
Married Filing Search Results


Uncrackable File Sharing: Securely Transfer Your Secrets with 4096-Bit Encryption
Do you need to email your wife your Social Security number? Send confidential business plans to your partner in Thailand? Send your hacker buddies the recovered hashes from last night's breach? Try using GPG, a valuable and easy to use open-source encryption program.

News: Simple XOR Text Encryption and Decryption in Visual C#
For this particular example, I will be working on Wndows (sorry X users). I might write a similar guide once I am more comfortable with programming in Linux.

How To: Set Up Auto-Scheduled Backups to Avoid Data Loss on Any OS
Backing up your files is a requirement in today's world of tech. In an instant, your storage device can fail. This is an unacceptable situation that should never happen to anyone. Storage is cheap, and backups are easier than ever to perform. Most of the time, this can be completely automated, so you can just set it and forget it. Today, Null Byte will be covering how we can automatically, and efficiently back up our data across all OS platforms, while giving a few alternatives to the built-i...

Goodnight Byte: HackThisSite Walkthrough, Part 2 - Legal Hacker Training
Welcome to the closing of the second HackThisSite and programming Community Byte. First and foremost, I would like to ask that people start showing up on time to the Community Bytes. If you need help converting your time zone to PST, go to Time Zone Converter. When users do not show up on time, we have to go backwards and catch everybody up. This wastes time and will also make other users' experience less enjoyable when they have to watch and listen to the same thing 100 times. Punctuality as...

How To: Download and Install Minecraft 1.0: The Final Pre-Release
Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. Well this is it folks, the final Pre-Release before Minecraft officially launches! These changes should be the final game changes until it releases in Vegas this Friday. Mojang has made it clear, however, that they will continue making changes to the game while it's released.

How To: Download and Install the Minecraft 1.9.6 Pre-Release Beta
Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. Minecraft Pre-Release 1.9 Version 6 is out! This update includes more bug fixes from Version 5 and Ender Dragons! We'll be reporting more changes as we find them, so stay tuned.

How To: Recover WinRAR and Zip Passwords
Archiving and compression is a great way to store and prepare files for sending. You can reduce the size of a file, turn a group of files into a single file, and even encrypt and password the contents! Just take a look at this image to see how much it compressed a 28GB text file.

How To: Download and Install Minecraft 1.9 Version 4 Pre-Release
Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. We're back again for another Pre-release!

How To: Download and Install Minecraft 1.9 Version 3 Pre-Release
UPDATE: Minecraft 1.9.5 Has Been Leaked! Get it Here. You heard right. This one is hot off the presses! Last night, Notch promised a 1.9 Version 3 Update and here it is!

Social Engineering, Part 2: Hacking a Friend's Facebook Password
Welcome to the second Null Byte in a series educating you on Social Engineering awareness and techniques. Today, I'm going to show you how a saavy Social Engineer would trick a friend into unknowingly surrendering their Facebook password. My intent is to warn and demonstrate how easy it is to succumb to phishing via Social Engineering, and therefore expose yourself.

News: Haptic Hacking Breathes New Life into Old Computer Mice
You've seen the felt mouse, which made computer clicking comfortable and chic, now brace yourself for something a little more interactive—DataBot.

News: Protect Your Dropbox Files from Prying Eyes (+ 2 Alternative File Hosting Options)
Dropbox continues to make headlines with their recent programming blunder which left the accounts of its 25 million customers wide open during a four-hour time span. During the duration, anyone in the world could access any Dropbox profile by typing in any password. And seeing as this wasn't the first security failure, everyone, including the most loyal users are considering dropping the Dropbox.

News: Automatically Manage and Sort Files Using Hazel [Mac]
In many of my articles, I will refer to applications designed to empower Mac users to automate various tasks on their computer. One such application is called Hazel. Like smart folders, smart playlists, and smart albums found in Mac OS X and iPhoto, Hazel can automate the task of moving, copying, or deleting files in folders on your Mac. I recommend Hazel as one of the most essential applications for any Mac user. Let's explore how it works.

How To: Safely Share Files Online
Okay, stop me if you've heard this one. You have a document that you want your co-workers' advice on. You attach said document onto a mass email. The first reply comes back with an edited version of the document. You begin to make changes, but another email comes in, with yet another edited version. Soon you're drowning in a desktop folder full of mismatched documents, all with the same name.
News: SOFTWARE HINTS, TIPS & TRICKS-"DITTO & DITTO PORTABLE"
SOFTWARE HINTS, TIPS & TRICKS-"DITTO & DITTO PORTABLE" Tips

News: Most Cuckoo Jackass Contest Entry: 25MPH Motorized File Cabinet
Look what came in the mail today! The File Cabinet from hell. Die hard Jackass fan and file cabinet mod-junkie Jeff Dahlin tracked us down to drop off this gem at WonderHowTo HQ today. It is his official entry for the Jackass Prank Contest.

