This is, by far, the easiest way to root your Android phone, and it's even got its own name— the "SuperOneClick" method. This is a universal technique that applies to most Android-based smartphones (minus the HTC Evo and T-Mobile G2/Vision). TheUnlockr shows you the secret behind rooting your Droid, so watch and learn. Anyone with an Android-enabled phone can do this.
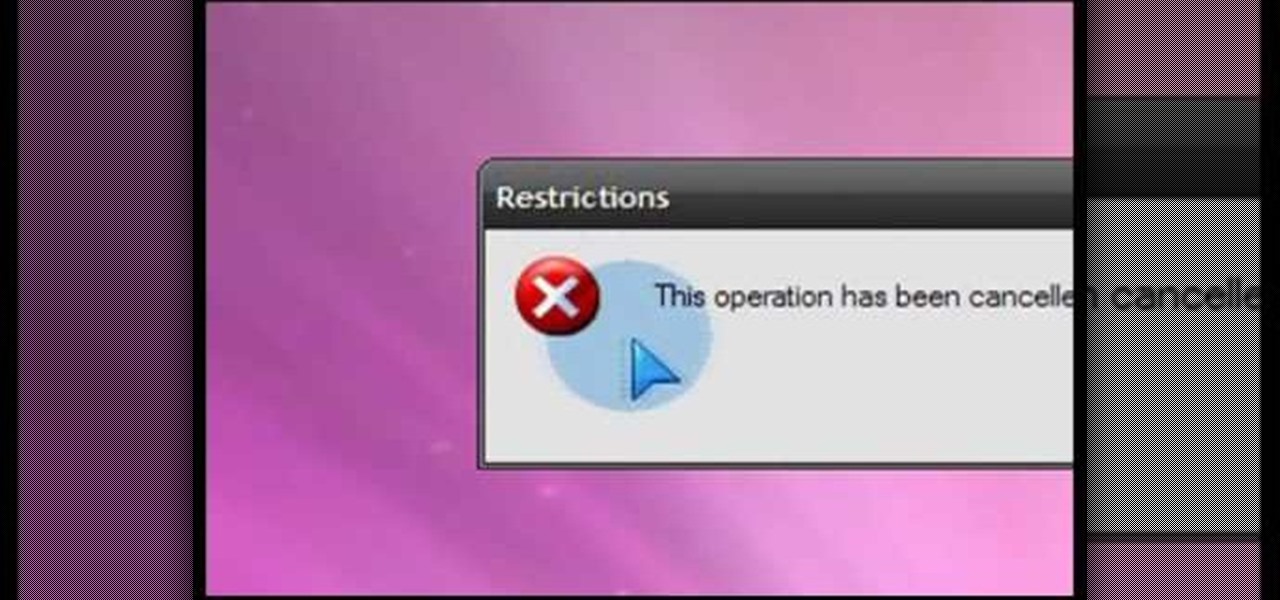
If you love computer pranks, this is one of the easiest ones to pull. This video will show you how to remove the Shut Down button from the start menu in Windows XP. Actually, it does't remove the shutdown button, it just disables it, giving the user a restriction message, stating "This operation has been cancelled due to restrictions in effect on this computer. Please contact your system administrator."

The Motorola Droid is getting a little long in the tooth, but it is still a remarkably capable phone with full keyboard, which makes it almost unique among it's Android-based competition. If you've rooted your phone (good for you!) and for some reason want to go back to the stock configuration that your phone was in when you took it out of the box, this video will show you how to do it. One good reason is if you want to update your phone's firmware, which will not work if you phone is rooted ...
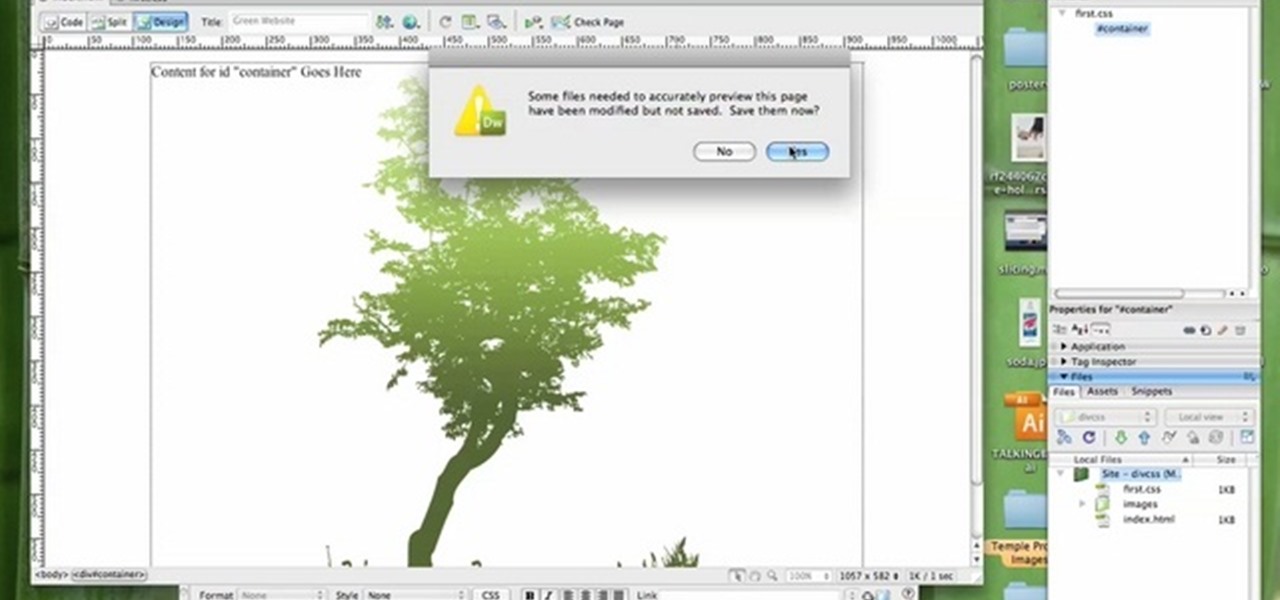
In this tutorial, we learn how to create a website with external CSS and HTML. Start off by managing your site like usual, then create a new HTML document and new CSS document. Now, name both of these to what you would like, then link them both together by linking the CSS in your HTML document. Now, make a container div, which is what will center your main document. Change your different settings so your div will be exactly how you want it to be. Next, make a banner for your page and set the ...
Have you played Heavy Rain on the PlayStation 3? It's an interactive drama with a film noir touch, where the four protagonists are on the hunt for a serial killer. And this serial killers name? The Origami Killer.

