In recent years, the tech innovation space has been dominated by the US and Asia, with Europe weighing in, but still being mostly lauded for its art history and architecture.

Highlight text, tap "Copy," open the app to paste the text into, long-press or double-tap where you want it, and hit "Paste." That's probably what you do when you need to copy text from one location to paste into another on your iPhone. It's a tried-and-true method, but there's a hidden trick for saving and sharing text on iOS that cuts down on that lengthy copy-paste process.

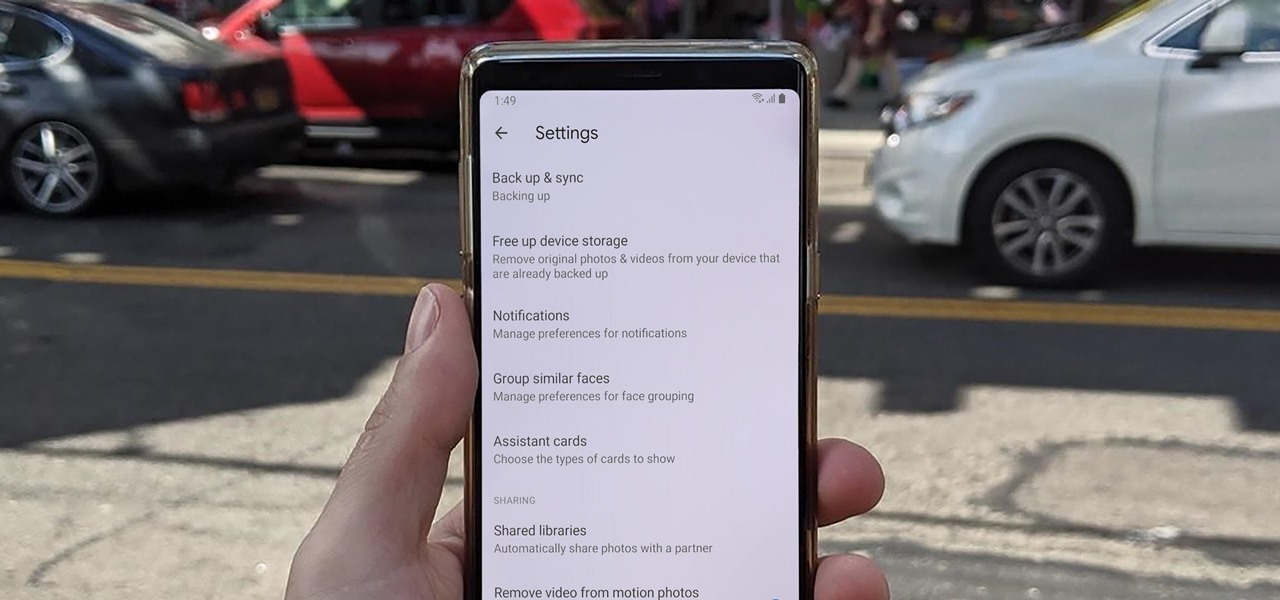
If you use iCloud Photos, Apple's iCloud link feature is meant to make sharing multiple photos and videos faster and easier, but it's not as great as you might think. Luckily, there's a way to stop your iPhone from creating them automatically, as long as you're running iOS 13 or later.

Mac users know why they love Apple. Of course, there are limitations. An entire universe of shortcuts is unavailable to the average user.

Whether you miss the good old days of Telnet or you want to know what hacking was like when security was nothing but an afterthought, Telehack is the game for you. The text-based hacking game is a simulation of a stylized combination of ARPANET and Usenet, circa 1985 to 1990, with a full multi-user universe and player interactions, including 26,600 hosts.

File permissions can get tricky on Linux and can be a valuable avenue of attack during privilege escalation if things aren't configured correctly. SUID binaries can often be an easy path to root, but sifting through all of the defaults can be a massive waste of time. Luckily, there's a simple script that can sort things out for us.

Starting with Android 9 and 10, Google made privacy and security the main priorities for Android updates. Both versions brought numerous changes to help erase the notion that Android isn't safe, but Android 11 might even have them beat.

