We last saw China-based augmented and virtual reality headset maker Shadow Technologies at last year's Augmented World Expo, where they had the Action One, one of the wildest augmented reality headsets we've seen, on display.

The spirit of Google's Tango augmented reality platform lives on at Vivo, a China-based company that has developed its own 3D sensor for mobile devices.

Enterprise augmented reality developer Atheer is bringing its AR solution for enterprise businesses to the HoloLens by way of a joint venture with fellow AR developer Design Interactive.

In October of 2017, Mathy Vanhoef released "Key Reinstallation Attacks: Forcing Nonce Reuse in WPA2." This paper demonstrates a way to decrypt traffic on practically any WPA2 network, the most commonly used form of wireless security (seeing as all other forms of Wi-Fi encryption have already been broken). Practically all of the network-connected devices we use will need to be updated in some way in order to protect against this vulnerability, each of them in a different way.

Android Oreo may not be the flashiest release, but it's got tons of under-the-hood changes. We recently discovered documentation in the AOSP source code that outlines one of these understated features, which has been dubbed "Rescue Party."
Measuring a room has never been so easy thanks to Apple's ARKit. SmartPicture 3D is known for its quick measurements based on pictures from your smartphone. Recently, they released a video of the company measuring a room using the ARKit.

Apple is working on autonomous systems for vehicles, which could then be implemented with the help of car manufacturers.

The latest trend in smartphone design is all about the display. Manufacturers want larger screens with smaller bezels. The rumors are heating up about Google's next big release, the Pixel 2, and with that, we may have a clue that shows us Google is hopping on the display train.

With autonomous technology being developed so quickly, auto companies have begun working on the next step in driverless development, passenger safety. German automotive supplier ZF has begun giving this some thought and has come up with a new kind of airbag, one that could define safety features in autonomous vehicles.

Volvo is joining the autonomous vehicle race. In a video released Tuesday, the company showed off its concept for a driverless garbage truck, adding themselves to a growing list of manufacturers pledging to work in the self-driving field.

With products and solutions offered by the likes of Scope AR, Trimble, DAQRI, VIATechnik, and others, augmented reality is becoming a hot commodity for improving productivity while maintaining safety in the construction and manufacturing industries.

Google released its "Android Security: 2016 Year in Review" report last month, and to no one's surprise, included its own flagship phones. However, one surprise on the list was the BlackBerry PRIV, which Google named one of the best Android devices for privacy.

It's the bane of many a tech geek's existence that the customizability of Android software cannot be combined with the sleek design of the iPhone. A new Kickstarter project titled Eye, however, is looking to change that with a new iPhone case that allows you to combine the two.

This year's Game Developers Conference, better known as the GDC, is underway at the Moscone Center in San Fransisco, California, and lasts until March 3, 2017. More importantly for us here at NextReality, the Virtual Reality Developers Conference (VRDC)—a new GDC sub-conference geared toward augmented, mixed, and virtual reality—has begun.

More proof is emerging that the iPhone 7 won't include a 3.5 mm headphone jack, and damn—it is not pretty. These third-party Lightning-to-3.5 mm dongles were spotted on Chinese site Tama, and they give us a glimpse into a horrifying future in which we have to attach one of these clunky monstrosities to an iPhone just to connect a set of standard headphones.

Chinese tech company OPPO has been on the cutting edge of smartphone battery charging since it released its VOOC Flash Charge in 2014. Using VOOC, you can charge your battery from 0-75% in 30 minutes.

It's looking more and more likely that rumors stating that the iPhone 7 will not include a 3.5 mm headphone jack are true. Chinese websites Wei Feng and Anzhuo.cn reported that anonymous sources on the supply chain confirmed that the controversial design choice is a reality.

Update (February 2019): The methods below will help on older Android versions, but we've recently revisited this topic. So if you have a newer Android phone and you want to get rid of Google, head here.