Special Delivery Mod: Dude Submits 25 MPH Motorized File Cabinet
It is the file cabinet from Hell. Look what came in the mail today! Die hard Jackass fan and file cabinet mod-junkie Jeff Dahlin tracked us down to drop off this gem at WonderHowTo HQ today. It is his official entry for the Jackass Prank Contest.

How To: Render video files in After Effects
This tutorial shows you how to take a video file and render it out as frames using After Effects. Render video files in After Effects.

How To: Convert Illustrator files to Graphtec GSD format
This tutorial shows you how to convert Illustrator files to the Graphtec GSD format for use with ROBO Master software. Convert Illustrator files to Graphtec GSD format.

How To: Export a SWF file from ImageReady CS2 to Flash 8
Learn how to export an SWF file from ImageReady CS2 into Flash 8 to optimize it's usability in Flash. Export a SWF file from ImageReady CS2 to Flash 8.

How To: Use Bridge in a design workflow
This video shows you how designers can use Bridge to find files and integrate them with In Design. Watch and learn how to search and group details of files, use Preview to examine high-resolution images, and use Compact mode to ease the process of dragging a file into another application. Check out this video created by Mordy Golding now! Use Bridge in a design workflow.

How To: Recover corrupt After Effects files & import projects
In this tutorial, Aharon Rabinowitz shares tips on the many uses of importing After Effects Projects, and how you can recover corrupt AE files. Recover corrupt After Effects files & import projects.
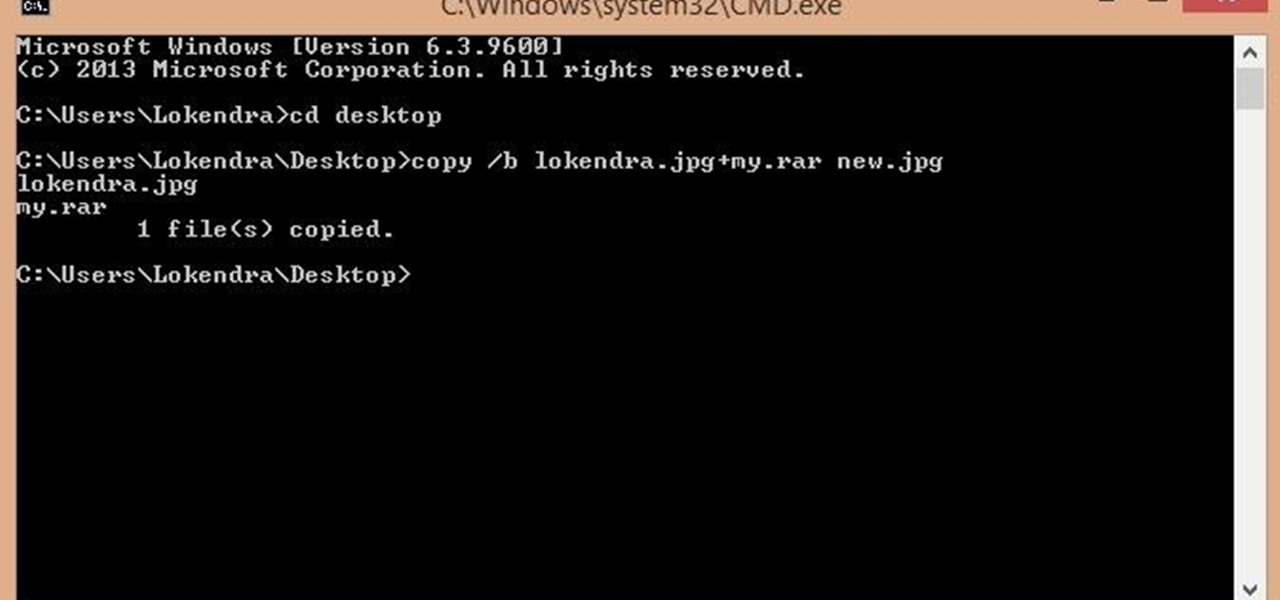
How To: Lock Your Files in an Image....... Amazing Trick Ever
First of all you should make a folder and rename it as 'my'. Move all your files on that folder and place it on desktop.
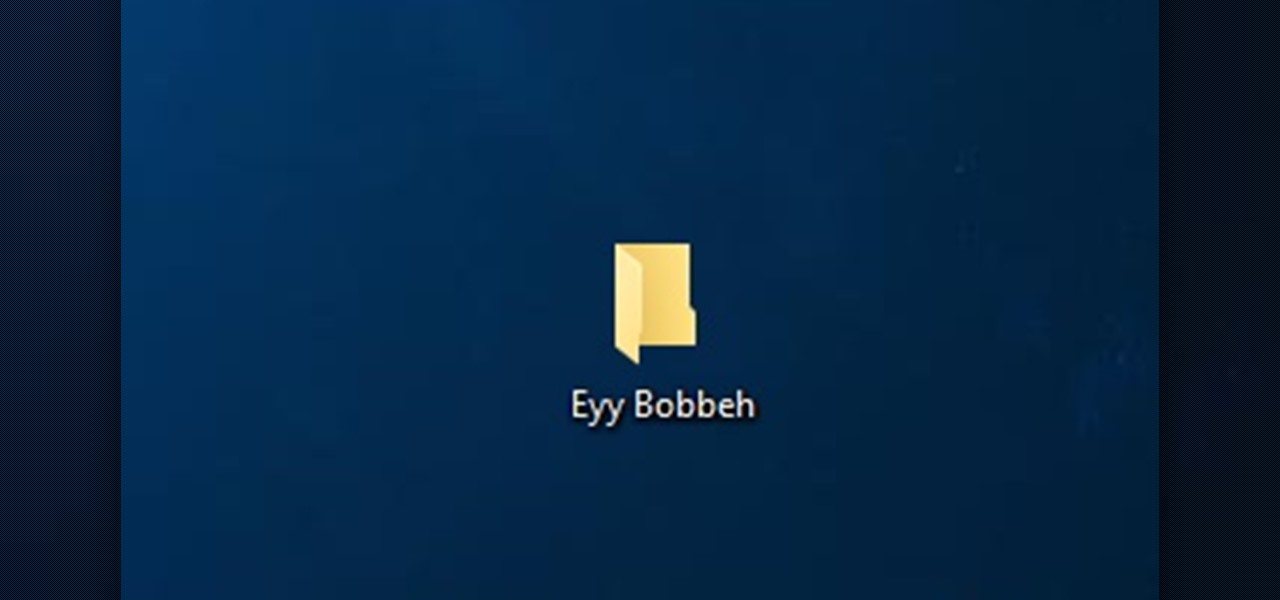
How To: Make Super Hidden Folders
Basically what this tutorial will show you is how to make folders that won't show up in windows even with the show hidden files/folders option on. First thing you need to do is make a folder on your desktop. Then you need top open up command Prompt and type in the following command (Don't forget quotations if file path has any spaces in it):