If you haven't used a Samsung device in a few years, the Galaxy S20 series will be your first taste of One UI 2, the skin running on top of Android 10. Although One UI is on the heavier side, it has loads of exciting features that go beyond what's offered in stock Android.

Password cracking is a specialty of some hackers, and it's often thought that raw computing power trumps everything else. That is true in some cases, but sometimes it's more about the wordlist. Making a custom, targeted wordlist can cut down cracking time considerably, and Wordlister can help with that.

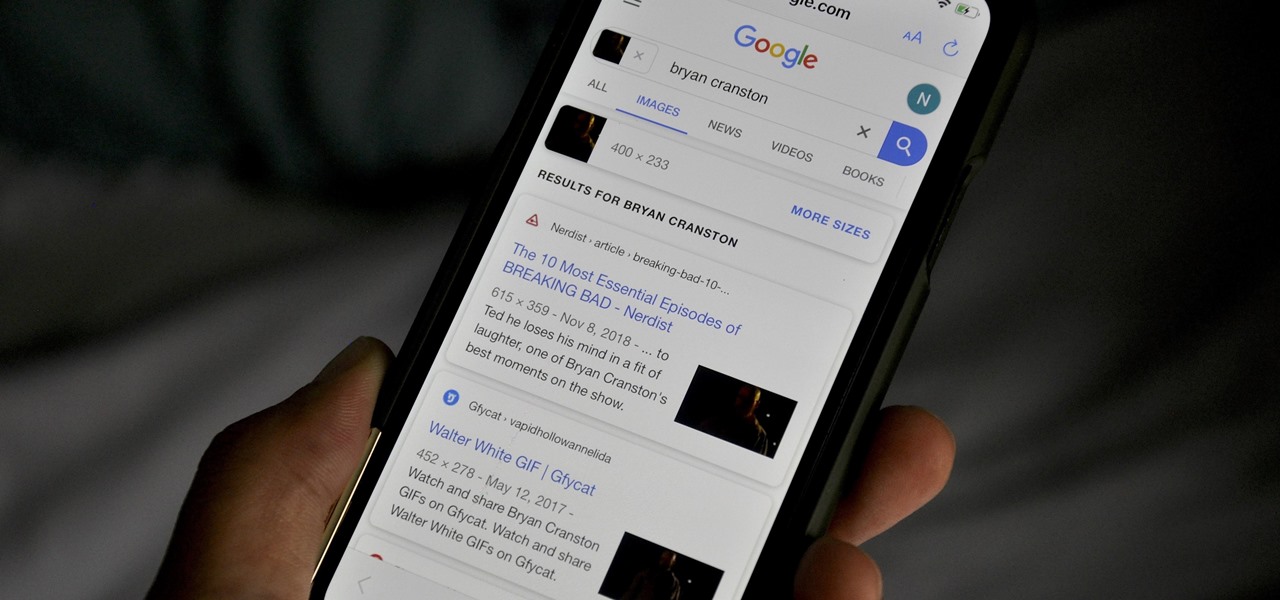
Google Images, TinEye, and other reverse image search engines can help you find where images appear on the internet. You can discover what TV show or movie an image comes from, who took a photo, and if the profile picture of someone you're talking to online is really them, among many other uses. And there's a shortcut for iOS that makes running a reverse image search easy.

Black Desert Mobile is one of the hottest new smartphone games around, but there seems to be something missing in the frame rate department. Gamers quickly noticed many Android phones are stuck on a 30 FPS cap when it comes to performance. It's not that the phones are too weak to handle higher frame rates, but that there is a particular list of approved devices that can achieve this.

For anyone interested in using cheap, Wi-Fi-connected microcontrollers like the ESP8266, the Arduino programming language can be a barrier to entry. Based on C++, Arduino requires knowledge of more computer science than languages like Python. Fortunately for beginners, setting up MicroPython on an ESP8266 allows anyone to write Python on affordable microcontrollers in a matter of minutes.

Pyrit is one of the most powerful WPA/WPA2 cracking tools in a hacker's arsenal, with the ability to benchmark a computer's CPU speeds, analyze capture files for crackable handshakes, and even tap into GPU password-cracking power. To demonstrate how quickly it can hack a WPA/WPA2 password, we'll use it to play a Wi-Fi hacking CTF game anyone can practice for less than $10.

