Welcome back, reader! In this tutorial, we will be covering our first program! So let's get to it. We all know the unspoken tradition of the first program when learning a language and of course, here we will respect and complete it. Fire up your favorite text editor (be it vim, emacs, gedit, it's all the same to me, no h8) and try to keep up.

Sony Corp. is working on new battery technology that the company says would have a 40% longer life than a lithium-ion battery of the same size. Sony is planning to have the higher-capacity batteries on the market around 2020.

Yes, the Indian wedding season is just around the corner, and I am going crazy with excitement! Check this super easy Indian Wedding Nails by superwowstyle for Bindi nail designs. And do not worry, this is totally a No Tools Nail Art, and perfectly easy for even those who are not used to doing their nails!

Those of you who have been a part of the Null Byte community for even a short while know that I sincerely and firmly believe that hacking is the most important skill set of the future.

Here's a great little video from a recent trip to Portugal (the Algarve) cooking some huge prawns over coals on the grill.

Due to recent conflicts, I feel the urge to post this, in hopes that some of you will feel less hatred towards newbies, or a more respectable name, beginners.

Flowers may be beautiful, but they're not usually appetizing. Sure, nasturtiums are hip in fancy restaurants, but they're primarily used as a garnish. Granted, fried squash blossoms are incredible, but the point remains: flowers are usually reserved for looking at, not masticating.

Fiddlehead ferns look like something from Alice in Wonderland, or something that you might see when you close your eyes while listening to Pink Floyd and enjoying some herbal refreshment. What they don't look like is a tasty vegetable that's perfect for any spring or summer dish. Yet that is exactly what these bizarre spirals are. What Are They?

With each day that dawns, there is a new, major hack that makes the news headlines. If you are paying attention, there are usually numerous hacks each day and far more that never make the news or are kept private by the victims. Every so often, a hack is so important that I feel compelled to comment on it here to help us learn something about the nature of hacking and IT security. This is one of those cases. Last week, the U.S. Office of Personnel Management (OPM) revealed that they had been ...

Welcome back, my tenderfoot hackers! Now that we have begun this trip down web app hacking lane, we need to first address target reconnaissance. Like any hack, reconnaissance is critical. (Are you tired of me saying that yet?)

For $35, there's hardly a better value in the online media player market than the Chromecast. Taking that sentiment a step further, if you factor in the promotions Google likes to offer with it, Chromecast practically pays for itself.

Essay writing is the bane of most students' educational existence. Whether you're a college student tired of slaving away over 30-plus page research papers or a high school student just trying to get through AP Language, chances are you'd love to find a way to cut down on all the writing. Before you spend hours googling facts and figures to cram into your next paper, work smarter by cutting down on content.

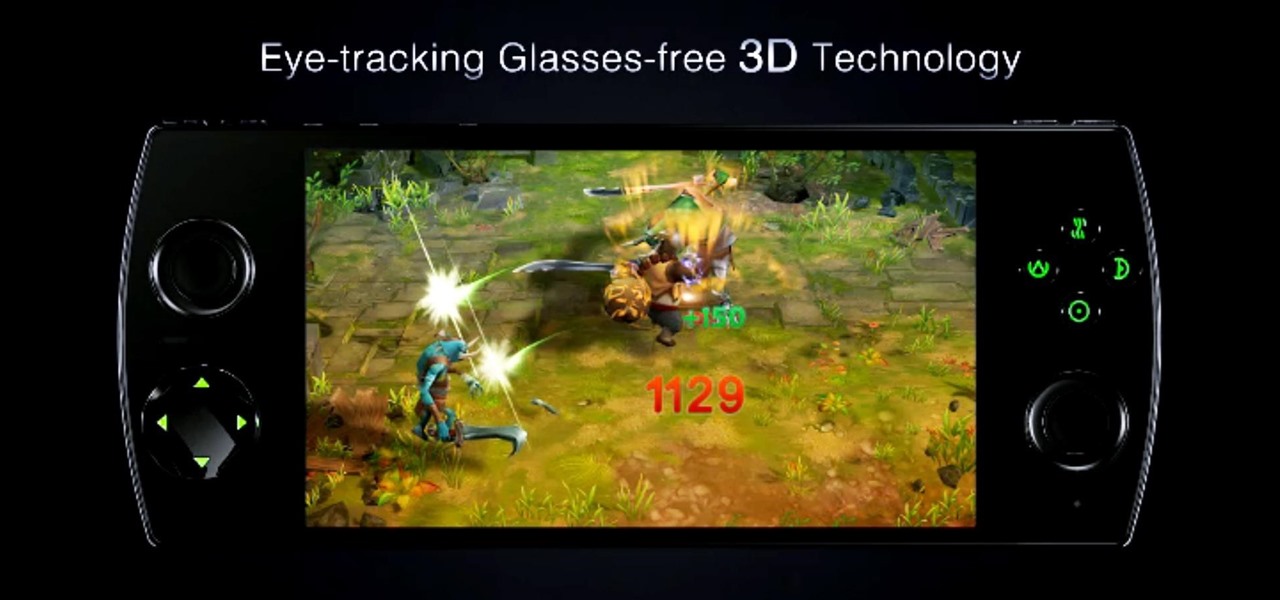
The upcoming W3D gaming smartphone by Snail isn't like anything you've ever seen before. It's pretty much a cross between an Android phone, Nintendo 3DS, and PlayStation Vita. It runs on Android, has a 3D screen similar to the 3DS, and gamepad controls like the Vita, making it one hell of a portable gaming device (that's also a phone).

