In this project, you'll learn step by step how to modify a microwave oven transformer into a high-current device that can pump out 800 amps of electrical current, which is enough amperage to melt metal. If you liked the Metal Melter you saw in my previous project, here's how you can make your own!

Is "Last Resort" Steampunk? Well, no. I mean, how could it be?

We've gathered some of our favorite pranks with the seasonally appropriate for all you college kids out there. You're more than likely cohabitating with a complete stranger, and what better way to make a good first impression and develop a strong personal relationship than subject them to a hilarious prank?

Losing your important data can be more painful than losing the hardware the data was stored on. Precious memories, files you don't often access but always want to have, there's so much you store on impermanent devices that you can't live without. Backing up your information to a secure, cloud-based location is the best way to stave off disaster here. Polar Backup Unlimited Cloud Backup Storage will give you an unlimited amount of cloud storage while making the process super easy.
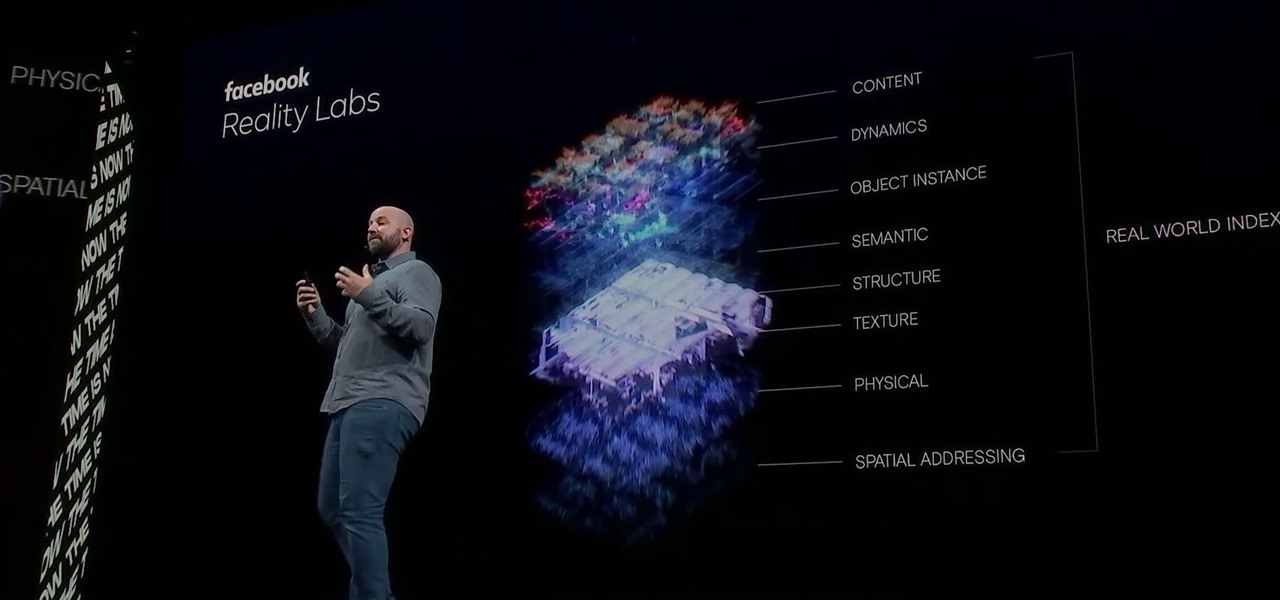
Facebook had a pretty big week in terms of augmented reality, with much of its news coming from the Oculus 6 keynote presentation. But Mark Zuckerberg's social media company found other areas of impact outside of Oculus 6 as well.

The company behind augmented reality's first real gaming hit, Pokémon GO, is quietly making moves toward supporting the rapidly growing smartglasses space that may one day move its content away from smartphones and tablets and onto AR lenses positioned on your face.

Amid the opulent and historic confines of Paris, Microsoft is now hosting an exhibit at a local museum that brings a historic map of a Normandy tourist destination to life in augmented reality.

Outside of early military applications, augmented reality is a relatively new technology. It stands to reason that the next company to make a splash in AR would be a startup, and Techstars wants to help.

Three years ago, with VR enthusiasts prepared to throw their money at Oculus to get their hands on the yet-to-be-release Rift headset, Google surprised the audience for Google I/O with Google Cardboard, a seemingly late April Fool's joke that actually jump-started virtual reality.

As the world goes into a frenzy over the latest strain of WannaCry ransomware, it might be a good time to remember to update all your devices. Yes, those little reminders your phone and computer throw at you every now and then to update your junk can be really annoying, but not without merit.

Osterhout Design Group just announced the upcoming release of the newest addition to their smartglasses lineup, the R-7HL, short for R-7 Hazardous Location. ODG worked directly with customers who work in extreme environments to come up with a durable solution that fits their needs; These smartglasses can not only survive but function well in many areas that would otherwise be considered too harsh for augmented reality tech.