Tired of cleaning the stove and oven every time you cook? (It always gets so messy, doesn't it?) Well, there's one solution to keep the cleanup to a minimum, albeit a little unconventional, and that is to use your dishwasher!

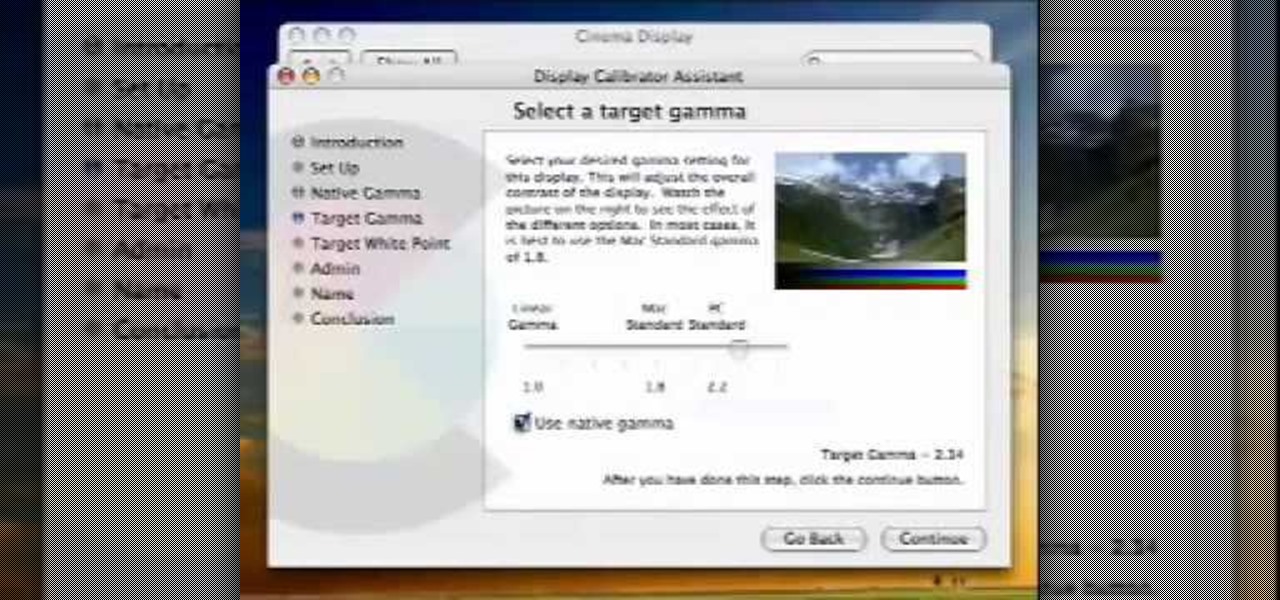
In this video from MacOSG we learn how to calibrate a Mac display by using ColorSync. Go to apple menu and select system preferences. Then go to Display. In there, click on color tab to access the profiles for your monitor. Click the calibrate button. It will bring up the Calibration Assistant. Make sure expert is checked. The goal here is to make the apple logo match the outside grid as much as possible. Click Continue and repeat the process. Next is gamma selection. In most cases the native...

Bowling is such a fun group activity and is perfect for birthdays and other types of gatherings. However, if you are not a pro bowler the scoring system can be pretty confusing. This tutorial will walk you through the steps of keeping score so you will know a strike from a spare and everything in between.

This video tutorial from TutVid shows how to create a simple movie poster text effect in Adobe Photoshop CS4.

There are a lot of things out there in the design world that people have seen and liked, but didn't know how to make. LIke vector lights. Watch this Illustrator video tutorial to take a look at those cool glowing, color changing, fading, bright, neon-like, fanning spread of glowing colors. Maybe there's no specific name for them, but for now, refer to them as 3D Light Ribs. You can use these in photographs, illustrations, composites, print work, web design, and maybe even a logo or two! You w...

Bid Whist can be a fun game for family or friends. It's challenging enough for adults, but enjoyable for kids too. Bidding and predicting wins are what make playing Bid Whist fun and exciting, whether you win or lose.

Learn how to create a warm, grungy background in Photoshop. - Open up a brand new document at 1280 x 720.

This is chemistry at its best! Europium is the chemical element (Eu) which was named after Europe. Dysprosium (Dy) is a rare earth element of a metallic silver luster. Watch this science video tutorial from Nurd Rage on how to make europium and dysprosium nitrate salts with Dr. Lithium.

Use this rigged game to cheat your friends twice in a row! The game functions just like 31, only this time you'll always win if you follow the instructions in this video.

Learn how to make Bento with YouTube's beloved Cooking With Dog. Ingredients for Bento

Right out of the box, iPhone is incredibly easy to use. If you want to get the most out of every feature, you’ve come to the right place. This video tutorial straight from Apple will teach you how to use Voice Control on the Apple iPhone 3G. The iPhone redefines what a mobile phone can do.

