Microsoft recently released the first sneak peak of their new operating system, Windows 8, and it's a pretty big departure from the last few major updates. The new Windows 8 was built from the ground up, and is designed primarily as a touchscreen interface, which is perfect for the expanding tablet market. They've ditched the clunky start screen that's dominated Windows 95 through Windows 7, replacing it with grids of application tiles, similar in functionality to an iPad or Android tablet, a...

In many of my articles, I will refer to applications designed to empower Mac users to automate various tasks on their computer. One such application is called Hazel. Like smart folders, smart playlists, and smart albums found in Mac OS X and iPhoto, Hazel can automate the task of moving, copying, or deleting files in folders on your Mac. I recommend Hazel as one of the most essential applications for any Mac user. Let's explore how it works.

If you're an owner of a BlackBerry smartphone, chances are you're going to want to use BBM, which for all of you newbie BlackBerry owners, stands for BlackBerry Messenger. BBM is an instant messaging application developed solely for BlackBerry device owners.

The PlayStation Phone is almost here, and the hybrid device from Sony Ericsson is rumored to have Android 2.3 (Gingerbread) as its mobile OS. YouTube user xxmajstor managed to get his hands on what is said to be the Sony Ericsson Zeus - Z1 PlayStation Phone. Below is the spy video of the device in action.
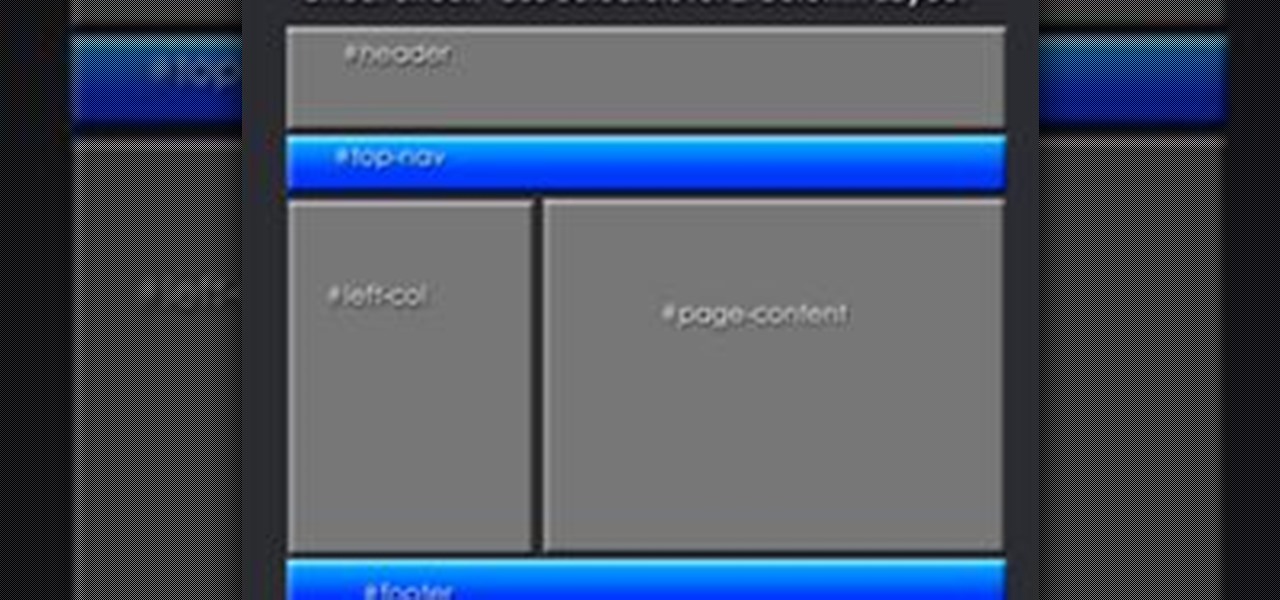
Getting Started Steps for Beginners If you are brand new to Expression Web 4, then read the following guide to quickly set up your web site and web pages.

Through Thursday, January 20th, Borders is offering the Kobo Wireless eReader for $99 with coupon—that's $40 off its typical retail price of $139! Though the Kobo comes preloaded with 100 out-of-copyright classics, new users will nevertheless be interested in filling their new eReaders with their own books.