The HoloLens is a natural medium for 3D data visualization, which offers a far more ideal approach over 2D screens to managing multiple resources simultaneously and grasping the bigger picture. We've already seen how management is using holograms to oversee cities, firefighters, and the military, and now training for sports teams is being addressed with VAR Football.

DigiLens, a company specializing in optical waveguide technology, recently announced that they had closed a $22 million round of strategic investment, also known as Series B funding. This round brought in Sony, Foxconn, Continental, and Panasonic, as well as more traditional venture investors such as Alsop Louie Partners, Bold Capital, Nautilus Venture Partners, and Dolby Family Ventures.

If you have some photos, videos, and documents that you want to keep completely hidden and encrypted on your Android device, Andrognito is the app you need. We showcased this app in the past, but since then, CODEX has rebuilt it from the ground up with new and improved features.

Welcome back, my novice hackers! As most of you know by now, a notorious commercial, legal hacking group named "Hacking Team" was recently hacked. As part of the hack, thousands of emails and other material on their servers was divulged. Among the material released were three zero-day exploits. In this tutorial, we will walk through the steps to load one of them, which has become known as the CVE-2015-5119 exploit.

Do you have a major mosquito problem? Well, here's a solution used by the military to drastically cut down their numbers.

Welcome back, my hacker novitiates!

Most of you already know that a zero-day exploit is an exploit that has not yet been revealed to the software vendor or the public. As a result, the vulnerability that enables the exploit hasn't been patched. This means that someone with a zero-day exploit can hack into any system that has that particular configuration or software, giving them free reign to steal information, identities, credit card info, and spy on victims.

Whenever you need to record a quick message to yourself or someone else, the stock Voice Recorder app on the Galaxy Note 2 does a fine job. However, the situations when you need it the most are when you forget or don't care to actually use it, like during a heated argument or a random police stop where your words can be misconstrued or altogether unheard.

No matter how careful or decent you are, there will always be pictures or videos that you want to keep private. They say a picture is worth a thousand words, but if someone were to go through my photo gallery, only one word would be coming out of my mouth—"%@&#!!"

Ever since the early days of their existence, cell phones have been reducing the common wristwatch to nothing more than a fashion accessory. I'm not exactly a watch aficionado, but I do own a few that I wear on a daily basis. Since I have family in different parts of the world, I love my watches that have a second time zone, allowing me to see what time it is where they are.

Over the past few years, indie game developers have gathered together to release their products in the widely popular Humble Indie Bundle, a collection that gamers can purchase for whatever price they want. It's a win-win for both. Developers get more exposure for their games, and customers get tons of games for whatever they could afford. Heck, charities even get a little piece of the pie.

There's really nothing safe about transmitting sensitive information electronically, but even if it gets there safely without being seen by prying eyes, there's no guarantee what happens to it once it reaches its destination. And let's face it, there are some things that you just don't want floating out there forever. So what can you do? Whether you want to send an email, a text, or a link, there are ways to send messages that self-destruct so that once they're read, they immediately vanish. ...

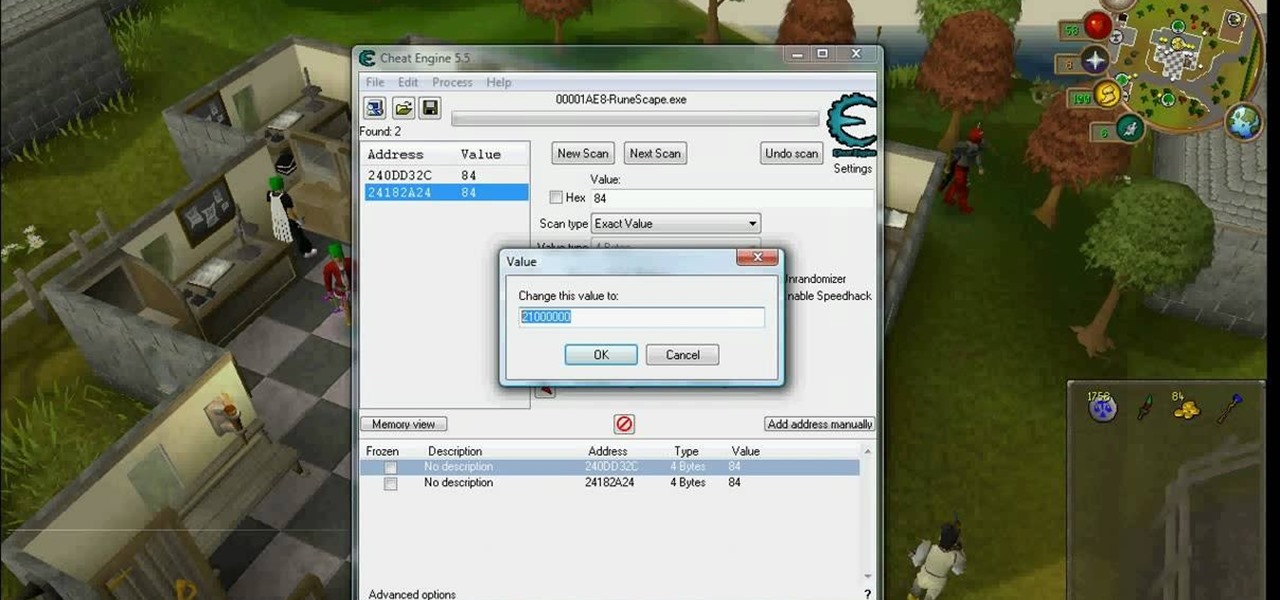
RuneScape hacks, cheats, glitches. How to hack the flash game RuneScape. Watch this video tutorial to learn how to hack RuneScape with Cheat Engine (08/31/09).