Find out how everything in a chemistry lab works, from pipettes to burners to recrystallization to storage. You'll get precise instructions on how to work and perform certain scientific duties in the chem lab, whether it's chemical or just ordinary high school science.

This video tutorial is for beginner puzzlers who are getting more advanced in their speedsolving of the Rubik's Cube. This 2-Look Method is exactly like taking 57 OLL algorithms and slimming them down to the single digits. First you orient the edges of the Rubiks Cube (or the cross if you prefer), then the corners, hence the name "2-Look OLL".

This tutorial video will teach you to make Shabu-Shabu. Shabu-Shabu is a Japanese beef hot pot served with porridge.

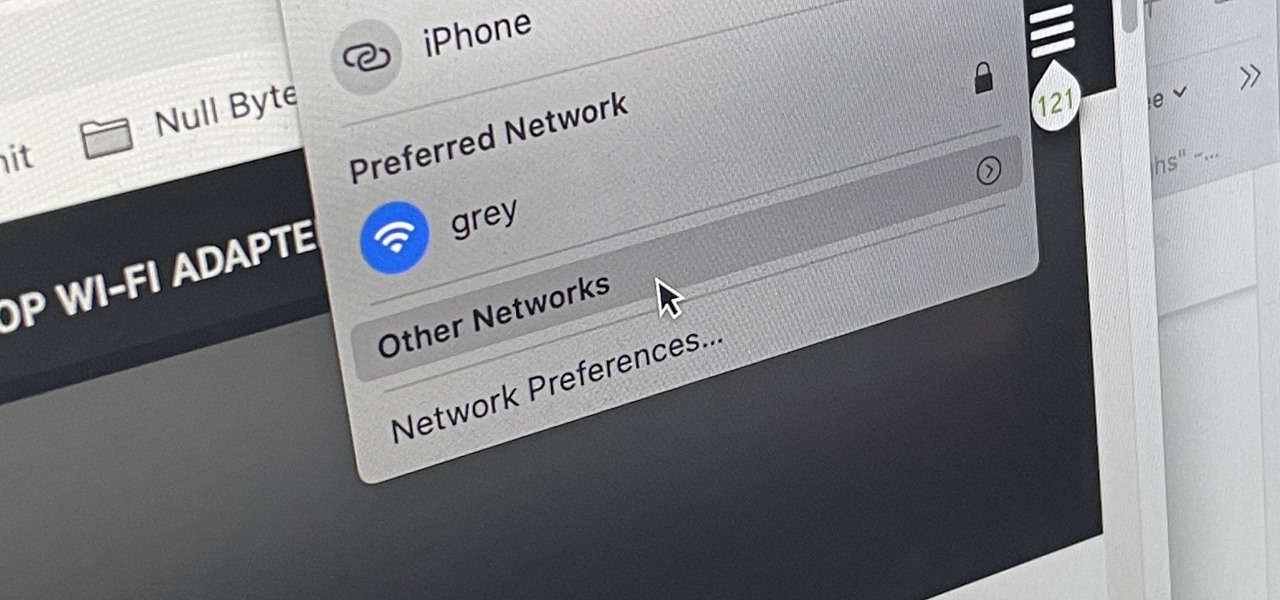
There are hidden Wi-Fi networks all around you — networks that will never show up in the list of available unlocked and password-protected hotspots that your phone or computer can see — but are they more secure than regular networks that broadcast their name to any nearby device?

Bloatware is a problem on Android, and it's not just a Samsung thing. Removing apps that have the Uninstall or Disable button grayed out in Settings has always involved sending ADB commands to your phone from a computer, which itself was always such a pain to set up. Thankfully, that has finally changed.

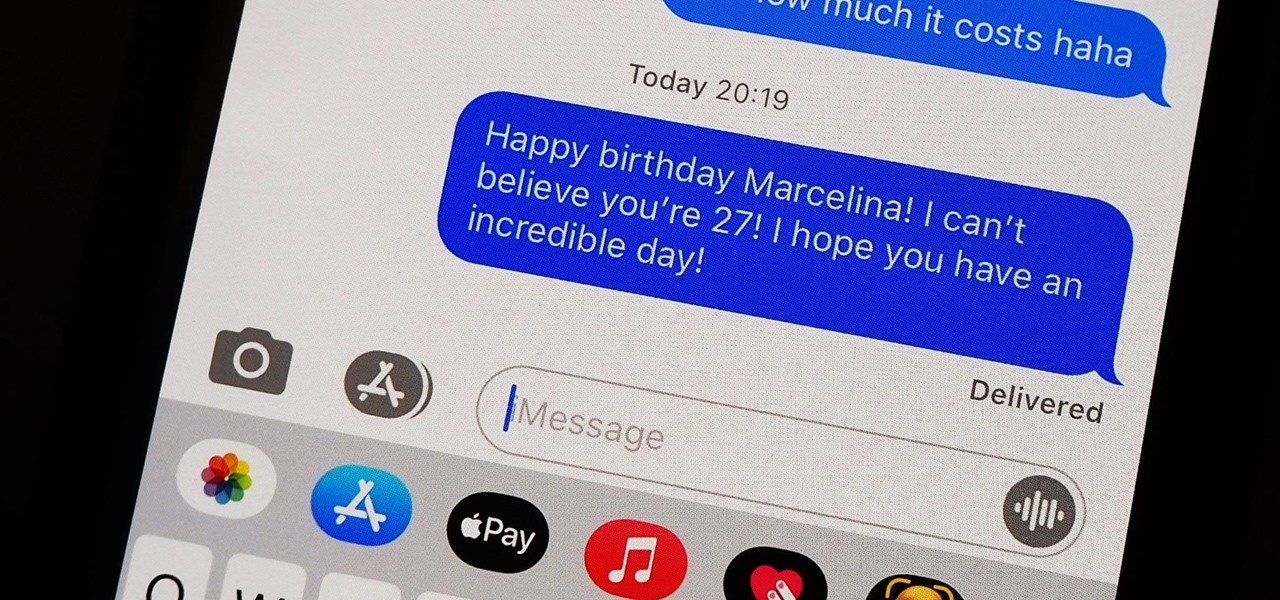
You should know the birthday for a parent, sibling, child, or significant other, but there are just too many people in your family and contacts to remember everybody's yearly birth anniversary. Still, everyone expects you to remember their birthday. To stop looking like a jerk, go a step further than putting birthdays in your calendar and make your iPhone help you send birthday wishes when their big day pops up.

