Apple's line of iPhones, iPads, and iPods are of some of the most advanced devices available on the market. Usually, the biggest complaint is that they are not customizable, but they can be if you exploit a few bugs in the system.

How many of us actually drink enough water? It's one of the easiest ways to improve your health, but most people don't get nearly as much as they should. We've grown so accustomed to soda, coffee, and sugary juices that water just seems bland by comparison. That's why drinks like VitaminWater are so popular. They're marketed as being just like water, but better tasting and with even more vitamins, minerals, electrolytes, and antioxidants. Who wouldn't want all the benefits of drinking water a...
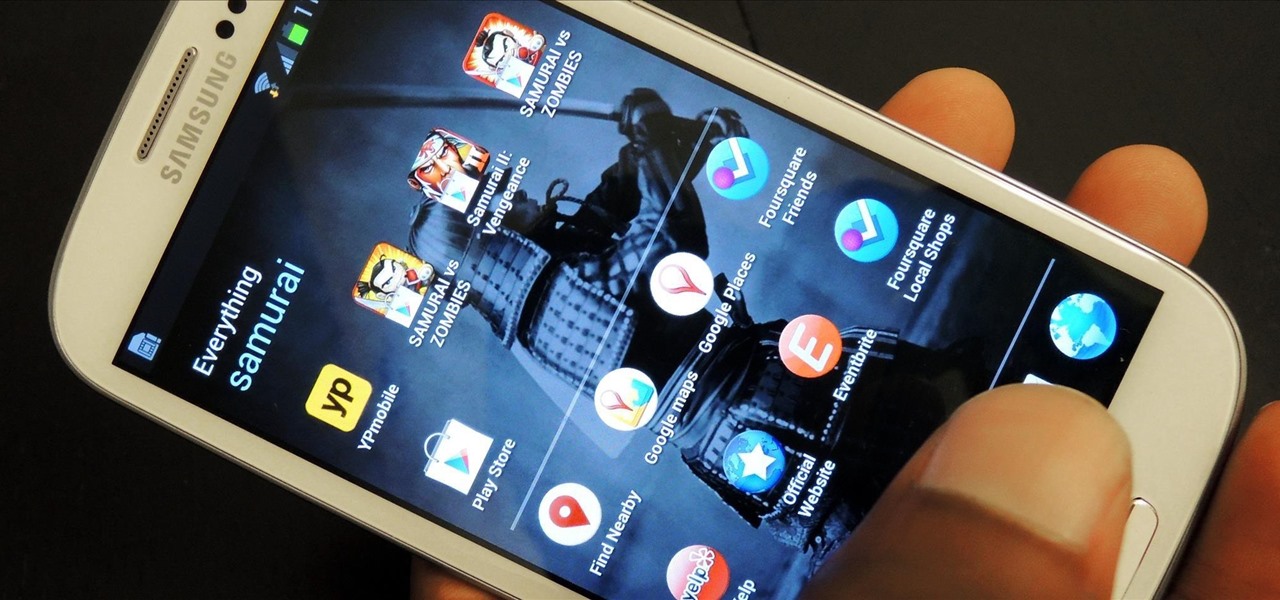
There's no shortage of cool customizations for my Samsung Galaxy S3, except when it comes to the launcher. Sure, there a ton of Android launchers out there, like Nova Launcher or Apex Launcher, that allow you to customize app placement, app grouping, infinite scrolling, etc. There's even Facebook Home for those who are Facebook addicts.

Samsung is currently dominating the Android market with their line of Galaxy devices, including the GS3, GS4, Note 2, and Tabs. All of these devices run Samsung's TouchWiz, which is something every softModder should try out eventually. The only thing is that Samsung devices are pretty expensive, and many of you don't actually need (or want) another Android tablet.

Don't always believe the marketing hype. "PlayStation Certified" does not mean anything to a softModder. All this indicates is that a smartphone or tablet labeled as "PlayStation Certified" has met the guidelines and hardware requirements issued by Sony to display PlayStation Mobile (PSM) content from the PlayStation Mobile Store correctly. No Nexus 7 here.

