While playing Fortnite Battle Royale, you may have noticed a few players wearing different outfits or using fancy dance moves. These are cosmetic items that can only be obtained by unlocking them. However, unlocking items in Fortnite is a little different than many free-to-play games.

In Guardians of the Galaxy Vol. 2, Mantis resides in the shadow of an Ego who considers himself the actual heart of the universe. But when it comes Halloween costumes? Mantis will be the center of attention every time. The internet sure has noticed Mantis, and it's abuzz with debate over who she is. Is she just another iteration of the submissive Asian woman stereotype? Or is her character an empowering representation of empathy and the autism spectrum?
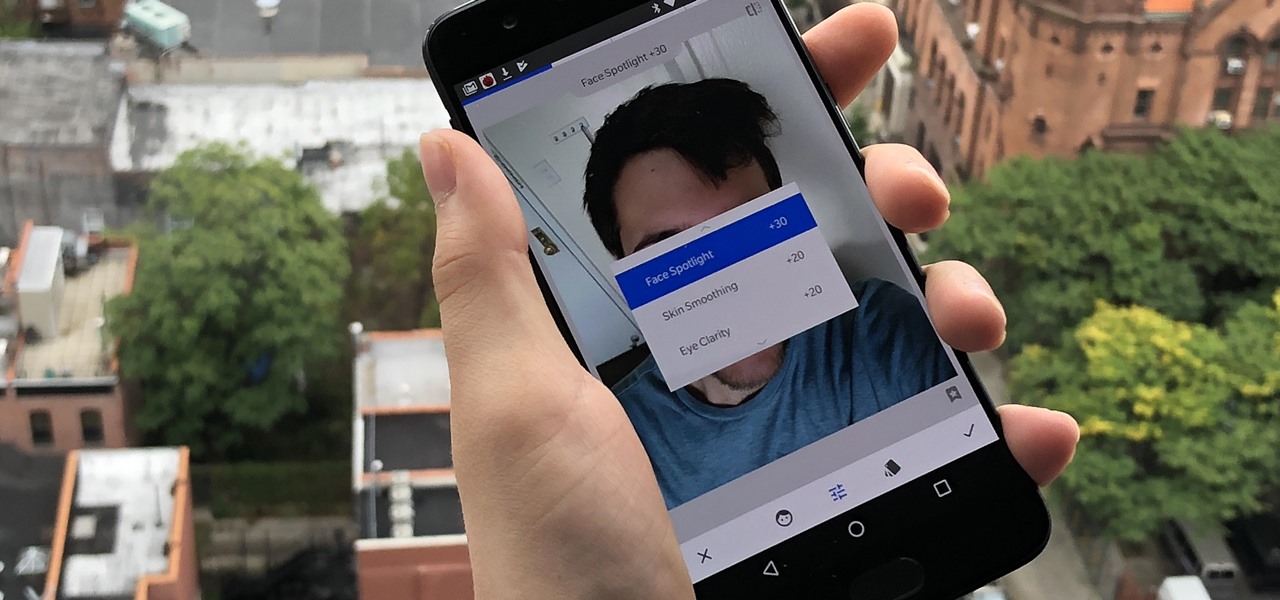
Google's Snapseed app has a plethora of editing tools to help make your photos even better. But did you know it has specific tools designed to edit your face? Not that it needs any help, of course!

For some of us, winter puts the brakes on apps like Pokémon GO since smartphone screens usually only respond to bare fingers. Nobody wants to be that guy who caught frostbite chasing a Sneasel. When you use normal gloves, the display's sensor simple doesn't activate, so that doesn't help any. Fortunately, several options for touchscreen-friendly capacitive gloves are on the market to help you through this last blast of winter.

Whether you're a seasoned wine drinker or just beginning to explore the wondrous world of fermented grapes, finding fantastic wine on a budget isn't as difficult as one may think. With these 8 tips, you'll see how and why you need not shell out $45 to get a great-tasting, high-quality bottle of wine without settling for vino.

In my last tutorial, I talked about creating a virus inside of a Word Document in the scenario of a mass-mailer attack. In this post, however, I'm going to be covering creating a fake image or screenshot with a meterpreter backdoor hidden inside to be used in a similar scenario. Step 1: Creating the Virus

Welcome back! Sorry for being so quiet, I've been rather busy with this project lately! Anyways, in the last iteration of how to train your python, we covered lists. Today we'll be introducing iteration and the two loops python has to offer, for and while. Also, we'll be covering a couple general use functions. So, let's get started!

Hello all, this is my first submission to null byte! I noticed something a little strange, particularly that whenever Meterpreter is discussed, it is virtually always in the context of Windows. Granted, the Windows Meterpreter is more powerful than the version that can run on OS X (it has several more commands/options), but I think it is still worth noting how to do it. I've even seen some people mistakenly say that Meterpreter can only be run on Windows, which is not true. Meterpreter can ea...

