Mike Lively of Northern Kentucky University demonstrates how to create a 3D plotting program for the sinc math function. Part 1 shows how to convert a Flash Package into a Flex application. Part 2 shows how to get the sinc function running and add different textures. Create a cool interactive 3D plotter in thie Adobe Flex Builder 3 and Papervision3D tutorial.

A PDF file is a great way to share your documents with anyone. Both Macs and PCs can read them and it's very easy to create them in Mac OS X. From any application that you can print from, go to File–Print–which will open up the print dialogue box–and find the PDF button in the lower left corner. To learn more, and for a complete walkthrough of printing to PDF in Mac OS X (as well as information on using the handy Web Receipts) feature, watch this video tutorial.

Pop/R&B singer Ashanti is the basis of this pretty silver and grey eye look. This how-to video demonstrates how to replicate this look that will really define your eyes. The cosmetic products used to create this look are Studio Fix Fluid Foundation, Makeup Forever HD Powder, Mineralize Skinfinish Duo in “Medium Dark,” Mineralize Blush in “Pleasantry,” Cream Color Base in “Pearl,” Painterly Paintpot, Platinum Pigment, Concrete e/s, Kid e/s, Brule e/s, White Frost e/s, Blacktrack Fluidline, Lor...

Just a few years ago, Britney Spears was considered hot. Regardless of what you think of her now, this how-to video recaptures her glory days via makeup. The cosmetic products used to create this look are MAC Studio Fix Fluid mixed with Covergirl Trublend, Bare Escentuals Foundation, NARS Laguna Bronzer, MAC Warm Soul Blush, MAC Cream Color Base in “Pearl,” MAC Blackground Paintpot, 88 Shimmer Palette from Coastal Scents, MAC Black Tied e/s, MAC Blacktrack Fluidline, Urban Decay 24/7 Eyeliner...

Three point lighting is the standard used to illuminate a subject for amateur film, video, and even theater application.

One of the worst-kept secrets in the tech world is Apple's plans for consumer-grade AR smartglasses, still unconfirmed publicly and only recently corroborated through a leaked account of an internal employee meeting.

With $100 million in grant funding already available to developers via its MegaGrants program, Epic Games is sweetening the pot with some gear for Magic Leap developers.

An augmented reality system developed by Lyft might make it less awkward for drivers to figure out who they are supposed to pick up.

Cross-site scripting is one of the most common vulnerabilities found on the web today, with repercussions of this type of flaw ranging from harmless defacement to sensitive data exposure. Probing for XSS can be tedious and time-consuming for an attacker, but luckily there are tools available to make things a little easier, including Burp Suite, Wfuzz, and XSStrike.

Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.

It's always a good idea to know how an attack works at the very basic level. Manual techniques for exploitation often find holes that even the most sophisticated tool cannot. Sometimes, though, using one of these tools can make things so much easier, especially if one has a solid foundation of how it works. One such tool can help us perform a cross-site request forgery with minimal difficulty.

Web 2.0 technology has provided a convenient way to post videos online, keep up with old friends on social media, and even bank from the comfort of your web browser. But when applications are poorly designed or incorrectly configured, certain flaws can be exploited. One such flaw, known as CSRF, allows an attacker to use a legitimate user's session to execute unauthorized requests to the server.

In the wake of the smoke from the meticulously orchestrated launch of Magic Leap One, the company has revealed what "leapers" can expect to experience via Lumin OS when their devices arrive between now and the end of the year.

Web application vulnerabilities are one of the most crucial points of consideration in any penetration test or security evaluation. While some security areas require a home network or computer for testing, creating a test website to learn web app security requires a slightly different approach. For a safe environment to learn about web app hacking, the OWASP Juice Shop can help.

With the V30, LG has really delivered an amazing smartphone that hits all the major features consumers want. Amazing camera, beautiful edge-to-edge display, great battery life, water resistance, and smooth performance — there isn't much not to like about the LG V30. Unfortunately, it does suffer from heavy bloatware thanks to the carriers. The good thing is, unlike in the past, you are not stuck with it.

A potentially groundbreaking new app targeting retail financial services hopes to bring augmented reality to your local bank and credit union.