How To: Embed a Backdoor in an Exe File
Welcome back Hackers! We have embed a Backdoor in to a PDF file,Android package File.

News: Merge Audio Files
My mp3 player is really crappy so it sometimes doesn't recognize books I rip, so if you want to play it in order you have to rename all the files. To make this easier, I merge each disc into one file. It's also great for other purposes. This program is free and works well! Merge MP3.

How To: Make Money Online by File Sharing
When I was unemployed I looked for different ways to make money. Most of that work was connected with online stuff; I’ve tried writing content, refreshed my old Photoshop skills and even created postcards, but then I realized that my passion to music can bring me more money than all of the other work. I was an active member of a few musical forums and started to add affiliate links to my posts instead of simple ones, so they can be profitable.

How To: Make a Yes/No Question Error Message
This article will teach you how to make an error similar to this one (also by me). This error message though, is a yes or no question. Clicking yes and no will give different results. Like the previous error message, this is 100% harmless.
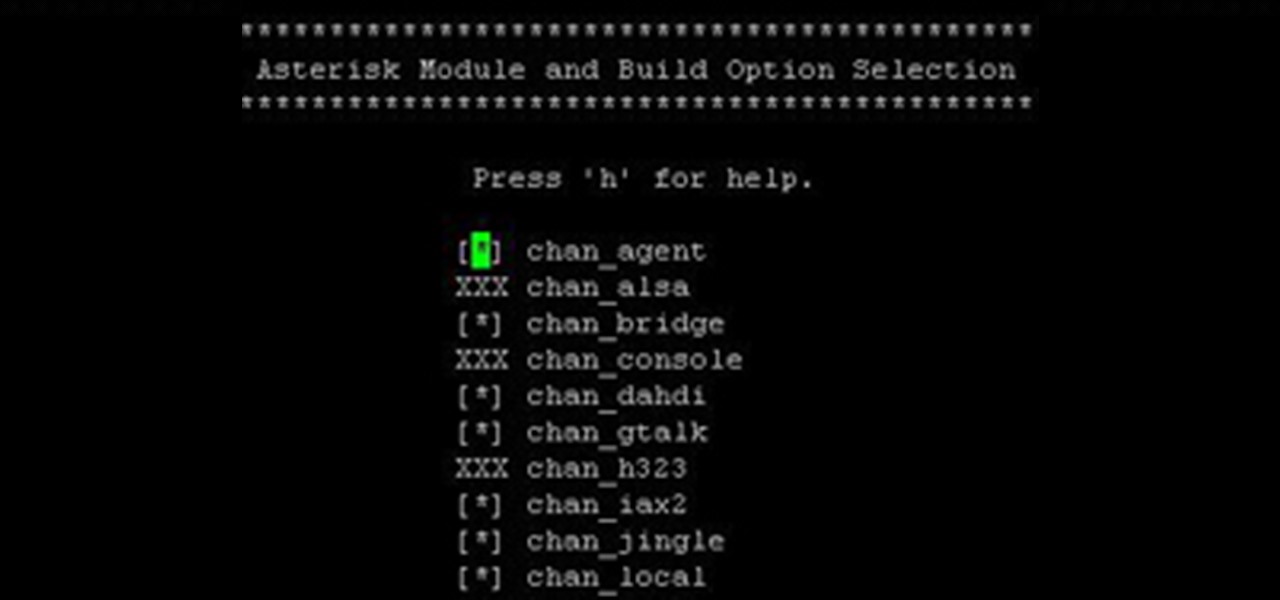
How To: Setup an Asterisk Server
Over the years, I have enjoyed playing with Asterisk. I have found Asterisk to be extremely powerful and fun to play with. There are several books and many scattered how to articles out there, but most are outdated and the information required to build Asterisk from beginning to end can be a bit daunting. I wanted to combine all the steps into a single article and share my experience with everyone. If I have left out any steps please let me know.