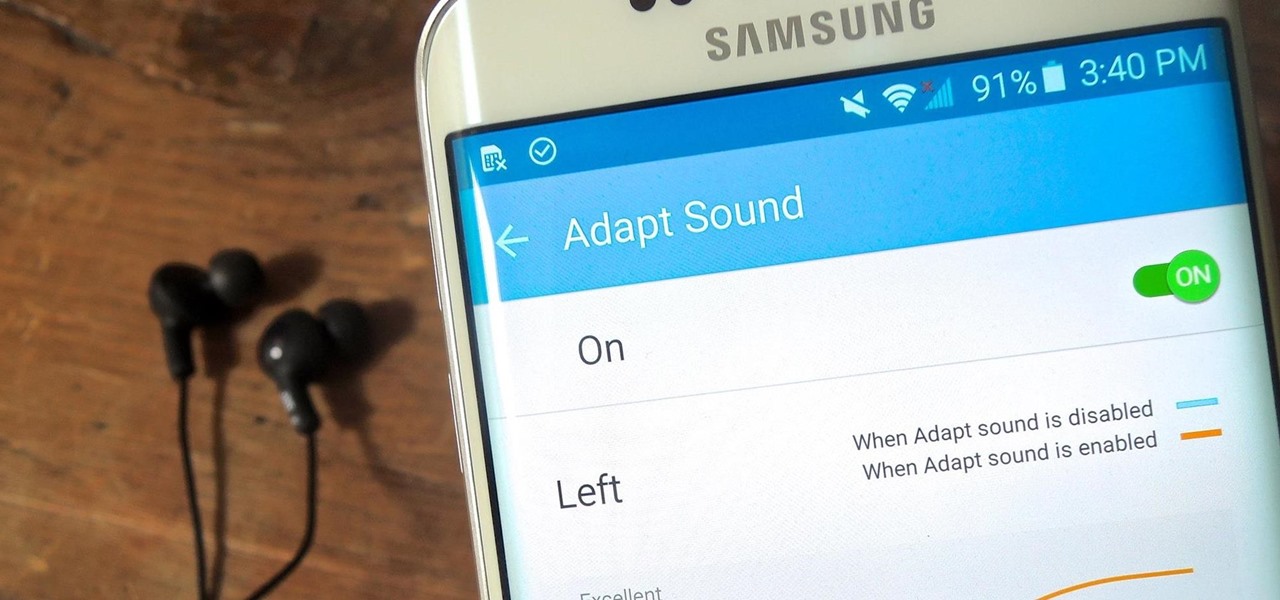
Chances are your hearing isn't the same as the person next to you. Personally, I have moderate hearing loss, so I tend to turn the volume nob towards the loud side. For others, it may be that one ear is slightly better or worse than the other, not only in perceiving volume, but tone as well. Considering this, is it possible for smartphone manufacturers to ensure the best sound quality on their devices?

With wearable tech becoming the latest trend in electronics, it's a shame that most smartwatches are locked down to one ecosystem. If you purchase a smartwatch, you can expect that it will not work with devices from competing manufacturers. That will be the case for the Apple Watch when the product finally hits shelves, and it has been the case for Android Wear devices like the Moto 360 for quite some time now.

Essentially, the Anti-Griddle does exactly what its name promises: it turns things almost instantaneously cold when you drop them on its "grilling" surface. Unlike home methods of flash freezing, its staggeringly low temperatures (-30°F/-34.4°C) allows ingredients that normally can't be frozen—like oil or alcohol—to turn into solids in the wink of an eye. As you might imagine, this allows chefs to play with textures and tastes in a way that was previously unimaginable.

The prevalence of smartphones has had profound effects on how we communicate, view media, and preserve memories, among other things. But all of these new forms of doing things are snatched away from us as soon as our phones lose power. While work is constantly being done to stretch and extend battery life, it hasn't moved fast enough for the vast majority of us.

Lollipop's imminent release should be cause for excitement with Google bringing out new features, a huge redesign, and under-the-hood changes. Unfortunately, the Nexus line of devices will be the first to receive the Android 5.0 update, leaving the rest of us to wait on manufacturers and carriers to release their skinned, bloatware-packed builds.

By now, Samsung's Multi-Window Mode is a pretty well-known feature. With other manufacturers now recreating this functionality in their own flagships, like LG, it's safe to say the feature has been a hit with consumers.