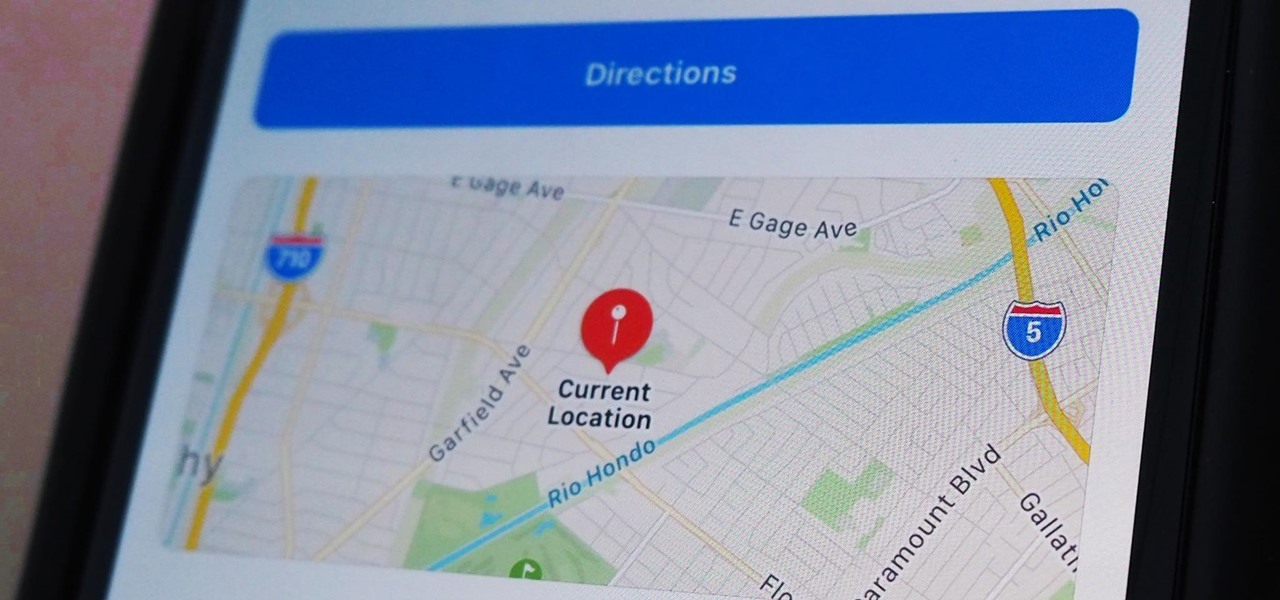
Apple makes it simple to share your location with your family and friends using tools built into the "info" page for each conversation thread in Messages. With those tools, you can send your current location or share trackable real-time coordinates. But iOS always has a few hidden tricks to make things easier than they seem, and that's precisely the case if all you need to do is share your current location.

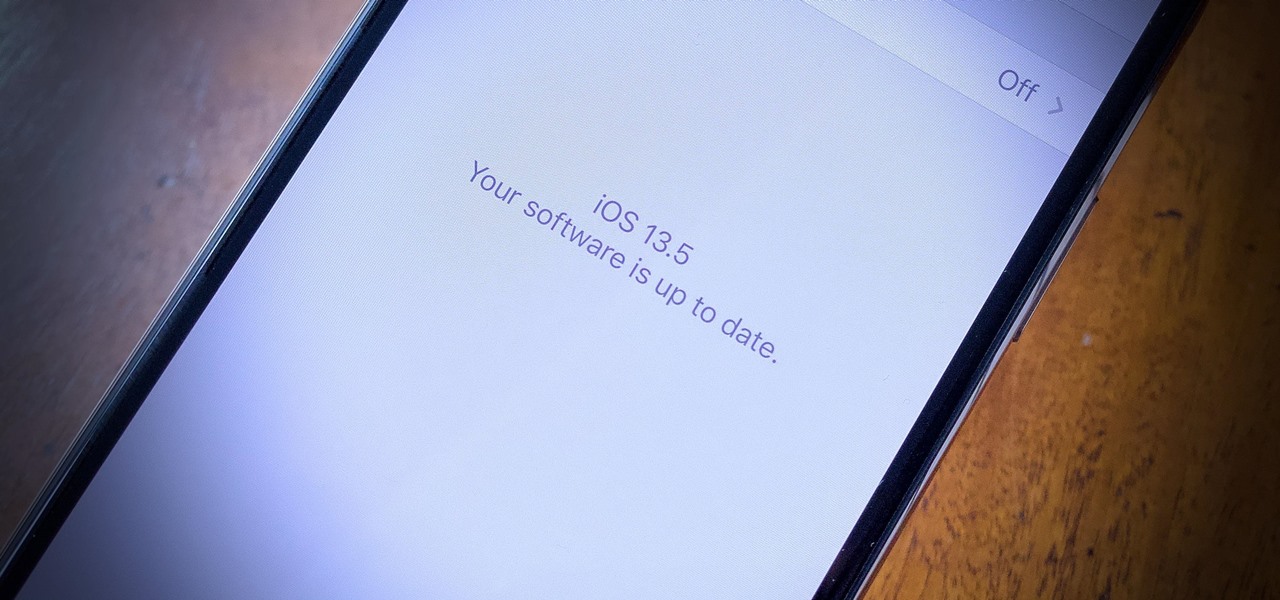
If you're a public beta tester, you woke up this morning with your iPhone running iOS 13.4.5. Today, Apple released the second beta for iOS 13.5. No, Apple didn't skip a version — 13.5 public beta 2 is essentially 13.4.5 public beta 2. So why the name change? Apple included the first API for its joint COVID-19 contact-tracing and exposure notification program with Google.

