
How To: 18 Awesome Ways to Reuse Old Pantyhose
The annoying thing about pantyhose? They snag and tear very easily. The amazing thing about pantyhose? They have about a gazillion practical uses even if you can no longer wear them.


The annoying thing about pantyhose? They snag and tear very easily. The amazing thing about pantyhose? They have about a gazillion practical uses even if you can no longer wear them.

Tom Friedman. One of my very favorite contemporary artists. Friedman injects the wonder into the humdrum. He creates magic from the unsuspected with his incredible sculptures assembled from simple, everyday materials. His materials have included: toilet paper, drinking straws, construction paper, masking tape, toothpicks, bubblegum, spaghetti, toothpaste, soap powder, sugar cubes.

Need to be undercover? Well, make yourself impossible to photograph. Get some infrared LEDs. They're undetectable to the human eye, but that's not the case with cameras. Wire them to the brim of your hat and you've got instant invisibility to any camera -- paparazzi, Big Brother or otherwise.

Fireworks, with its hybrid vector/raster type operation is especially well suited to mask work. Fireworks masks are based on one image clipping another. In this Fireworks 8 video tutorial you will learn how to create and use image masks. Make sure to hit "play tutorial" in the top left corner of the video to start the video. There is no sound, so you'll need to watch the pop-up directions. Create and use image masks in Fireworks 8.

25-year-old Anthony Le, of Colorado is THE ultimate Iron Man fan. A cosplay fan, Anthony decided to try his hand at building a super realistic Iron Man suit, just in time for the release of Iron Man 2. The incredibly talented fitness consultant did above and beyond what you might expect. Check out the two videos below. Le's insane suit features the following: a dent-proof exterior, a motorized faceplate, and a spinning mock Gatling gun. He spent one month and approximately $4k building his ma...

Word of mouth is that Zynga is preparing to harvest the world. Is this a horror movie? No, but FarmVille has already invaded millions of homes, and now it wishes to conquer our pockets. They're gearing up for a mobile platform, one that will reach millions more via the iPhone, iPod Touch, iPad, and Android.

This video teaches one how to get rid of blackheads. First, we have to open the skin pores by putting a warm towel on our face. Keep it there a while, until it starts to cool. After that, the pores are open. Put a clay mask in your skin - any clay mask will do. Keep the clay mask on your face for 8 to 12 minutes; do not allow the clay mask to dry because your face will make more oil to compensate. Then use the same towel to clean your skin. Your face will be softer, and the blackheads will di...

In this Illustrator CS2 video tutorial you will learn to create a picture clipping mask. In another words, you will learn how to clip a picture with any closed vector path. Make sure you select both objects when applying the Make Clipping Mask command. Make sure to hit "play tutorial" in the top left corner of the video to start the video. There is no sound, so you'll need to watch the pop-up directions. Create a picture clipping mask in Illustrator CS2.

Pulp heroism rules! And everyone's favorite masked vigilante hits the big screen tomorrow night, thanks to fantastical filmmaker Michel Gondry and his new superhero movie, The Green Hornet.

Skin care products need to be properly applied to do their best work and be effective. Here we show you the techniques to applying skin care products properly. Serum

The worst can always happen. Even if you think you're absolutely prepared, you can somehow find yourself stranded in the middle of nowhere by yourself. It can happen. Without a map, without a compass, without a cell phone... without food and water.

This three-part series presents a look at the various forces in DOPs and how they work. This tutorial covers all the major forces except for the vortex, bouyancy and fluid forces. It covers both basic aspects and some more advanced techniques (animated masks, using RBD object position to drive a magnet force).

Photographer Chris Alvanas uses some of the new tools and functionality of Photoshop CS4 to retouch the eyes of his subject. This video involves Quick Mask mode, and isolating Hue/Saturation adjustments for a specific tone.

Step 1: Have most of the Jackass crew think they are doing a photo shoot for the upcoming movie. Schedule the shoot in a tear gas chamber that is dressed to look like a photo set. Have secret film cameras planted in the chamber so you don't have any obvious camera men walking around with gas masks on inside the room.

