Watch this software tutorial video to learn how to quickly unzip archived files using the program WinZip. WinZip makes unzipping and unarchiving archived files quick and easy, and this how-to video provides helpful tips on how to use the program.

This computer programming tutorial screencast teaches programming tips and tricks on Ruby on Rails. This Ruby on Rails how to video covers basic string manipulation.

To avoid sports-related injuries, it is essential to warm-up before a race or a game or even before a training or practice session. Watch this video tutorial to learn how to warm up before running by doing side steps from Gilbert's Gazelle training program. This how-to video is a must watch for all track and field athletes.
Check out this video screencast tutorial to help beginner iPhone programmers get started. This tutorial shows how to draw "Hello World!" text on the screen of the iPhone in Mac OSX with the help of Objective C (ObjC) in Xcode for Cocoa programming on your Mac OS.
Learn how to apply for a Google Books Partner Program account, which allows you to submit your content for display on Google Book Search.

A VB.Net 2008 tutorial on how to make a program that can count cards in a blackjack game.

A tutorial on how to unroll and append elements to an array when programming in Java.

Learn to program If & Switch Statements in Java. This tutorial uses Java 1.6 with NetBeans 5.5.1 beta

Delphi controls have an owner and parent property, find out what the difference is and how to use them when programming in Delphi.

You can connect your Nintendo Wii Wiimote to your PC using GlovePie input emulation software and a bluetooth connection. Learn how to program your PC to detect motion from dual input the Wiimote using GlovePie. You'll be able to connect two Wiimotes to your PC.

In this tutorial you will see how to use Jimmy's speed math program that he wrote in Flash. A download to the program is included. This is a GREAT way to help your kids or students (or maybe adults?) get better at math.

Microsoft Excel is one of the most powerful programs for modern businesses. By allowing you to manage, sort, and analyze large collections of data, Excel provides an essential service for any company interested in using the power of data science to its advantage.

The week in AR business news started out with a bang with two bombshell reports that cast a shadow on the AR industry as a whole.

Augmented reality gaming pioneer and Pokémon GO mastermind Niantic is putting the pieces on the gameboard to prepare developers and gamers for the launch of its AR cloud platform.

While MacOS computers have been spared from some of the most famous malware attacks, there is no shortage of malicious programs written for them. To keep your computer safe from some of the most common types of malware, we'll check out two free tools. These tools can automatically detect ransomware encrypting your files and watch for unauthorized access to your microphone and camera.

The enterprise sector is where the money is for augmented reality at the moment, and remote assistance apps are the go-to app for many enterprise customers. We took a look at the leading apps and platforms from this category, from the top contenders to the underdogs with unique features.

While Apple's smartglasses development reportedly moves forward behind-the-scenes, the company continues to build on its AR software foundation in its mobile ecosystem with further iterations to its ARKit platform and the introduction of new AR development tools.

To borrow from the canon of Game of Thrones, what is dead may never die. And while the Meta Company that we knew this time last year is no more, the patent infringement lawsuit filed against the company lives on.

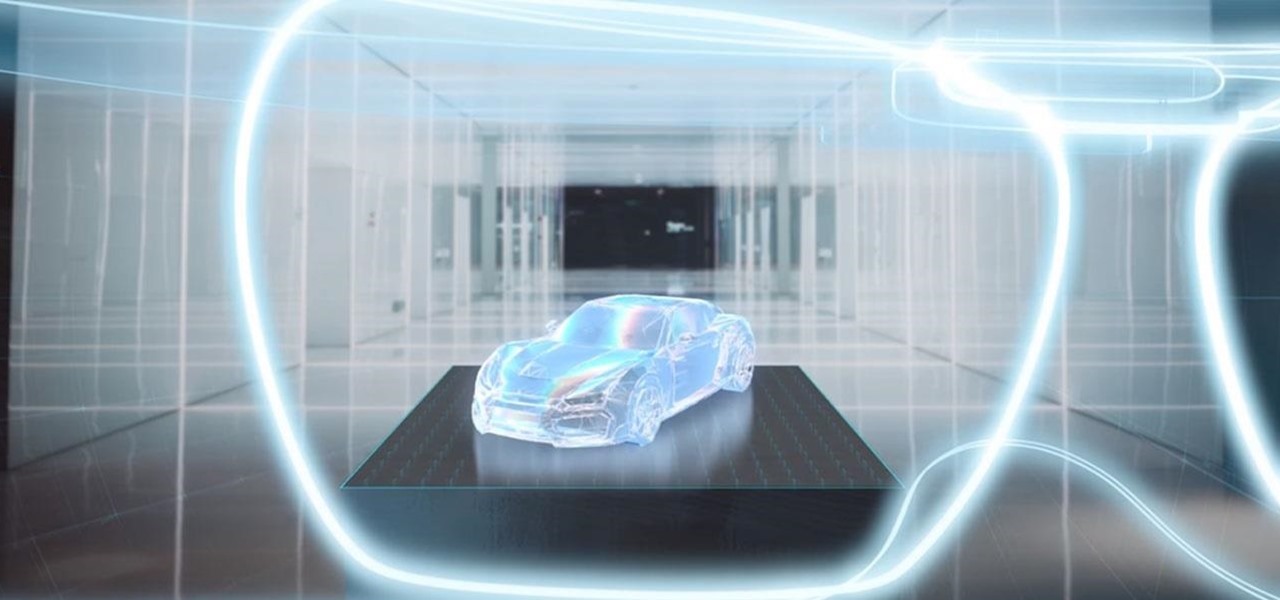
The augmented reality industry has a bright future built on innovation and growth, but that doesn't mean we can't look back at the close of the year to see what the industry has accomplished from a business perspective.