While the legality of recording phone conversations varies from state to state, it's still a sought-after feature for most people. How else are we going to shame all of those bad Comcast customer service reps? Since it's a legal gray area, HTC and other smartphone manufacturers have omitted call recording capabilities from their devices.

Screenshots are all the rage. From sharing high game scores with friends to placing conversation threads online for the world to see to secretly capturing Snapchats, this function of smartphones is prevalent through modern society.

Electronic devices seem to have an uncanny ability to make noise at the worst possible times. It's always during an important meeting, a quiet study session at the library, or a biology final that your laptop or smartphone decides to play some obnoxious or embarrassing sound.

Samsung bucked the trend and threw hard keys onto the Galaxy S3 while most manufacturers are going the soft key route. This hack will add on-screen buttons to your TouchWiz-based ROM. You'll need a root file manager with a system writable text editor—I recommend ES File Explorer for this, but feel free to use whatever you want. If using ES, hit Menu, Settings, go down to Root Settings, and check Root Exploerer, Up to Root, and Mount File System.

Planning on getting the iPhone 5, but want to keep your SIM card? The new nano-SIMs that manufacturers are adopting will be even smaller than the micro-SIMs that most of us currently use. It's fairly easy to cut a regular SIM down to a micro-SIM, but because the nano-SIM will be thinner as well as smaller than the micro, cutting it down to size will require a little more work. Photo by Tech Digest

Windows users have been getting a lot of bad news about their security lately. First, we found out that passwords in Windows 7 and 8 can easily be exploited if password hints are enabled, and now, Russian password-cracking software developer Elcomsoft has found another huge vulnerability.

Some of us use our smartphones for almost everything. Manufacturers know this, so they try to make their devices as convenient as possible to use, but sometimes that convenience comes with a cost to security. The very same technology that allows you to easily share music with friends and make purchases can also put you at risk. Photo by sam_churchill

Apple's Find My app just got way more useful. While it's great for locating a lost or stolen iPad, iPhone, iPod Touch, Apple Watch, Mac, and AirPods, as well as anything attached to an AirTag tracker, it's even better now that it works with third-party accessories and gear.

If you want to get started sniffing Wi-Fi networks, you usually need to start with a wireless network adapter. But thanks to a Wi-Fi sniffing library written in Arduino and the ultra-cheap ESP8266 chip, you might not need one. For less than $10 in electronics, you can build a tiny Arduino Wi-Fi sniffer that saves Wireshark-compatible PCAP files and fits anywhere.

To hack a Wi-Fi network, you need your wireless card to support monitor mode and packet injection. Not all wireless cards can do this, but you can quickly test one you already own for compatibility, and you can verify that the chipset inside an adapter you're thinking of purchasing will work for Wi-Fi hacking.

Design flaws in many routers can allow hackers to steal Wi-Fi credentials, even if WPA or WPA2 encryption is used with a strong password. While this tactic used to take up to 8 hours, the newer WPS Pixie-Dust attack can crack networks in seconds. To do this, a modern wireless attack framework called Airgeddon is used to find vulnerable networks, and then Bully is used to crack them.

Your home has walls for privacy, but Wi-Fi signals passing through them and can be detected up to a mile away with a directional Wi-Fi antenna and a direct line of sight. An amazing amount of information can be learned from this data, including when residents come and go, the manufacturer of all nearby wireless devices, and what on the network is in use at any given time.

When shopping for a new smartphone, you'll encounter comparisons and spec sheets that are filled to the brim with values like mAh, GB, and GHz. To the average consumer, however, these values are meaningless, so we end up looking at which device has the specs with the highest actual numbers.

There's a little-known secret in the world of microwave ovens that even the manufacturers don't care to tell you in their manuals. And once you know it, you'll never go back to using your microwave as you used to.

Following its dominance as a provider of silicon for smartphones, Qualcomm is eager to replicate that ubiquity with not only processors for augmented reality headsets but also reference designs to give device makers a head start.

The company that supplied some of the technology behind the Star Wars Jedi Challenges AR playset now has its own headset to offer.