Sometimes it's not the look of a product that makes it unique, but the thought that went into it. That's what struck me about TobyRich's SmartPlane—it isn't the most elegant toy on the market, but its simplicity and function make it a winner.

Tuesday has long been considered the best day to save money on a plane ticket. Airlines typically announce new deals on Monday, so by Tuesday, all other airlines have matched their competitor's lowest fares. It's a tip that I learned at a young age from my father and was solidified by countless others who swore by it. Well, it turns out that we were all wrong.

I may not be a well-traveled man, but one thing I've learned from my few excursions across the world is that currency exchange rates are a serious pain to keep up with. With global markets seemingly in a continuous flux, I started looking for anything to make staying on top of them easier, and thats when I found Price Helper.

With the release of the iPhone 6 Plus, comparisons to the Samsung Galaxy Note series have been circulating like crazy, and it's only natural. The Note was panned as an oversized gimmick when it was released, but after its enormous success, Apple caved and built their own "phablet," something that Samsung took little time to call them out on.

Welcome back, my tenderfoot hackers! As you know, DNS, or Domain Name System, is critical to the operation of the Internet. It provides us with the ability to type in domain names such as www.wonderhowto.com rather than the IP address. This simple service saves us from having to memorize thousands of our favorite website IP addresses. Instead, we simply type in a domain name to retrieve the website.

There are a gazillion app switchers on the market, and some are really awesome, like Edge, GloveBox, Loopr, and Switchr, to name just a few. However, these can all be a little bit more complicated and cumbersome than necessary when I just want to switch back to the last app I was in.

Welcome back, my tenderfoot hackers! In continuing my series on digital forensics using Kali, I want to introduce you to two complementary tools, both built right into Kali Linux. These are Brian Carrier's tools Autopsy and Sleuth Kit.

With just a swipe and tap of a finger, we can access enormous libraries of information on our smartphones like never before. Whether we want more info about gluten sensitivity or just want to brush up on 18th century philosophers, there's an article somewhere in the vast ocean of the internet that can lend us a hand.

Last year, The New York Times wrote that certain restaurants in Manhattan and Brooklyn banned patrons from taking photos of their meals. That means no flash photography, no standing on chairs for a better angle, not even a quick pic for your Instagram followers before the first bite. Little do these restaurants know, this ban can actually make their customers' food taste worse, so to speak.

Think eating food is as easy as putting it in your mouth? It's considerably more complicated than that. Your brain plays a big role in determining what and how you eat. Understanding how your brain interprets food choices is key to managing your eating habits.

Just in case you weren't aware, Google has more money than you and I will probably ever see in our lifetime, and now it seems that the search giant will be spending that money sending satellites into space.

One of the down-sides of international long-haul travel is layovers between flights in unfamiliar places. We have a flight to Europe this year via Guangzhou, China, and I've been putting together my notes on how to make the best use of 7 hours between flights, which I'd like to share.