Mixed reviews of Magic Leap One aside, it would be hard to deny that Magic Leap has had a big year. And the AR unicorn isn't coasting to the finish line, with a number of new apps dropping and prescription frames finally arriving to bring relief to those who wear eyeglasses.

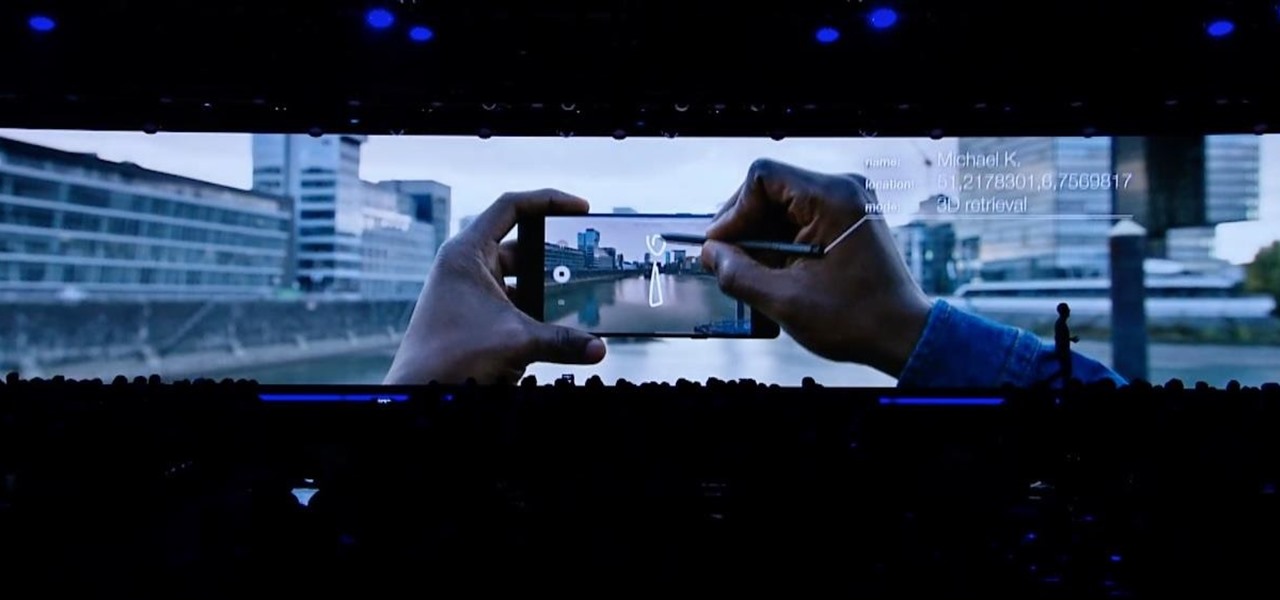
This week, at its developer's conference, Samsung took the wraps off a new tool from Wacom that bestows the S-Pen with AR powers, as well as its own entry to the AR cloud market called Project Whare.

This week, inside sources divulged details of how Apple nearly acquired Leap Motion, twice. Otherwise, companies offering or working on augmented reality technology had more successes than failures to talk about.

Influencers of augmented reality demonstrate expertise in their fields and outline a strong vision for the future that they evangelize to others. They help define the direction of the industry and identify others who foster and create innovation in the field.

This week, Next Reality published profiles on the leaders in augmented reality hardware industry, with Magic Leap CEO Rony Abovitz topping the list. So, it should be no surprise that two app makers want to align themselves with Magic Leap's flagship product.

While most kids his age are busy playing Fortnite, 11-year-old Yumo Soerianto is developing augmented reality games. Kids like Soerianto are the future of the augmented reality field — they'll likely be coming into their own as professional developers right as AR technologies become lightweight and powerful enough to be contained in a pair of sunglasses.

This week, Next Reality published its annual feature on the leaders in the augmented reality industry, the Next Reality 30. So it's no coincidence that the companies represented in the top four spots of the NR30 also made business headlines in AR this week.

Despite the launch of ARKit a year ago, and ARCore this year, a true killer app has not arrived for either platform, that's according to the head honcho for one of the leading development environments for 3D applications.