Desktop users have taken advantage of dual-booting operating systems for decades now. If your core system software is lacking in any regard, dual-booting a secondary OS can give you access to those features that you're missing out on.

Welcome back, my hacker novitiates! A short while ago, I introduced you to regular expressions. Regular expressions are a language that is particularly useful for finding complex text patterns in streams of data.

When the Chromecast first came out about a year ago, developers were quick to find a way to root the streaming device. Google was almost as fast, however, in updating the Chromecast's firmware to close the loophole that this method used.

My phablet has incredible battery life, but that doesn't mean I wouldn't like it to last even longer. Unlike the Samsung Galaxy S5, the Note 3 does not come equipped with Ultra Power Saving Mode, which can keep the phone running for another 24 hours with only 10% power remaining.

Why can't I see who is stalking my Facebook profile?

Many of us in the Steampunk community have pets that we love and cherish, myself included, and we want those pets to share our joy of Steampunk. In reality, they couldn't care less, but for some reason we still love to dress them up. Their reactions usually range from bemused acceptance to temper tantrums, but the awwwws we get from onlookers usually makes it worthwhile.

During its annual autumn keynote address, Apple didn't move heaven and earth. Instead, the company pushed the envelope ever so slightly forward for its marquee consumer devices.

After piloting the Nreal Light in South Korea and Japan via carrier partnerships and securing another round of funding, Nreal is now ready to begin selling the consumer edition of the smartglasses to the western world as well as introduce a version for enterprise customers.

The two primary design paradigms in Samsung's One UI Android skin are vertical padding and rounded UI elements. The extra empty space at the top of most menus moves touchable elements closer to your thumb, and the rounded UI elements match the curved corners of modern smartphone screens. While you can't add the vertical padding on other Android phones, you can now get the rounded corners.

Like with many aspects of One UI, Samsung's changes to Android's volume panel are controversial. Between the different orientation and alternative design, it isn't for everyone. Fortunately for Android purists, there's an app to solve this problem.

If you've ever wanted to track down the source of a Wi-Fi transmission, doing so can be relatively easy with the right equipment.

While many people may use Bluetooth every day, the majority don't know how it works or that it can be hacked. Bluetooth hacking gives a clear window into the world of the target. Nearly every device has Bluetooth capabilities, and people store a great deal of personal info on their phones and tablets. Hack their Bluetooth connection, and you may be able to access all of that data.

We've already shown you our favorite new action games that have come out this year, but now it's time to share our all-time top ten list. These games are available for both Android and iPhone, they don't have intrusive ads or freemium schemes, and most importantly, they're all completely free to play.

The PlayStation 4 has been around since 2013 and has brought with it countless game releases since then. One thing that hasn't changed, though, is the strict device restrictions on the PS4 Remote Play feature for streaming your games. The capability has always been there, but you still had to have an iPhone or Sony smartphone to get the best experience possible — until now.

Nintendo may be developing cases that'll turn your iPhone into a gaming device like the Game Boy, but until something materializes there, you're stuck with cheap knockoffs on Amazon or a real Game Boy or Game Boy Color. But there's something else you can do to play eight-bit Nintendo games on your iPhone right now.

When new Android versions come out, the modding community has to find new ways to root the OS. It's a fun cat and mouse game to follow, but it also means the process of rooting isn't exactly the same as it was the last time you did it. Android 10 changes how root works on a system level for some devices, but luckily, the developers are already on top of things.

Samsung Health has become one of the most comprehensive wellness apps thanks to features that cover everything from step counting to nutrition logging and symptom diagnosis. But because the app has so much to offer, it can be easy to overlook some smaller, but useful features.

For anyone wanting to keep information private, plain text is a format of the past. Instead, cheap, powerful encryption is widely available, but often not easy enough to use to attract widespread adoption. An exception to this rule is EncryptPad, an easy to use application that lets you encrypt text, photos, or archives with strong encryption using a password, keyfile, or both.

The Raspberry Pi Zero W and Pi 3 Model B+ include integrated Wi-Fi, Bluetooth Low Energy, and more than enough power to run Kali Linux. They sound like perfect all-in-one penetration testing devices, but the lack of support for monitor mode and packet injection usually meant buying a supported Wi-Fi adapter. Now, it's possible to use monitor mode on the built-in Wi-Fi chip with Nexmon.

Single sign-on (SSO) lets users login across different sites without having to manage multiple accounts. I'm sure most of us appreciate the convenience of seeing "Sign in with …" buttons that let us login with a single username. Hackers, however, see a possible avenue for exploitation, and you'll soon learn how an attacker can exploit a SAML vulnerability to assume another user's identity.

PUBG is currently taking the mobile world by storm, and it's easy to see why. The game has breathed much-needed life to the multiplayer shooting genre, primarily by adding an element of sheer terror as you scavenge for weapons in a hostile environment. With new players continually joining in on the fun, many players are looking for ways to gain an edge.