Welcome back, my novice hackers! I have tried to emphasize throughout this "Hack Like a Pro" series that good reconnaissance is critical to effective hacking. As you have seen in many of these hacks, the techniques that we use are VERY specific to the:

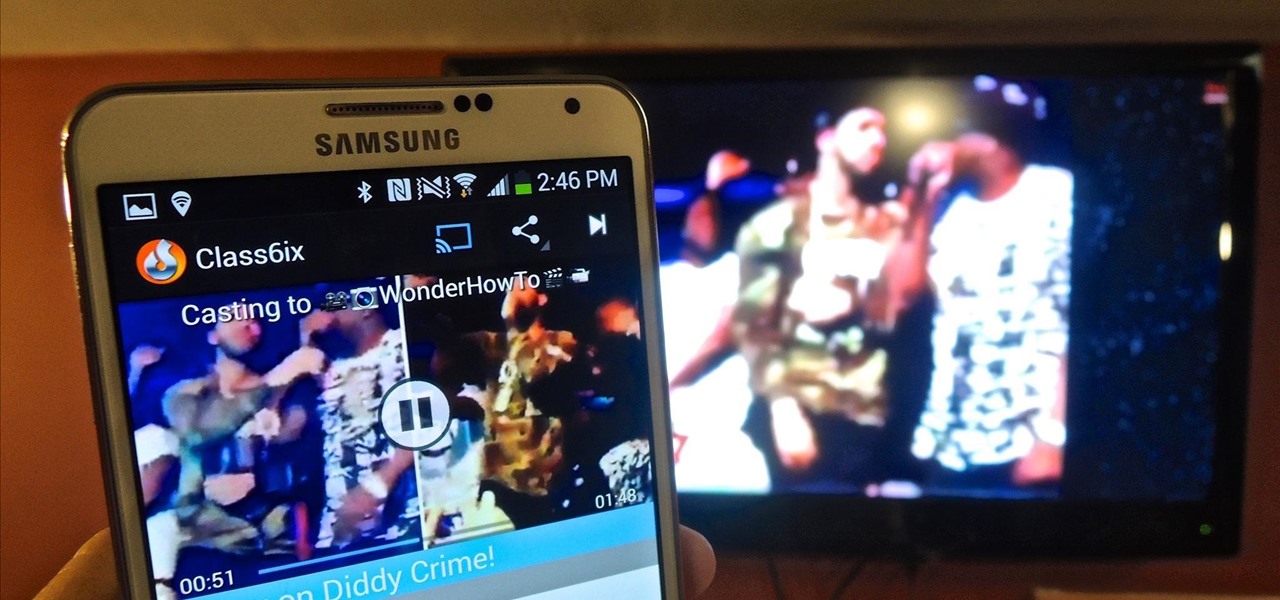
With Chromecast-capable applications slowly seeping into the market, it's difficult to find useful ones that we might use on a daily basis.

The original Kit Kat was a mutton pie served at a political club in London during the 18th century, which is quite different than the chocolatey version we're familiar with today. Kit Kat bars have been around since 1911, are produced in 13 countries, and have been sold in over 200 flavors in Japan.

The Xperia Z1, Sony's flagship device, has been extremely popular overseas, so much so that it has made its way into the U.S. market as the Xperia Z1S, a modified version of the original. Known more commonly as the "waterproof smartphone," the Xperia Z1 packs one of the most powerful cameras on the market, with an impressive 20.7 megapixels. Since the device is only available for T-Mobile here in the States, unless you currently have that carrier, the chances of you getting your hands on Sony...

