To name just a few companies, VK, µTorrent, and ClixSense all suffered significant data breaches at some point in the past. The leaked password databases from those and other online sites can be used to understand better how human-passwords are created and increase a hacker's success when performing brute-force attacks.

The war on dehydration is a commercially burgeoning marketplace. An increasingly sophisticated consumer population hoping to conquer everything from 26-mile marathons to vodka shots is deconstructing every functional remedy in the fight to quell the effects of severe dehydration.

For almost a decade, projector phones have tried to entice consumers with their convenience as media machines. While these devices are alluring, they've never really taken off with mainstream success. The latest effort, Moviphone, sounds tempting if you watch a lot of films and TV on your smartphone, but is it good enough to be your daily driver?

In October of 2017, Mathy Vanhoef released "Key Reinstallation Attacks: Forcing Nonce Reuse in WPA2." This paper demonstrates a way to decrypt traffic on practically any WPA2 network, the most commonly used form of wireless security (seeing as all other forms of Wi-Fi encryption have already been broken). Practically all of the network-connected devices we use will need to be updated in some way in order to protect against this vulnerability, each of them in a different way.

Tossing an old Android smartphone with a decent battery into your hacking kit can let you quickly map hundreds of vulnerable networks in your area just by walking or driving by them. The practice of wardriving uses a Wi-Fi network card and GPS receiver to stealthily discover and record the location and settings of any nearby routers, and your phone allows you to easily discover those with security issues.

Throughout this NR50 series, we have talked about the incredible growth the augmented and mixed reality space has seen in the last year. More devices, software, developers, and use-cases seem to arrive daily. For this growth to have occurred, it took the work of many people, from many different backgrounds and skill sets — and Next Reality wants to recognize them for all that they have done and are doing.

It looks like Chris Urmson has spent the six months since he left Google's Self Driving Car Project trying to build a get-rich-quick self-driving unicorn, along with Sterling Anderson, formerly with Tesla Motors. At least that is one of several scandalous accusations in a Tesla lawsuit aimed at the pair, and their secretive startup Aurora Innovation, LLC.

There are all kinds of theories—many supported by science—about what causes Alzheimer's disease. Tangles of protein called ß-amyloid (pronounced beta amyloid) plaques are prominently on the list of possible causes or, at least, contributors. An emerging theory of the disease suggests that those plaques aren't the problem, but are actually our brains' defenders. They show up to help fight an infection, and decades later, they become the problem.

The year was 1947. Scientists had isolated a virus from a pyrexial rhesus monkey in Uganda and named it after the forest where the monkey lived — Zika.

When you think of all the fun and games smartphones have to offer, it's easy to forget that they also make a great tool for getting things done. With utilities like document scanners, calendars, to-do lists, office apps, and password managers, that little computer you carry around in your pocket has the potential to increase your productivity levels in all aspects of life.

Hello people again, I wrote my last post about crypto about 10 months ago, now I will introduce something not fresh for the science, but fresh for the people who wants to learn. In my http://null-byte.wonderhowto.com/forum/cryptography-0161538/ post of crypto concepts, there is just basics, today we will see something that targets wide concepts like Symmetric crypto, Public Key Cryptography, Hashing, Keys etc...

Welcome back, my hacker novitiates! In the previous two posts in this series, we looked at the basics of buffer overflows. In this post, we will look at one technique for finding buffer overflows. We will try to send random, oversized, and invalid data at a variable to see whether we can make it crash or overflow. This process is known as fuzzing. It is often the first step to developing an exploit, as we need to find some variable that is susceptible to overflowing.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Welcome back, my greenhorn hackers, and happy New Year! Now that your heads have recovered from your New Year's Eve regaling, I'd like to grab your attention for just a moment to preview 2015 here at Null Byte. I hope you will add your comments as to what you would like to see, and I'll try to honor as many requests as I can.

There's a 2800mAh battery powering the Samsung Galaxy S5, but even it's no match for the constant day-to-day torture you put it through. Taking photos, watching videos, and playing games can make your fully charged S5 powerless in no time.