If you're using or need to use Zoom, the popular video teleconferencing service, you've almost certainly heard about "Zoombombing" by now. While Zoom has been adding security measures to address the problem, there are other things you can do to prevent or stop Zoombombers in their tracks so that your video meetings and chats go undisturbed and uninterrupted.

When it comes to sniffing Wi-Fi, Wireshark is cross-platform and capable of capturing vast amounts of data. Making sense of that data is another task entirely. That's where Jupyter Notebook comes in. It can help analyze Wi-Fi packets and determine which networks a particular phone has connected to before, giving us insight into the identity of the owner.

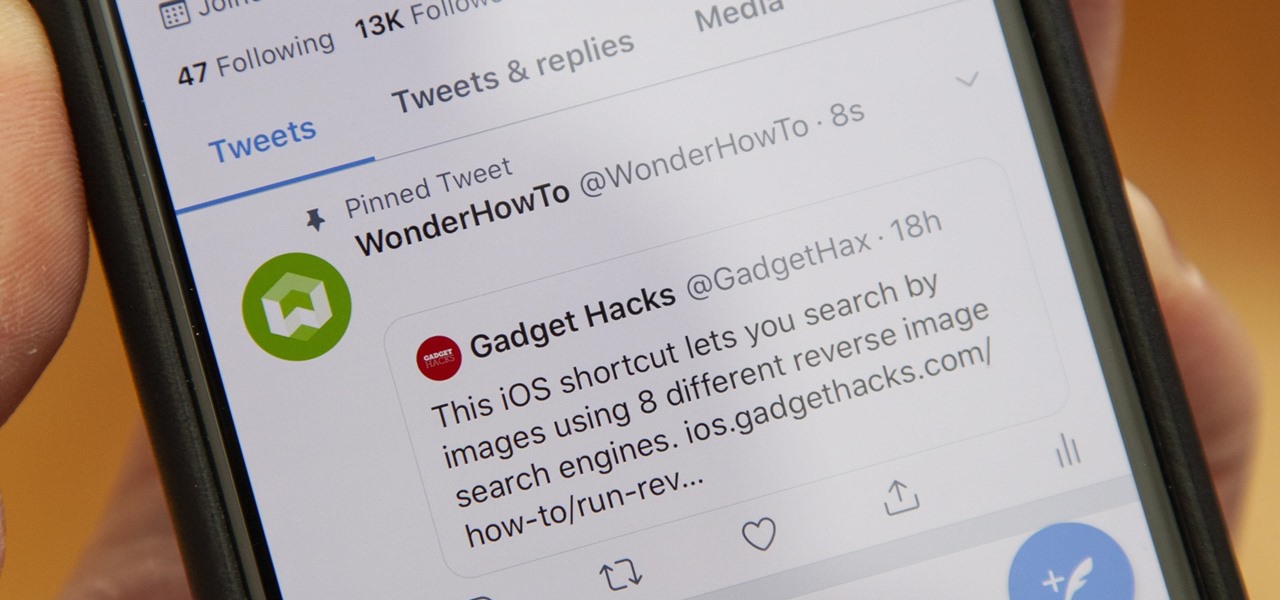
On Twitter, you can pin one of your tweets or replies to your profile, so it's the first post people see when they visit your page. However, Twitter prevents you from pinning someone else's tweet. You can't even pin something you retweet. There is a clever workaround, though, and it also works for posting empty tweets.

While many people may use Bluetooth every day, the majority don't know how it works or that it can be hacked. Bluetooth hacking gives a clear window into the world of the target. Nearly every device has Bluetooth capabilities, and people store a great deal of personal info on their phones and tablets. Hack their Bluetooth connection, and you may be able to access all of that data.

What if you went to an art installation at one of the coolest venues in New York that you could then take with you anywhere in the world?