Over the past several weeks, I’ve had the pleasure of test driving Samsung’s next big thing, the Galaxy S4. After putting the GS4 through its paces, I have a clear picture of what this device is capable of. I’ve covered the features of the device before, and now I’ll tell you why I believe it's currently the best Android phone on the market. Initial Impressions

In a previous article, I pointed out a few criticisms of the Google Play Store, mostly about how unpolished and inefficient it is. To give you a better idea of what I mean, here are just a few of my complaints with the Play Store:

Samsung unveiled their new flagship device, the Galaxy S4, at a live event in New York City today. Here's a quick rundown of the specs and all of the new features that you can expect when you finally get your hands on one (whenever that will be). The GS4's Specs

We frequently associate plastics with the modern era, starting at around the 1950s with the prevalence of bakelite. However, for all of you "you can't use plastic in Steampunk" purists out there, I have bad news for you:

SNAP. That's the sound of your Samsung Galaxy S3's camera going off. Not that big of deal, unless you're trying to take some top secret pics or some candid shots of your friends. The shutter sound gives you away, and the next thing you know, you're deleting pictures. On most other smartphones, if the users turns the phone on silent or vibrate, the shutter sound is killed. If that doesn't do the trick, usually muting the shutter sound itself in the settings will do the trick. But for some of y...

Winter is coming... and if you don't get that Game of Thrones reference, it's okay, you're still cool in my book.

For the first time in history, Apple has decided to scrap the dock for its new iPhone release. As if the maps fiasco wasn't enough, users took to the web to complain not only about the dock ordeal, but why Apple decided to make it obsolete. 9to5mac first posted about a concerned iPhone user who decided to email Phil Schiller, Apple Senior VP of Marketing, to ask why there were no docks included in the iPhone 5 package. Schiller replied with,"We do not plan on making a dock for the iPhone 5. M...

Getting a new phone is like getting a pair of new socks—you can't wait to try them on and when you do, they feel totally awesome. Maybe that's just me, but for many customers that have already received their highly anticipated iPhone 5 in the mail, awesome is definitely not the word they are using.

This may seem like an odd subject, because what do Steampunks and iPhones even have to do with each other? Actually, more than you might think!

It can be extremely frustrating when you've forgotten the pattern you use to lock your smartphone, and even more so if someone has managed to prank you by changing it. Luckily, there's an easy fix if you know the username and password for the Gmail account you used to set up the lock.
(Series designed to help explore whether your ideal employment ideas should be formalized into a business venture or as an employee or volunteer value added problem solver).

Everyone who owns or runs a website needs to know how they can improve traffic, and search engine optimization is the answer. This 13-part video series on SEO basics and strategies will give you more traffic for your site. It's jam-packed full of tons of great SEO tips! Check out each video in the series:

This is a Halo Interactive Strategy Game 'Tabletop' tutorial. We've seen this before. It's like Warhammer, but for Halo. With an accompanying DVD that's more Nightmare than Bungie. So, is this a good idea? With Halo Wars on the way and better board games on the market we'd have to say no, but then, who are we to tell hardcore Halo fans what they can and can't blow their money on.

The Samsung Tocco, also known as F480 is the first in a series of capacitive touchscreen phones hitting the market this year. The Tocco features a new and unique TOUCHWIZ UI replacing the Croix UI. The 5-megapixel camera featuring auto focus and a CMOS video lens; are normally only found in high-end or prosumer DSLR cameras. So it’s an amazing feature to have on a phone, especially when the Tocco only measures 11.6 mm thick by 98.4 mm tall and 55 mm wide. In addition to CMOS, the F480 also fe...

One of the best recent outings in the Marvel universe is the animated series What If...?, which explores alternate universe takes on various superhero storylines that deliver fascinating scenarios if one single factor had been different in the story.

It's already been a banner year for mergers and acquisitions in the augmented reality industry, with WaveOptics and Ubiquity6 among the notable companies acquired. Two of the more active M&A players, Snap and Epic Games, continued their respective buying sprees this week with major deals supporting their AR strategies.

Over the past few weeks, Google, Snap, and Facebook have all taken their turns to show off their new augmented reality technologies. This week, it was Apple's turn, with new AR features for iOS 15 along with new capabilities for developers.

Apple just released iOS 14.4.1 for iPhone today, Monday, Mar. 8. The event marks 41 days since Apple released a public update for iPhones, with iOS 14.4 back on Jan. 26.