All kinds of people pretend to be someone they're not on the internet, including scammers, people attempting to wind others up, hackers and web predators. Almost all of these people will leave bases uncovered and they're all easy to expose when you understand how to. Here are my favorite ways of finding out when somebody is lying quickly. Image Search

It can be hard finding fellow singles in the suburbs but it can be done! Keep your eyes peeled and make sure you are out and about meeting new people in public settings. Don’t forget about your online or in print options.

Dyeing your hair is a great way to change your look. But if you don't do it right, the results can be pretty ghastly. If you seek a new do without the harsh chemicals, these steps will give you the locks you’ve been looking for.

A CNC router machine is probably the most useful tool a hobbyist can own, but the price for a CNC machine on the market is way more than the average hobbyist is willing to spend. You can build your own CNC with very basic tools, little knowledge of machinery, mechanics, or electronics, but be warned, these machines are inherently dangerous, so wear the proper protection and use common sense. At the very least, read the instructions and precautions on every tool you use.

Human life has been wiped out. Extinct for 20 years. Destroyed by a nuclear holocaust. But there are a few survivors on Earth, and they're forced to live in the underground metro systems in the big cities. But it gets worse. There's mutant beasts, communists, Nazi factions, and even psychic powered Dark Ones that endanger your lives every second. This is Metro 2033, and this walkthrough series from Mahalo will show you the entire gameplay on the Xbox 360. Can life really be like this in the M...

And then there was light…on your pen. Have a little fun and with a little ingenuity and a couple of matchsticks you can liven up any afternoon by pranking your friends with this magically burning pen.

You can learn to deal with the thing we all dread, a computer crash. Hopefully you diligently back up work but even if that's not case, stay calm. There is still hope and even if you're not a wiz at computers there are people out there who can help.

A CNC router machine is probably the most useful tool a hobbyist can own, but the price for a CNC machine on the market is way more than the average hobbyist is willing to spend. You can build your own CNC with very basic tools, little knowledge of machinery, mechanics, or electronics, but be warned, these machines are inherently dangerous, so wear the proper protection and use common sense. At the very least, read the instructions and precautions on every tool you use.

There are a few julienne peelers on the market, but how do they work. Watch this how to video for a quick demonstration on the proper or way to utilize a julienne peeler.

In this video series, our expert Tim Kimmel will show you ho to do a non-fiction book proposal. Mr. Kimmel will teach you how to write a title page, a table of contents, and a synopsis for a book proposal; all in the way the publishers like to receive them. Tim will also teach you how to write an author's bio, and tell you a bit about market strategy so you know your words are reaching the right ears.

One of the primary assumptions in the world of VR and augmented reality is that the user has the ability to "see" virtual objects and the real world structures around them. But what if the user doesn't have perfect eyesight, or any eyesight at all?

The practice of using sound to trigger augmented reality interactions hasn't been widely used, but a new experience is so impressive that it could kick off more use of the dynamic.