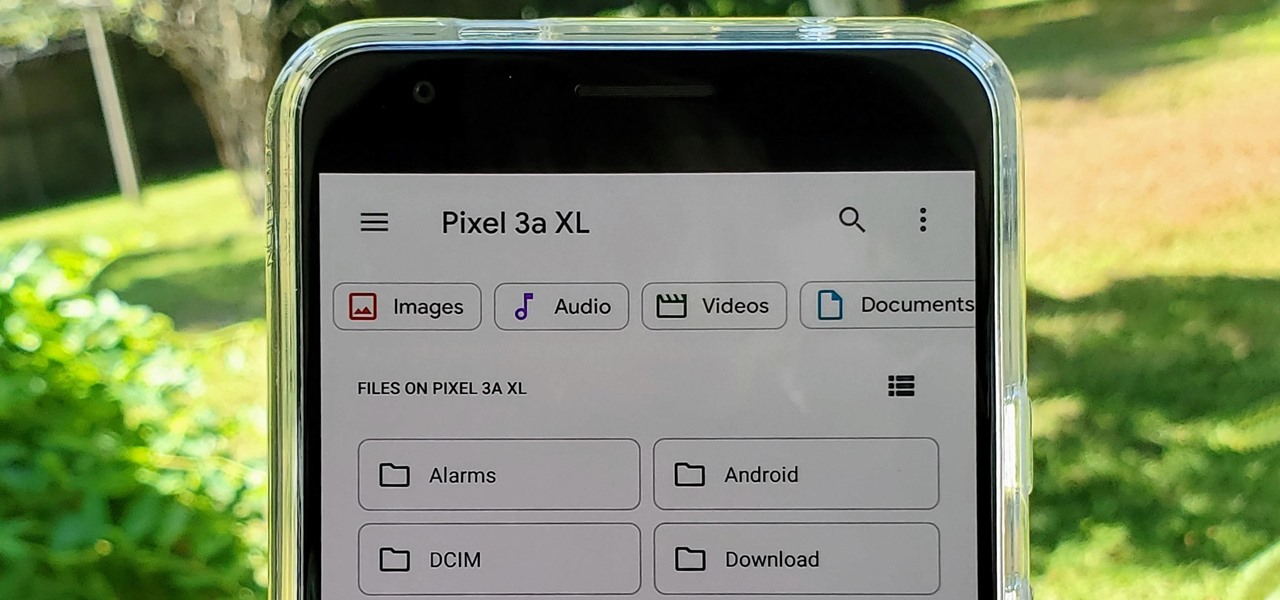
With the files on our devices getting more important as the years go by, the need to keep things organized continues to rise. The longer you have a device, the messier the internal storage might become. Having a file manager would be extremely useful in this situation. You could also reorganize the folder structure as well, just like you could on a desktop computer.

There's something about alcohol that compels you to contact people. Most of the time, the drunken calls or messages you send out will have you cringing hard tomorrow morning. But if you have a jailbroken iPhone, you can help prevent this potential embarrassment with a free tweak.

Sure, Tony Stark was able to build the original Iron Man suit in a cave with a box of scraps, but can the average do-it-yourselfer replicate the EDITH smartglasses from Spider-Man: Far From Home in a similar fashion?

Businesses that have adopted enterprise-grade wearables for their workforces now have a new option among the multitude of AR productivity apps that can help their team members communicate in AR.

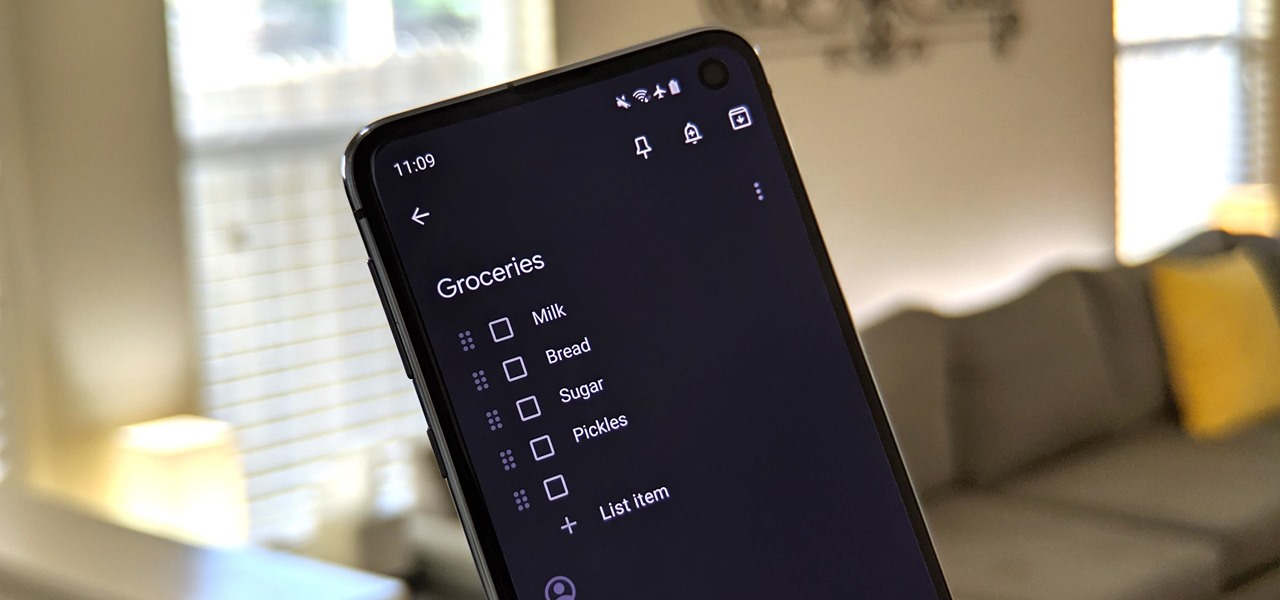
Life can get busy. Between work, school, and all the extracurricular activities, weekly chores like making a grocery list can get pushed to the back burner. But with a little help from the Google Keep app for Android or iPhone, you can at least make one thing easier.