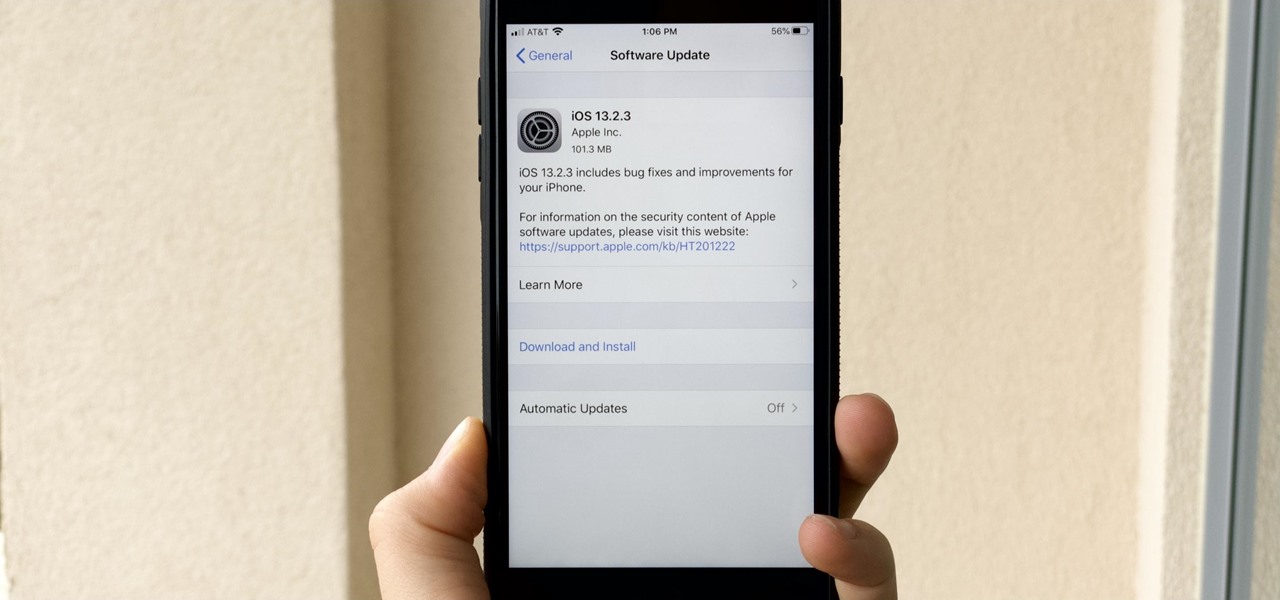
While we all refer to Apple's latest iPhone operating system as iOS 13, in truth, we're well beyond that number. The company has issued numerous updates to its big 2019 release since September, including major steps like iOS 13.1 and iOS 13.2. We've also seen minor updates, like iOS 13.2.2 eleven days ago. Today, Nov. 18, Apple releases another "minor" update, this time dubbed iOS 13.2.3.

The long wait is over — the best augmented reality device on the planet is finally available.

What appears to be an ordinary MP4 may have been designed by an attacker to compromise your Linux Mint operating system. Opening the file will indeed play the intended video, but it will also silently create a connection to the attacker's system.

Businesses leave paper trails for nearly every activity they do, making it easy for a hacker or researcher to dig up everything from business licenses to a CEO's signature if they know where to look. To do this, we'll dig into the databases of government organizations and private companies to learn everything we can about businesses and the people behind them.

Google is an incredibly useful database of indexed websites, but querying Google doesn't search for what you type literally. The algorithms behind Google's searches can lead to a lot of irrelevant results. Still, with the right operators, we can be more exact while searching for information that's time-sensitive or difficult to find.

SMB (Server Message Block) is a protocol that allows resources on the same network to share files, browse the network, and print over the network. It was initially used on Windows, but Unix systems can use SMB through Samba. Today, we will be using a tool called Enum4linux to extract information from a target, as well as smbclient to connect to an SMB share and transfer files.