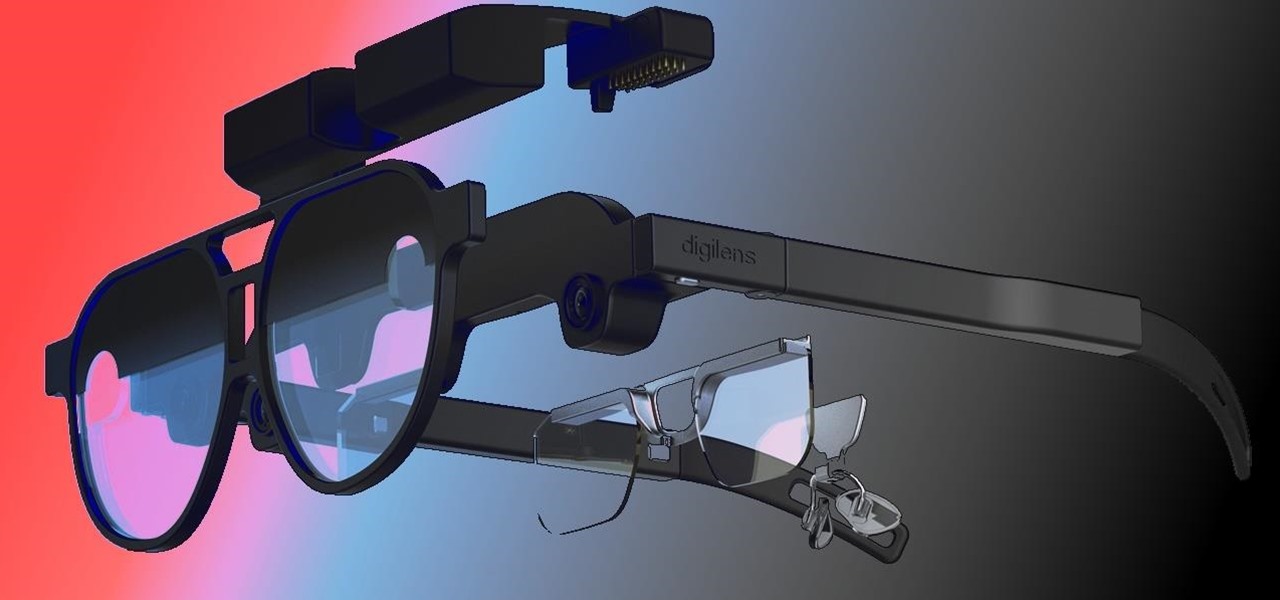
When it comes to the future of AR smartglasses, DigiLens has one word for you. Just one word. Are you listening? Plastics.

No, Jack Dorsey's Cash app isn't about to launch an augmented reality device (er, I don't think...), but its latest outing is about as close as we've come to full confirmation that the wearable AR age is upon us.

The march of Snap to become the world's augmented reality engine isn't slowing down. In a new deal announced on Thursday, Snap has revealed that it has signed an agreement to become the software driving Universal Music Group's (UMG) mobile AR music offerings.

The recent announcement that Facebook will begin inserting advertisements into its VR experience on its Oculus Quest headset has set the VR and augmented reality industry into a frenzy.

Project managers — and those hoping to become one — should rejoice at this killer deal. The Project Manager's Essential Certification Bundle Ft. Scrum, Agile & PMP usually runs for $1,990 but is only $49.99 for a limited time.

Apps went from a novelty to the main way we control the functionality of our phones and tablets in what felt like an instant. Apps are ubiquitous, and you can find one for virtually every need. However, what's right for someone else isn't always right for you, and what's right for you might be right for more people.

When you're working, in class, or just browsing the internet away from an outlet, the last thing you want is to string your devices along with a portable charger that can't recharge them as fast as you need. The Ultimate Charger: Portable Multi-Device Power Bank is exactly what it says it is — the ultimate portable charger that can power even a laptop at full speed, and it's on sale for $149.99 (it's normally $179.99).

Learning to code is difficult, particularly if you're doing it alone. While coding may be among the most valued job skills in many markets, the education is sometimes inaccessible.

Despite the unfortunate social media-driven association of Corona beer with the virus behind a global pandemic, beverage maker Constellation Brands has pushed its marketing forward like a lime through the mouth of a beer bottle.

The latest whispers about Apple's plans to launch its long-awaited (yet still unconfirmed) augmented reality device hits several familiar notes, but lands on a different refrain.