Intel's driverless division will be managed by Israel-based Mobileye, as the chip giant emerges from relative obscurity in the driverless space to become a major supplier after completing its $15.3-billion purchase of Mobileye this week.

Getting your green card can be an extraordinarily complicated and difficult task. Often times it seems so daunting that it's hard to know where to begin. Thankfully, Facebook Messenger introduced "Visabot" last year, a chatbot in the app that helps with all things immigration. Now including applying for your green card.

Magic Leap has always been intensely secretive about its work on its augmented reality headset, so it's interesting that they're now publicly recruiting developers to build software for the device before its launch.

This week's Brief Reality is led by a pair of stories with an eye to the future of the augmented reality industry, first in terms of standards for the industry, then with regards to its future applications in the automotive realm. Finally, one company looks to boost its future sales with an executive hire.

Augmented reality software developer Edgybees has launched Drone Prix. The new mobile app immerses DJI drones and their pilots in more than 30 augmented reality obstacle courses.

Have you ever wanted to control a swarm of robots? Well, now you can! Robotics researchers at New York University (NYU) have created an app which controls 'bots from your smartphone, using augmented reality. This AR app would certainly come in handy when you want to make a coffee from the comfort of your couch, but let's not get ahead of ourselves!

Apple recently scored a patent (number 9,488,488) to create augmented reality maps, hinting at possible AR integration into the iOS Maps application for iPhone. Does this mean we'll be seeing super visionary projections of places in the app in the near future? Maybe.

A development team in Silicon Valley is nearing early access release of a new hardware-independent augmented reality platform called Phantom AR.

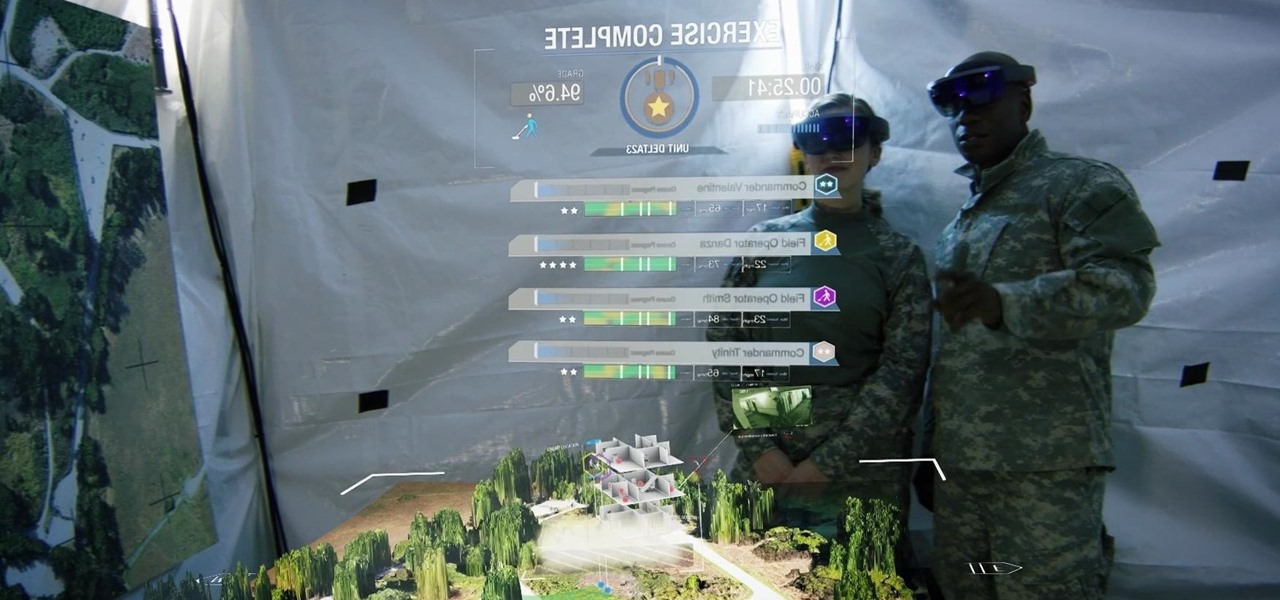
The limitless applications of 3D data visualization will enable a more efficient approach to many of life's problems. Each day, developers exploring this technology are finding new ways to solve these problems in mixed reality; 3D modeling, easier house management, spinal surgery, and forest fire management are just a few recent examples of ways 3D data visualization can benefit us all.