Meet Aperture 3.1.1, Apple's powerful photo post-production tool with the Amazing Shrinking Price Tag. First released in 2005 for $500, Aperture is now available in the Mac App Store for a measly $79.99—a price reduction of 83.67%! That means a lot of new buyers and, as a result, a lot of new users.

I recommend you take a look into this issue and suggest that your friends delete their association with Gamers Unite and any other cheat providing site. This post is meant only as my advice for how to remove Gamers Unite or any other spammy app. This is all based on my personal feelings about the snag bar and websites that would hand out such cheats. I've provided this as INFORMATION ONLY. Please decide on your own what you think of the whole situation.
Warnings i cant be held responsible for any illegal act done by anyone but myself and there are copyrights so notise that taken the trademarks or copyrights are strigtly prohibeted by law and will be punshied by law and i or my partners cant be held responsible for sudo cammands plz notise that sudo commands are harmful both pysics and fyskel

Assuring A Proper Repair When Welding Vehicle Sheet Metal Any weld that is performed on a vehicle requires certain steps to assure a proper repair. For example, weld-through-primer must be applied to the welded surface being welded; corrosion protection must be applied to the back side of the welded area, etc. In this article we are going to discuss why fiberglass is required for auto body repair.

Many of you who tried to wake up to your iPhone's alarm clock this morning didn't. Reports say that after the stroke of midnight last night, the alarm clock application on all iOS 4 devices simply didn't work— unless you set a recurring alarm.

One of the best new features available in Windows Live Essentials 2011 is Microsoft Office compatibility. The Microsoft Office Web Apps, which are free online companions to all of the Office applications (Word, Excel, PowerPoint, OneNote), allow you to not only view Office documents, but edit and share them, too!

This clip presents a guide on using Soundbooth to access Resource Central and purchase audio files to use in video projects. Accessing and Editing Adobe Sound documents with Adobe media applications.

See how to use Adobe Photoshop CS4 to make the eyes of your subject pop. Whether you're new to Adobe's popular graphic editing program or a seasoned design professional looking to better acquaint yourself with the new features and functions of this particular iteration of the application, you're sure to benefit from this free software tutorial. For more information, watch this designer's guide.

Check out this interactive video tutorial from Verizon Wireless on the Samsung i730 mobile phone. If you have just purchases this sleek cell phone, here's your chance to learn everything you can possibly know about it.

Have you ever noticed that whenever you setup your voicemail account after getting a new cell phone number, it asks you to create a security pin to access your voicemail from other phone lines?

Two weeks ago I reviewed browser-based video editor WeVideo and was amazed. Amazed not because WeVideo is a competent iMovie replacement for the casual editor (which it is), but amazed that a browser-based editor can work at all.

Don't want one of your Facebook "friends" knowing your status updates? Prefer to keep a few of those "friends" out of your photo albums? Would you like to prevent a few "friends" from accessing your address?

Facebook Fan Pages have become extremely popular and are being used by everyone from large companies like Coca Cola and Ford Motors all the way down to people's pets.

This three-part series presents a look at the various forces in DOPs and how they work. This tutorial covers all the major forces except for the vortex, bouyancy and fluid forces. It covers both basic aspects and some more advanced techniques (animated masks, using RBD object position to drive a magnet force).

This tutorial offers a look at using point clouds in shading, and the pcopen, pciterate, and pcimport nodes in VOPs. It also gives a further example of a POP network. Whether you're new to Side Effects Software's popular 3D production program or a seasoned graphic artist just interested in better acquainting yourself with the application, you're sure to be well served by this free video tutorial. For more information, including detailed instructions, take a look.

This four-part tutorial series presents a look at how to combine traditional keyframe animation with DOPs simulation. This first part contains an overview of how DOPs differs from SOPs and how to examine DOPs data using the Details View. It then looks at the RBDKeyFrameActive node as a method for combining keyframe and simulation animation. Whether you're new to Side Effects Software's popular 3D production program or a seasoned graphic artist just interested in better acquainting yourself wi...

An introduction to building a surface shader in VOPs that combines an image texture with procedural shading. This is a rather longer set of videos than normal as it is a complete walk through of creating a shader. The videos are in total are roughly an hour long. Whether you're new to Side Effects Software's popular 3D production program or a seasoned graphic artist just interested in better acquainting yourself with the application, you're sure to be well served by this free video tutorial. ...