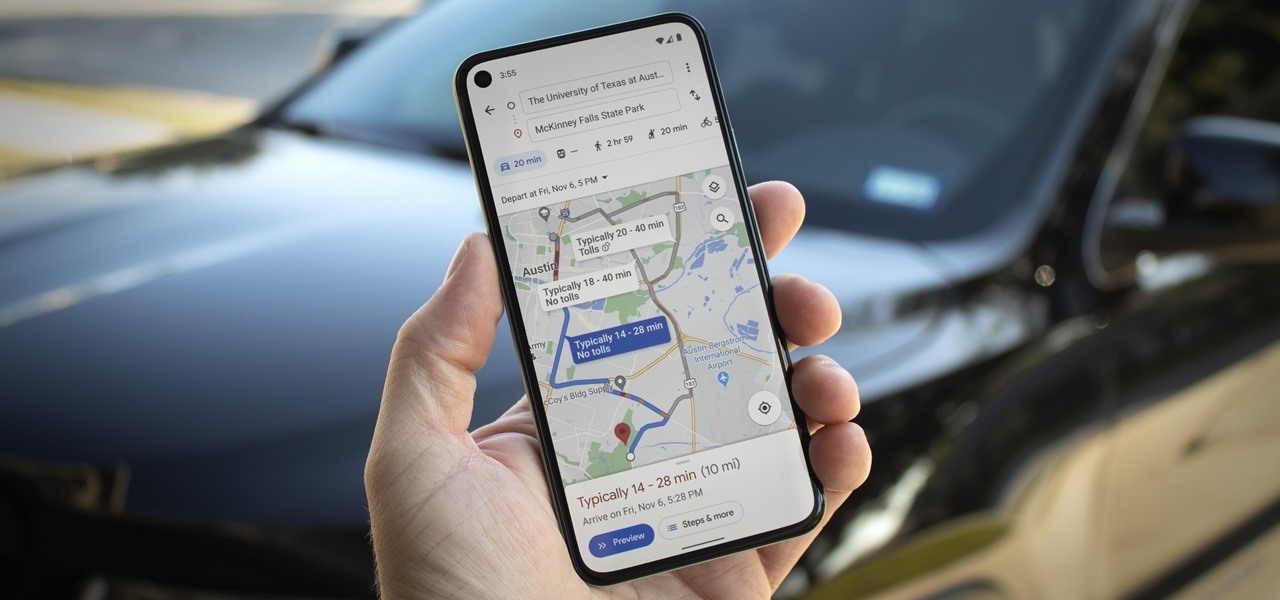
If you're in the market for a new house, how do you know what your commute would be like if current traffic is unseasonably low? Or if you're considering a new job across town and want to weigh the pay raise against the extra time stuck in a gridlock, how do you measure the discrepancy? Google Maps can help.

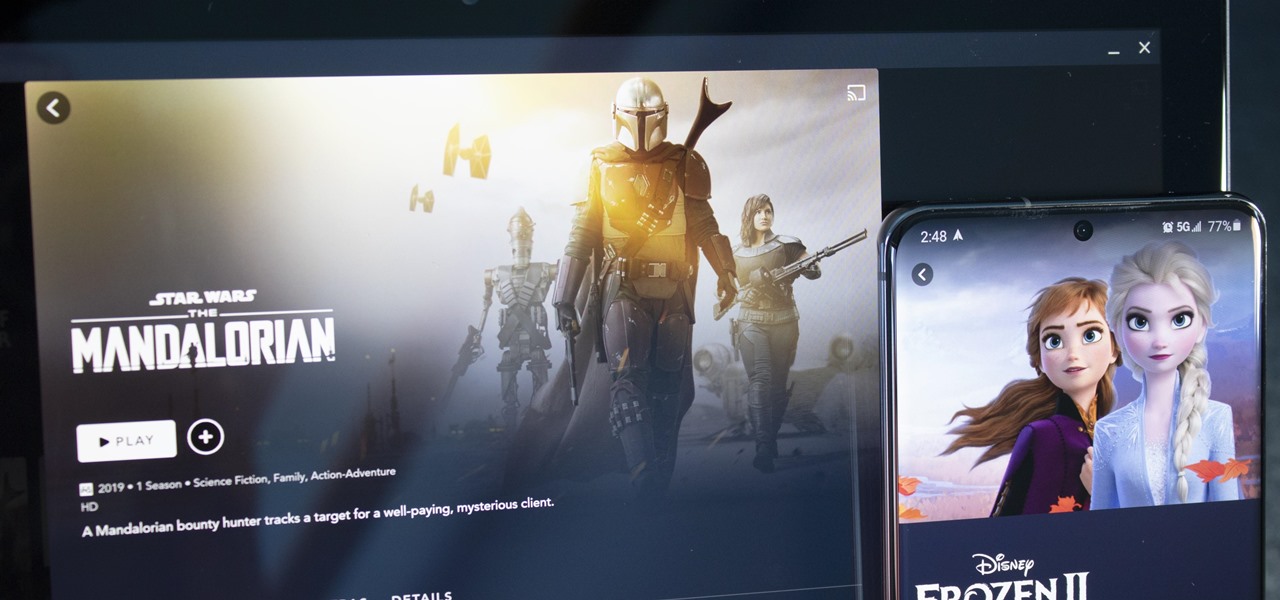
With shows like "The Mandalorian" and movies like "Frozen 2," Disney+ has quickly become a must-have streaming service. However, with Netflix, Amazon Prime Video, and Hulu, adding another subscription-based service can become expensive — but there are ways to trim down the cost.