How To: Install Linux on a USB With Unetbootin
There are lots of Linux distros out there. Normally, you'll have to download the ISO and then burn the image onto a CD. But nowadays, it's easier and cheap to install it on a USB drive.

How To: Convert PDF Documents to JPG Images Online for Free
PDF is a convenient format for documents that can embed text and pictures and can be read by almost any device—personal computers, laptops, smartphones, etc. However, PDFs are mostly read-only files, so sometimes it's necessary to convert them to JPG images, a universal format for pictures. JPGs can be modified by software such as Adobe Photoshop or posted on Facebook.

Hack Logs and Linux Commands: What's Going On Here?
This morning, I received a message from a friend who was reading a hack log, and she had some questions about the commands used. This got me thinking, as Linux has a ton of commands and some can be archaic, yet useful. We are going to go over everything you need to know to read a hack log and hopefully implant the steps in your head for future use.

How To: enable & disable Page File Encryption
Hello, welcome to my first post! Today, I would like to talk about setting up a Page File Encryption in Windows 7 and Vista. But first - what is a Page File Encryption? Why should you enable this option?

How To: Convert Protected M4P Files to MP3 Songs with iMovie and iTunes
I'm not sure exactly when it happened, but it's awesome that you can now download music from the iTunes Store that's free of DRM (digital rights management) limitations. That was always my biggest problem with buying music from iTunes. Paying a buck for a song that I can only play on Apple devices? Really? That's what finally led me away to other legal music downloading services like eMusic and Amazon.

How To: Run an FTP Server from Home with Linux
File Transfer Protocol, or FTP, is a network protocol made for transferring files in a client and host fashion over a Transmission Control Protocol (TCP) network, such as the internet. FTP is integrated into most browsers, and you have probably used it before. It is a common way to host files and transfer them easily. To access an FTP, a login is required, unless the server is configured to use anonymous logins (like the Arch Linux mirrors).

How To: Recover a Windows Password with Ophcrack
When Windows stores a password, it is done so by hashing the password in an LM hash and putting it in the Windows SAM file. In the scary moment that you lose your password, but don't want to pay some geek to have full root access to your computer, you need to recover it using Ophcrack. Ophcrack doesn't remove the password, or bypass it, it cracks the password hash using rainbow tables.

How To: Download and Install the Minecraft 1.8 Pre-Release
Update 2: 1.9 Version3 is currently out. Click here to download and install 1.9 Version 3. Update: 1.8 is now officially out! It'll prompt you to update the next time you launch.

News: Easy Skype iPhone Exploit Exposes Your Phone Book & More
Like the recent XSS 0day exploit found in the Mac and Windows versions of Skype, a similar one has been found in the Skype app for iPhone. The vulnerability allows an attacker to send a message that contains malicious JavaScript code in the "Name" parameter. This code can steal your phonebook, crash the app, and potentially do a lot worse. The URI scheme is improperly identified for the web-kit browser. Instead of going to a blank browser page, it defaults to "file://". The code could steal a...

How To: Get By with the Cheaper 16GB Option for iPhone or iPad
There are a few different types of Apple iPhone and iPad users: general household users who largely consume media—e.g. surfing the web, watching movies, listening to music. Other iPhone and iPad owners use their device(s) to produce stuff—written documents, edited movies, blog posts, music tracks, and the like. And then there are those who are very mobile with their devices. They commute to and from work on a regular basis with their iPhone or iPad. Some users may travel a lot on business, or...