Format strings are a handy way for programmers to whip up a string from several variables. They are designed to save the programmer time and allow their code to look much cleaner. Unbeknownst to some programmers, format strings can also be used by an attacker to compromise their entire program. In this guide, we are going to look at just how we can use a format string to exploit a running program.

As the calendar year (and, for many companies, the fiscal year) comes to a close, it appears 2017 may stand as the new high-water mark for investment in augmented and virtual reality technology.

When a firm like Techstars believes that augmented reality is an attractive industry to invest in, there's a high probability that it's right.

As demand for AR and VR developers continues to increase, particularly with the advent of Apple's ARKit platform, Unity has partnered with online learning company Udacity to help developers sharpen their skills for these jobs.

Every year, football fans get excited about the next crop of blue chip prospects joining their teams, from five-star high school recruits graduating to college to first-round rookies drafted into the NFL.

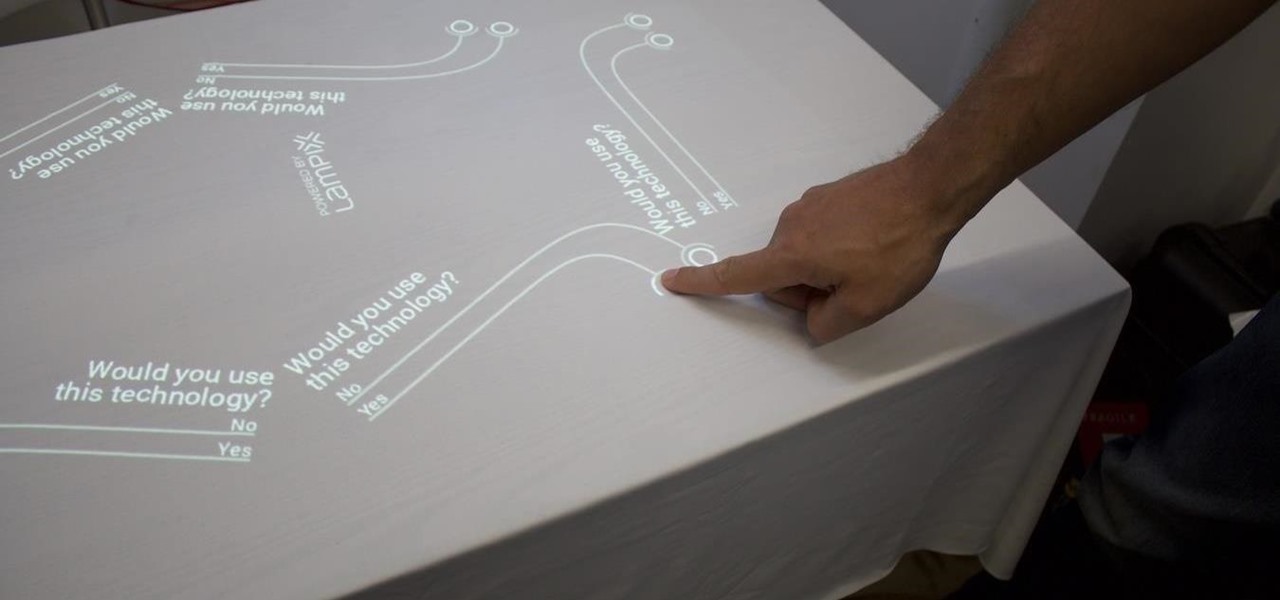
Over the past week, companies took a variety of approaches to investing in augmented reality. Lampix is backing its own effort to build an ecosystem for augmented reality platforms. Nokia and Xiaomi are teaming up on numerous fronts, potentially including augmented reality.

At the moment, it would be safe to say that demand for devices running Tango, Google's augmented reality smartphone platform, is relatively low among consumers. Kaon Interactive, a B2B software company who has built more than 5,000 interactive applications for use at trade shows, remote sales demonstrations, and other customer engagements, is betting that there is a market for the devices in sales and marketing.

User interfaces for computers have evolved over the years, from the introduction of the keyboard and mouse on the personal computer, to touchscreens on mobile devices, to natural voice recognition. However, the same cannot be said for robots or drones—until now.

If you want to make some money from catching bugs and are sick of pentesting Facebook, Google, and Microsoft's products, Uber may be your new favorite playground.

Researchers have discovered a "severe vulnerability" that allows attackers to use eBay to distribute malware, and the online auction company has no plans to fix the problem.

How's it goin'? In this tutorial, we will learn about the security issues of the popen and system functions. I've seen a few people attempting to run command line utilities or whatever it is they require with calls to these two functions but may not know the security implications which come along with it. I will show you using an example from the wargame IO Smash The Stack.

In many programs on Linux, you'll come across programs which allow you to specify additional arguments instead of just simply running the program by itself. If you've used the Kali distribution, I'm more than certain you'll have come across these with the command line tools, else if you have been following these tutorials, we have already come across three tools which also use the same technique, i.e. gcc, gdb and wc. How do we do this with C? Let's find out.

Smartphones don't generally play nice with tripods, so videos taken with our handheld devices make terrible source material for time-lapse photography.