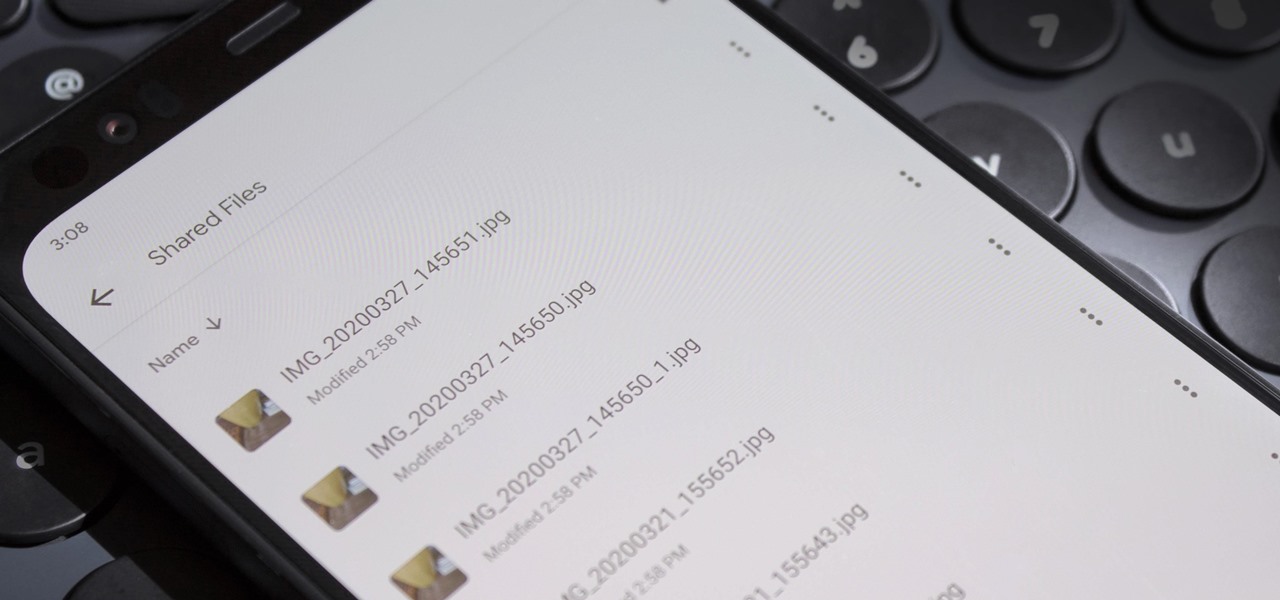
I recently picked up a Pixel Slate when Google had a deal going on. I'd been in the market for an Android tablet since the Nexus 7, and this was the closest thing to it. Unfortunately, I soon learned Chrome OS and Android aren't as integrated as I had hoped.