Last month, Dr. Sung-Hoon Hong, Vice President of Samsung Electronics, announced at the Virtual Reality Summit in San Diego that Samsung would be moving into the augmented reality market. According to a recently published patent application, that move has begun.

Here at NextReality, we talk a lot about the many different ways of controlling holograms in the HoloLens and other augmented and mixed reality devices; New and creative ways are coming more and more every day. Most recently is something called the HoloSuit. In the 25-second clip below, you can see a woman moving the arm of a jacket which in turn moves a 3D model of Darth Vader on the screen. It's a simple idea with big potential.

Welcome back, my tenderfoot hackers! As you should know from before, Snort is the most widely deployed intrusion detection system (IDS) in the world, and every hacker and IT security professional should be familiar with it. Hackers need to understand it for evasion, and IT security professionals to prevent intrusions. So a basic understanding of this ubiquitous IDS is crucial.

Hola my fellow hackers! I promised you the tutorials on setting up RAT's and Botnets, but before jumping into those, i want you to know about the precautionary measures and detection of RATs which might be on the system without your prior knowledge. Of course the Anti-virus do most of the job but there are some RATs which slips past the Anti-viruses (This is where Hacker's skill come into play).

Apple makes it easy to access your favorite and most recently used applications and documents in Mac OS X. You can simply add your favorite apps and folders to the dock, and you can always visit the Apple menu from the menu bar to see a list of your most recently used apps and docs.

A lot of people think that TOR services are unhackable because they are on a "secure environment", but the truth is that those services are exactly the same that run on any normal server, and can be hacked with the same tools (metasploit,hydra,sqlmap...), the only thing you have to do is launch a transparent proxy that pass all your packets through the TOR network to the hidden service.

The dock in Mac OS X is intuitive, customizable, and aesthetically pleasing, which is a stark difference from its clunky Windows alternative. In fact, in Windows, it takes both the Start menu and taskbar to accomplish what Apple's dock does—but it doesn't have to be like that. Below, I'll show you how to add an OS X-inspired dock on any PC running Windows XP or higher. Step 1: Install Aqua Dock

Are you tired of uploading videos to different sites separately? It's really time consuming and difficult. Finally, there is a way to upload and distribute your videos to YouTube, Facebook, Dailymotion, and many more video-hosting websites in one go. No need to upload to every site separately and one by one.

Keyboard shortcuts can make using your Mac faster and easier, and leave your mouse feeling archaic. With just a few taps, you can save files, open new tabs, or play a movie—all without using your mouse even once.

There are countless beauty tools, from expensive brushes that perfect your application of powder to carefully shaped smoothing pads that help you to blend your makeup. Yet hiding in your silverware drawer is a free and highly useful beauty tool that can help you create an even more sophisticated look: a spoon.

Believe it or not, not every Apple lover is willing to make the commitment and fork over $350+ for the Apple Watch. Like many others, I'm not willing to put that much faith into Apple's first attempt at wearable tech.

Welcome back, my hacker novitiates! In an earlier tutorial, I had introduced you to two essential tools for cracking online passwords—Tamper Data and THC-Hydra. In that guide, I promised to follow up with another tutorial on how to use THC-Hydra against web forms, so here we go. Although you can use Tamper Data for this purpose, I want to introduce you to another tool that is built into Kali, Burp Suite.

By default, whenever you plug your iPhone into your Mac computer, iPhoto automatically launches alongside iTunes. While this can be useful for those who like syncing their photos with iPhoto, it's annoying to those who don't. Even if you do sync with iPhoto, chances are you don't want it popping up every time you want to charge your iPhone or sync with iTunes.

You don't need a study to tell you how beneficial music is to helping you fall asleep. Most of you probably have your soothing playlist and SleepPhones queued up and ready to go before you get into bed and count those Zs.

Welcome back, my nascent hackers!