Dating websites allow you to see a person in a very intimate context, framing their successes and accomplishments in life to an important audience. The information contained in these profiles often can't be found elsewhere, offering a unique look into the personal life of the user.

To please those of us who love to mod and root our Androids, OnePlus has made both the OnePlus 5 and 5T relatively easy to customize — so much so that the 5T topped our list for the best phones for rooting. Unfortunately, unlocking the bootloader and using root to modify the firmware on your OnePlus 5 or 5T makes it hard to update to a new firmware such as Oreo when compared to stock.

Nova Launcher is one of the most popular apps on the Play Store thanks to its rich features and fluid navigation. But one downside that comes with this abundance of features is that much of Nova's functionality is lost on the masses. Fortunately, I've used Nova for several years and learned a few tricks along the way.

Apple released the iOS 11.2 update for the iPhone to the masses early morning on Dec. 2, and here are all the new features and important bug fixes you need to know about.

Threats to your privacy and security are everywhere, so protecting your data should be the highest priority for anyone with a smartphone. However, one threat many people overlook is the company who supplies the operating system your Android phone runs — Google.

Despite concerns with SafetyNet, Google actually cares about root. Every phone they sell has an unlockable bootloader, so you can toggle a setting and send a Fastboot command, then start flashing custom firmware right away. The Pixel 2 and Pixel 2 XL continue this tradition, and now they have an official root method.

If preorder delays are any indication, the iPhone X certainly has some buzz. But does the X have the quality to support that buzz in the long run? After all, a $1,000 (or more) iPhone feels more like an investment than a smartphone purchase. The question on any prospective buyer's mind should be, "Is this thing worth it?"

In 2013, Offensive Security released Kali Linux, a rebuild of BackTrack Linux derived from Debian. Since then, Kali has gone on to become somewhat of a standard for penetration testing. It comes preconfigured with a collection of tools accessible by a menu system, tied together with the Gnome desktop environment. However, Kali Linux isn't the only penetration-testing distribution available.

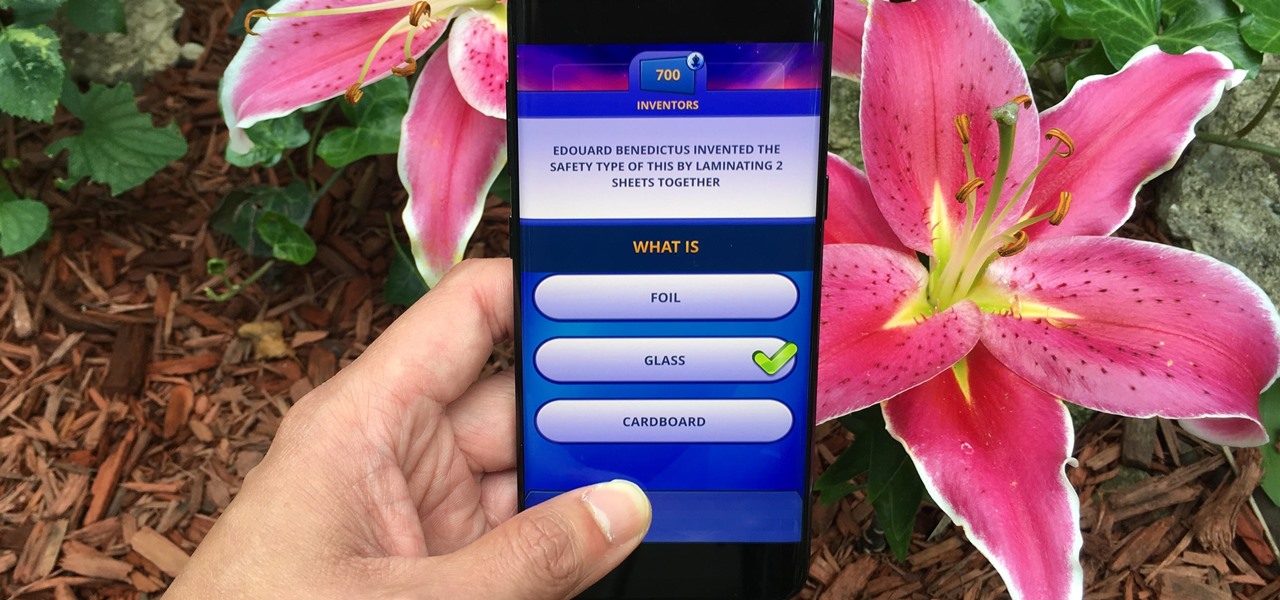
Trivia games are a great way to test your knowledge and learn about people and things you never knew of before. They're ideal in a group setting because they can serve as the perfect conversation starter when you're enjoying time with friends, family, or even complete strangers.

The Galaxy S8 has finally touched down, and it's an absolutely gorgeous device. Samsung's brand new flagship comes jam-packed with new features — some refined, and some that aren't. Luckily, we've compiled some major features to help you get started as quickly as possible so you can go about the rest of your day and show off your shiny new S8 to friends and coworkers.