In order to build a garden tuteur, you will need the following: found sticks, screws, twine, a drill, and a rubber band.

You can get a spa like experience in your own home. Follow these tips to treat yourself to a well deserved facial at home. Create your environment

MineCon 2011 (held at the Mandalay Bay in Vegas) was in a word, awesome. The crowd was overwhelmingly young, the vibe was fun and nerdy, and best of all, the costumes were inspired. Below are my favorites, which unfortunately aren't of the best quality (lighting was low and super yellow, which wasn't helped much by my standard point-and-shoot). If you happened to attend Minecon as well, post about your experience to the community corkboard... if you're pictured below, please comment!

XSS stands for cross-site scripting, which is a form of web-based exploitation that uses client-side vulnerabilities in a web page to execute malicious JavaScript codes. JavaScript is referred to as "cross-site" because it usually involves an external website containing the malicious code. That code is most commonly used to steal cookies with a website that the attacker created and hosted on another server. The cookies can then be used to escalate privileges and gain root access to someone's ...

Airsoft doesn't get any better than a cloud chamber BB machine gun, aka Cloud BBMG. This design has an incredible rate of fire. If you've got a full charge of compressed air, it can easily fire more than 50 rounds per second at a 350 ft/s muzzle velocity. Since this is a legit airsoft build, it should be handled safely with the same care as any other airsoft firearm, and you should be wearing the same protective gear—protective mask, safety glasses, etc. My video details the build of this bea...

Medicine, like the internet, is serious business. So when the text that appears on the labels of our medicine bottles makes about as much sense as an epileptic in a rave club, we can't help but take pause. Follow us on a journey of prescriptions and misdescriptions!

Scrabble Bingo of the Day: NOSEGAY [n] A nosegay is simply a bouquet of flowers, typically given as gifts. It comes from Middle English, from the words nose and gay, which in this case means brightly colored and showy. It does not reference homosexuality; the modern sense of gay.

Welcome to Part 3 in my series on protecting your computer from prying eyes (Part 1, Part 2). In today's segment, we will be going over drive encryption using the TrueCrypt program on Windows OS. Drive encryption is a technique that masks your data with a cryptographic function. The encryption header stores the password that you have entered for the archive, which allows the data to be reversed and read from. Encrypted data is safe from anyone who wants to read it, other than people with the ...

Encryped traffic and tunneling is a must when away from home to keep you and your information safe. SSH tunnels can be slow, and are heavily encrypted. VPNs are an all port solution, and proxies are just not what we need in most cases. Then, there is Tor.
Curso Photoshop Fundamentals - 15h, 94 eur+IVA Curso Photoshop Mastering - 33h, 194 eur+IVA

GUISARD n pl. -S a masker 59 points (9 points without the bingo)

Japan has a tendency to produce things that boggle the Western mind. Its citizens are already responsible for without a question the weirdest music video in the history of the medium. With that said, here is a video reenactment of several Pokemon (Pocket Monster in Japan) games released by Japanese performance art troupe Kusarine Project: Kusarine Project and their amazing YouTube channel first became known through the Japanese video sharing site/meme originator NicoNicoDouba. Their white mas...

Dr. Elena Bodnar proposes a silly idea. Why not wear a bra that double as a gas mask? No point in being ill equipped (in the event of fires, terrorist attacks, dust storms or a swine flu outbreak). The instructions are simple: In the event of an emergency, remove bra.

Ok, so for this one its going to be on my friend Nathans cousin, Justin, once again. We mess with this guy sooo much ha. Read the whole prank, but it short, He thinks he's gonna be in an actual movie, but instead its a Jurassic Park themed gay porn shoot. So we're gonna tell him we're going to California to be in Jurassic Park 4(he'll believe it, trust me). On the flight we can even have a couple pages of a fake script to read. When we get there it'll be just like any other shoot or at least ...