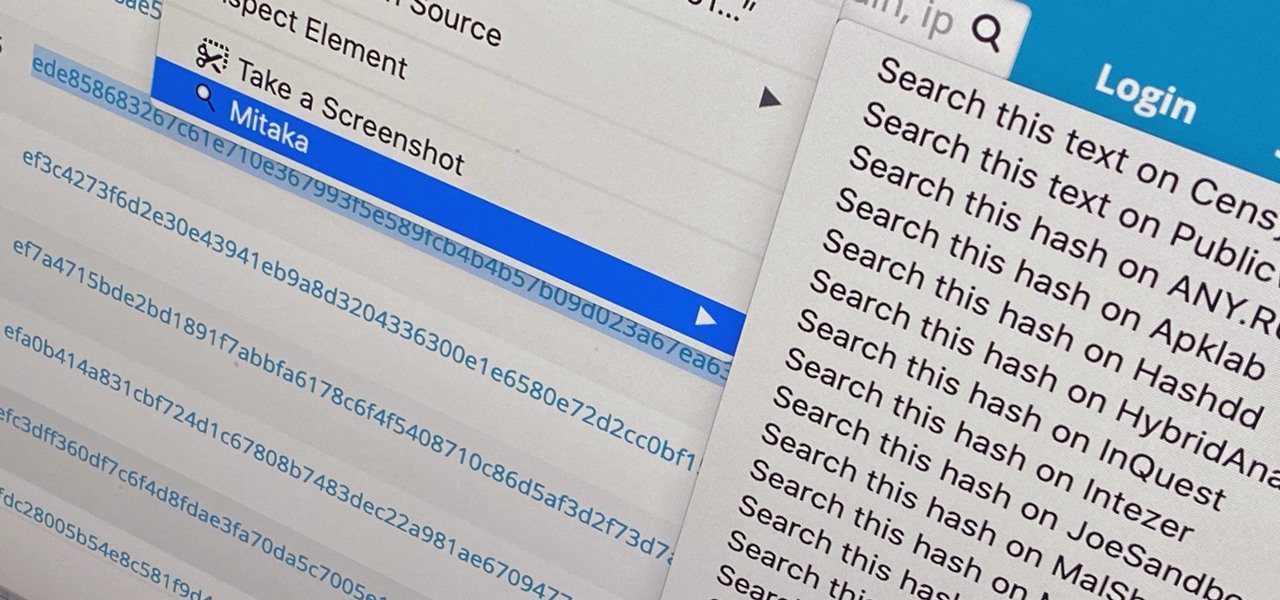
Web browser extensions are one of the simplest ways to get starting using open-source intelligence tools because they're cross-platform. So anyone using Chrome on Linux, macOS, and Windows can use them all the same. The same goes for Firefox. One desktop browser add-on, in particular, makes OSINT as easy as right-clicking to search for hashes, email addresses, and URLs.

The majority of us have been shown, again and again, that we want our own business. Business software is making this a reality by automating and simplifying the complex parts of running any company.

It's safe to say that we can call the annual ranking of AR investments a holiday tradition at Next Reality.

You may not have thought of dorks as powerful, but with the right dorks, you can hack devices just by Googling the password to log in. Because Google is fantastic at indexing everything connected to the internet, it's possible to find files that are exposed accidentally and contain critical information for anyone to see.

The landscape of the augmented reality space is broad, diverse, and constantly shifting, perhaps more so than any other vertical in technology. At the same time, major players are attempting to standardize various hardware designs and delivery methods, while still others are rushing to claim their piece of virtual property through AR clouds and application stores.

By using almost any packet-crafting tool, a hacker can perform denial-of-service (DoS) attacks. With the power to create just about any packet with any characteristics, a hacker can easily find one that will take down a host or network. Nmap and Hping are effective packet manipulation tools, but there's also Scapy, which is almost infinitely customizable.

Complex shell scripts can be implanted into photo metadata and later used to exploit a MacBook. In addition to obfuscating the true nature of an attack, this technique can be used to evade network firewalls as well as vigilant sysadmins.

Before attacking any website, a hacker or penetration tester will first compile a list of target surfaces. After they've used some good recon and found the right places to point their scope at, they'll use a web server scanning tool such as Nikto for hunting down vulnerabilities that could be potential attack vectors.

The year 2018 was a rough one for Snap, the company behind the Snapchat app and the Spectacles wearable camera device. From executive departures to reports of slowed user growth, the company that once spurned Facebook's multibillion-dollar advances is now facing a moment of truth as it stares down its uncertain future.