Who needs a pen when you've got an iPhone? If you have a form, agreement, or contract that you need to quickly sign, you do it directly from iOS without the use of a third-party app. Using Markup, which is available in several native Apple apps, you can sign and send important documents in just a few seconds.

Sharing pictures from Google Photos by sending a link saves time because you don't have to download the image from Google, then reupload it somewhere else. But anyone who has your link can access your pictures, and baked into every file is metadata that you may not want prying eyes to know about.

Apple's annual iPhone launch is set for Sept. 10 and iOS 13 is expected to be released soon thereafter, but it appears that the likelihood of a "one more thing" reveal just got a big boost.

QR codes are everywhere, from product packaging to airline boarding passes, making the scanners that read them a juicy target for hackers. Thanks to flaws in many of these proprietary scanning devices, it's possible to exploit common vulnerabilities using exploits packed into custom QR codes.

We know that Microsoft's HoloLens 2 is due to start shipping later this year, but despite the trickle of news about the device, we still don't know when.

The latest immersive production from Magic Leap Studios finally got its debut on Monday at Siggraph, during which the company also released the app to the general public, so we took it for a spin.

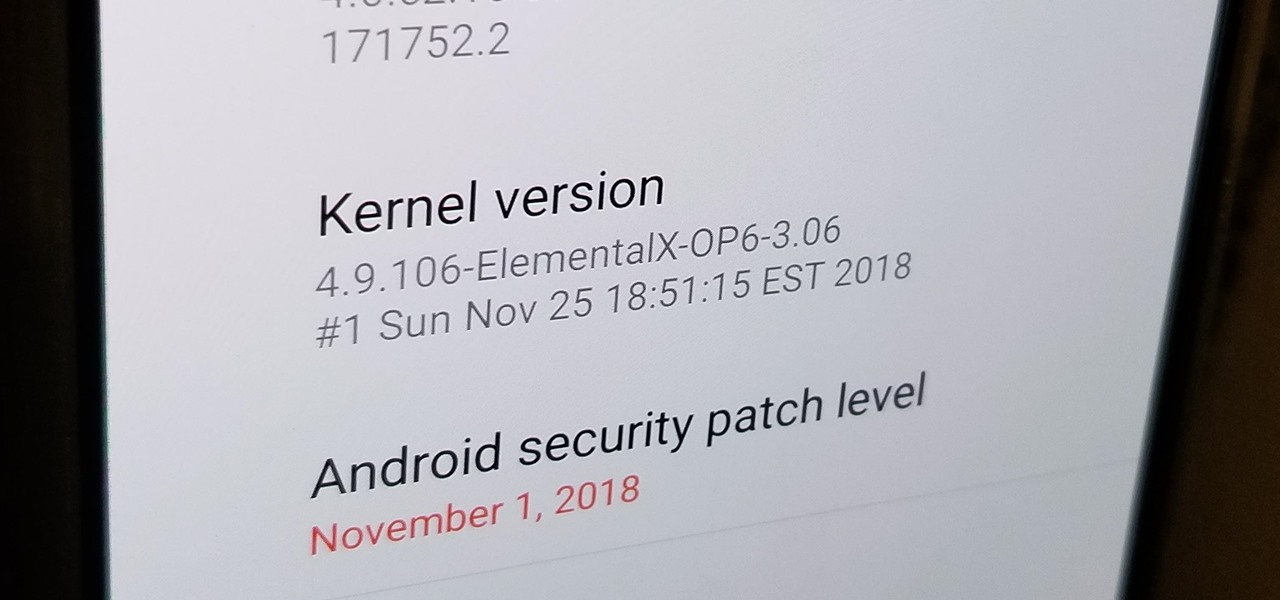
The Pixel 3a runs smoothly out of the box already, but installing a custom kernel can supercharge your experience even more. From fine-tuned CPU tweaks for boosting performance or battery life to adjusting the display colors for your screen how you want, ElementalX kernel can provide you with a ton of new features you didn't know you were missing.