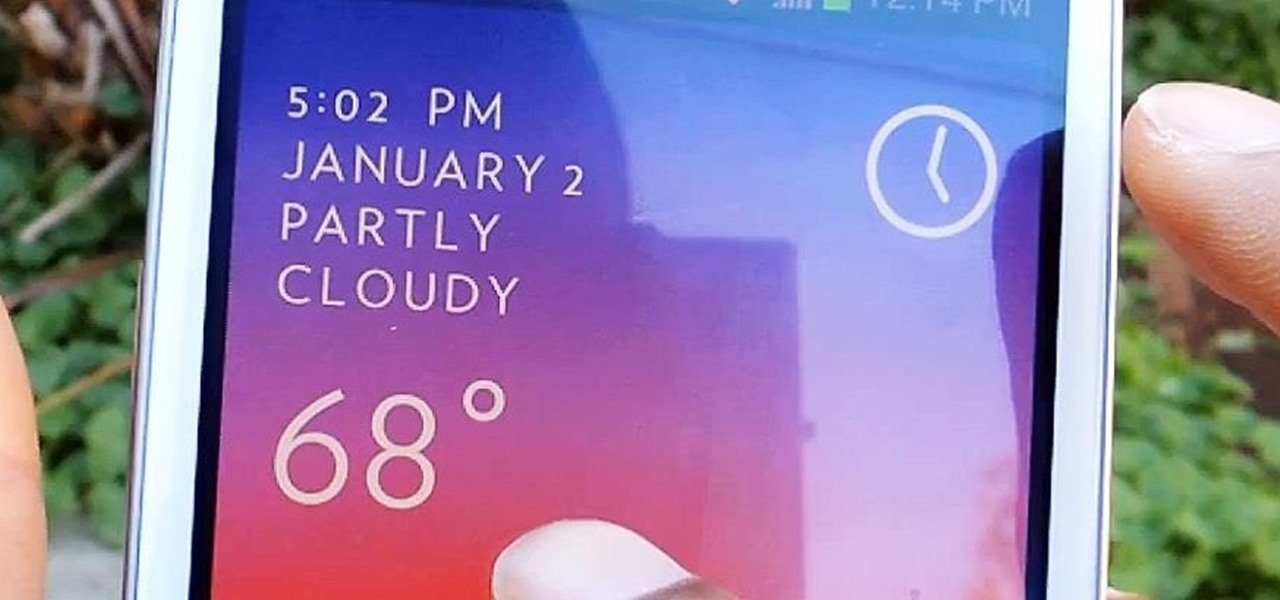
Living in Los Angeles so long has perhaps spoiled me a bit. The only time I check my weather apps is to send screenshots of my 70 degree Decembers to my friends in Chicago and New York. So for these bragging occasions, I like to have a good looking app.

Welcome back, my rookie hackers! The more we know about a system or network, the better our chances of owning it and not leaving a trace for investigators to follow. One of the often overlooked sources for information is the Simple Network Management Protocol (SNMP). Many rookie hackers are not even aware of it, but it can prove to be a treasure trove of information, if you understand how it works and how to hack it.

One of the biggest problems in data security is authentication of data and its source. How can Alice be certain that the executable in her inbox is from the venerable Bob, and not from the not-so-venerable Oscar? Clearly Alice wants to know because if this file is actually sent to her by Oscar, the file might not be a game, but a trojan that can do anything on her computer such as sift through her email and passwords, upload her honeymoon pictures, or even turn on microphones and webcams. Thi...
There has been much talk about how unsecure the cloud is because of PRISM’s newfound ability to demand all of your data without any resistance. This has spin doctors in the Cloud Storage industry losing their mind. They suddenly went from a central hub for 10GB of your files, to an easy window for Big Brother to track you through. Centralized cloud storage is no longer a safe way to keep your files, but we still need a way to access our files anywhere we go.

Welcome back, my nascent Hackers! In my last blog, we looked at a passive way to gather information necessary for a hack. The advantage of using passive recon is that it's totally undetectable, meaning that the target never knows you're scouting them and you leave no tracks. The disadvantage, of course, is that it's limited to only some websites and not entirely reliable.

According to WitsView, 8-inch displays will rule the tablet scene this year at 11.9% market share, compared to yesteryear's 2.6% market share. By year's end, it'll be almost 18%.

If you pre-ordered your Samsung Galaxy S4, it might very well be possible that you're reading this on your brand spanking new Android device. As is commonplace with the release of popular smartphones, rooting instructions are usually released simultaneously. I mean, what's the point of paying so much for an expensive phone if you can't have a little fun? Android developer Dan Rosenberg (aka djrbliss) recently announced that you can root your Samsung Galaxy S4 using the root exploit he origina...

Newsletters, subscriptions, and receipts are all necessary evils that come along with online services and shopping, and they take up a significant amount of space in a lot of people's inboxes. If you've ever signed up for an account on a website, chances are you've gotten an email from them.

While the phenomena of viral videos and internet celebrities are relatively new, it seems like there's a new one every other day. Sometimes they're funny, other times they have a social mission, like Kony 2012, and sometimes they're just videos of cats jumping in boxes.