Watch as world freediving champion Guillaume Nery takes an incredible dive into Dean's Blue Hole in the Bahamas (on ONE SINGLE BREATH!)

It's been almost a century since we've last seen Kid Icarus start in his own game! The result of Project Sora, Kid Icarus will be released for the Nintendo 3DS!
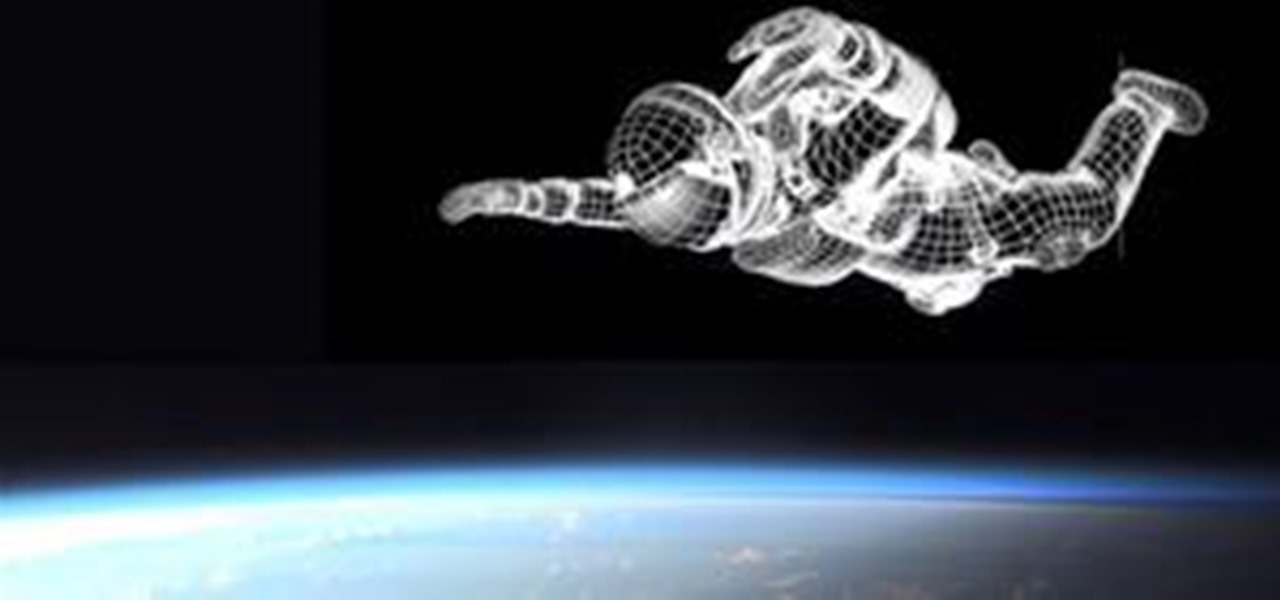
Felix Baumgartner plans to leap a record 120,000 feet, breaking four world records. If all goes well, Baumgartner will set records for highest altitude freefall, longest distance freefall, highest manned balloon fight, and fastest speed freefall (he will actually break the sound of speed!).

IP Hider masks the real IP of a user, allowing him to browse all kind of pages without ever worrying that the ISPs or any other marketing tool is monitoring your surfing habits or spammers are attacking your computer. The simplest way to do this is to have traffic redirected through anonymous proxies.

This ten-part video tutorial series covers all the new features and uses of Fireworks CS4. This is a great introduction to any user new to Fireworks in general, or wanting to learn what changes have happened from Fireworks CS3 to CS4.

Apple just released iOS 13.5.1, the latest update for iPhone, on Monday, June 1. The update comes 12 days after iOS 13.5, which introduced COVID-19 exposure notifications, a Group FaceTime update, and Face ID improvements when wearing a mask.