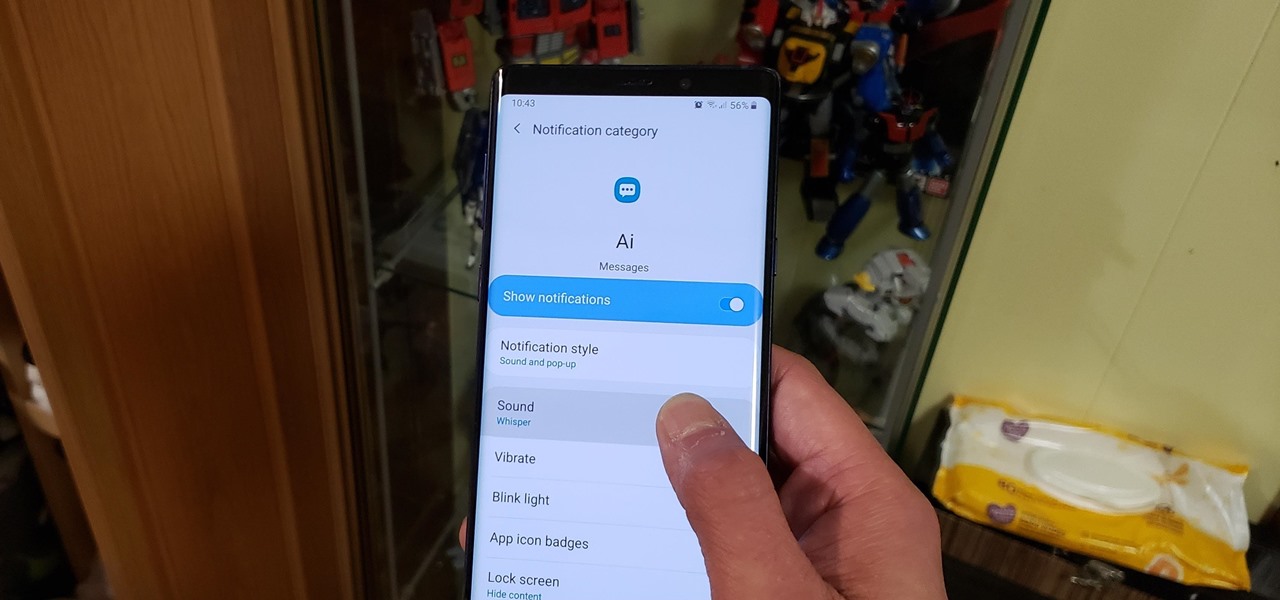
Some messages take precedence over others, so having the same notification tone for all your threads isn't always the best solution. Fortunately, Samsung Messages has a simple option you can tweak to set custom sounds for specific chats to help you stay on top of priority conversations and reply much faster.

UAC is something we've all dealt with on Windows, either as a user, administrator, or attacker. It's a core feature of the Windows security model, and for the most part, it does what it's supposed to. But it can be frustrating as a hacker when attempting privilege escalation, but it's easy enough to bypass UAC and obtain System access with Metasploit.

It looks like it's cuffing season for AR hardware makers and telecommunications corporations. With AT&T aligned with Magic Leap as its exclusive wireless retailer on the high-end AR side, Verizon has also reached a master reseller agreement with Vuzix, according to a filing with the Securities Exchange Commission.

Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands.

Many online users worry about their accounts being breached by some master hacker, but the more likely scenario is falling victim to a bot written to use leaked passwords in data breaches from companies like LinkedIn, MySpace, and Tumblr. For instance, a tool called H8mail can search through over 1 billion leaked credentials to discover passwords that might still be in use today.

After you unlock the bootloader, install TWRP custom recovery, and flash Magisk to gain root access, what might be the next step of your modding adventure? A custom kernel, of course! Flashing a custom kernel onto your device gives you a whole new level of tweaks and customizations, and it allows you to have full control over how your system performs.

By now, you've probably already seen Andy Serkis and his performance capture demo for Magic Leap. And sure, marrying motion capture acting and augmented reality sounds compelling, but how does it really work as an experience?

Like many things associated with Magic Leap, the start of the company's first annual L.E.A.P. conference got off to a unique start. Taking the stage on Wednesday morning in Los Angeles, the company's CEO, Rony Abovitz, gave a brief introductory speech welcoming the crowd and outlining the mission of Magic Leap.