A tutorial covering a classic rigid body simulation of ball crashing through a wall of bricks. The first two parts cover building a (procedural) brick wall, and the final two parts cover converting it into a RBD simulation. Whether you're new to Side Effects Software's popular 3D production program or a seasoned graphic artist just interested in better acquainting yourself with the application, you're sure to be well served by this free video tutorial. For more information, including detailed...

This is a Photoshop tutorial for digital photographers. Learn how to improve the midtone contrast of your images with this Photoshop tutorial. You can really improve the midtone contrast of your images just by following a few simple step. Watch this tutorial to find out how.

Once you learn how to knit an I-CORD you will find many different applications in which to use them. One thing I like to do is to make a FLOWER from an I-Cord. The flower can then be applied to a sweater, a blanket, a scarf, a purse. There are limitless possibilities.

OpenGL (OPEN Graphics Language) is a 3D graphics language developed by SGI. It has become a de facto standard supported in all Unix, Linux, Windows and Macintosh computers. To start out developing your own 3D games and programs, you need to know OpenGL and C++. This video lesson will show you how to use transformations and timers with OpenGL and GLUT for C++, so you can start making your own 3D programs. If you want to create your very first OpenGL project, this is the place to be.

Edit your photos with ease with Canon's free software, Digital Photo Professional (DPP). It's primarily for editing and processing Canon RAW files. See everything there is to know about this comprehensive photo editing software bundled with most of your Canon Digital SLR cameras.

In this four-part programming lesson from the Absolute Beginner's Series of Visual Web Developer C#/ASP.NET video tutorials, you'll learn how to build a quiz engine.

This video tutorial will show you the process of drawing blood from rats through the saphenous vein and by cardiac puncture.

There are a million tutorials on the Internet for how to transmit redstone power up and down, but that's because vertical power transfers are both really important and very counterintuitive. This quick and easy guide should help clear it up!

Looking for some new furniture? Don't know what to do with that small corner in the living room? Do you need more room for storing and organizing, but that tiny gap of space gives you no real freedom of choice?

Here's a nasty little Null Byte. An open redirect vulnerability was found in both Facebook and Google that could allow hackers to steal user credentials via phishing. This also potentially allows redirects to malicious sites that exploit other vulnerabilities in your OS or browser. This could even get your computer flooded with spam, and these holes have been known about for over a month.

Only so much data can be passed through the network and to your computer's networking interfaces. This is limited by the amount of bandwidth you have. The more bandwidth you have, the faster your network connections will be. Not only this, but your transfers will be more parallel and distributed so that all of your speed isn't taken up by one transfer. When all of your bandwidth is sapped and unable to be used, this is called a denial of service, or a DOS.

If you've ever wondered how software pirates can take software and crack it time and time again, even with security in place, this small series is for you. Even with today's most advanced methods of defeating piracy in place, it is still relatively easy to crack almost any program in the world. This is mainly due to computer processes' ability to be completely manipulated by an assembly debugger. Using this, you can completely bypass the registration process by making it skip the application'...

The HP Touchpad 64 GB is out in action with a robust processor and additional applications in the market. Using the best technology on earth, it is looking forward to give a tough fight to the Apple’s iPad 2. The 64 GB HP TouchPad sound more promising to its predecessors. The experts feel that the two device, HP TouchPad 64 and Apple’s iPad-2 is more or less the same. Let’s have a glance over the device by discussing the various features it encompasses.

You'll see a lot of Linux action going down here at Null Byte. We use Linux for hacking-related stuff because it provides a more relaxed programming environment, making it easy to write exploits and tools. Linux has many features Windows is lacking, such as full control over the OS right down to the Kernel and massive availability of mature, open source (read: free & tweakable) tools & projects.

There are lots of Linux distros out there. Normally, you'll have to download the ISO and then burn the image onto a CD. But nowadays, it's easier and cheap to install it on a USB drive.

Today's segment of Making Art on Your iOS Device takes us into the third dimension. The below apps are suitable for beginners looking to venture into the world of 3d modeling, as well as pros who simply want the basics of Maya in their pocket.

If you've gained entry into Google+, one of the first things you should do is adjust your Google account settings. Your settings will now look quite different, and you can adjust your notifications, password retrieval methods, and more. There are many settings that you may not have been aware of before.