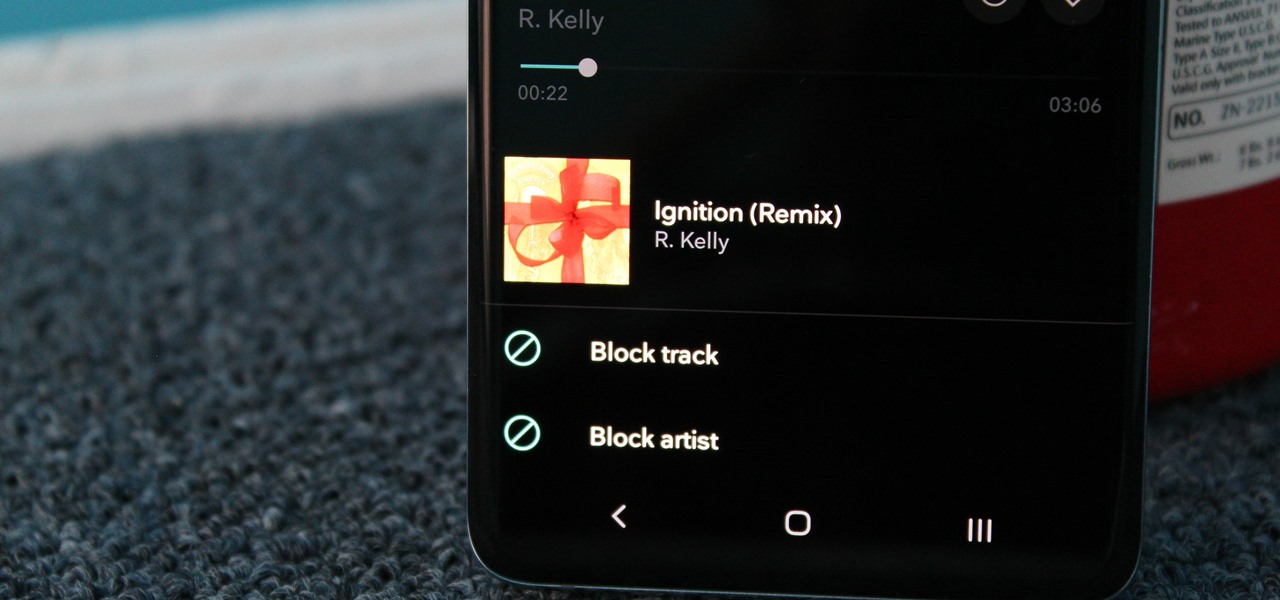
From XXXTentacion to R. Kelly, many artists have been accused of inappropriate actions, so some of us just don't want to hear their music anymore. However, each time streaming services attempt to ban such artists, they face heavy backlash. Recognizing this, Tidal decided to offer a different solution.

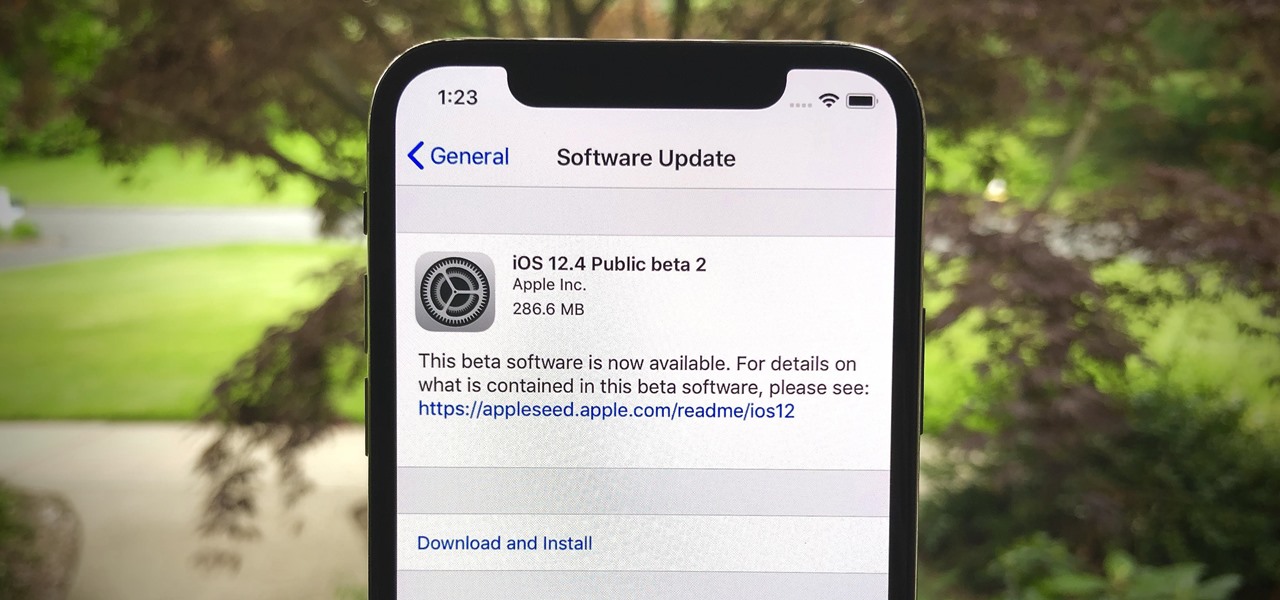
Public beta testers, you're in luck. Apple just released the second iOS 12.4 public beta today, May 20. The update comes five days after the release of the first developer beta for iOS 12.4 and seven days after the release of iOS 12.3. Public beta 2 and dev beta 2 were both released at the same time, something that doesn't happen often.

The Windows 10 desktop and microphone can be livestreamed without using Remote Desktop Protocol (RDP) software and without opening any ports on the target computer. A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in real time no matter where they are. Hackers are watching and listening, and there are few ways to protect yourself.

The price of hacking Wi-Fi has fallen dramatically, and low-cost microcontrollers are increasingly being turned into cheap yet powerful hacking tools. One of the most popular is the ESP8266, an Arduino-programmable chip on which the Wi-Fi Deauther project is based. On this inexpensive board, a hacker can create fake networks, clone real ones, or disable all Wi-Fi in an area from a slick web interface.