You can never replace the skills and expertise of a professional graphic designer, but Canva comes pretty damn close. It's ridiculously easy to use the drag-and-drop design tool for both professionals and people like me who don't have the need (or knowledge required) to use more advanced graphic design software.

Time to play — Fortnite is now officially available on Android. However, the game won't be available across the Android ecosystem right away. Fortnite Battle Royale launches on Samsung devices first. That means if you have a Galaxy S7, S8, S9, Note 8, Tab 3, or Tab 4, you can download the game right now.

Developers creating login systems know better than to store passwords in plain text, usually storing hashes of a password to prevent storing the credentials in a way a hacker could steal. Due to the way hashes work, not all are created equal. Some are more vulnerable than others, and a little Python could be used to brute-force any weak hashes to get the passwords they were created from.

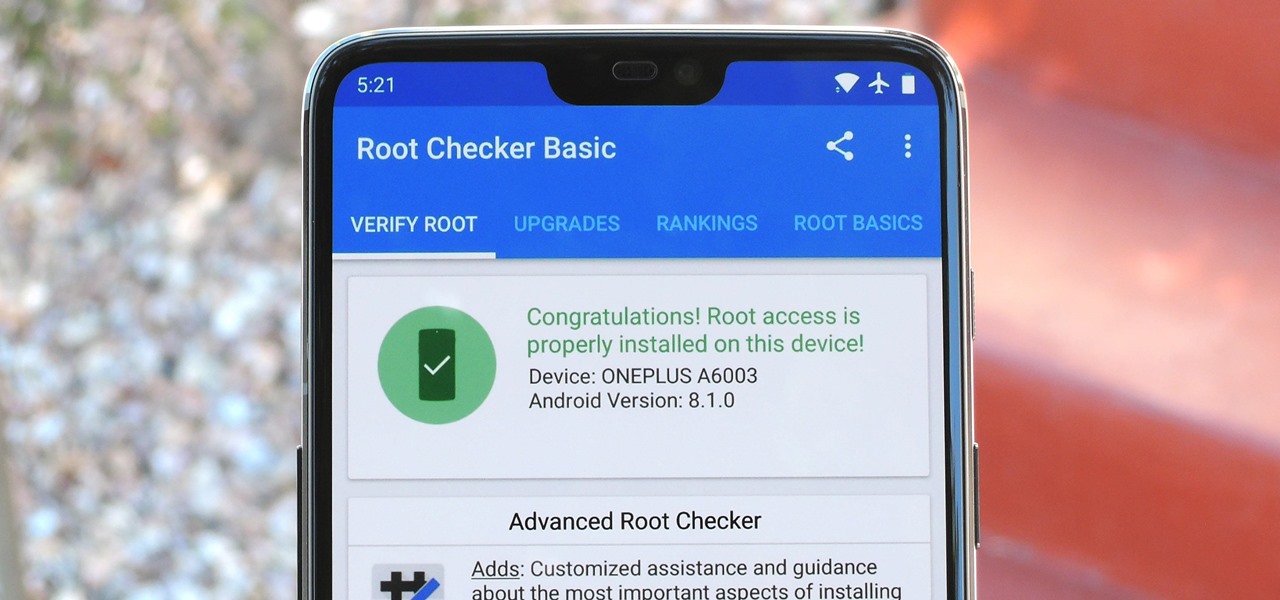
Year in and year out, OnePlus flagships top our list of the best phones for rooting. Why? Primarily because rooting does not void your warranty, and OnePlus goes out of their way to make the whole process as easy as possible.

Google's ARCore has expanded its support to include the Galaxy S9 and S9+, which means you get access to all the cool new apps that can sense the world around them. But one of ARCore's coolest uses so far is still Pixel-exclusive: AR stickers built right into the Google Camera app. Thankfully, XDA user lofass33 has an ingenious workaround for using these stickers on your S9.

Backdooring a powered-off MacBook is easy when a few minutes of physical access is allowed. That attack works well if the hacker also shares a Wi-Fi network with the victim, but this time, I'll show how to remotely establish a connection to the backdoored MacBook as it moves between different Wi-Fi networks.