Imagine… being able to watch television on your PC. And imagine being able to stop, pause and record those television shows. Well, in Windows 7 it's totally possible. This video shows you the possibilities of Windows Media Center.

Hiddenstuff.com has great tips and tricks for the massive, multiplayer, online, role-playing game, World of Warcraft. Their guides and strategies for WoW are bound to help you out, outlining some of the most important tactics in the video game. This video tutorial will show you how to find the best gold farming maps in World of Warcraft.

There's a new download available for Mafia II on the Xbox 360 (and PlayStation 3), and this walkthrough series will cover the entire gameplay for "Jimmy's Vendetta", which follows the first DLC for Mafia 2, "The Betrayal of Jimmy" (only available for the PS3). This is a lengthy add-on to Mafia II, so watch and learn to see everything involved with getting out alive, as both the Italians and Irish.

The most viral internet cat of the moment is a virtual kitty trapped in a billboard in the Shinjuku district of Tokyo, Japan.

We are now in the age of 5G. Carriers worldwide are upgrading their networks to the newest standard for mobile, which will dramatically improve your phone experience. How? By giving it download speeds and latency that surpass Wi-Fi. But before you upgrade, there are few things you should know first.

Every summer for the last 26 years, hoards of hackers have descended on the Las Vegas Strip for DEFCON, the biggest hacker conference in the US. There's a wealth of talks every season (DEFCON 27 has at least 95 scheduled), and there have been some essential topics to learn from in past discussions. We've dug through the last ten years and found the 15 most popular talks you should watch.

There's something extremely satisfying about hunting down your online adversaries and knocking them out with a well-placed shot, which probably explains why shooting games are still one some of the most popular time killers for iOS and Android.

It is almost indisputable that smartglasses and head-worn displays are the future of augmented reality. However, at this precise moment, they are still a very niche market.

Augmented reality is beginning to leak out into the mainstream world. This is thanks, in part, to ARKit and ARCore. These releases turned the current smartphones owned by millions of Apple and Android users into AR-capable machines. And while there are definitely some awesome use cases for mobile AR, the real future in AR is headworn.

It finally happened! In a world of "go big or go home," Magic Leap has finally done something other than tease us with vague promises and rendered video concepts. Although, other than actually showing us what the developer's kit will look like, it seems little more than a slightly different kind of a tease. To demystify this new product, we here at Next Reality decided to put together what we know about the hardware.

With the release of the Pixel 2 XL and the iPhone X, smartphones have hit a new high not just in price, but also raw processing power. These new flagships not only cost more than twice as much as an Xbox One or PlayStation 4, they have also become almost as powerful as far as gaming goes. Because of this, a lot of games once reserved for consoles and PCs have made their way to our smartphones.

Tossing an old Android smartphone with a decent battery into your hacking kit can let you quickly map hundreds of vulnerable networks in your area just by walking or driving by them. The practice of wardriving uses a Wi-Fi network card and GPS receiver to stealthily discover and record the location and settings of any nearby routers, and your phone allows you to easily discover those with security issues.

Will the predicted apocalyptic date—December 21st, 2012—really be the end of the world? In this ongoing five-part series, we examine what would happen if zombies, nuclear weapons, cyber wars, earthquakes, or aliens actually destroyed our planet—and how you might survive.

Whenever you're on an audio call in the Phone or FaceTime app and accidentally press your iPhone's Side button, the call ends immediately. It's a helpful feature for those who like to terminate calls that way, but it's flat-out annoying for everyone else who inadvertently ends calls prematurely. Now, everybody wins because you can choose what happens during calls when you lock your device.

The march to the mainstreaming of augmented reality can sometimes seem slow, but this week things picked up in earnest.

In the early days of the internet, if something was there and not password protected, you could see it. In the process of becoming the indispensable work and entertainment resource that it is, the internet also grew the same borders that countries have while also getting less safe for the people using it. If you want to watch something, you have to hope it was available in your country. If you want to keep your information safe, you have to take some extra steps to make sure that happens. The...