with Dassault Systèmes to bring augmented reality support to the latter's Solidworks 3D CAD software.

As a long-distance runner off and on for the past, I absolutely detests hills. While there are many apps that can measure elevation and slope for certain routes, understanding spatial data on a line graph or even an elevation map can be difficult.

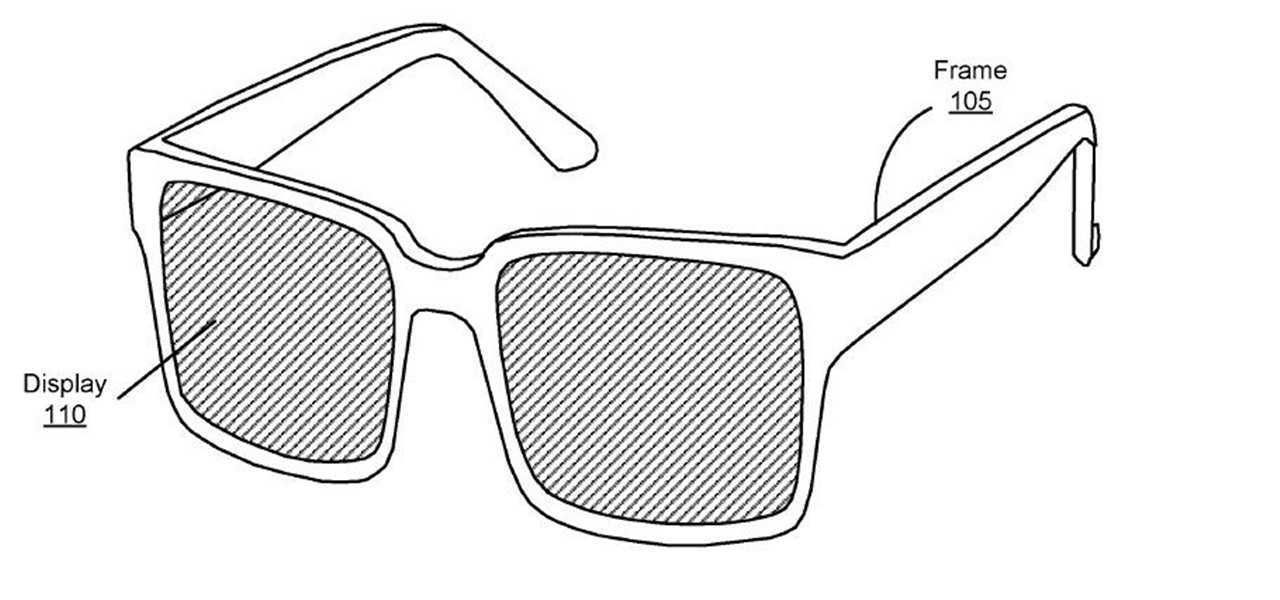
A patent application for waveguide-based smart glasses submitted by way of their subsidiary Oculus sheds light on Facebook's plans to escalate their augmented reality efforts.

While augmented reality is a means for presenting news to their audiences to some media outlets, Bloomberg is interested in how the technology can improve the way journalists work.

Theorem Solutions, a company that helps engineering and manufacturing companies reduce their costs, has taken the next step with their mixed reality technology. The company has now added their own app, called Visualization Experience, to the Windows Store for the Microsoft HoloLens

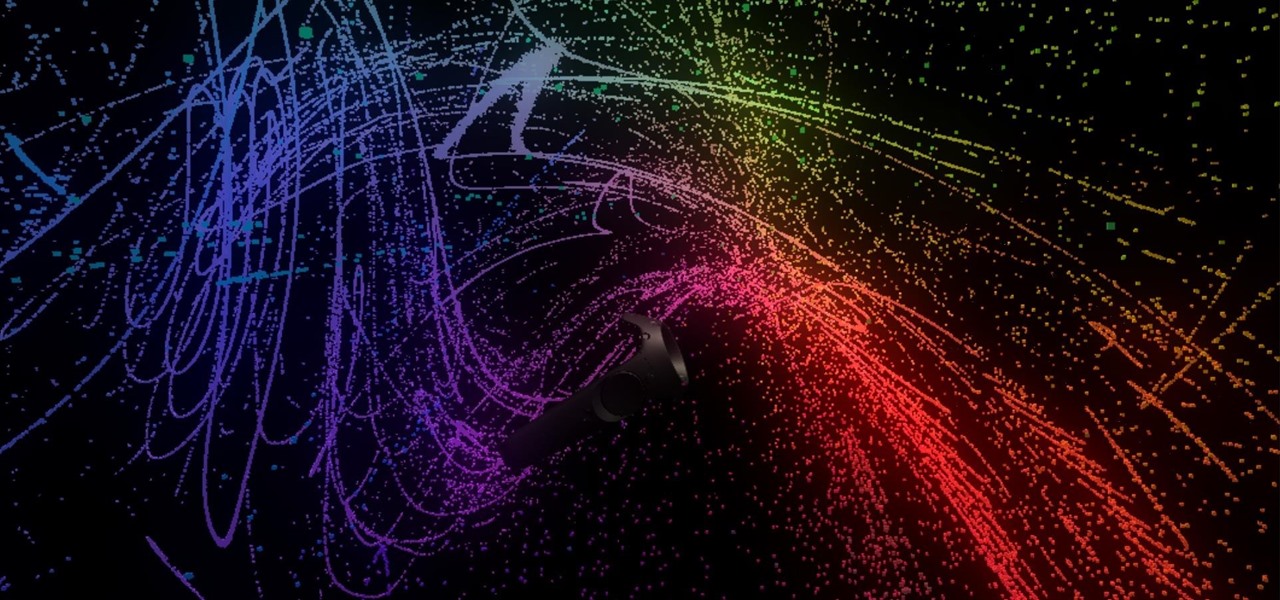
Want proof that user experiences matter? Look no further than the HTC Vive and Omnipudding's particle generator, GPU Cubes VR, which lets you interact with thousands of colorful, cubic particles in a black void. If this was a simulator for your computer only, controlled with a mouse or keyboard, you'd be bored in seconds—but it's just simple, instant fun on the Vive.

The Microsoft HoloLens has a good amount of content available, but it's fairly limited in terms of what you can customize. You can access a built-in library of holograms, but if you want to create your own you have to do that with code.

When opening a link or sharing a photo, your Android device will bring up a list of possible applications that you can complete the action with. However, some of the apps included you never use or didn't even know existed, and this leads to unnecessary clutter. Fortunately, if you're rooted, there's an easy way to remove apps from the "Open with" and "Share via" lists.

Yes, they're called volume keys, but they can do much more than adjust your volume. With minimal effort, you can do some amazing things with these physical buttons, like secretly record videos, toggle on your flashlight, scroll through pages, control your music, and much more. And while using them to wake your screen is useful, let's take it a step further and show you how to use them to completely unlock your device, even if the screen is off.

Welcome back, my greenhorn hackers, and happy New Year! Now that your heads have recovered from your New Year's Eve regaling, I'd like to grab your attention for just a moment to preview 2015 here at Null Byte. I hope you will add your comments as to what you would like to see, and I'll try to honor as many requests as I can.