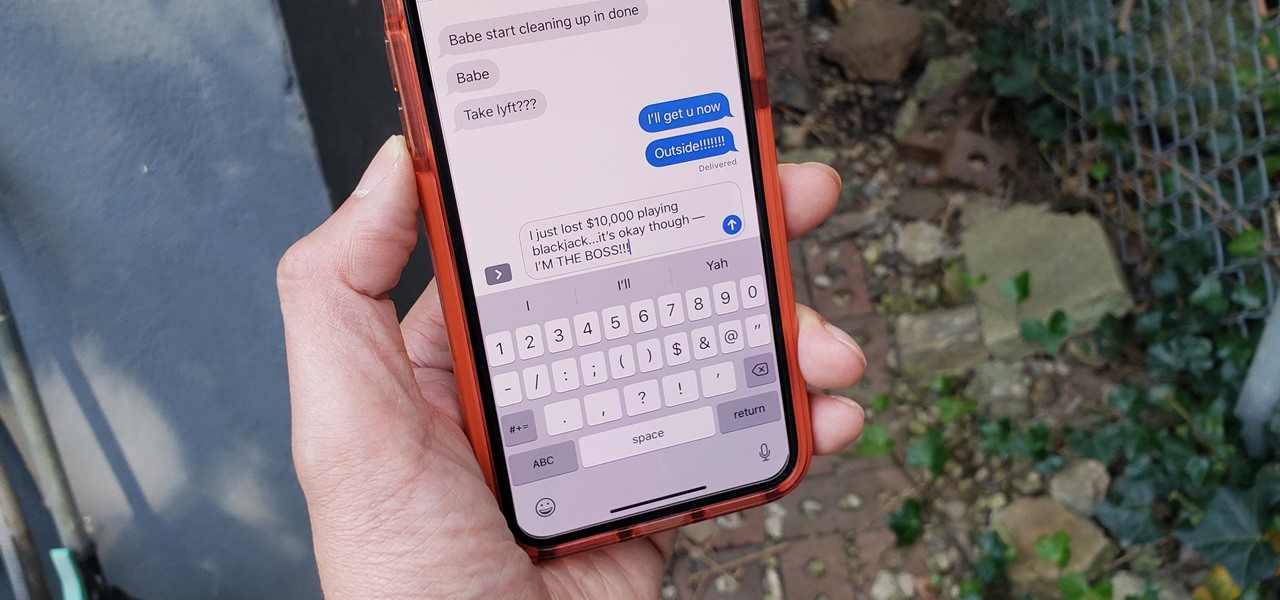
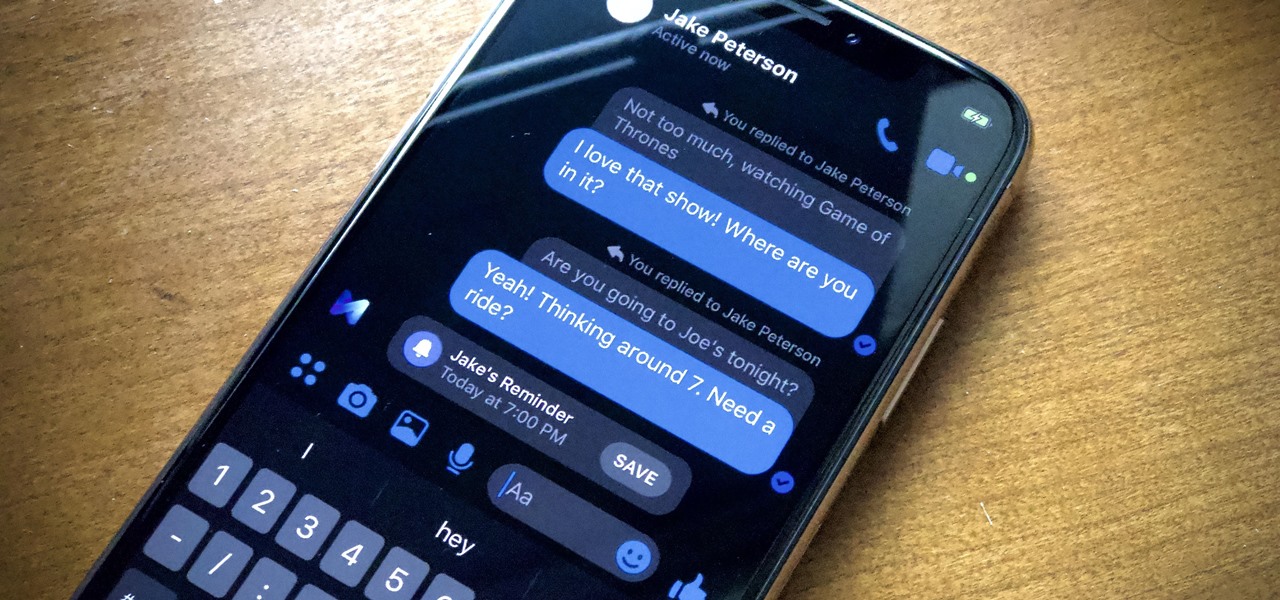
Text conversations can get confusing fast. In the time it takes to type up a response to your friend, they can send you one, two, three, or more messages. Once you send the original reply, it no longer makes sense in the context of the chat. Clear up the confusion with Facebook Messenger's "new" quote reply feature, which shows both you and your friend exactly what message you're responding to.

Directory traversal, or path traversal, is an HTTP attack which allows attackers to access restricted directories by using the ../ characters to backtrack into files or directories outside the root folder. If a web app is vulnerable to this, an attacker can potentially access restricted files that contain info about all registered users on the system, their permissions, and encrypted passwords.