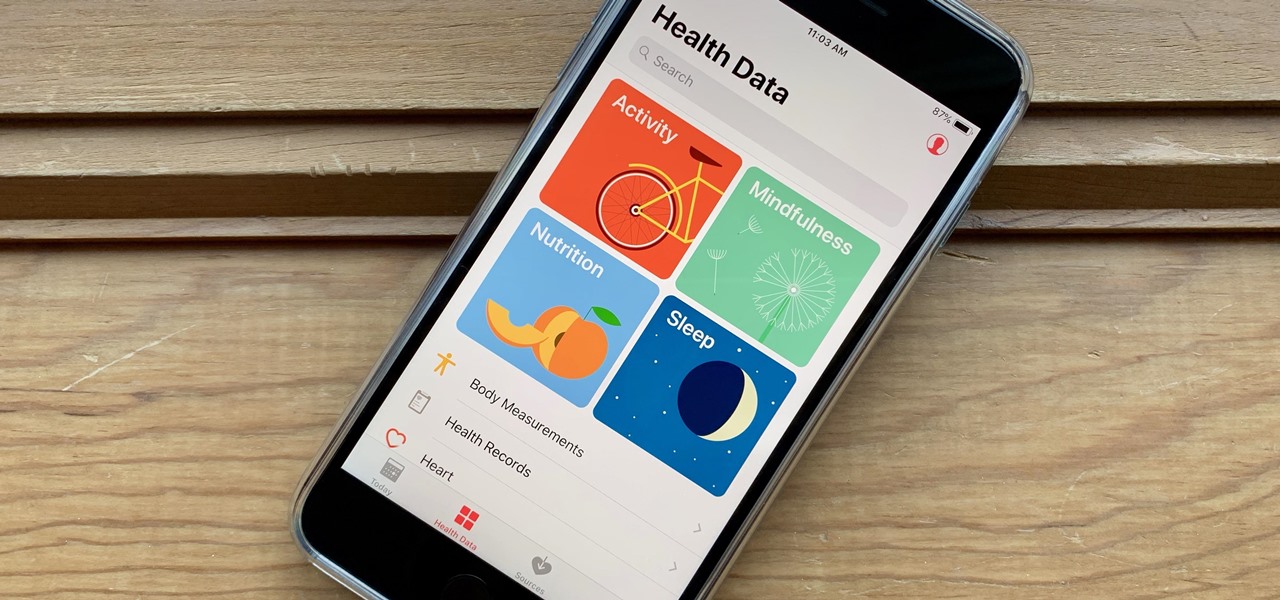
It's not easy staying fit and healthy these days with addicting phones, oversized portions, and long workdays, to name just a few things. To succeed, it takes work, commitment, and an understanding of your mind and body — and your iPhone can help you with some of that. While Apple pushed its Screen Time tool to help curb unhealthy smartphone habits, its "Health" app can help with everything else.

Whether it's for health reasons or just to look better, many of us want to get in shape. It's a long process that starts with nutrition, and dieting is never easy. Fortunately, there are some great food-tracking apps that will make it a lot easier to become a healthier version of yourself.

While keeping your iPhone out of the bedroom might help to avoid unnecessary distractions before bedtime, it could be better served right by your side to help diagnose sleeping issues you may be experiencing each night.

Ever since the announcement of the Razer Phone, a wave of gaming smartphones started to hit the market. With ASUS being such a big name in gaming, it made sense for them to throw their hat in the ring. The result is the ROG Phone. And with this first try, ASUS has topped the rest, creating a gaming phone others should try to emulate.

For anyone using open source information to conduct an investigation, a balance between powerful tools and privacy controls are a must. Buscador is a virtual machine packed full of useful OSINT tools and streamlined for online research. This program can easily be set up in VirtualBox, and once that's done, we'll walk you through some of the most useful tools included in it.

Kali Linux, by default, probably doesn't have everything you need to get you through day-to-day penetration testing with ease. With a few tips, tricks, and applications, we can quickly get started using Kali like a professional white hat.

Don't think because your MacBook is using FileVault disk encryption your device is secure or immune to hackers. Here's how to find out if that FileVault password is strong enough to withstand an attack from a motivated attacker.

As you're surely aware, your phone can be used against you. Thanks to our cameras and microphones, a clever hacker can obtain access to your device and invade your privacy. But spying isn't limited to just these two sensors — gyroscopes, proximity sensors, QR codes, and even ads can be used to paint a very clear picture about who you are and what you're currently doing.