There are many opportunities to make Steampunk clothing. Clothing can be elegant and relate to the aristocrats of the 19th century. But Steampunk also can be rough and dirty, inspired by the adventurer from stories like 2000 miles under the sea or even movies like "Mad Max" or Wild "Wild West".. There are no rules how Steampunk has to look...
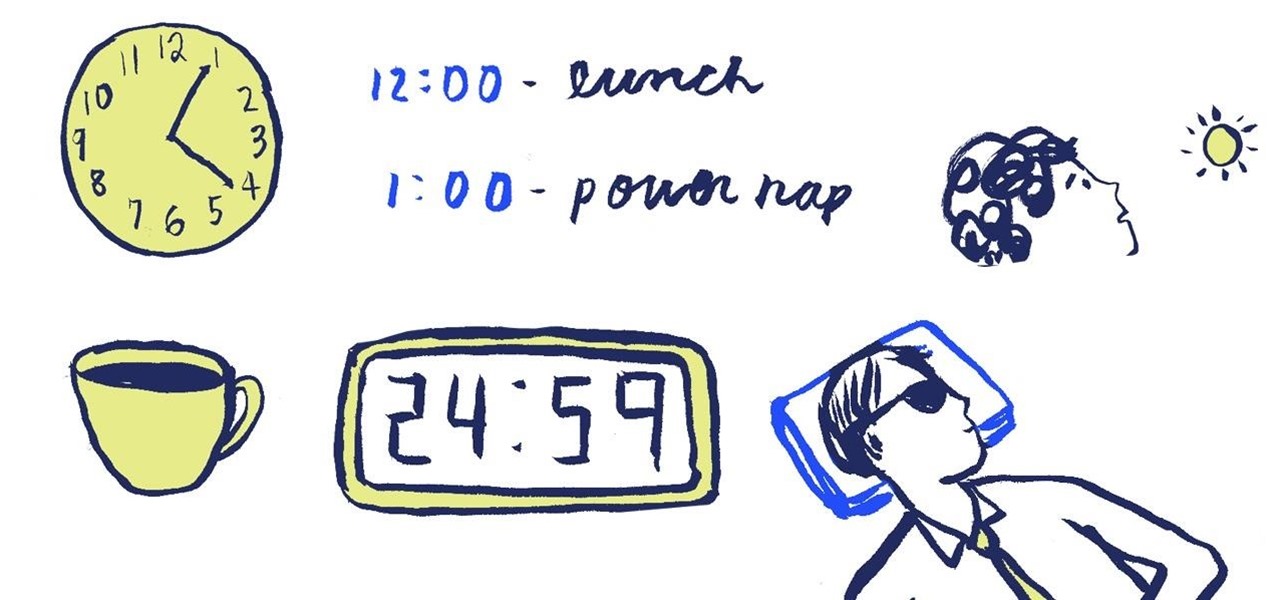
If you like the idea of napping but have difficulty waking up after 20 minutes, drink a cup of coffee right before you lay down. As caffeine takes about 15 to 20 minutes to take physical effect, you can wake up from your nap ready to conquer the world just as the caffeine high starts kicking in.

Unlike your more artistically-minded friends who've been working on their homemade, hand-stitched, conceptually-brilliant Halloween costumes since May, you need to put together a last-minute costume in a matter of hours. What can you possibly do if you're cheap, kind of lazy, and don't know how to sew to save your life?

Have you ever come across somebody on the streets looking like this? Pretty freaky, especially if it's not Halloween. But you know what, Halloween is almost here, so freaky is good. Thanks to creative folks like Eric Testroete and Bhautik Joshi, you can now create an awesome papercraft portrait of your own head for Halloween this year.

Rain can make for an amazing photograph, but it can do disastrous things to your equipment. This super simple DIY cover from Purple Summit Photography will keep out the rain so you can capture beautiful shots no matter the weather, and it's made using things you probably have lying around. Photo by Jon Shave

Itching to make your own guerrilla-style street art on the side of buildings, freeway overpasses, and abandoned billboards? The beauty of street art is that you don't need an expensive canvas or frame to display your creative expression.